I may have been PWNED
I recently wen't through a large overhaul of my home lab's network topology to properly integrate a SOC node, running Security Onion. After I got everything setup and confirmed decent coverage of the network, I started exploring to learn the ropes.
How I Discovered
I'm used to securing systems, but I don't have any SOC experience. I was looking through Connections to see if I had all my sensors configured correctly.
I noticed some traffic from my ISP Subnet, 192.168.2.0/24 which is sort of weird because I don't actually have a sensor between ISP Wifi and the gateway because it's the ISP's device! I kept this wifi up as a backup for if my homelab went down, or to put untrusted devices onto like guests and IoT bullshit.
I noticed something that stuck out:
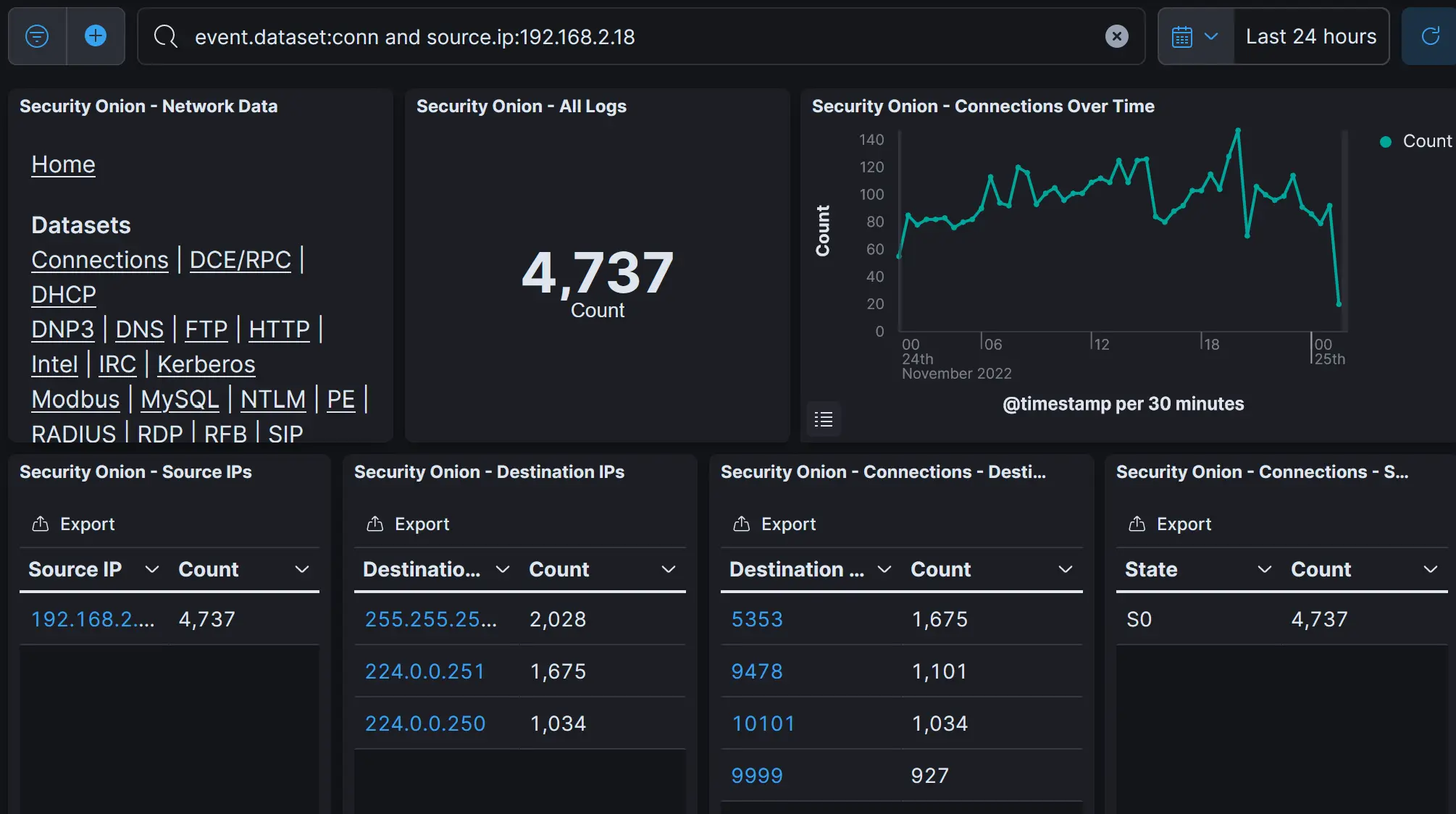 Traffic on
Traffic on 10101 struck me as weird. I did a quick search, and discovered it may be from one of a few pieces of malware.
HUNT!
Zeek and Suricata use a flow hashing algorithm to tag related traffic streams, letting us quickly pinpoint this traffic for further analysis.
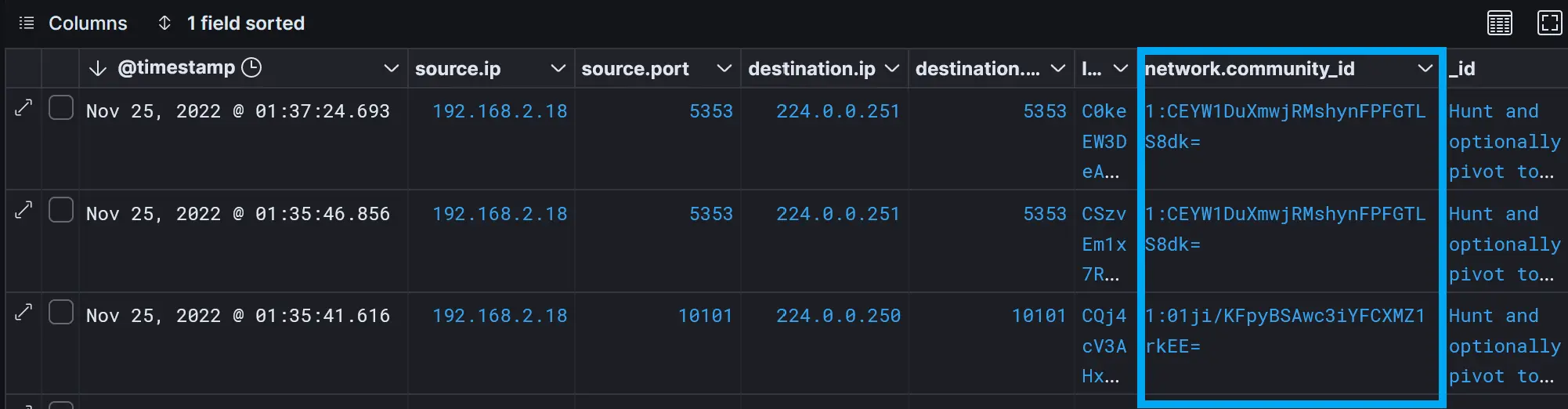
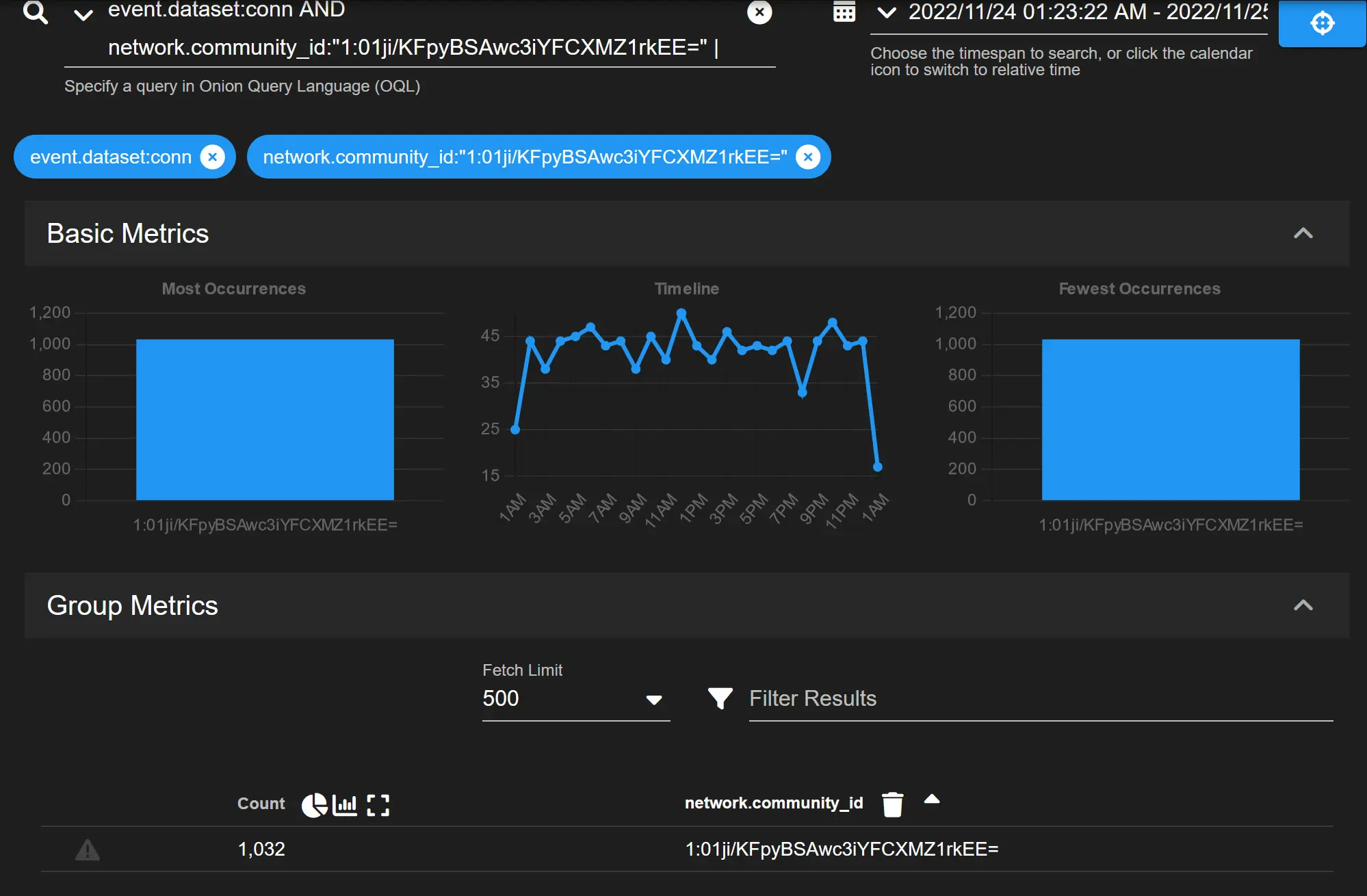
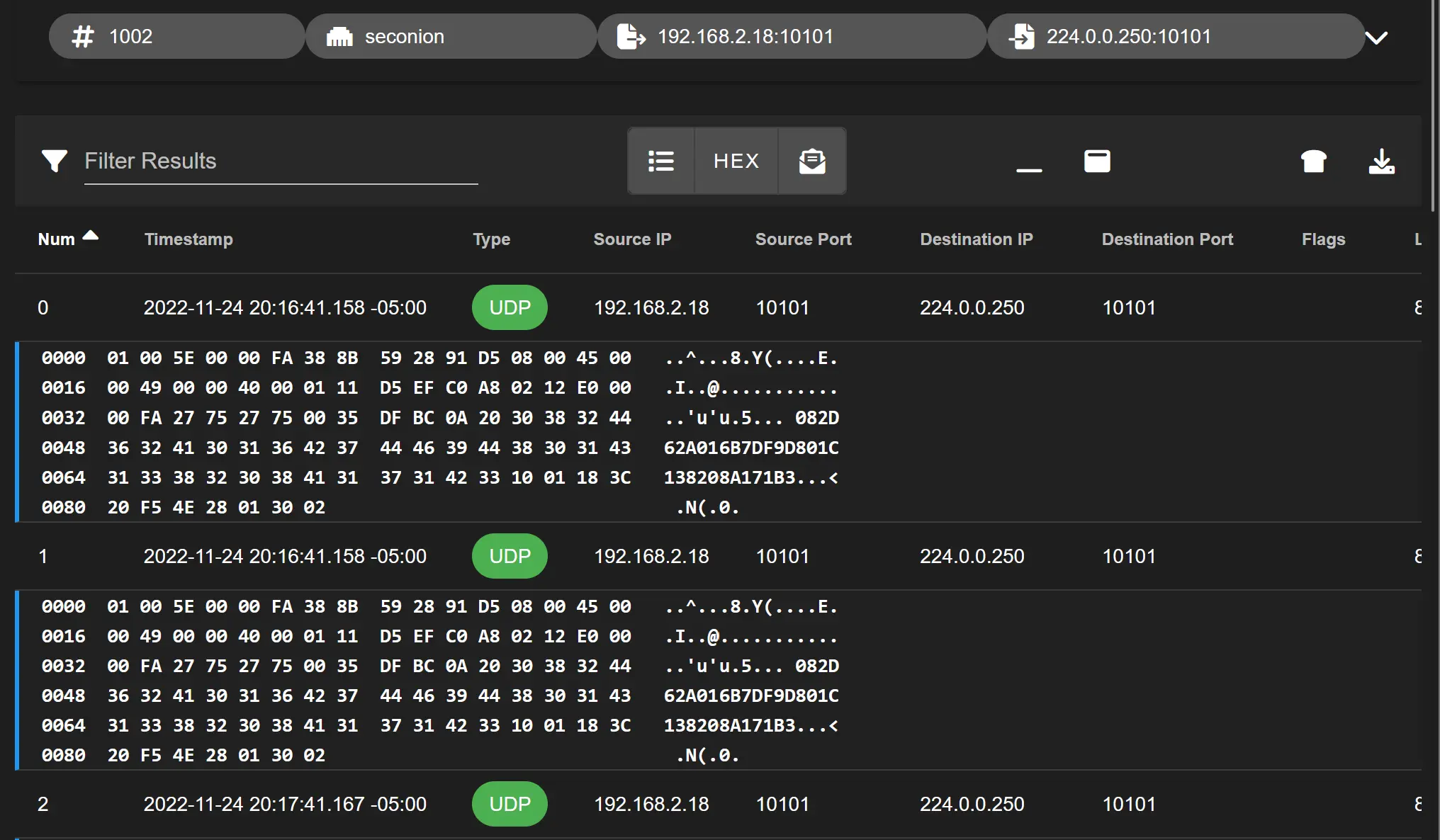
 This looks like a beacon for a backdoor doesn't it? I bet the payload in that
This looks like a beacon for a backdoor doesn't it? I bet the payload in that UDP packet is just a system identifier to a C&C Server.
There's a few paths I want to explore:
- Do some OSINT about the destination
- Analyize the host
First the host! It turns out... it's a Google Home Mini. Of course the IoT device got breached! At this point, I'm honestly relieved it wasn't my partner's laptop.
I bought this device off an online marketplace, met the guy in person. I do remember him being a little nervous, is it possible he planted malware on the device? Doesn't really matter. It's on the WAN network which is outside pfSense so it's unlikely it has made it's way into my homelab.
How do I analyize this thing? I took it off the network for now at least.
I searched for the destination
224.0.0.250and found virus total thinks everything is fine. This IP does look really weird though, right? Turns out, it's a multicast IP! The specific subnet it falls in is reserved for the use of routing protocols. It also can't be transmitted over the internet! Suman in this stack post thinks they're Bonjour/mDNS requests. In 2012, he thought they could be from iTunes. This all adds up so far. I kept looking around about known traffic from this device, and found that google has had a flaw in their device IP's in the past allowing remote code execution. Anyway it turns out this is just the google home making itself discoverable on the network, and announcing some details about it's capabilities. Phew!
Follow Up
This wasn't flagged in any alert, so this was really just my first experience threat hunting. I closed the case out but didn't have to create any filters or update any rules. I did verify that this traffic is blocked at pfSense and that no devices on my segmented network are easily discoverable from the WAN.