Try Hack Me - REvil Corp
I've been enjoying the IR challenges lately, perhaps just because I've gotten bored of the same webapp attack vectors and am learning something new over here. Anyhew, let's learn some memory analysis techniques! At the time of writing there's no write-up for this challenge, so hopefully I can be the first to the draw here and help others.
Walkthrough
Compromised Employee's Full Name
- Load the Redline file
- Click System Information in the left-hand menu
- Look Under
User Information
What is the operating system of the compromised host?
System Information->Operating System Information
What is the name of the malicious executable that the user opened?
- Click
File Download History
What is the full URL that the user visited to download the malicious binary?
- Click
File Download History
What is the MD5 hash of the binary?
- Go to
homeand click the second option - Wait for the dashboard to be generated
- Search for the malicious binary name
- Move through the results until you find the File creation event that includes the MD5 hash!
What is the size of the binary in kilobytes?
- Click
File Download History
What is the extension to which the user's files got renamed?
- Click
File Systemin the Analysis Data menu - Look for files that look like they had a weird extension appended to them (.txt or .zip originally)
What is the number of files that got renamed and changed to that extension?
Select the entire disk:
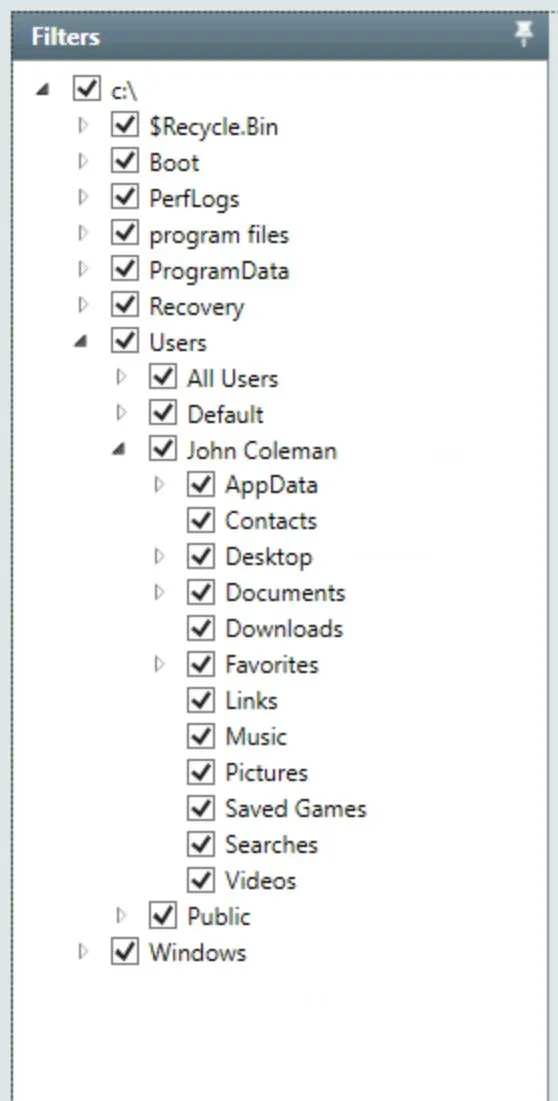 Filter for the extension change, the answer should be
Filter for the extension change, the answer should be matches/2, but it's actually matches*2 (An error in the room I think!)
What is the full path to the wallpaper that got changed by an attacker, including the image name?
Go to the timeline and filter to .bmp
The attacker left a note for the user on the Desktop; provide the name of the note with the extension.
Click filesystem and look for a readme file!
The attacker created a folder "Links for United States" under C:\Users\John Coleman\Favorites\ and left a file there. Provide the name of the file.
Filter for Favorites folder - the answer is the longest filename.
There is a hidden file that was created on the user's Desktop that has 0 bytes. Provide the name of the hidden file.
Filter for desktop and look at the two files with 0 bytes.
The user downloaded a decryptor hoping to decrypt all the files, but he failed. Provide the MD5 hash of the decryptor file.
We can see the file he downloaded onto his deskop. Take the filename and search the timeline to get the MD5 hash.
In the ransomware note, the attacker provided a URL that is accessible through the normal browser in order to decrypt one of the encrypted files for free. The user attempted to visit it. Provide the full URL path.
Look at the user's browser history and search for decrypt
What are some three names associated with the malware which infected this host? (enter the names in alphabetical order)
This one was tricky because I could only find two names myself. You can quickly get two from Virustotal, the third was actually an alias for the group name rather than the payload itself, but I found it mentioned on Tripwire.com.
Write-Up
We're provided a machine with the challenge that we boot up, there's one folder on the desktop containing a redline session that I opened:
 Fair warning - I've never heard of this software before so this is all new to me!
Alright once it finished loading we're presenting a big nested list of analysis data:
Fair warning - I've never heard of this software before so this is all new to me!
Alright once it finished loading we're presenting a big nested list of analysis data:
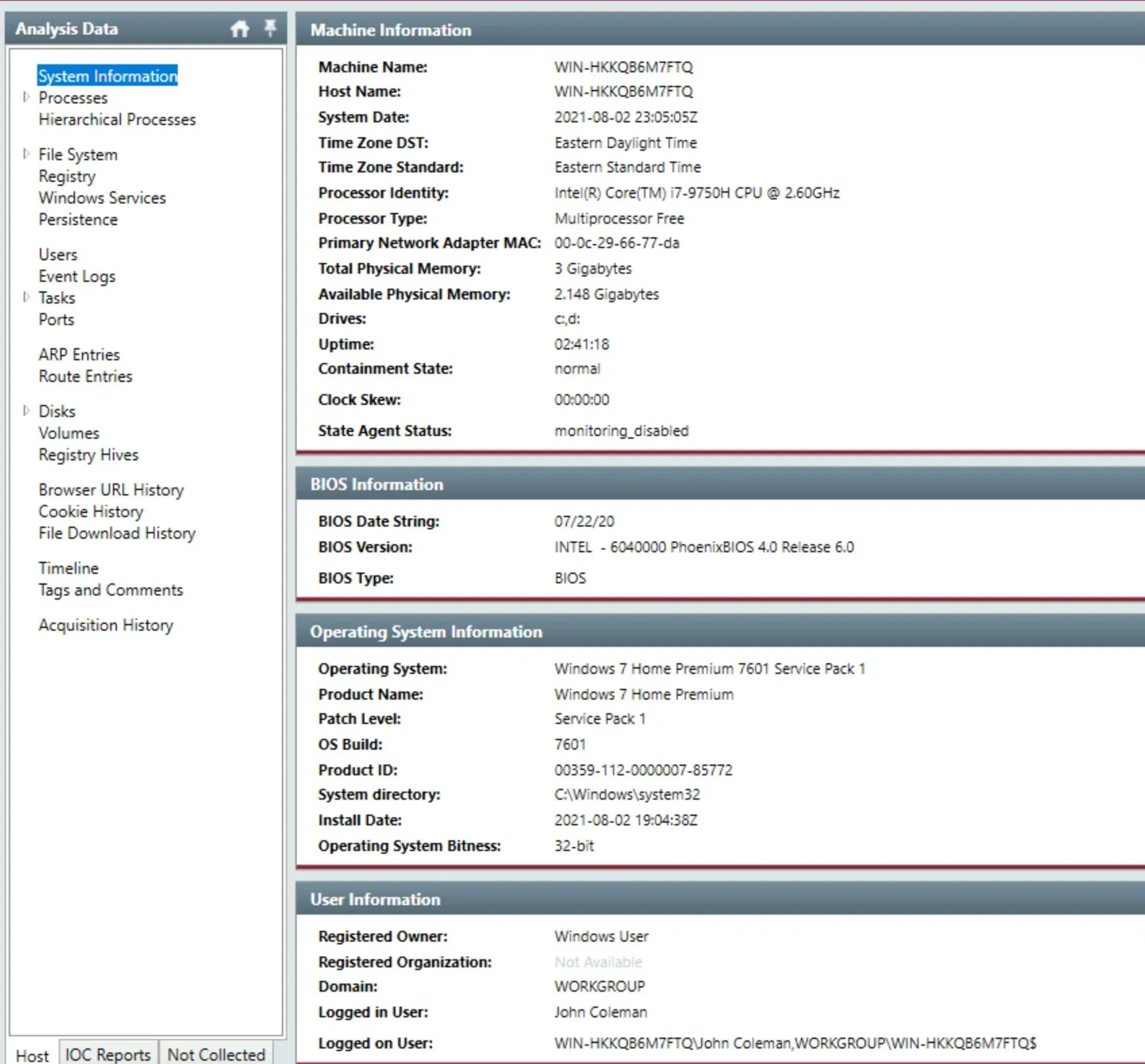 I quickly found the first few pieces of information, and started looking to figure out what malicious payload has been executed. There is no data in the
I quickly found the first few pieces of information, and started looking to figure out what malicious payload has been executed. There is no data in the Processes menu.
I looked in event logs, and there are logs starting from 2011 to 2021 here. No wonder it took so long to load this.
I sorted for newest logs first and started reading through to try to notice some paterns.
There's a huge list of System fatal alters near the end of log capture with fatal alert was received: 70 || 40. I tried to scroll to the top of that to see what may have triggered it:
- DNS query for
gavelmasters.com MSIEXEC.exetriggered a system reboot Their browser history may prove useful as well: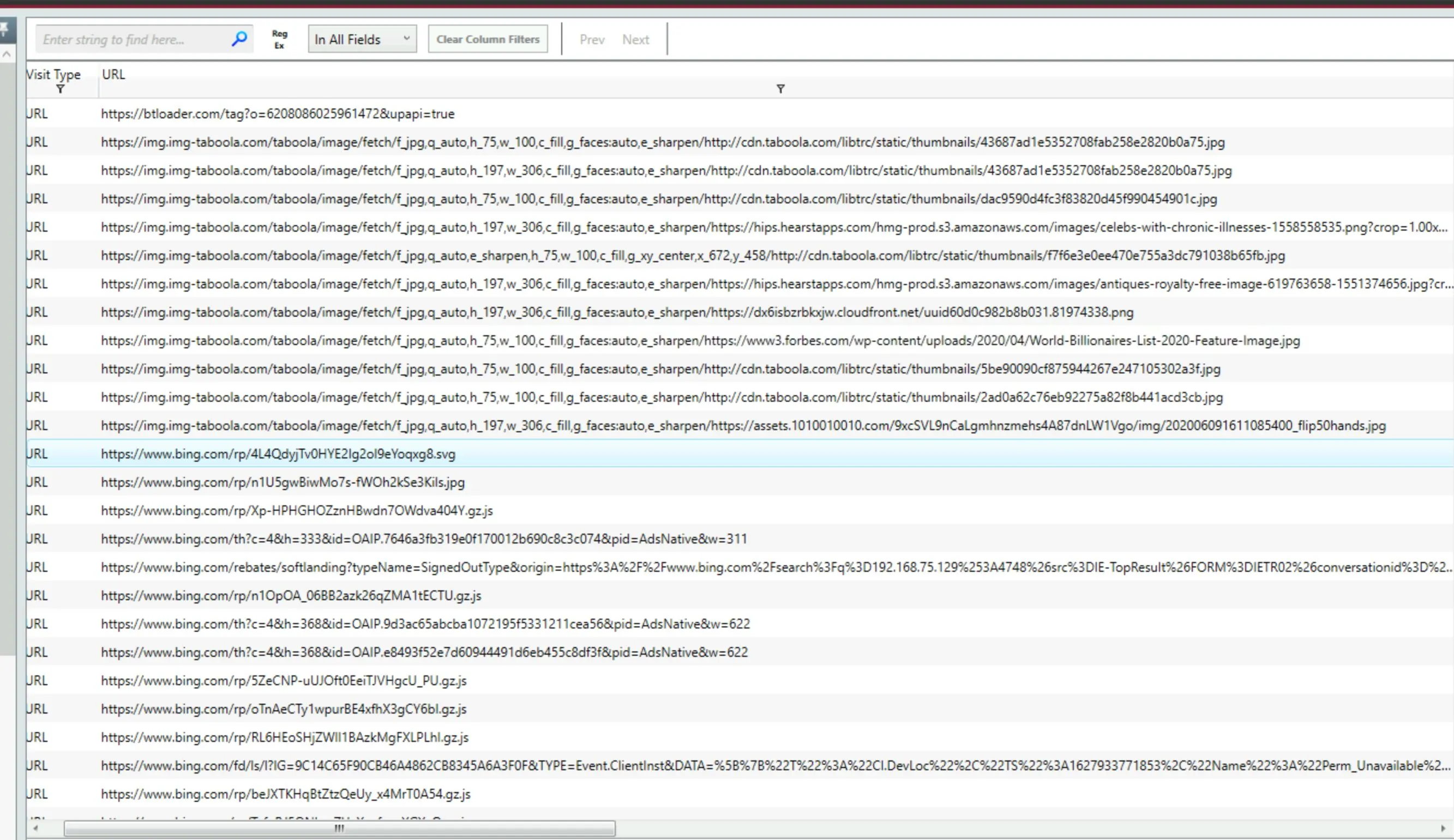 Here's a little summary of notable activity:
Here's a little summary of notable activity:- Last visited was
btloader.com - Visited Torproject frequently, could easily have contracted malware from there while trying to obtain something himself...
- Was hosting something on his machine:
http://192.168.75.129:4748/Documents(Not from future self, this wasn't his machines IP!) - It looks like a browser was used to access some files on the system (Is this remote access activity or something?), picture below
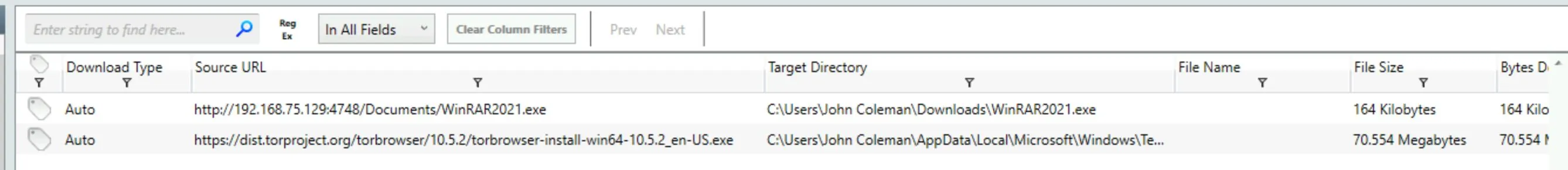
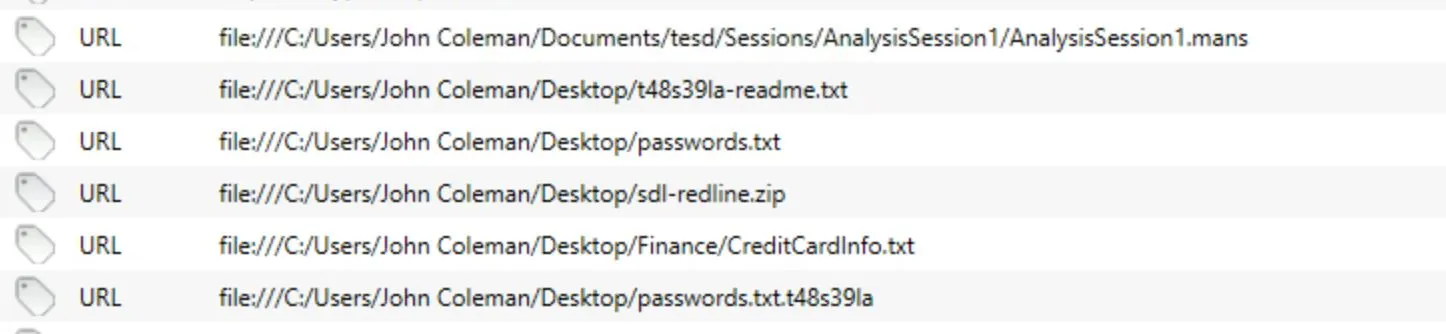 File downloads seem very telling:
File downloads seem very telling:
 I kept poking around, and wound up going back to home and clicking the second option which produced a lovely filtered dashboard of what appears to be everything important. I searched for the
I kept poking around, and wound up going back to home and clicking the second option which produced a lovely filtered dashboard of what appears to be everything important. I searched for the .exeand found the MD5 of the payload!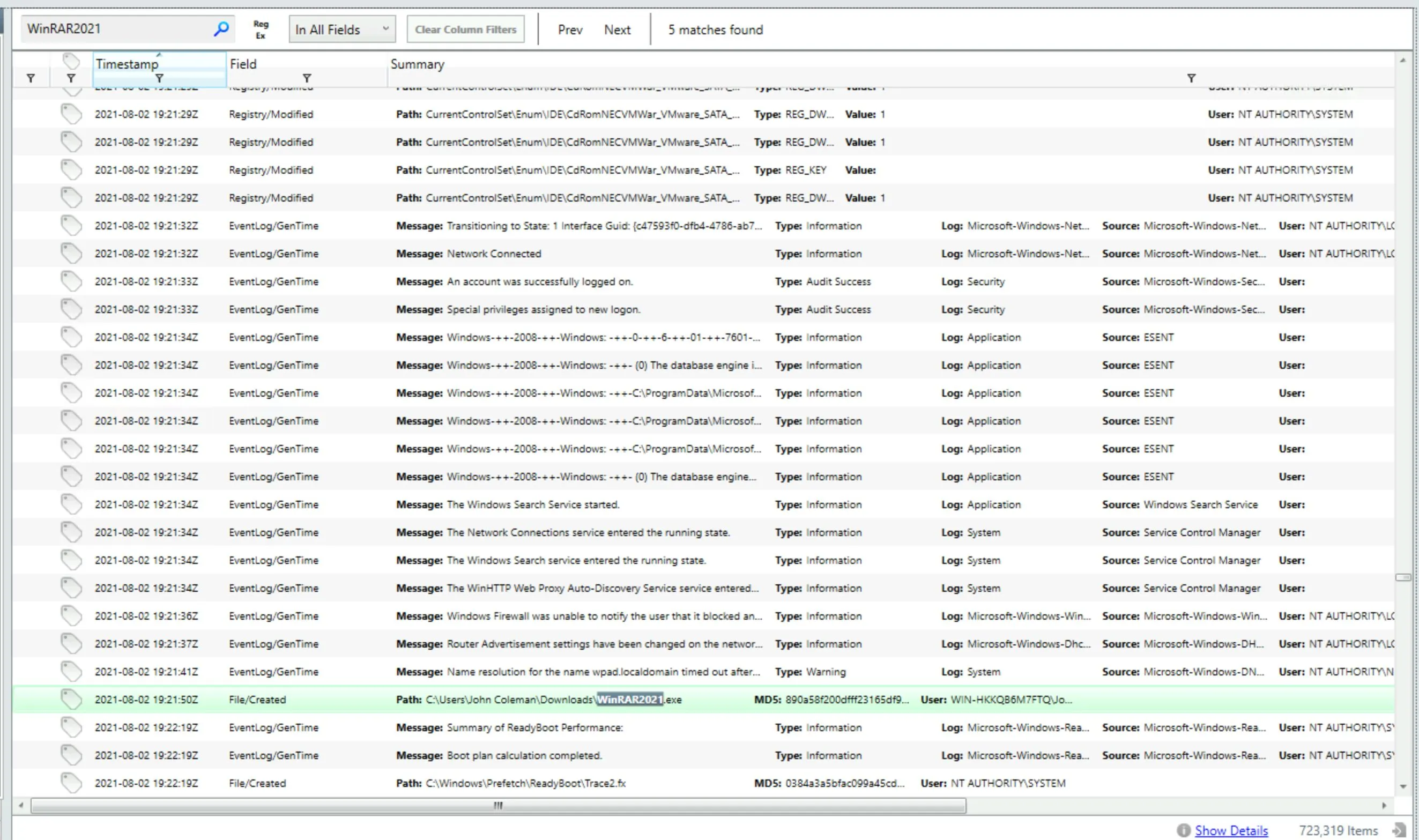 This is pretty well discussed on Virustotal.
The Hints in this room tell us to look at the user's desktop but I can't seem to figure out how to do that... turns out you just need to click
This is pretty well discussed on Virustotal.
The Hints in this room tell us to look at the user's desktop but I can't seem to figure out how to do that... turns out you just need to click file systemwhich I thought was just a heading not an actual menu: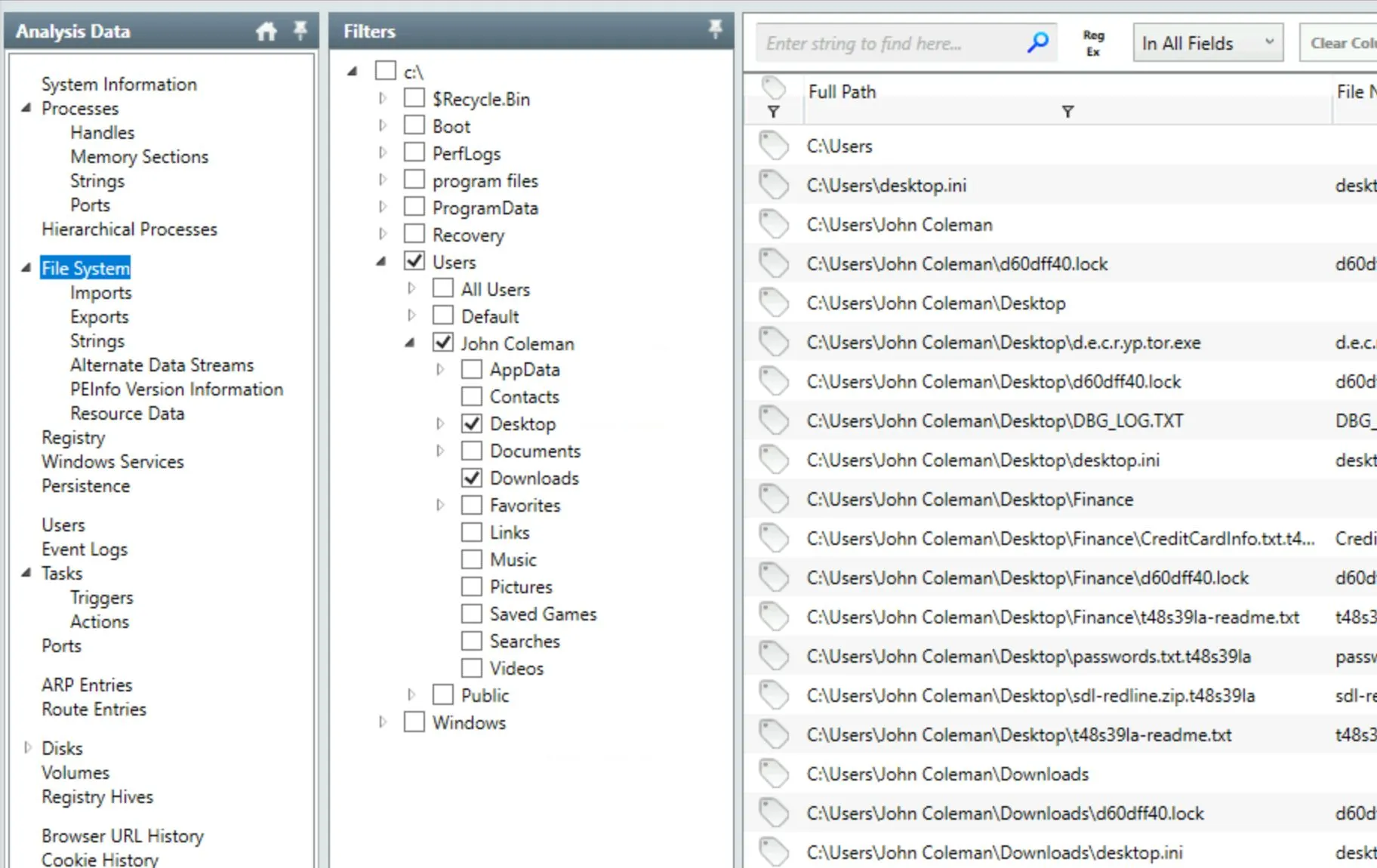 A lot of the remaining questions are very easy once you know how to navigate around this UI a little...
interesting to note, the file he downloading trying to get his files back was another piece of malware. Poor guy.
Using the virustotal page I quickly found two of the names associated with this piece of malware, but I had trouble finding the third... because it turned out to actually be an alias for the group rather than the payload...
A lot of the remaining questions are very easy once you know how to navigate around this UI a little...
interesting to note, the file he downloading trying to get his files back was another piece of malware. Poor guy.
Using the virustotal page I quickly found two of the names associated with this piece of malware, but I had trouble finding the third... because it turned out to actually be an alias for the group rather than the payload...