Try Hack Me - Neighbour
I want to dive into a CTF to test my new fancy C2 framework and staged payload magic! This is the newest box released on THM, let's go!
$ rustscan -a $TARGET -- -A -sC
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 1048476'.
Open 10.10.236.47:22
Open 10.10.236.47:80
$ nikto --host $TARGET --port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.236.47
+ Target Hostname: 10.10.236.47
+ Target Port: 80
+ Start Time: 2022-11-17 22:44:13 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.53 (Debian)
+ Cookie PHPSESSID created without the httponly flag
+ Retrieved x-powered-by header: PHP/8.0.19
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3093: /db.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ /login.php: Admin login page/section found.
+ 7889 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2022-11-17 22:57:34 (GMT-5) (801 seconds)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
curl $TARGET
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Login</title>
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css">
<style>
body{ font: 14px sans-serif; }
.wrapper{ width: 360px; padding: 20px; margin: 0 auto; }
</style>
</head>
<body>
<div class="wrapper">
<h2>Login</h2>
<p>Please fill in your credentials to login.</p>
<form action="/index.php" method="post">
<div class="form-group">
<label>Username</label>
<input type="text" name="username" class="form-control " value="">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<label>Password</label>
<input type="password" name="password" class="form-control ">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<input type="submit" class="btn btn-primary" value="Login">
</div>
<p>Don't have an account? Use the guest account! (<code>Ctrl+U</code>)</p>
<!-- use guest:guest credentials until registration is fixed. "admin" user account is off limits!!!!! -->
</form>
</div>
</body>
</html>
curl $TARGET/login.php
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Login</title>
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css">
<style>
body{ font: 14px sans-serif; }
.wrapper{ width: 360px; padding: 20px; margin: 0 auto; }
</style>
</head>
<body>
<div class="wrapper">
<h2>Login</h2>
<p>Please fill in your credentials to login.</p>
<form action="/login.php" method="post">
<div class="form-group">
<label>Username</label>
<input type="text" name="username" class="form-control " value="">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<label>Password</label>
<input type="password" name="password" class="form-control ">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<input type="submit" class="btn btn-primary" value="Login">
</div>
<p>Don't have an account? Use the guest account! (<code>Ctrl+U</code>)</p>
<!-- use guest:guest credentials until registration is fixed -->
</form>
</div>
</body>
</html>
curl -v $TARGET/db.php
* Trying 10.10.236.47:80...
* Connected to 10.10.236.47 (10.10.236.47) port 80 (#0)
> GET /db.php HTTP/1.1
> Host: 10.10.236.47
> User-Agent: curl/7.85.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Fri, 18 Nov 2022 04:06:07 GMT
< Server: Apache/2.4.53 (Debian)
< X-Powered-By: PHP/8.0.19
< Content-Length: 0
< Content-Type: text/html; charset=UTF-8
<
* Connection #0 to host 10.10.236.47 left intact
Time to start poking with Burpsuite...
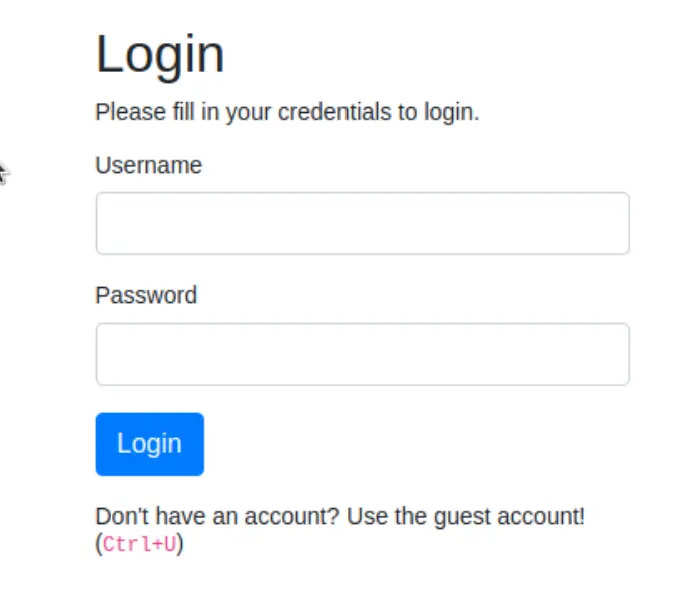 I logged in with the guest credentials found in the html...
I logged in with the guest credentials found in the html...
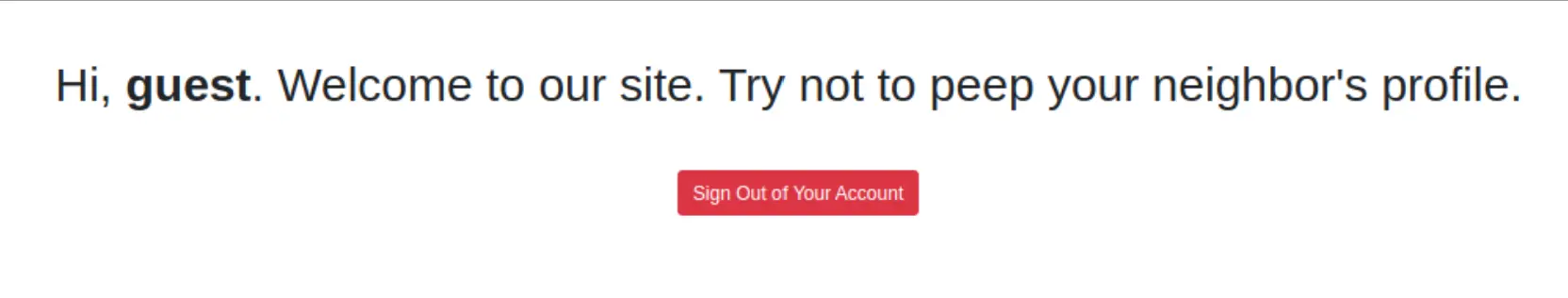 Okay this probably means there's a vulnerable session we can mess with. There's nothing in the response in Burp though... The login sequence is:
Okay this probably means there's a vulnerable session we can mess with. There's nothing in the response in Burp though... The login sequence is:
- Get
/, render index page shown above - Post
/index.phpwith data:username=guest&password=guest - Get
/profile.php?user=guestThe URL does look like something we should play with, though. The obvious thing to do was put inneighbor.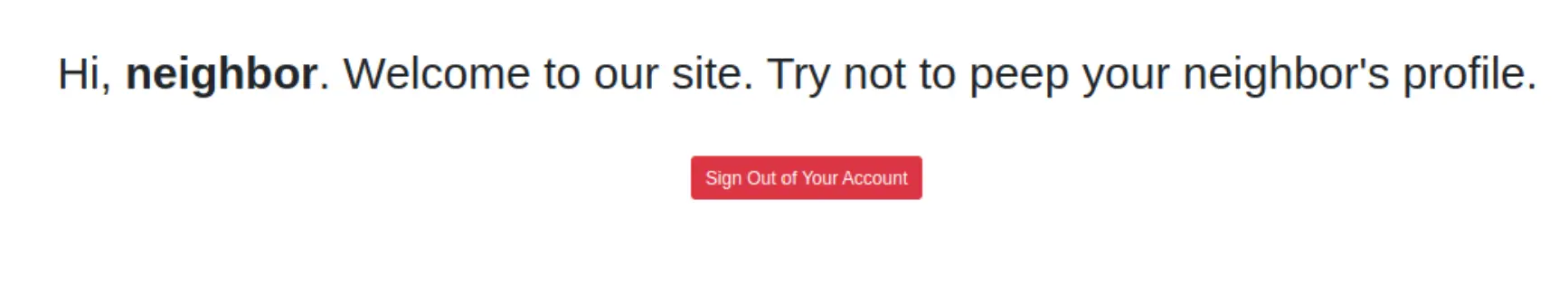 Okay... it must just get rendered right onto the page. Yeah whatever I change it to, is rendered on the page.
So this is likely PHP Injection, or perhaps just XSS? I tried a few payloads, and as I was looking at the output I noticed "The admin account could be vulnerable"... So I slapped in
Okay... it must just get rendered right onto the page. Yeah whatever I change it to, is rendered on the page.
So this is likely PHP Injection, or perhaps just XSS? I tried a few payloads, and as I was looking at the output I noticed "The admin account could be vulnerable"... So I slapped in adminas the user... and got the flag. I didn't even get to try my fancy Post framework :(