ChatGPT for Hardening Ubuntu 22.04 Desktop
Every so often I reinstall my daily driver OS, this is a weird habit I've had for as long as I can remember. It's sort of like spring cleaning! It's so fast these days to get software installed, and all my data is baked up in my homelab so what do I have to lose? Hopefully just all the bloatware that I've hap-hazardly installed each year. The piece that is annoying for me is doing all the hardening steps required. I could of course go use a pre-hardened distro but I don't want all the other bloatware that comes with it. I also don't want to be completely hardcore and setup Arch so I'm starting from a minimal install of Ubuntu Desktop 22.04 LTS. I've been using ChatGPT at work to make some tasks a little easier, with varying levels of success. I was thinking ChatGPT could be perfect for this hardening task - if I were to do it manually it's essentially hours of searching google for best practices and procedures to meeting them. ChatGPT should be able to quickly get me the info I need, right? We'll see!
Getting Started

This isn't too bad at a high level - I think the only categories it missed was something to watch file integrity and anything about the general steps you'd immedately take to make the OS settings more secure. For file integrity I'll be using Wazuh with Security Onion. Let's ask ChatGPT to provide some initial settings for the OS.
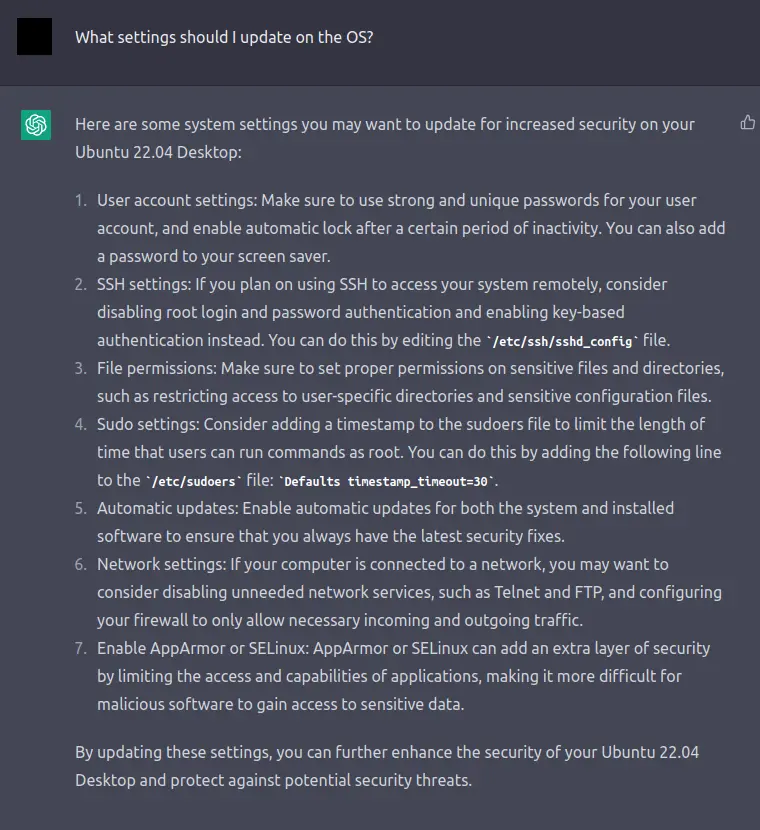
That's more like it! Let's actually follow the procedure, it's fairly valid.
User Account Settings
Ensure a strong password is used - check.
Ensure automatic lockout is configured - check:
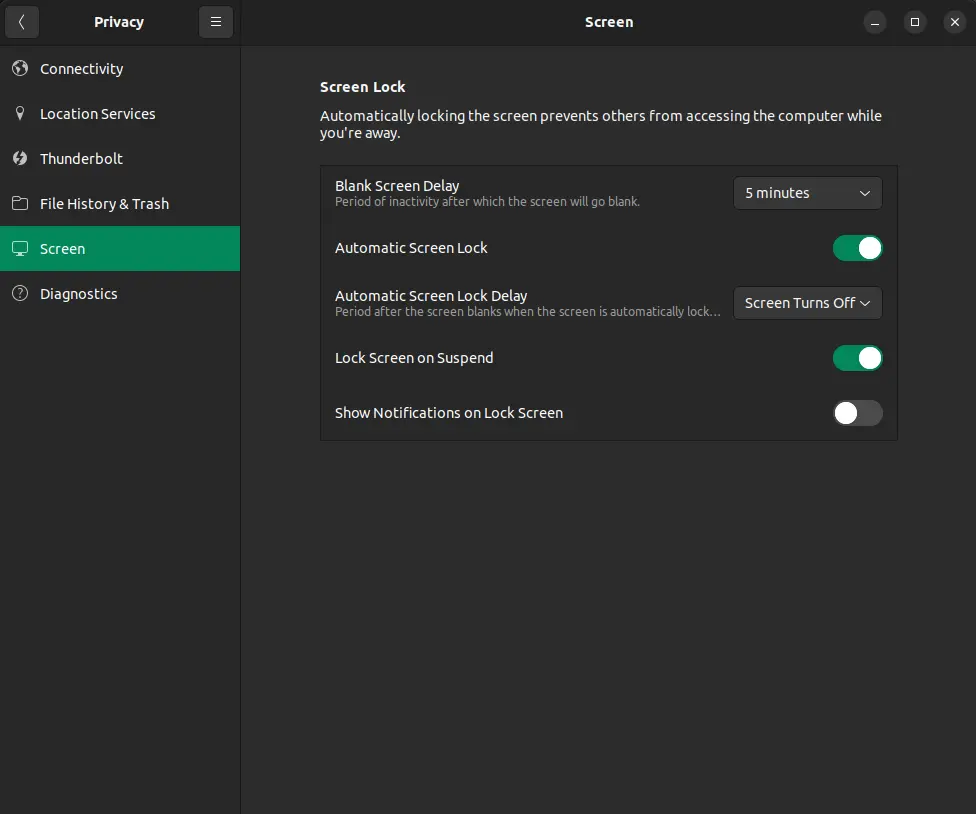
'Password to screensaver' - check.
All of these settings were sufficient out of the box.
SSH Settings
The next item ChatGPT suggests we dive into is configuring our OpenSSH server. I don't plan on allowing ssh inbound to my workstation, so I just confirmed that openssh server is not running.
File Permissions
This one is more of an issue as we continue to use the system, other than doing things like locking down /tmp? Perhaps there's more, let's ask!
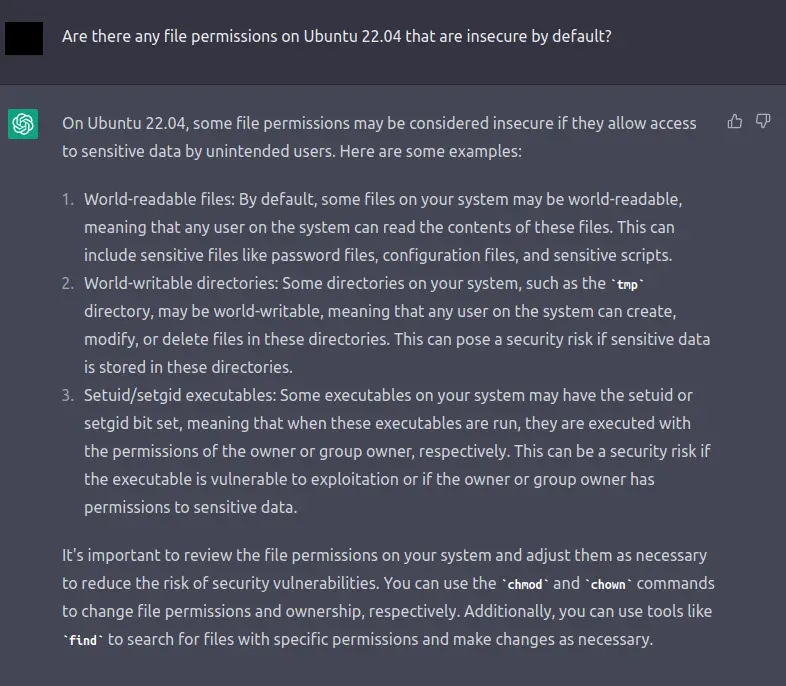
These are all things we look for while doing privilege escalation. Let's have ChatGPT write us a script to look for these on our system.
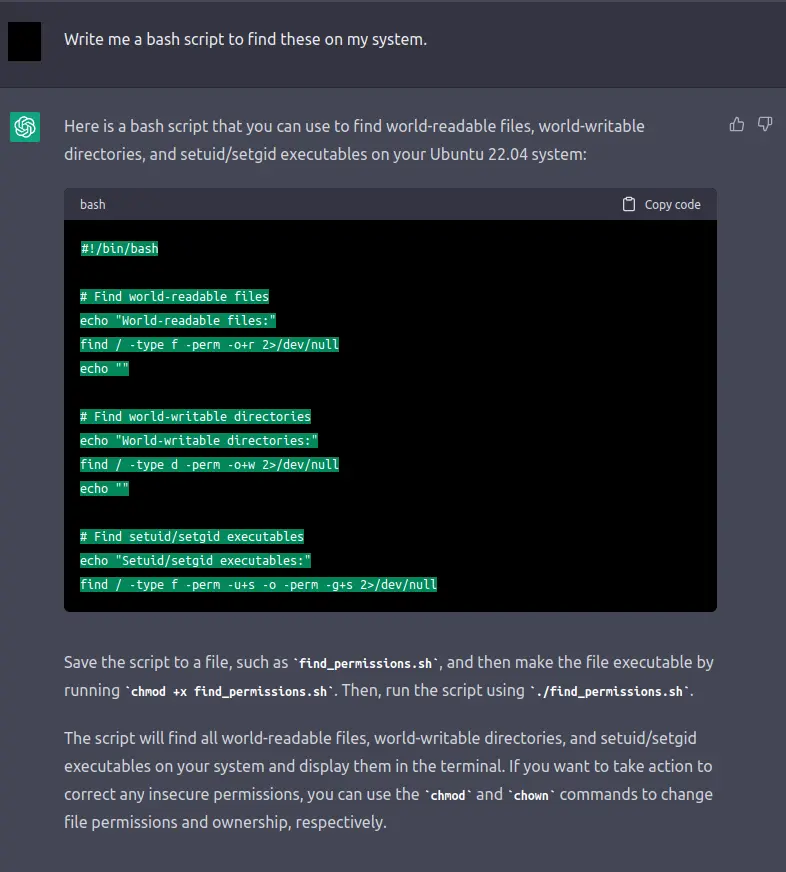
So of course when we execute this is going to give us a ton of output, it'll take us quite a while to ponder over this. Instead I'll run linpeas.
Sudo Settings
This is another good suggestion! Let's ask if there are any additional options we should set. Let's peek at our defaults:
$ sudo -l
[sudo] password for matt:
Matching Defaults entries for matt on ubuntu-desktop-0:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User matt may run the following commands on ubuntu-desktop-0:
(ALL : ALL) ALL
I'm going to take the stance that I don't mind logging in as root to preform an administrator action. As I continue using the system perhaps I'll want to add specific bin's here - but for now I'm going to disable everything and just allow the usage of su to gain root.
Let's have ChatGPT explain the output of sudo -l:

We should check the permissions of the secure_path to ensure I can't modify binaries there without first logging in as root.
ls -al /usr/local/sbin /usr/local/bin /usr/sbin /usr/bin /sbin /bin /snap/bin
This dumped permissions of all the binaries accessible via sudo. I confirmed I could not write to any of them or modify any of the directories.
Everything else here is fine, my user needs to get root on my system... so why restrict anything else? Does ChatGPT agree?
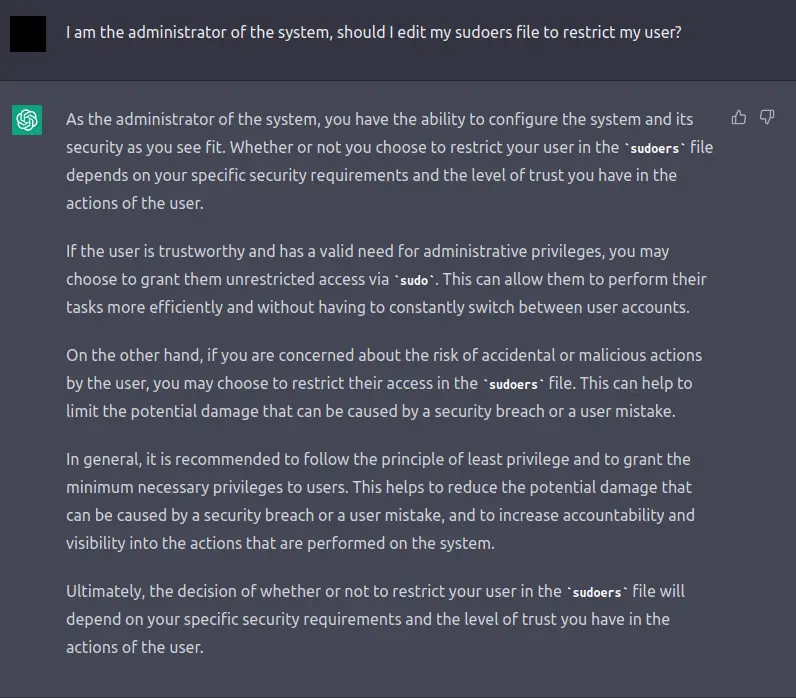
It does indeed! The key is to not just login as root and have a root session hanging around, stick to using sudo and configure the timeouts correctly.
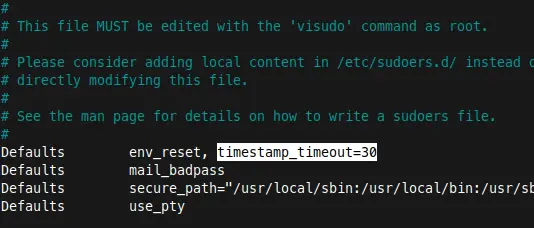
I did take ChatGPT's suggestion with the environment reset timer:
Automatic updates
Enable unattended-upgrades.
# install
sudo apt install unattended-upgrades
# Verify
sudo systemctl status unattended-upgrades
On Ubuntu 22.04 this is installed by default, though. You should check your configuration to make sure you're happy with it.
Check /etc/apt/apt.conf.d/20auto-upgrades. By default this basically runs apt update automatically every so often, and preforms apt upgrade automatically.
Also check etc/apt/apt.conf.d/50unattended-upgrades for fine grained control over what is actually updated.
Firewall
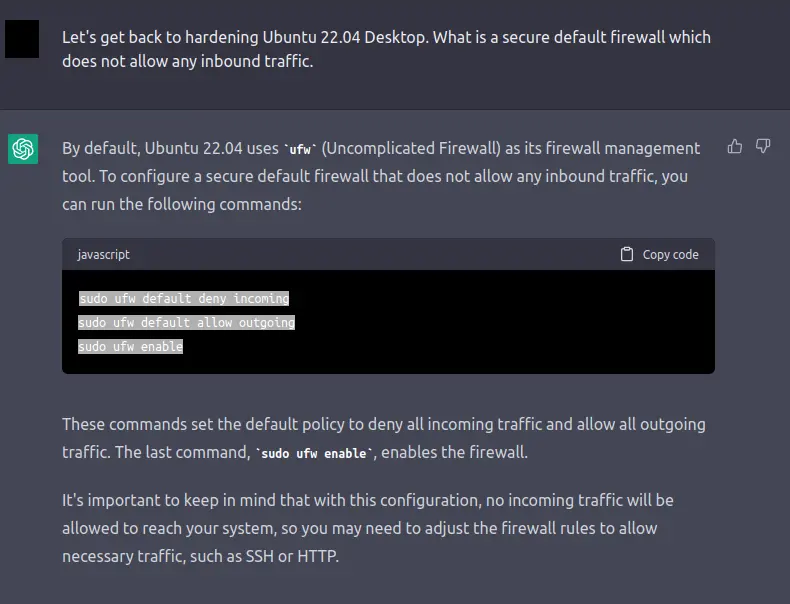
That's actually exactly what I wanted! I handle the nitty-gritty with pfSense I just needed something simple.
Application Fencing
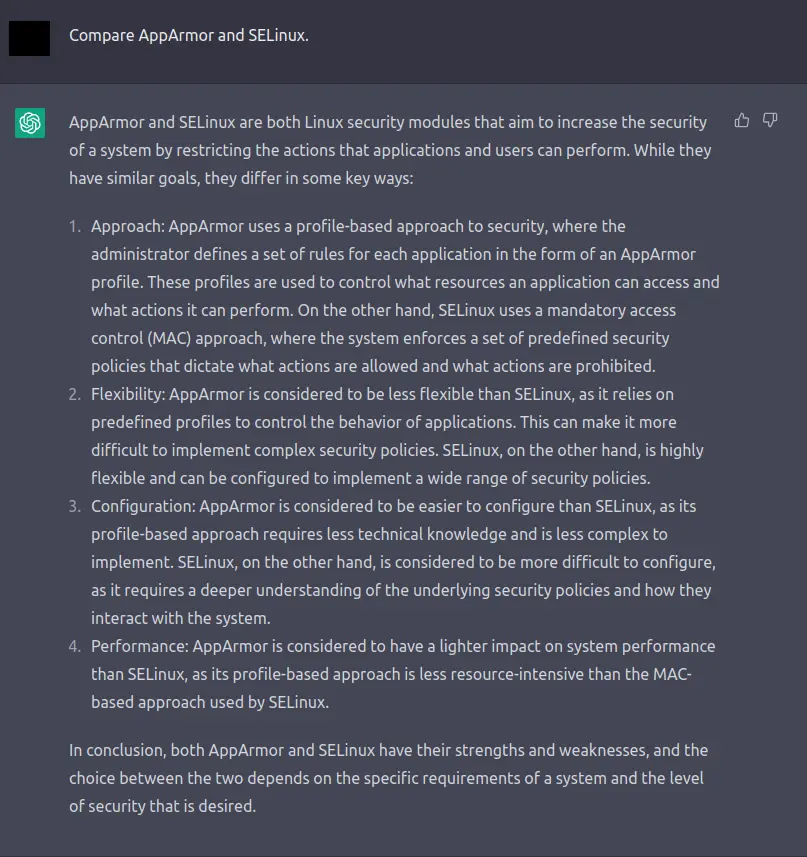
I think for a Desktop environment, SELinux is overkill as it's going to be constantly changing. I'll eventually write a guide on how I configured SELinux for my Proxmox docker nodes though.
For now, AppArmor is pre-installed on Ubuntu and it's easy enough for everyday use on my Desktop. I won't go through the details of how it works or how to use it, canonical's documentation is fully sufficient.
Most packages that are installed via snap ship with a profile, which is quite nice!
Network Services
Check out what's running ss -antpl:
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 127.0.0.1:631 0.0.0.0:*
LISTEN 0 128 [::1]:631 [::]:*
Port 53 is required for resolved so that's fine. But 631 is a printer discover service! I don't use printers, so I can safely disable it.
$ systemctl stop cups
Synchronizing state of cups.service with SysV service script with /lib/systemd/systemd-sysv-install.
Executing: /lib/systemd/systemd-sysv-install disable cups
Removed /etc/systemd/system/sockets.target.wants/cups.socket.
Removed /etc/systemd/system/multi-user.target.wants/cups.service.
Removed /etc/systemd/system/multi-user.target.wants/cups.path/
Removed /etc/systemd/system/printer.target.wants/cups.service.
$ systemctl disable cups
$ss -antpl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
Summary
ChatGPT did a decent job at giving me a head start into the basics. Of course the other custom parts I need to deep dive on, like setting up all the agents for integration with SecurityOnion and whatnot but ChatGPT wouldn't know about that unless I told it! It made a few mistakes, but nothing detrimental.