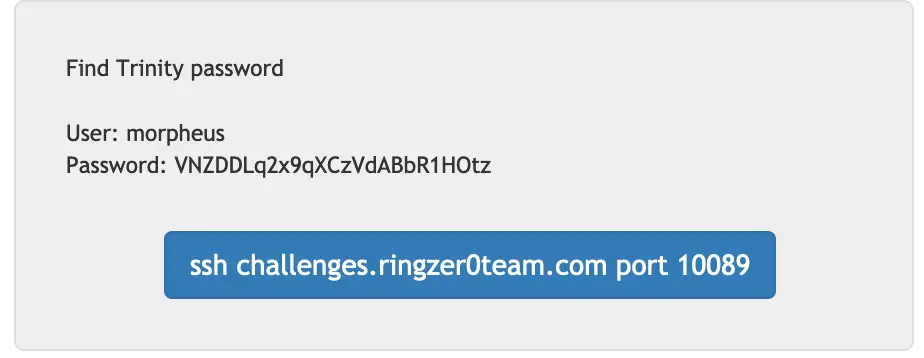
We're given a box to ssh into, lets do this.
$ ssh morpheus@challenges.ringzer0team.com -p 10089
The authenticity of host '[challenges.ringzer0team.com]:10089 ([78.109.87.50]:10089)' can't be established.
ECDSA key fingerprint is SHA256:ay3OoeHJOwmJrQs+ug/kjJHyNCaV3hUcxrqat7jmFI8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[challenges.ringzer0team.com]:10089,[78.109.87.50]:10089' (ECDSA) to the list of known hosts.
morpheus@challenges.ringzer0team.com's password:
888888ba oo d8888888P a8888a d888888P
88 8b .d8' d8 8b 88
88aaaa8P dP 88d888b. .d8888b. .d8' .d8888b. 88d888b. 88 P 88 88 .d8888b. .d8888b. 88d8b.d8b.
88 8b. 88 88 88 88 88 .d8' 88ooood8 88 88 88 d 88 88 88ooood8 88 88 88 88 88
88 88 88 88 88 88 88 d8' 88. ... 88 Y8 8P 88 88. ... 88 88 88 88 88
dP dP dP dP dP `8888P88 Y8888888P `88888P' dP Y8888P dP `88888P' `88888P8 dP dP dP
oooooooooooooooooooooooo 88 ooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo
d8888P
+---------------------------------+
| Welcome to the Sysadmin track |
| |
| - Play nice and play Fair - |
| |
|----[ info@ringzer0team.com ]----|
Last login: Mon Jul 13 12:46:43 2020 from 69.159.171.94
morpheus@lxc-sysadmin:~$
And let's start poking around:
$ ls -al
morpheus@lxc-sysadmin:~$ ls -al
total 20
dr-x------ 2 morpheus morpheus 4096 Oct 17 2018 .
drwxr-xr-x 8 root root 4096 May 30 2018 ..
lrwxrwxrwx 1 root root 9 May 30 2018 .bash_history -> /dev/null
-r-x------ 1 morpheus morpheus 220 Aug 31 2015 .bash_logout
-r-x------ 1 morpheus morpheus 3771 Jun 2 2018 .bashrc
lrwxrwxrwx 1 root root 9 Oct 17 2018 .mysql_history -> /dev/null
-r-x------ 1 morpheus morpheus 655 May 16 2017 .profile
Huh, I was expecting a readme or something to go off...
$ cat .profile
# ~/.profile: executed by the command interpreter for login shells.
# This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login
# exists.
# see /usr/share/doc/bash/examples/startup-files for examples.
# the files are located in the bash-doc package.
# the default umask is set in /etc/profile; for setting the umask
# for ssh logins, install and configure the libpam-umask package.
#umask 022
# if running bash
if [ -n "$BASH_VERSION" ]; then
# include .bashrc if it exists
if [ -f "$HOME/.bashrc" ]; then
. "$HOME/.bashrc"
fi
fi
# set PATH so it includes user's private bin directories
PATH="$HOME/bin:$HOME/.local/bin:$PATH"
.local in the path would be useful for phishing, but other than that, nothing interesting.
Let's keep poking around
$ ls -al /home
total 32
drwxr-xr-x 8 root root 4096 May 30 2018 .
drwxr-xr-x 22 root root 4096 Jul 7 01:26 ..
dr-x------ 2 architect architect 4096 Oct 17 2018 architect
dr-x------ 2 cypher cypher 4096 Oct 17 2018 cypher
dr-x------ 2 morpheus morpheus 4096 Oct 17 2018 morpheus
dr-x------ 2 neo neo 4096 Oct 17 2018 neo
dr-x------ 3 oracle oracle 4096 Oct 17 2018 oracle
dr-xr-x--- 2 trinity neo 4096 Oct 17 2018 trinity
$ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.0 37228 5304 ? Ss Jul07 0:44 /sbin/init
root 38 0.0 0.1 158480 106316 ? Ss Jul07 10:22 /lib/systemd/systemd-journald
root 84 0.0 0.0 28980 2924 ? Ss Jul07 0:02 /usr/sbin/cron -f
syslog 86 0.0 0.0 256392 4208 ? Ssl Jul07 2:09 /usr/sbin/rsyslogd -n
root 156 0.0 0.0 65508 6528 ? Ss Jul07 2:37 /usr/sbin/sshd -D
root 159 0.0 0.0 4504 1608 ? S Jul07 0:10 /bin/sh /root/files/backup.sh -u trinity -p Flag-xxx
root 172 0.0 0.0 15752 2212 pts/2 Ss+ Jul07 0:00 /sbin/agetty --noclear --keep-baud pts/2 115200 38400 9600 vt220
root 175 0.0 0.0 15752 2212 pts/0 Ss+ Jul07 0:00 /sbin/agetty --noclear --keep-baud pts/0 115200 38400 9600 vt220
root 176 0.0 0.0 15752 2212 ? Ss+ Jul07 0:00 /sbin/agetty --noclear --keep-baud console 115200 38400 9600 vt220
root 177 0.0 0.0 15752 2212 pts/3 Ss+ Jul07 0:00 /sbin/agetty --noclear --keep-baud pts/3 115200 38400 9600 vt220
root 179 0.0 0.0 15752 2212 pts/1 Ss+ Jul07 0:00 /sbin/agetty --noclear --keep-baud pts/1 115200 38400 9600 vt220
mysql 182 0.0 0.2 1282828 190004 ? Ssl Jul07 3:53 /usr/sbin/mysqld
root 1353 0.0 0.0 90488 6840 ? SNs 22:47 0:00 sshd: morpheus [priv]
morpheus 1368 0.0 0.0 90488 3380 ? SN 22:47 0:00 sshd: morpheus@pts/4
morpheus 1369 0.0 0.0 21180 3740 pts/4 SNs 22:47 0:00 -bash
root 1598 0.0 0.0 65508 6264 ? Ss 22:50 0:00 sshd: [accepted]
sshd 1599 0.0 0.0 65508 724 ? S 22:50 0:00 sshd: [net]
root 1600 0.0 0.0 7288 640 ? S 22:50 0:00 sleep 10
root 1603 0.0 0.0 90340 6816 ? Ss 22:50 0:00 sshd: unknown [priv]
sshd 1604 0.0 0.0 65508 3336 ? S 22:50 0:00 sshd: unknown [net]
root 1605 0.0 0.0 90340 6816 ? Ss 22:50 0:00 sshd: unknown [priv]
sshd 1606 0.0 0.0 65508 3336 ? S 22:50 0:00 sshd: unknown [net]
morpheus 1607 0.0 0.0 37364 3320 pts/4 RN+ 22:50 0:00 ps -aux
root 30389 0.0 0.0 49932 3404 ? SN 22:00 0:00 su neo -c /bin/monitor
neo 30391 0.0 0.0 4216 612 ? SNs 22:00 0:00 /bin/monitor
Oh damn, that was easy! Flag-xxx